One of the relating to mistakes your website guests can come across is a safety caution. With the entire brute drive assaults, malware, and denial of carrier assaults, it’s seriously essential for web customers to browse and store securely. In case your website is showing the ERR_SSL_OBSOLETE_VERSION caution, guests received’t have the ability to get admission to your website with out clicking on a hyperlink within the error that principally tells them that they shouldn’t go back.
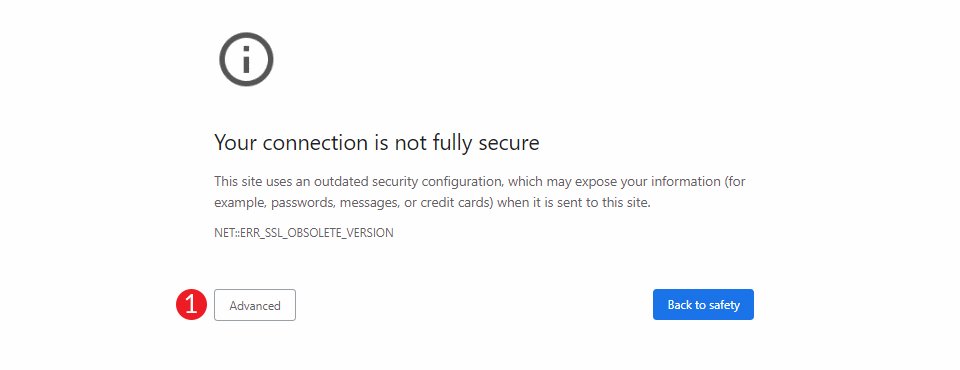
On this put up, we’ll talk about what the ERR_SSL_OBSOLETE_VERSION caution is and what steps you’ll take to mend it. We’ll additionally display you how one can check those fixes in the neighborhood at the two maximum commonplace internet servers — Apache and NGINX. Let’s rock and roll.
What’s the ERR_SSL_OBSOLETE_VERSION Caution?
The ERR_SSL_OBSOLETE_VERSION caution is an error message your website guests see in case your safety certificates is the use of an old-fashioned model akin to TLS 1.0 or 1.1. Starting with the discharge of Chrome 72, the ones variations have been now not supported.
What’s TLS vs SSL?
Delivery Layer Safety (TLS) is an web safety protocol that allows authentication and secure supply of content material on the web. For instance, it makes such things as the use of a bank card for purchases or filling out worker packages with delicate knowledge on web sites secure.
Protected Socket Layers (SSL) is a deprecated means of encrypting the relationship between a shopper and a server that has been changed by way of the brand new TLS means. The distinction between TLS and SSL at the present time is in point of fact just a topic of terminology. Most of the people nonetheless use the time period SSL despite the fact that TLS is the real protocol getting used.
Why Will have to You Care About TLS in case you have an SSL?
As up to now discussed, your website is technically now not the use of SSL anymore anyway. Usually talking, all SSL certificate are if truth be told TLS certificate at the present time. Maximum web hosting suppliers nonetheless use the time period SSL certificates as a result of the notoriety it brings, however use TLS for its safety and pace benefits.
How Updating Your Server’s TLS Model Can Repair ERR_SSL_OBSOLETE_VERSION
In 2019, Google introduced that they might be discontinuing TLS 1.0 and 1.1 on Chrome as a result of their safety vulnerabilities. For the reason that liberate of TLS 1.3 in 2018, Chrome has required no less than model 1.2 to show web sites and not using a caution. In consequence, all web sites using earlier variations of TLS are slapped with an unpleasant ERR_SSL_OBSOLETE_VERSION message. The use of unsupported variations of TLS is bad — now not most effective in your web site but in addition in your guests.
Maximum primary browsers now enhance TLS 1.3 (IE excluded) and its the default for delivery safety for Google, Youtube, and Netflix since 2020, amongst others. No longer most effective does TLS 1.3 be offering upper ranges of safety, but it surely additionally transfers information a lot sooner. For instance, TLS 1.3 takes part the time to switch information out of your customer’s browser for your server than TLS 1.2 does. As well as, different web protocols akin to HTTPS, SMTP, and POP3 (used for emails), are already using more moderen variations of TLS. Despite the fact that you aren’t receiving a caution to your website, you must make certain that your website is working no less than TLS model 1.2. The protection of your web site is determined by it.
