In terms of WordPress safety, there are a large number of issues you’ll do to fasten down your web site to forestall hackers and vulnerabilities from affecting your ecommerce web site or weblog. The very last thing you need to occur is to get up one morning to find your web site in shambles. So these days we’re going to be sharing a large number of guidelines, methods, and strategies you’ll use to raised your WordPress safety and keep secure.
When you’re a Kinsta shopper, you don’t wish to concern about a large number of those, as we provide loose hack fixes! However even with this ensure, you will have to at all times apply the most efficient safety practices.
Is WordPress Safe?
The primary query you’re most definitely questioning, is WordPress secure? For probably the most phase, sure. Alternatively, WordPress generally will get a nasty rap for being at risk of safety vulnerabilities and inherently now not being a protected platform to make use of for a industry. Extra ceaselessly than now not that is because of the truth that customers stay following industry-proven safety worst-practices.
Nonetheless searching for that best WordPress host?
-
Absolutely controlled -
Safe like Castle Knox
-
Loose migrations
-
Final velocity
-
Day-to-day backups
-
Google Cloud Platform
The use of out of date WordPress instrument, nulled plugins, deficient gadget management, credentials control, and loss of essential Internet and safety wisdom amongst non-techie WordPress customers stay hackers on best of their cyber-crime recreation. Even {industry} leaders don’t at all times use the most efficient practices. Reuters was hacked as a result of they had been the usage of an out of date model of WordPress.
Basically, safety isn’t about completely safe programs. This kind of factor may nicely be impractical, or inconceivable to search out and/or handle. What safety is even though is possibility relief, now not possibility removal. It’s about using all of the suitable controls to be had to you, is fairly, that can help you reinforce your total posture decreasing the percentages of constructing your self a goal, due to this fact getting hacked. – WordPress Security Codex
Now, this isn’t to mention vulnerabilities don’t exist. In step with a Q3 2017 study via Sucuri, a multi-platform safety corporate, WordPress continues to steer the inflamed internet sites they labored on (at 83%). That is up from 74% in 2016.

WordPress safety vulnerabilities
WordPress powers over 33% of all websites on the net, and with loads of hundreds of theme and plugin combos available in the market, it’s now not unexpected that vulnerabilities exist and are repeatedly being came upon. Alternatively, there may be a perfect group across the WordPress platform, to verify this stuff get patched ASAP. As of 2019, the WordPress security team is made up of roughly 50 (up from 25 in 2017) professionals together with lead builders and safety researchers — about part are staff of Automattic and a host paintings within the internet safety box.
WordPress Vulnerabilities
Take a look at one of the vital various kinds of WordPress safety vulnerabilities beneath.
- Backdoors
- Pharma Hacks
- Brute-force Login Attempts
- Malicious Redirects
- Cross-site Scripting (XSS)
- Denial of Service
Backdoors
The aptly named backdoor vulnerability supplies hackers with hidden passages bypassing safety encryption to achieve get entry to to WordPress internet sites by the use of extraordinary strategies – wp-Admin, SFTP, FTP, and many others. As soon as exploited, backdoors allow hackers to wreak havoc on internet hosting servers with cross-site contamination assaults – compromising more than one websites hosted at the identical server. In Q3 2017 Sucuri reported that backdoors proceed to be one of the most many post-hack movements attackers take, with 71% of the inflamed websites having some type of backdoor injection.

Malware circle of relatives distribution
Backdoors are ceaselessly encrypted to seem like official WordPress gadget recordsdata, and make their method thru to WordPress databases via exploiting weaknesses and insects in out of date variations of the platform. The TimThumb fiasco used to be a main instance of backdoor vulnerability exploiting shady scripts and out of date instrument compromising hundreds of thousands of internet sites.
Thankfully, prevention and treatment of this vulnerability is slightly easy. You’ll be able to scan your WordPress web site with equipment like SiteCheck which will simply hit upon commonplace backdoors. Two-factor authentication, blocking off IPs, limiting admin get entry to and fighting unauthorized execution of PHP recordsdata simply looks after commonplace backdoor threats, which we can cross into extra beneath. Canton Becker additionally has a perfect put up on cleansing up the backdoor mess in your WordPress installations.
Pharma Hacks
The Pharma Hack exploit is used to insert rogue code in out of date variations of WordPress internet sites and plugins, inflicting engines like google to go back commercials for pharmaceutical merchandise when a compromised website online looked for. The vulnerability is extra of a junk mail risk than conventional malware, however provides engines like google sufficient explanation why to dam the web site on accusations of distributing junk mail.
Shifting portions of a Pharma Hack come with backdoors in plugins and databases, which will also be wiped clean up following the directions from this Sucuri blog. Alternatively, the exploits are ceaselessly vicious variants of encrypted malicious injections hidden in databases and require a radical clean-up procedure to mend the vulnerability. However, you’ll simply save you Pharma Hacks via the usage of suggest WordPress internet hosting suppliers with up-to-the-minute servers and ceaselessly updating your WordPress installations, topics, and plugins. Hosts like Kinsta additionally be offering loose hack fixes.
Brute-force Login Makes an attempt
Brute-force login makes an attempt use automatic scripts to milk vulnerable passwords and achieve get entry to on your web site. Two-step authentication, limiting login attempts, tracking unauthorized logins, blocking off IPs and the usage of robust passwords are one of the vital highest and extremely efficient techniques to forestall brute-force assaults. However sadly, plenty of WordPress website online homeowners fail to accomplish those safety practices while hackers are simply ready to compromise up to 30,000 websites in a single day the usage of brute-force assaults.
Malicious Redirects
Malicious redirects create backdoors in WordPress installations the usage of FTP, SFTP, wp-admin, and different protocols and inject redirection codes into the website online. The redirects are ceaselessly positioned to your .htaccess report and different WordPress core recordsdata in encoded paperwork, directing the internet visitors to malicious websites. We can undergo many ways you’ll save you those in our WordPress safety steps beneath.
Go-Web site Scripting (XSS)
Go-Web site Scripting (XSS) is when a malicious script is injected right into a depended on website online or utility. The attacker makes use of this to ship malicious code, normally browser-side scripts, to the tip consumer with out them figuring out it. The aim is generally to grasp cookie or consultation information or possibly even rewrite HTML on a web page.
According to WordFence, Go-Web site Scripting vulnerabilities are the commonest vulnerability present in WordPress plugins via a vital margin.
Denial of Provider
In all probability probably the most unhealthy of all of them, Denial of Service (DoS) vulnerability exploits mistakes and insects within the code to crush the reminiscence of website online running programs. Hackers have compromised millions of websites and raked in millions of dollars via exploiting out of date and buggy variations of WordPress instrument with DoS assaults. Despite the fact that financially motivated cybercriminals are much less prone to goal small corporations, they generally tend to compromise out of date inclined internet sites in developing botnet chains to attack massive companies.
Even the newest variations of WordPress instrument can’t comprehensively defend against high-profile DoS attacks, however will a minimum of let you to keep away from getting stuck within the crossfire between monetary establishments and complicated cybercriminals. And don’t fail to remember about October twenty first, 2016. This used to be the day the web went down because of a DNS DDoS assault. Learn extra about why it is important to use a premium DNS provider to extend your WordPress safety.
WordPress Safety Information 2019
In step with internet live stats over 100,000 internet sites are hacked on a daily basis.  That’s why it’s so vital to take a little time and cross during the following suggestions beneath on easy methods to higher harden your WordPress safety.
That’s why it’s so vital to take a little time and cross during the following suggestions beneath on easy methods to higher harden your WordPress safety.

WordPress websites hacked on a daily basis
We can be sure to stay this put up up-to-the-minute with related knowledge as issues exchange with the WordPress platform and new vulnerabilities emerge.
- Secure WordPress Hosting
- Use Latest PHP Version
- Clever Usernames and Passwords
- Latest Versions
- Lock Down WordPress Admin
- Two-Factor Authentication
- HTTPS – SSL Certificate
- Hardening wp-config.php
- Disable XML-RPC
- Hide WordPress Version
- HTTP Security Headers
- WordPress Security Plugins
- Database Security
- Secure Connections
- File and Server Permissions
- Disable Editing in Dashboard
- Prevent Hotlinking
- Always Take WordPress Backups
- DDoS Protection
1. Make investments in Safe WordPress Website hosting
In terms of WordPress safety, there may be a lot more than simply locking down your web site, even if we’ll provide the absolute best tips about how to try this beneath. There may be internet server-level safety for which your WordPress host is accountable. We take safety very severely right here at Kinsta and maintain a large number of those problems for our purchasers.
It’s essential that you simply make a selection a number that you’ll consider with your enterprise. Or in case you are internet hosting WordPress by yourself VPS, then you wish to have to have the technical wisdom to do this stuff your self.
Server hardening is the important thing to keeping up a thoroughly-secure WordPress surroundings. It takes more than one layers of {hardware} and instrument point security features to verify the IT infrastructure internet hosting WordPress websites is in a position to protecting towards subtle threats, each bodily and digital.
Because of this, servers internet hosting WordPress will have to be up to date with the newest running gadget and (safety) instrument in addition to very well examined and scanned for vulnerabilities and malware. A excellent instance of this is when Kinsta needed to patch NGINX for OpenSSL security vulnerabilities that had been came upon.
Server-level firewalls and intrusion detection programs will have to be in position sooner than putting in WordPress at the server to stay it well-protected even right through the WordPress set up and website online building levels. Alternatively, each instrument put in at the device meant to give protection to WordPress content material will have to be appropriate with the newest database control programs to handle optimum efficiency. The server will have to even be configured to make use of safe networking and report switch encryption protocols (similar to SFTP as a substitute of FTP) to cover away delicate content material from malicious intruders.
We use Google Cloud Platform right here at Kinsta for all of our WordPress shoppers to verify secure WordPress hosting. A large good thing about that is that it’s constructed on a safety style that has been constructed upon over the process 15 years, and recently secures services and products like Gmail, Seek, and many others. Google recently employs greater than 500 full-time safety execs.
Kinsta additionally makes use of Linux packing containers (LXC), and LXD to orchestrate them, on best of Google Cloud Platform which allows us to totally isolate now not simply each and every account, however each and every separate WordPress web site. Safety is constructed into our structure from the start and this is a a lot more safe manner than introduced via different competition.
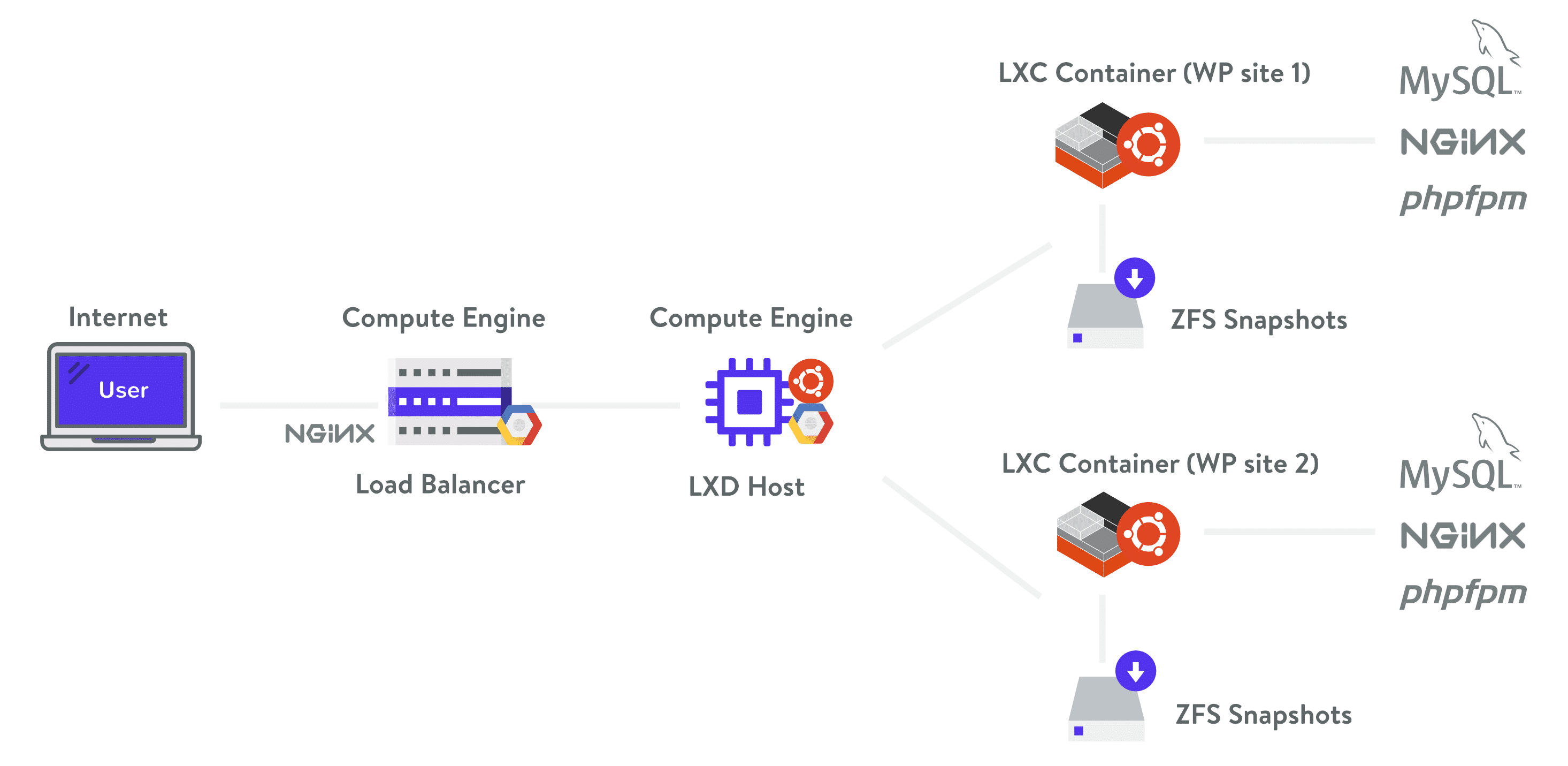
Kinsta structure
2. Use Newest PHP Model
PHP is the spine of your WordPress web site and so the usage of the newest model in your server is essential. Every primary free up of PHP is normally totally supported for two years after its free up. All the way through that point, insects and safety problems are fastened and patch frequently. As of at this time, any person working on a model beneath PHP 7.0 not has safety reinforce and are uncovered to unpatched safety vulnerabilities.
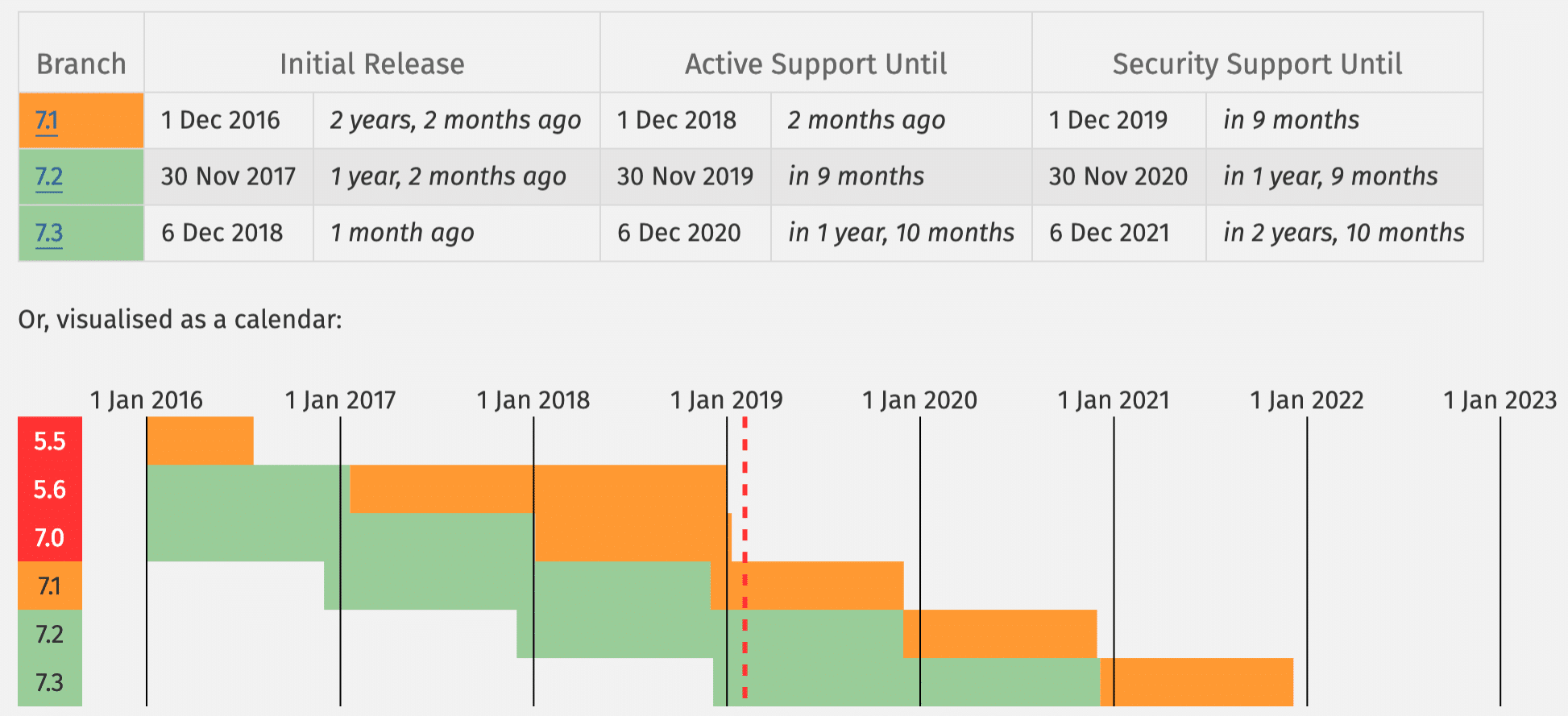
Supported PHP Variations
And bet what? In step with the respectable WordPress Stats web page, as of penning this, over 57% of WordPress customers are nonetheless on PHP 5.6 or decrease. When you mix this with PHP 7.0, a whopping 77.5% of customers are recently the usage of PHP variations this is not supported. This is horrifying!
Occasionally it does take companies and builders time to check and make sure compatibility with their code, however they’ve no excuse to run on one thing with out safety reinforce. To not point out the large efficiency have an effect on working on older variations has.