How you can repair ERR_SSL_OBSOLETE_VERSION in Chrome
In case you are already seeing this mistake in Chrome when looking to get admission to your web site, your website is most probably working an old-fashioned TLS model. Solving this downside would require quite a lot of other strategies that rely in the end to your explicit web hosting supplier. On the other hand, a great spot to begin is to make sure what model of TLS your website is working.
How To In finding What Model of TLS Your Web page is Working
You’ll be able to get admission to this data in Chrome by way of the use of the dev equipment and a keyboard shortcut. Press the Command+Choice+C keys (on Mac) or Keep an eye on+Shift+C (on Home windows and Linux). Subsequent, click on at the safety tab. The display will pop up and disclose the model of TLS working to your website.

How To In finding What Model of TLS Your Site Host/Server is Working
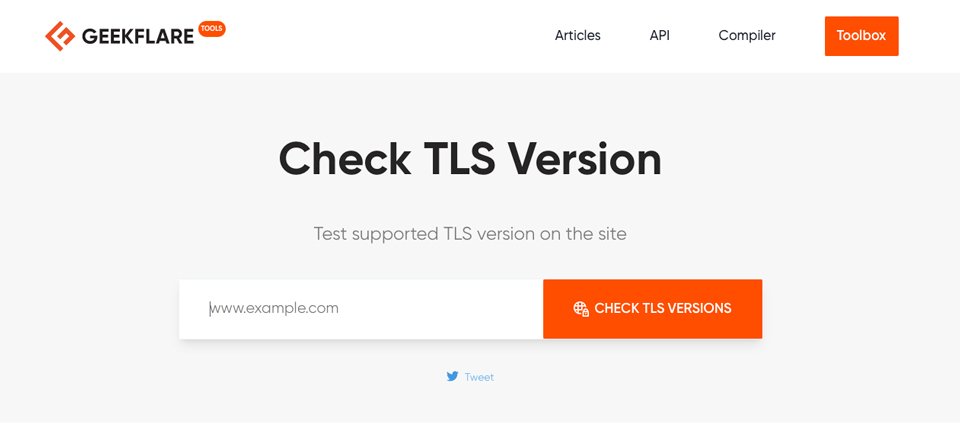
Prior to contacting your host or making any adjustments for your internet host’s information, it’s a good suggestion to test to look in case your host server helps TLS 1.2 or 1.3. You’ll be able to accomplish this by way of visiting Geekflare’s TLS checker. Kind to your host’s URL and click on put up. When the consequences seem, scroll down till you notice protocols put in. Search for TLS 1.2 and 1.3. If they’re supported, you’ll see sure subsequent to every.
Touch or Replace Your Website hosting Supplier
Upon getting verified that your website and/or server is working an old-fashioned TLS model, the simplest option to the ERR_SSL_OBSOLETE_VERSION error is to achieve out for your web hosting supplier to resolve in case your model of TLS may also be upgraded. Switching from TLS 1.0 or 1.1 to TLS 1.2+ would repair your downside. If that isn’t an choice, it’s time to begin researching a brand new host in your website.
We performed exams on a number of most sensible web hosting suppliers to check their server’s capacity for working TLS 1.3. Siteground, WP Engine, Pressable, Flywheel, Bluehost, and Cloudways all enhance it. So, when you host with any of those suppliers, likelihood is that you received’t see the ERR_SSL_OBSOLETE_VERSION error. On the other hand, we must observe that simply because a web hosting supplier might enhance probably the most present TLS model, that doesn’t imply they’re if truth be told working it. Some internet hosts nonetheless use 1.1 by way of default, which isn’t nice. That’s why it’s essential to test which model is recently put in to your website.