WordPress PHP model Stats
Don’t know which model of PHP you’re recently on? Maximum hosts normally come with this in a header request in your web site. A snappy method to take a look at is to run your web site thru Pingdom. Click on into the primary request and search for a X-Powered-By way of parameter. Generally this will likely display the model of PHP your internet server is recently the usage of. Alternatively, some hosts will take away this header because of safety causes. Kinsta eliminates this header via default to stay your web site protected.
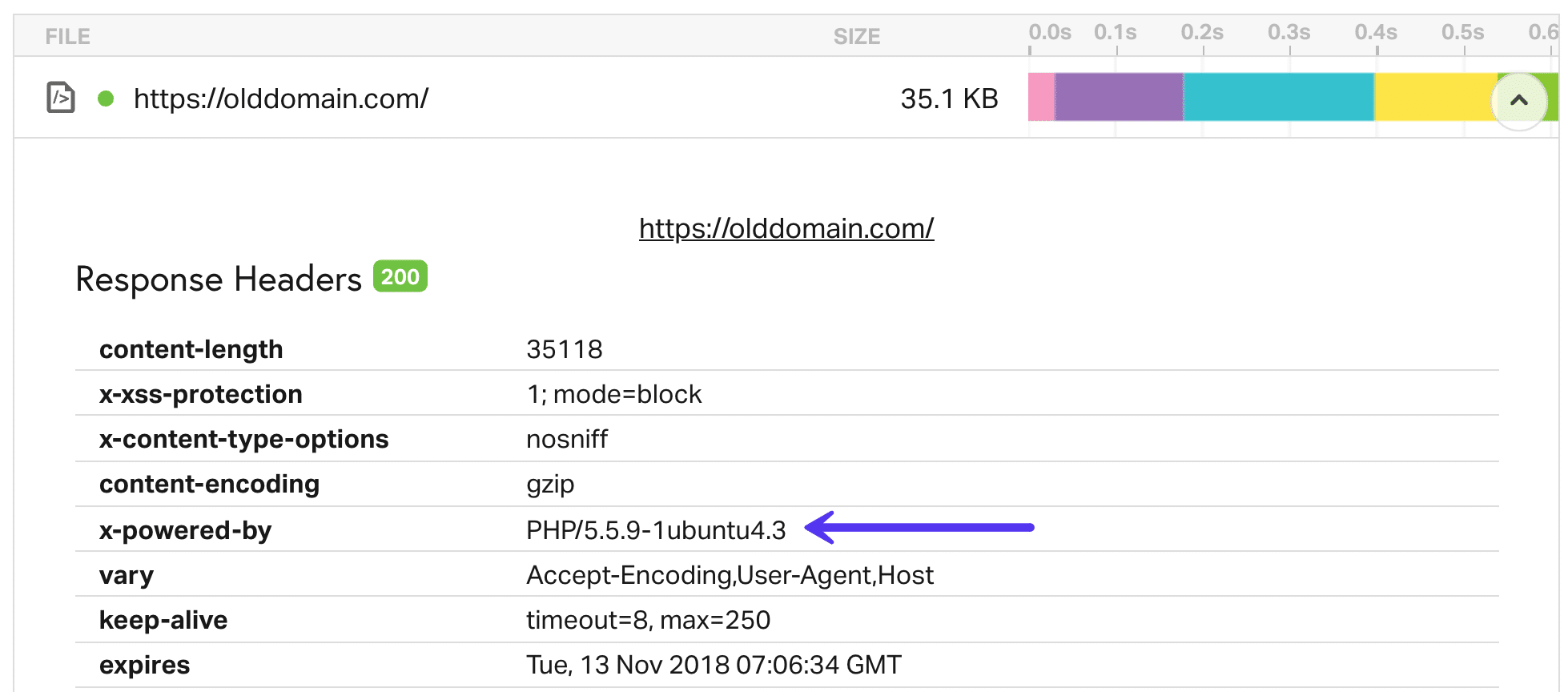
Test PHP model in Pingdom
Right here at Kinsta we best suggest the usage of strong and supported variations of PHP, together with 7.1, 7.2, and seven.3. PHP 5.6 and seven.0 will quickly be phased out. You’ll be able to even switch between PHP versions with a click on of a button from inside the MyKinsta dashboard.

Trade PHP model
If you’re on a WordPress host that makes use of cPanel, you’ll generally transfer between PHP variations via clicking into “PHP Make a selection” below the instrument class.

cPanel PHP model
3. Use Suave Usernames and Passwords
Strangely one of the most absolute best techniques to harden your WordPress safety is to easily use suave usernames and passwords. Sounds beautiful simple proper? Neatly, take a look at SplashData’s 2018 annual list of the preferred passwords stolen during the 12 months (taken care of so as of recognition).
- 123456
- password
- 123456789
- 12345678
- 12345
- 111111
- 1234567
- sunshine
- qwerty
- iloveyou
This is proper! The most well liked password is “123456”, adopted via an astonishing “password”. This is one explanation why right here at Kinsta on new WordPress installs we in truth pressure a fancy password for use to your wp-admin login (as observed beneath on our one-click set up procedure). This isn’t not obligatory.

Pressure safe WordPress password
The core WordPress wp_hash_password function makes use of the phpass password hashing framework and 8 passes of MD5-based hashing.
One of the vital absolute best safety begins from the fundamentals. Google has some nice tips about how to choose a strong password. Or you’ll use a web based software like Strong Password Generator.
Additionally it is vital to make use of other passwords for each website online. One of the best ways to retailer them is in the community in an encrypted database in your laptop. A excellent loose software for that is KeePass. When you don’t need to cross down this course there also are on-line password managers similar to 1Password or LastPass. Even if your information is hosted securely within the cloud, those are normally more secure because you aren’t the usage of the similar password throughout more than one websites. It additionally helps to keep you from the usage of sticky notes. 
And so far as your WordPress set up is going you will have to by no means use the default “admin” username. Create a singular WordPress username for the administrator account and delete the “admin” consumer if it exists. You’ll be able to do that via including a brand new consumer below “Customers” within the dashboard and assigning it the “Administrator” profile (as observed beneath).

WordPress administrator position
While you assign the brand new account the administrator position you’ll return and delete the unique “Admin” consumer. Make certain that whilst you click on on delete that you select the “Characteristic all content material to” choice and make a selection your new administrator profile. This may increasingly assign the individual because the writer of the ones posts.

Characteristic all content material to admin
You’ll be able to additionally rename your present admin username manually in phpMyAdmin with the next command. You’ll want to backup your database sooner than enhancing tables.
UPDATE wp_users SET user_login = 'newcomplexadminuser' WHERE user_login = 'admin';4. At all times Use the Newest Model of WordPress, Plugins, and Issues
Some other essential method to harden your WordPress safety is to at all times stay it up-to-the-minute. This entails WordPress core, plugins, and topics (each the ones from the WordPress repository and top rate). Those are up to date for a explanation why, and a large number of instances those come with safety improvements and insect fixes. We propose you to learn our in-depth information on how WordPress automatic updates paintings.

Stay WordPress up-to-the-minute
Sadly, hundreds of thousands of companies available in the market working out of date variations of WordPress instrument and plugins, and nonetheless consider they’re at the proper trail of commercial good fortune. They cite causes for now not updating similar to “their web site will ruin” or “core changes will likely be long past” or “plugin X received’t paintings” or “they only don’t want the brand new capability”.
Actually, internet sites ruin most commonly on account of insects in older WordPress variations. Core changes are by no means beneficial via the WordPress group and skilled builders who perceive the hazards concerned. And WordPress updates most commonly come with must-have safety patches together with the added capability required to run the newest plugins.
Do you know that it’s been reported that plugin vulnerabilities represent 55.9% of the recognized access issues for hackers? That’s what WordFence present in a find out about the place they interviewed over 1,000 WordPress web site homeowners that have been sufferers of assaults. By way of updating your plugins you’ll higher be sure that you aren’t this sort of sufferers.
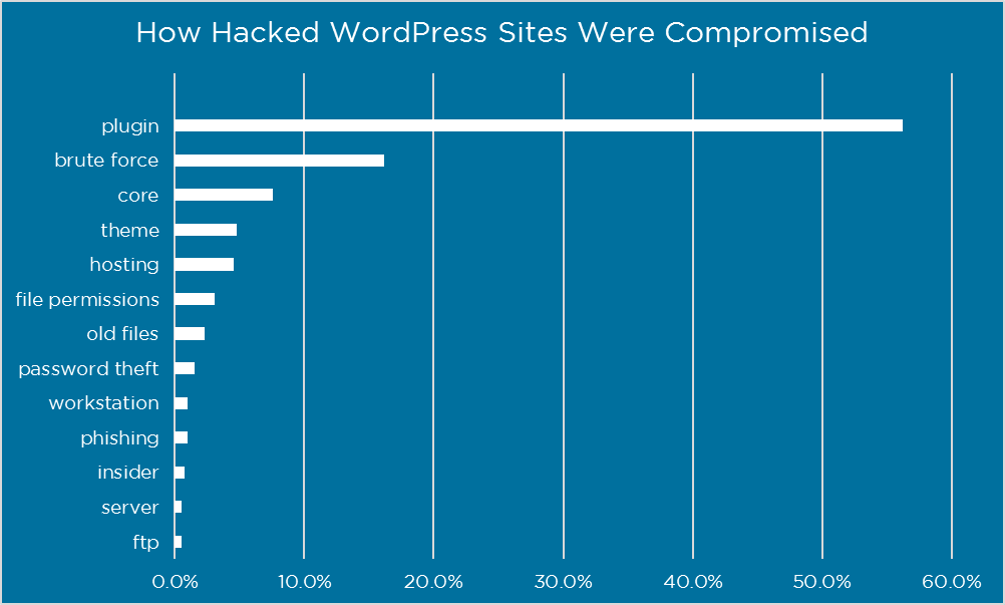
Hacked WordPress websites
Additionally it is beneficial that you simply best set up depended on plugins. The “featured” and “well-liked” classes within the WordPress repository generally is a excellent position to begin. Or obtain it at once from the developer’s website online. We strongly discourage any use of nulled WordPress plugins and themes. First off, you by no means know what the changed code may comprise. This will simply finally end up to your web site getting hacked. Now not paying for top rate WordPress plugins additionally doesn’t assist the group develop as an entire. We wish to reinforce builders.
You’ll be able to use a web based software like VirusTotal to scan a plugin or theme’s recordsdata to look if it detects any form of malware.
VirusTotal
Learn how to Replace WordPress Core
There are a pair simple techniques to replace your WordPress set up. If you’re a Kinsta buyer we supplied automatic backups with a one-click repair choice. This manner you’ll check new variations of WordPress and plugins with no need to fret about it breaking the rest. Or it is advisable additionally first check in our staging environment.
To replace WordPress core you’ll click on into “Updates” to your WordPress dashboard and click on at the “Replace Now” button.

Replace WordPress core
You’ll be able to additionally replace WordPress manually via downloading the latest version and importing it by the use of SFTP.
Observe the stairs beneath to update your existing installation:
- Delete the previous
wp-includesandwp-admindirectories. - Add the brand new
wp-includesandwp-admindirectories. - Add the person recordsdata from the brand new
wp-contentfolder on your presentwp-contentfolder, overwriting present recordsdata. Do NOT delete your presentwp-contentfolder. Do NOT delete any recordsdata or folders to your presentwp-contentlisting (excluding for the only being overwritten via new recordsdata). - Add all new free recordsdata from the basis listing of the brand new model on your present WordPress root listing.
Learn how to Replace WordPress Plugins
Updating your WordPress plugins is an excessively equivalent procedure to updating WordPress core. Click on into “Updates” to your WordPress dashboard, make a selection the plugins you need to replace, and click on on “Replace Plugins.”

Replace WordPress plugins
Likewise, you’ll additionally replace a plugin manually. Merely grasp the newest model from the plugin developer or WordPress repository and add it by the use of FTP, overwriting the prevailing plugin inside the /wp-content/plugins listing.
It’s additionally vital to notice that builders don’t at all times stay their plugins up-to-the-minute. The group over at WP Loop did a perfect little research of simply what number of WordPress plugins within the repository aren’t up-to-the-minute with the present WordPress core. According to their research just about 50% of the plugins within the repository have now not been up to date in over 2 years.
This doesn’t imply the plugin received’t paintings with the present model of WordPress, nevertheless it’s beneficial that you select plugins which might be actively up to date. Old-fashioned plugins are much more likely to comprise safety vulnerabilities.

img src: WP Loop
Use your absolute best judgment on the subject of plugins. Take a look at the “Ultimate Up to date” date and what number of rankings a plugin has. As observed within the instance beneath, this one is old-fashioned and has dangerous evaluations so we’d in all probability suggest staying clear of it. WordPress additionally has a caution on the best of maximum plugins that haven’t been up to date shortly.

Previous WordPress plugin with dangerous rankings
There also are a large number of assets available in the market that will help you keep on best of the newest WordPress safety updates and vulnerabilities. See a few of them beneath:
- WP Security Bloggers: A fantastic aggregated useful resource of 20+ safety feeds.
- WPScan Vulnerability Database: Catalogs over 10,000 WordPress Core, Plugin and Theme vulnerabilities.
- ThreatPress: Day-to-day up to date database of WordPress plugins, topics, and WordPress core vulnerabilities.
- Official WordPress Security Archive