Trying out a Repair to the ERR_SSL_OBSOLETE_VERSION Error on a Native Server
If you wish to examine that updating the TLS model will repair the ERR_SSL_OBSOLETE_VERSION error in your web site, you’ll at all times check it the use of a neighborhood server.
In case you’re working WordPress, your web hosting supplier possibly makes use of Apache or NGINX internet servers. For the aim of this educational, we’ll be the use of a native server and MAMP Professional to edit our SSLProtocol information on Apache and NGINX to disable TLS 1.0 and 1.1. Subsequent, we’ll permit enhance for TLS 1.2 and 1.3. In case you are the use of a Home windows system, you’ll practice along side us the use of WAMP to perform the similar process.

We’d love to reiterate that you simply take a look at together with your host to verify that they enhance TLS 1.2 or 1.3. Making adjustments for your SSLProtocols with out the right kind enhance will lead to breaking your SSL certificates.
How you can Replace TSL Model in Apache The use of Mamp Professional
In case you’re the use of MAMP Professional for this educational, we’ll suppose you’re already aware of how one can create a WordPress website and set up an SSL. If you wish to have some route on how to try this, take a look at our Final Information to MAMP Professional for WordPress Customers.
How Disable TLS 1.0 and 1.1 in Apache
To be able to disable TLS 1.0 and 1.1 in Apache, you’ll want to edit the configuration report that incorporates the SSLProtocol in your internet server. Relying at the platform you’re the use of, this report may well be positioned in other places.
On a default Apache location, it’s more likely to be positioned right here:
/usr/native/apache2/conf/additional/httpd-ssl.conf
In case you are working an Ubuntu/Debian server, the report shall be discovered right here:
/and so forth/apache2/mods-enabled/ssl.conf
After all, if you’re working a neighborhood server on macOS by means of MAMP Professional (as we’re), you’ll to find the report right here:
/mamp/conf/apache/additional/httpd-ssl.conf