WordPress safety archive
5. Lock Down Your WordPress Admin
Occasionally the preferred means of WordPress safety via obscurity is accurately efficient for a mean on-line industry and WordPress web site. If you’re making it more difficult for hackers to search out sure backdoors then you’re much less prone to be attacked. Locking down your WordPress admin space and login is a great way to enhance your safety. Two nice techniques to do that is first via converting your default wp-admin login URL and in addition proscribing login makes an attempt.
Learn how to Trade Your WordPress Login URL
By way of default your WordPress web site’s login URL is area.com/wp-admin. Some of the issues of that is that the entire bots, hackers, and scripts available in the market additionally know this. By way of converting the URL you’ll make your self much less of a goal and higher give protection to your self towards brute pressure assaults. This isn’t a repair all resolution, it’s merely one little trick that may certainly assist give protection to you.
To change your WordPress login URL we advise the usage of the loose WPS Hide login plugin or the top rate Perfmatters plugin. Either one of the plugins have a easy enter box. Make sure that you select one thing distinctive that received’t already be on a listing {that a} bot or script may try to scan.
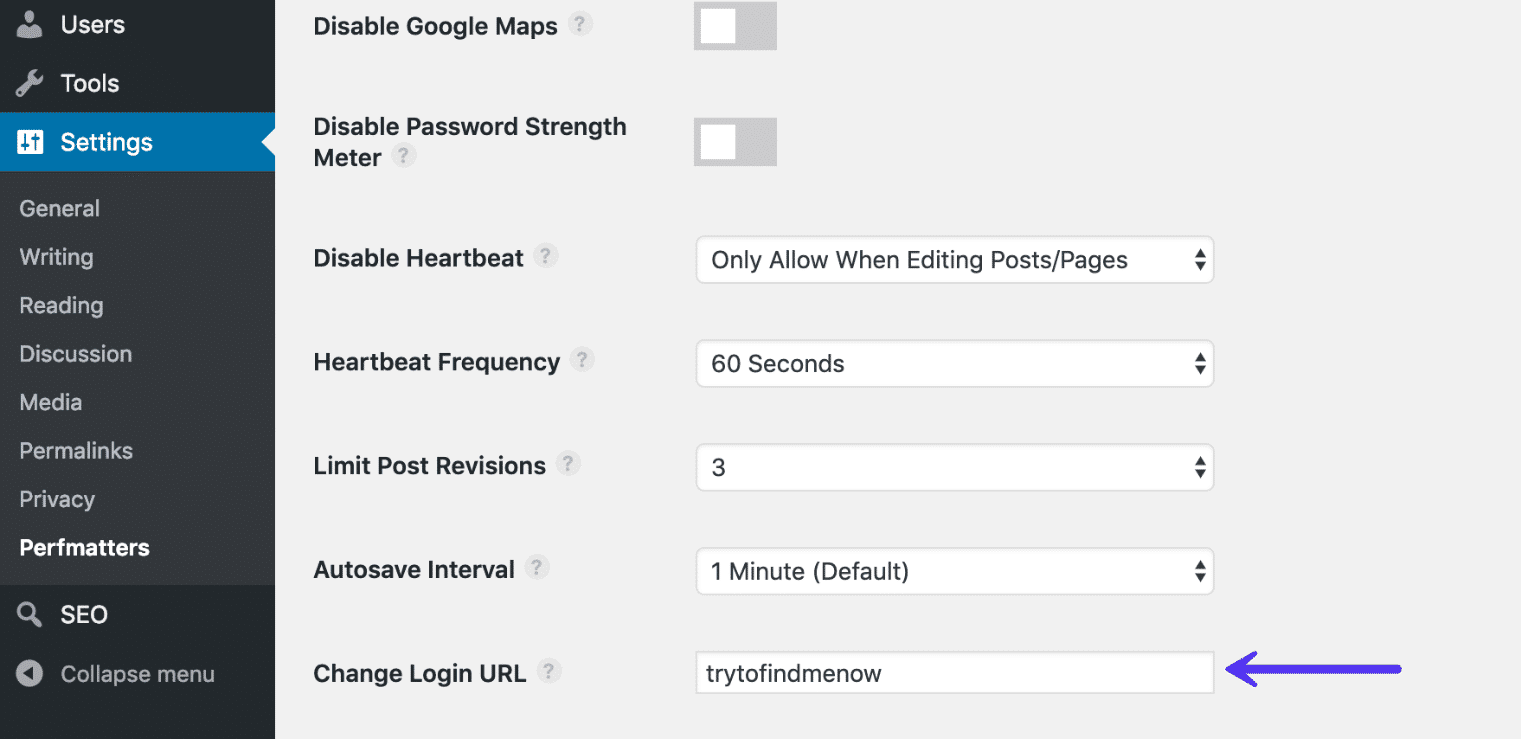
Conceal WordPress login URL with Perfmatters
Learn how to Prohibit Login Makes an attempt
Whilst the above resolution of adjusting your admin login URL can assist lower the vast majority of the dangerous login makes an attempt, hanging a prohibit in position can be very efficient. The loose Cerber Limit Login Attempts plugin is a good way to simply setup lockout intervals, login makes an attempt, and IP whitelists and blacklists.
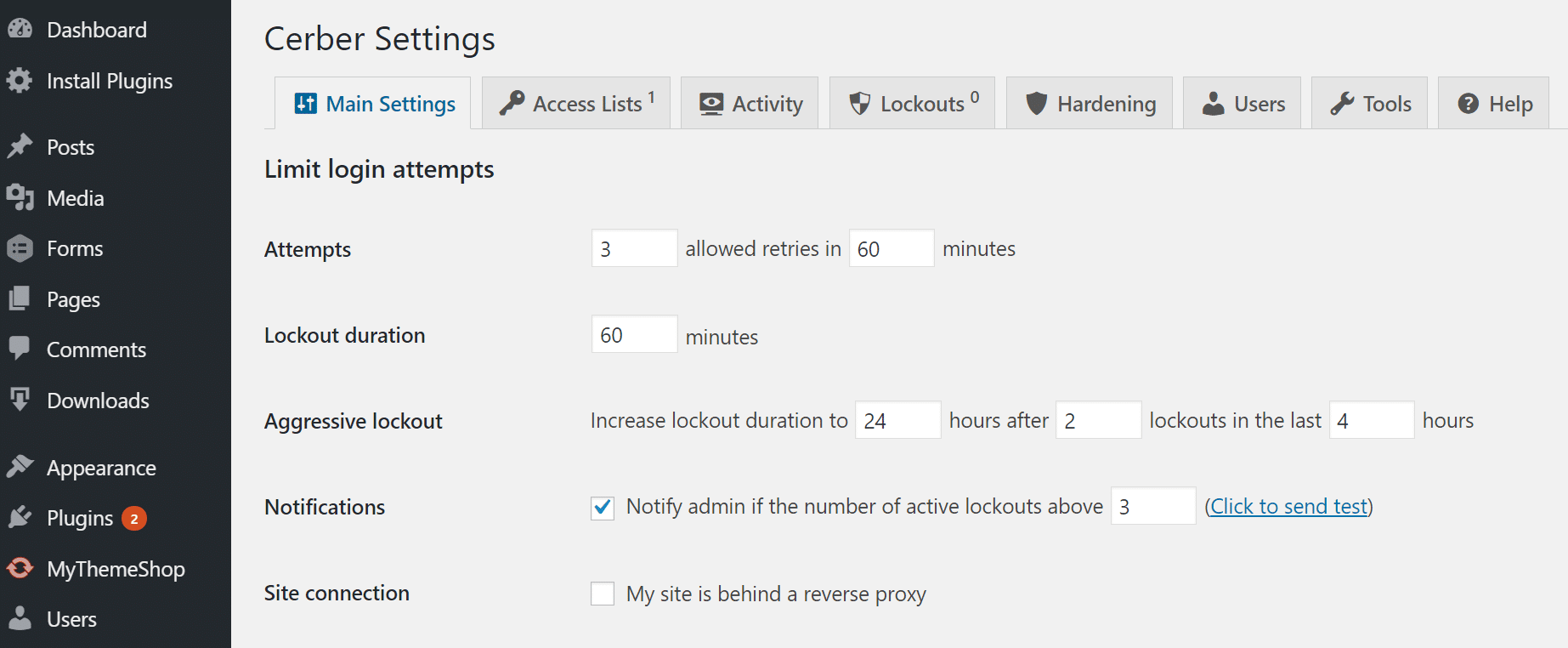
Prohibit login makes an attempt in WordPress
If you’re searching for a extra easy WordPress safety resolution, any other nice choice is the loose Login Lockdown plugin. Login LockDown data the IP deal with and timestamp of each failed login try. If greater than a definite selection of makes an attempt are detected inside a brief time period from the similar IP vary, then the login serve as is disabled for all requests from that vary. And it’s utterly appropriate with the WPS Conceal login plugin we discussed above.
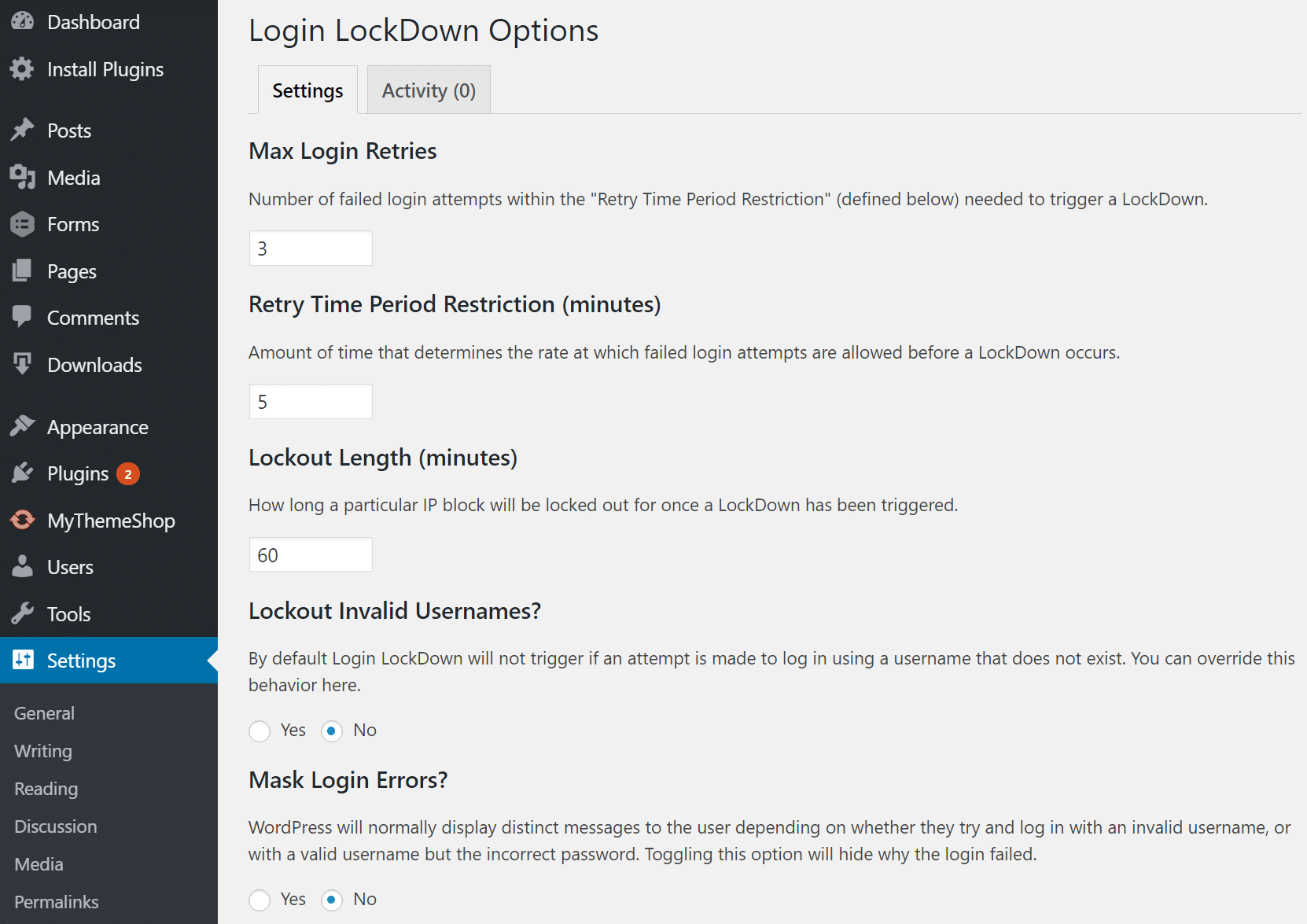
Lockdown WordPress
Learn how to Upload Fundamental HTTP Authentication (htpasswd coverage)
In a different way to fasten down your admin is so as to add HTTP authentication. This calls for a username and password sooner than having the ability to even get entry to the WordPress login web page. Observe: This normally shouldn’t be used on eCommerce websites or club websites. However it may be an excessively efficient method to save you bots from hitting your web site.
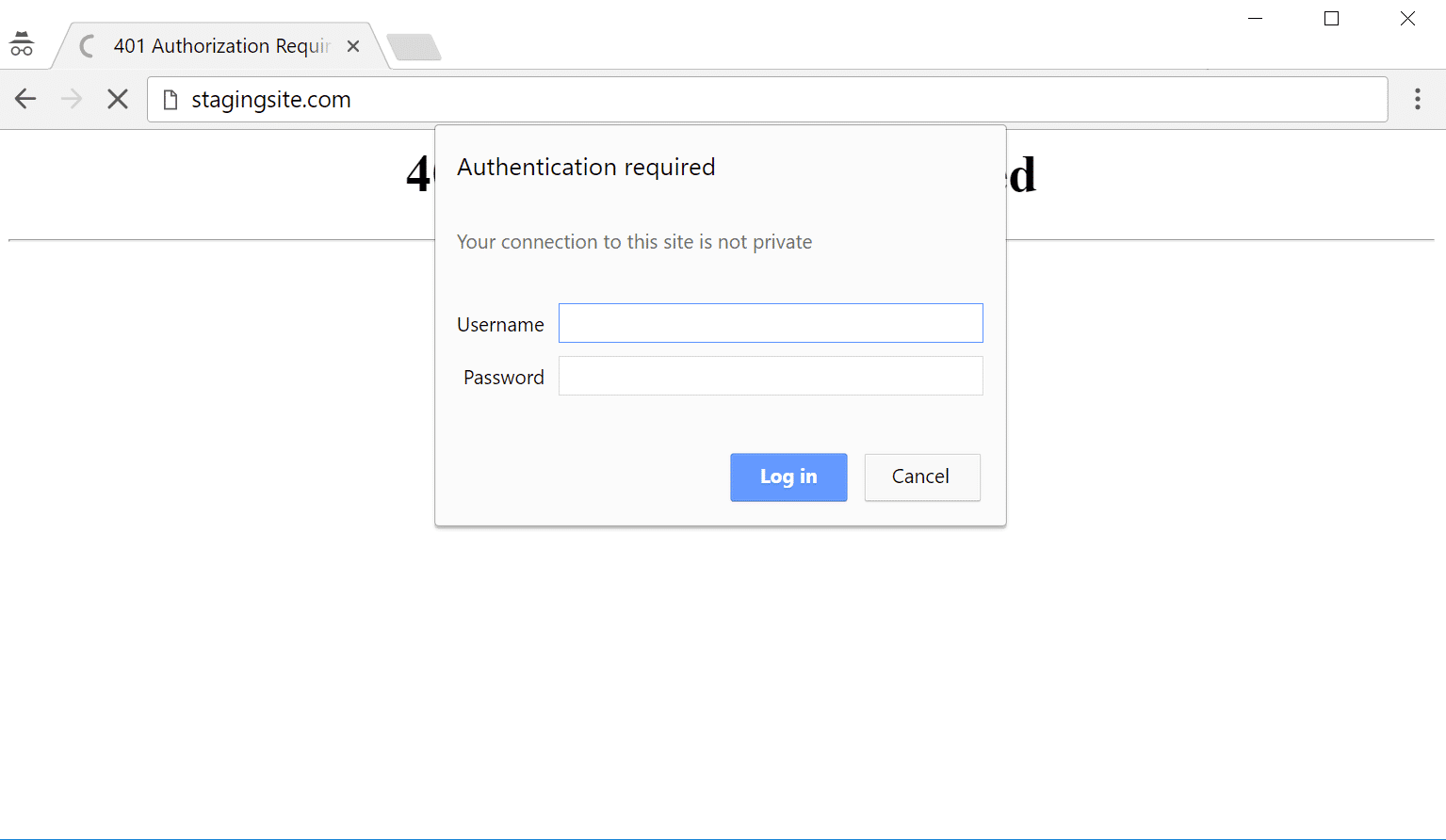
Fundamental HTTP authentication
Apache
If you’re the usage of a cPanel host, you’ll allow password secure directories from their keep watch over panel. To set it up manually, you’ll first wish to create a .htpasswd report. You’ll be able to use this at hand generator tool. Then add the report to a listing below your wp-admin folder, similar to:
house/consumer/.htpasswds/public_html/wp-admin/htpasswd/Then create a .htaccess report with the next code and add it on your /wp-admin/ listing. Be sure to replace the listing trail and username.
AuthName "Admins Most effective"
AuthUserFile /house/yourdirectory/.htpasswds/public_html/wp-admin/htpasswd
AuthType fundamental
require consumer yourusernameThe only caveat to doing it this fashion is that it’s going to ruin AJAX (admin-ajax) at the front-end of your web site. That is required via some third-party plugins. Subsequently you’ll additionally wish to add the following code to the above .htaccess report.
Order permit,deny
Permit from all
Fulfill any
Nginx
If you’re working Nginx, you’ll additionally limit get entry to with HTTP fundamental authentication. Take a look at this tutorial. If you’re a Kinsta shopper, achieve out to our reinforce group and we will be able to simply upload this for you.
Lockdown a URL trail
When you’re the usage of a internet utility firewall (WAF) similar to Cloudflare or Sucuri, additionally they have techniques to lockdown a URL trail. Necessarily you’ll arrange a rule in order that best your IP deal with is in a position to get entry to your WordPress admin login URL. Once more, this normally shouldn’t be used on eCommerce websites or club websites as additionally they depend on having access to your web site’s back-end.
- Cloudflare has a lockdown URL feature of their Professional and better accounts. You’ll be able to arrange a rule for any URL or trail.
- Sucuri has a blacklist URL path feature. That you must then whitelist your personal IP.
6. Take Benefit of Two-Issue Authentication
And naturally, we will be able to’t fail to remember two-factor authentication! Regardless of how safe your password is there may be at all times a possibility of anyone finding it. Two-factor authentication comes to a two-step procedure wherein you wish to have now not best your password to login however a 2d manner. It’s normally a textual content (SMS), telephone name, or time-based one-time password (TOTP). Most often, that is 100% efficient in fighting brute pressure assaults on your WordPress web site. Why? As a result of it’s virtually inconceivable that the attacker can have each your password and your mobile phone.
There are in point of fact two portions on the subject of two-factor authentication. The primary is your account and or dashboard that you’ve got along with your internet internet hosting supplier. If anyone will get get entry to to this they might exchange your passwords, delete your internet sites, exchange DNS data, and all forms of terrible issues. We right here at Kinsta partnered up with Authy and feature two-factor authentication to be had to your MyKinsta dashboard.
The second one a part of two-factor authentication relates to your precise WordPress set up. For this there are a pair plugins we advise:
Many of those have their very own Authenticator Apps you’ll in your telephone:
- Android Duo Mobile App
- iPhone Duo Mobile App
- Android Google Authenticator App
- iPhone Google Authenticator App
After putting in and configuring one of the most above plugins, you’ll normally have an extra box in your WordPress login web page to go into your safety code. Or, with the Duo plugin, you first log in along with your credentials and are then required to make a choice an authentication manner, similar to Duo Push, name, or passcode.
This technique can simply be mixed with converting your default login URL, which we went over previous. So now not best is your WordPress login URL one thing best you already know, nevertheless it now calls for additional authentication to get in. 
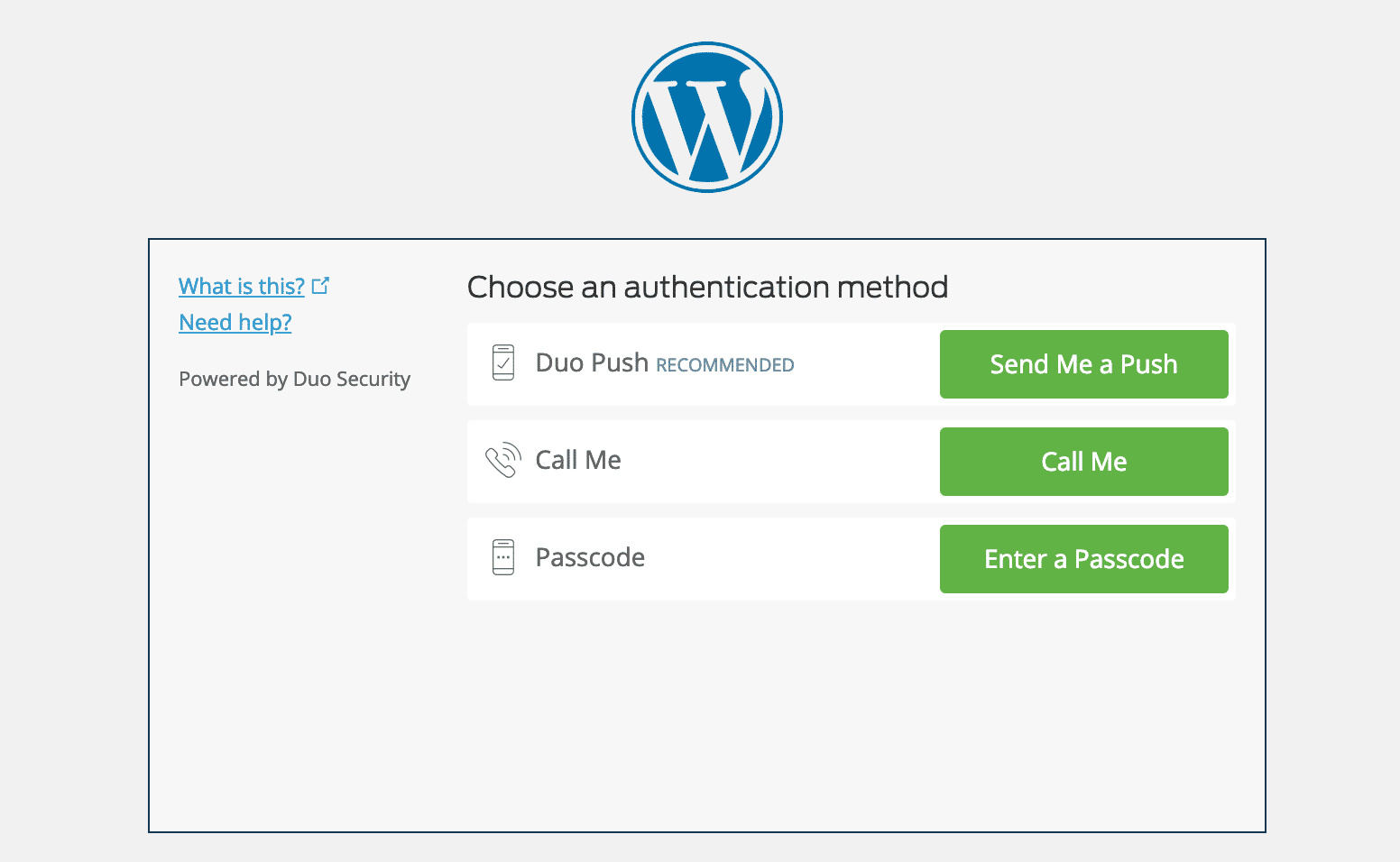
WordPress two-factor authenticator web page
So be sure to benefit from two-factor authentication, it may be a very easy method to enhance your WordPress safety.
7. Use HTTPS for Encrypted Connections – SSL Certificates
Some of the overpassed techniques to harden your WordPress safety is to install an SSL certificate and run your web site over HTTPS. HTTPS (Hyper Textual content Switch Protocol Safe) is a mechanism that permits your browser or internet utility to safely connect to a website online. A large false impression is that in case you aren’t accepting bank cards that you simply don’t want SSL.
Neatly, allow us to give an explanation for a couple of explanation why HTTPS is vital past simply eCommerce. Many hosts, together with Kinsta, be offering loose SSL certificate with Let’s Encrypt.