Subsequent, search for the SSL Protocol Strengthen segment, which is able to include a couple of traces of code. That is the default surroundings of your httpd-ssl.conf report:
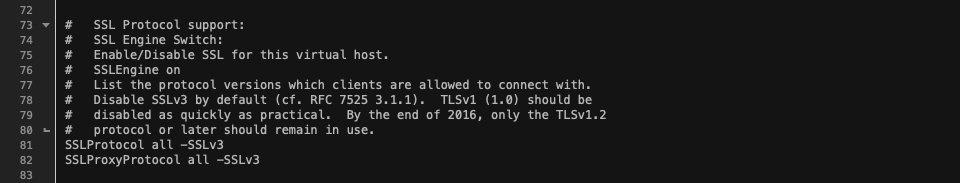
To resolve what protocols are enabled, have a look at the ultimate two traces of code.
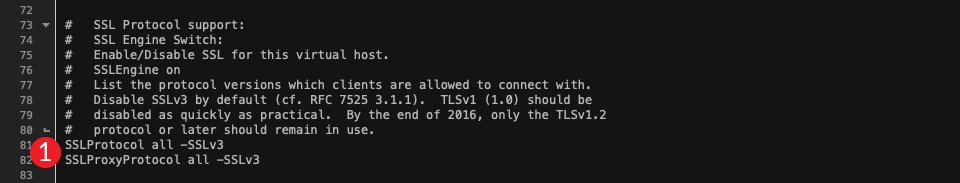
We can want to inform Apache to simply run variations of TLS 1.2 or above. At the moment, all variations are enabled. To switch that, you’ll alternate SSLProtocol all -SSLv3 SSLProxyProtocol all -SSLv3 to the next:
SSLProtocol TLSv1.1 TLSv1.2
The report must now appear to be this:
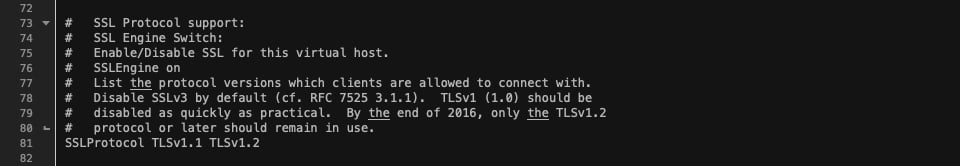
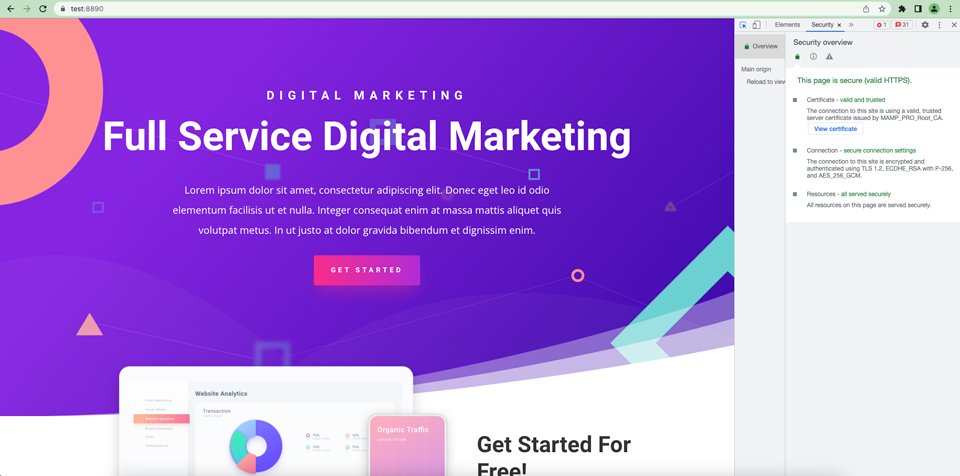
The ultimate step is to restart the server. As soon as the server restarts, open your web site in an incognito window. The ERR_SSL_OBSOLETE_VERSION caution must be long past. Open your website and use the dev equipment to view your safety settings.
How you can Replace TLS Model in NGINX The use of Mamp Professional
To replace the SSLProtocol on an NGINX internet server, you’ll want to find your website’s configuration information. It may be positioned in the main NGINX configuration report, as in with MAMP Professional. To edit the report the use of MAMP, navigate to mamp/conf/nginx/nginx.conf. Open the report together with your HTML/textual content editor. For this educational, we’re the use of BBedit, however any editor will do. In case you aren’t following alongside the use of MAMP Professional, the nginx.conf report is normally positioned in /and so forth/nginx/nginx.conf.
Scroll against the ground till you notice the road starting with ssl_protocols. If in case you have all TLS variations enabled, your report will appear to be this:
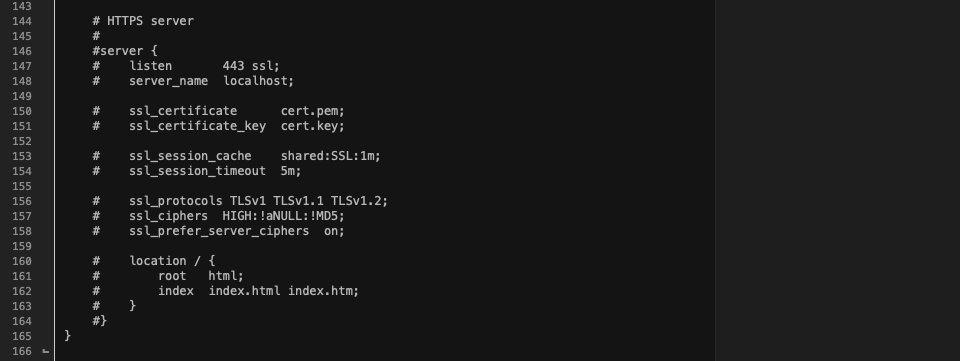
As you’ll see, TLS 1.0, 1.1, and 1.2 are enabled, however there’s no enhance for 1.3. To switch that, you’ll need to alternate ssl_protocols TLSv1 TLSv1.1 TLSv1.2; to the next:
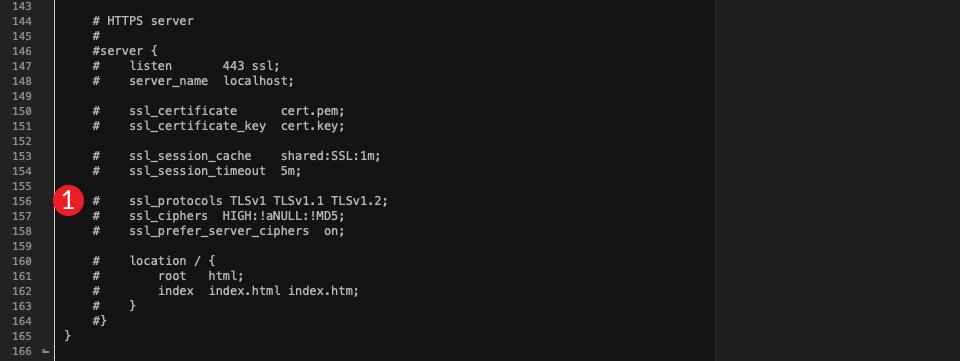
ssl_protocols TLSv1.2 TLSv1.3;
The report must now appear to be this:
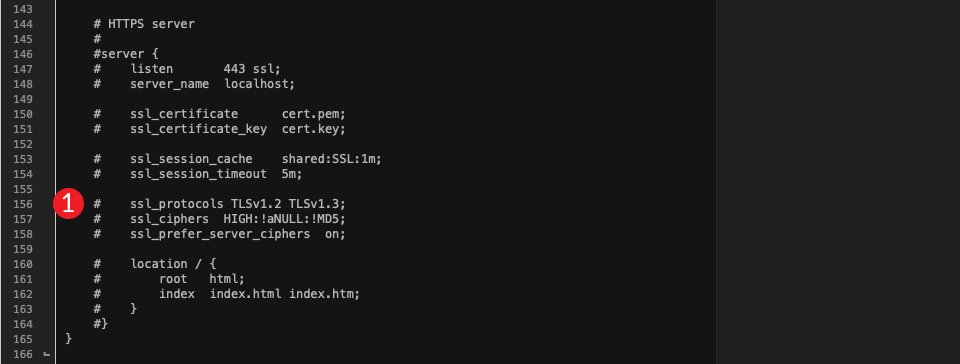
Your server must now most effective be the use of TLS variations 1.2 and 1.3. To substantiate, restart your server and pull up your website in Chrome. Take a look at your settings the use of the dev inspector equipment. As up to now discussed, you’ll do that by way of urgent the Command+Choice+C keys (on Mac) or Keep an eye on+Shift+C (on Home windows and Linux), then clicking at the safety tab.
We’d like to say that settings to your default configuration may well be overwritten by way of a person area’s server block. If in case you have carried out our repair and are nonetheless getting the ERR_SSL_OBSOLETE_VERSION caution, that may be the foundation purpose.
Wrapping Issues Up
With safety considerations rising at a speedy tempo, it’s essential to stay your website up-to-the-minute with the newest variations of TLS. We all know that browser mistakes could be a irritating enjoy, particularly when you don’t know what to do to mend them. You’ll be able to verify the problem the use of equipment like Chrome Dev Gear and Geekflare’s TLS checker. However, sadly, the option to the issue is updating the TLS model which will most effective be accomplished on the server degree. So the most productive factor to do is touch your host or, if wanted, improve your web hosting supplier to ensure they enhance the brand new TLS variations. It additionally could be useful to check more moderen variations of TLS to your website in the neighborhood on Apache and NGINX internet servers. This may occasionally lend a hand make certain that your guests received’t be faced with the unpleasant ERR_SSL_OBSOLETE_VERSION caution while you do take the ones adjustments reside.
Have you ever ever encountered the ERR_SSL_OBSOLETE_VERSION caution error in Chrome? If that is so, pontificate within the remark segment beneath.
Featured Symbol valeriya kozoriz, Funtap / shutterstock.com
The put up How you can Repair ERR_SSL_OBSOLETE_VERSION Caution in Chrome gave the impression first on Chic Issues Weblog.
WordPress Web Design