HTTPS encrypted connections
1. Safety
After all, the largest explanation why for HTTPS is the added safety, and sure this does pertain strongly to eCommerce websites. Alternatively, how vital is your login knowledge? For the ones of you working multi-author WordPress internet sites, in case you are working over HTTP, each time an individual logs in, that knowledge is being handed to the server in simple textual content. HTTPS is actually essential in keeping up a safe connection between a website online and a browser. This manner you’ll higher save you hackers and or a center guy from getting access to your website online.
So whether or not you could have a weblog, information web site, company, and many others., they are able to all can have the benefit of HTTPS as this guarantees not anything ever passes in simple textual content.
2. search engine optimization
Google has formally mentioned that HTTPS is a ranking factor. Whilst it is just a small rating aspect, maximum of you can most definitely take any benefit you’ll get in SERPs to overcome your competition.
3. Agree with and Credibility
In step with a survey from GlobalSign, 28.9% of holiday makers search for the golf green deal with bar of their browser. And 77% of them are nervous about their information being intercepted or misused on-line. By way of seeing that inexperienced padlock, shoppers will immediately have extra peace of thoughts figuring out that their information is extra safe.
4. Referral Information
A lot of other people don’t notice is that HTTPS to HTTP referral information is blocked in Google Analytics. So what occurs to the information? Neatly, maximum of it is only lumped in conjunction with the “direct visitors” segment. If anyone goes from HTTP to HTTPS the referrer continues to be handed.
5. Chrome Warnings
As of July 24th, 2018, variations of Chrome 68 and better began marking all non-HTTPS websites as “Now not Safe.” Without reference to whether or not they accumulate information or now not. For this reason HTTPS is extra vital than ever!
That is particularly vital in case your website online will get a majority of its visitors from Chrome. You’ll be able to glance in Google Analytics below the Target audience segment in Browser & OS so see the share of visitors your WordPress web site will get from Google Chrome. Google is making it much more transparent to guests that your WordPress website online is probably not working on a secured connection.

Chrome now not a safe website online
6. Efficiency
As a result of a protocol known as HTTP/2, a large number of instances, the ones working correctly optimized websites over HTTPS may even see velocity enhancements. HTTP/2 calls for HTTPS on account of browser reinforce. The advance in efficiency is because of quite a lot of causes similar to HTTP/2 having the ability to reinforce higher multiplexing, parallelism, HPACK compression with Huffman encoding, the ALPN extension, and server push. And with TLS 1.3, HTTPS connections are even quicker.
Re-thinking HTTPS now? Take a look at our in-depth WordPress HTTPS migration guide to get you up and going.
To put into effect a safe, encrypted connection between you and the server when logging into and administering your web site, upload the next line on your wp-config.php report:
outline('FORCE_SSL_ADMIN', true);
8. Harden Your wp-config.php report
Your wp-config.php report is like the guts and soul of your WordPress set up. It’s via a long way crucial report in your web site on the subject of WordPress safety. It incorporates your database login knowledge and safety keys which maintain the encryption of data in cookies. Beneath are a pair issues you’ll do to raised give protection to this vital report.
1. Transfer wp-config.php
By way of default, your wp-config.php report is living within the root listing of your WordPress set up (your /public HTML folder). However you’ll transfer this to a non-www obtainable listing. Aaron Adams wrote up a great explanation of why that is really helpful.
To transport your wp-config.php report merely reproduction the whole lot out of it into a distinct report. Then to your wp-config.php report you’ll position the next snippet to easily come with your different report. Observe: the listing trail could be other in response to your internet host and setup. Generally even though it’s merely one listing above.
Observe: this received’t paintings for Kinsta purchasers and can ruin capability on our platform. It's because our open_basedir restrictions don’t permit execution of PHP above the
~/publiclisting for safety causes. The excellent news is we maintain this for you! We do successfully the similar factor via blocking off get entry to towp-login.phpinside the~/publiclisting. Our default Nginx config features a rule that may go back a 403 for any tried get entry to ofwp-config.php.2. Replace WordPress Safety Keys
WordPress safety keys are a collection of random variables that reinforce encryption of data saved within the consumer’s cookies. Since WordPress 2.7 there were 4 other keys:
AUTH_KEY,SECURE_AUTH_KEY,LOGGED_IN_KEY, andNONCE_KEY.Whilst you set up WordPress those are generated randomly for you. Alternatively, when you've got long past thru more than one migrations or bought a web site from anyone else, it may be excellent to create recent WordPress keys.
WordPress in truth has a loose software which you'll use to generate random keys. You'll be able to replace your present keys which can be saved to your wp-config.php file.

WordPress safety keys
Learn extra about WordPress security keys.
3. Trade Permissions
Generally recordsdata within the root listing of a WordPress web site will likely be set to 644, this means that that recordsdata are readable and writeable via the landlord of the report and readable via customers within the staff proprietor of that report and readable via everybody else. In step with the WordPress documentation, the permissions at the
wp-config.phpreport will have to be set to 440 or 400 to forestall different customers at the server from studying it. You'll be able to simply exchange this along with your FTP shopper.
wp-config.php permissions
On some internet hosting platforms, the permissions may wish to be other for the reason that consumer working the internet server doesn’t have permission to put in writing recordsdata. When you aren’t positive about this, take a look at along with your internet hosting supplier.
9. Disable XML-RPC
Within the past years XML-RPC has turn out to be an increasingly large goal for brute pressure assaults. As Sucuri discussed, one of the most hidden options of XML-RPC is that you'll use the gadget.multicall option to execute more than one strategies within a unmarried request. That’s very helpful because it permit utility to move more than one instructions inside one HTTP request. However what additionally occurs is that it's used for malicious intent.
Suffering with downtime and WordPress issues? Kinsta is the internet hosting resolution designed to avoid wasting you time! Check out our featuresThere are a couple of WordPress plugins like Jetpack that depend on XML-RPC, however a majority of other people available in the market received’t want this and it may be really helpful to easily disable get entry to to it. Now not positive if XML-RPC is recently working in your website online? Danilo Ercoli, from the Automattic group, wrote just a little software known as the XML-RPC Validator. You'll be able to run your WordPress web site thru that to look if it has XML-RPC enabled. If it isn’t, you'll see a failure message similar to proven within the symbol beneath at the Kinsta weblog.

WordPress XML-RPC validator
To disable this utterly you'll set up the loose Disable XML-RPC plugin. Or you'll disable it with the top rate perfmatters plugin, which additionally incorporates internet efficiency enhancements.
If you're a buyer right here at Kinsta this isn't wanted as a result of when an assault thru XML-RPC is detected just a little snippet of code is added into the NGINX config report to prevent them of their tracks – generating a 403 error.
location ~* ^/xmlrpc.php$ { go back 403; }10. Conceal Your WordPress Model
Hiding your WordPress model touches once more relating to WordPress safety via obscurity. The fewer other folks learn about your WordPress web site configuration the simpler. In the event that they see you're working an old-fashioned WordPress set up, this can be a welcome signal to intruders. By way of default, the WordPress model presentations up within the header of your web site’s supply code. Once more, we advise merely ensuring your WordPress set up is at all times up-to-the-minute so that you don’t have to fret about this.
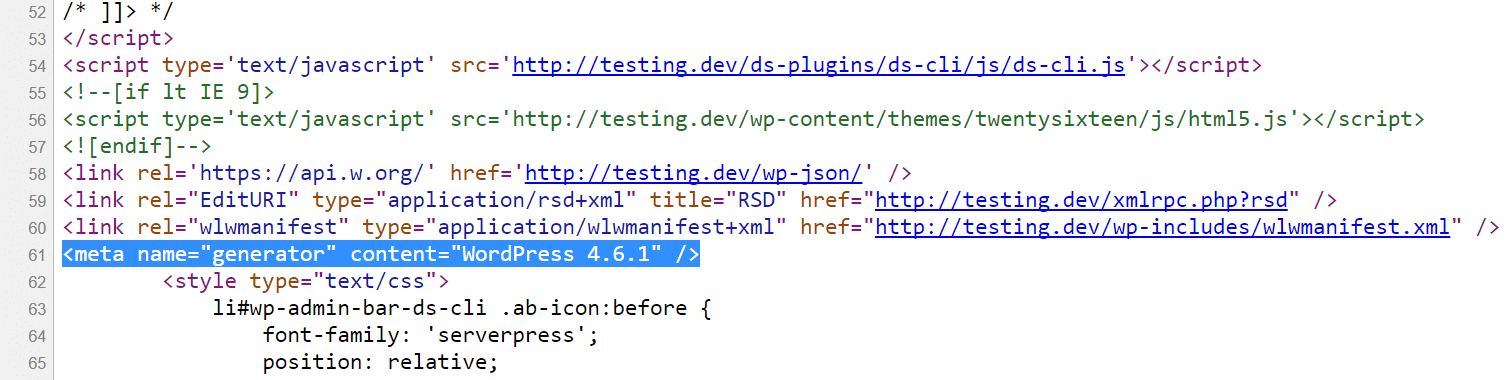
WordPress model in supply code
You'll be able to use the next code to take away this. Merely upload it on your WordPress theme’s
purposes.phpreport.Necessary! Enhancing the supply code of a WordPress theme may just ruin your web site if now not carried out accurately. When you don't seem to be at ease doing this, please take a look at with a developer first.serve as wp_version_remove_version() { go back ''; } add_filter('the_generator', 'wp_version_remove_version');That you must additionally use a top rate plugin like perfmatters (advanced via a group member at Kinsta), which lets you conceal the WordPress model with one-click, together with different optimizations to your WordPress web site.

Conceal WordPress model with Perfmatters
Some other position the place the WordPress model presentations up is within the default
readme.htmlreport (as proven beneath) this is integrated in each WordPress model. It's positioned within the root of your set up,area.com/readme.html. You'll be able to safely delete this report by the use of FTP.
WordPress model in readme report
When you’re working WordPress 5.0 or upper that is not acceptable because the model quantity is not integrated within the report.
11. Upload Newest HTTP Safety Headers
Some other step you'll take to harden your WordPress safety is to benefit from HTTP safety headers. Those are generally configured on the internet server point and inform the browser easy methods to behave when dealing with your web site’s content material. There are a large number of other HTTP safety headers, however beneath are normally crucial ones.
- Content-Security Policy
- X-XSS-Coverage
- Strict-Transport-Security
- X-Body-Choices
- Public-Key-Pins
- X-Content material-Sort
KeyCDN has a perfect in-depth put up if you wish to learn extra about HTTP security headers.
You'll be able to take a look at which headers are recently working in your WordPress web site via launching Chrome devtools and taking a look on the header in your web site’s preliminary reaction. Beneath is an instance on kinsta.com. You'll be able to see we're using the strict-transport-security, x-content-type, and x-frame-options headers.

HTTP safety headers
You'll be able to additionally scan your WordPress website online with the loose securityheaders.io software via Scott Helme. This may increasingly display you which ones HTTP safety headers you presently have in your web site. When you aren’t positive easy methods to put in force them you'll at all times ask your host if they are able to assist.

HTTP safety headers scan
Observe: Additionally it is vital to take into account that whilst you put in force HTTP safety headers how it would have an effect on your WordPress subdomains. For instance, in case you upload the Content material Safety Coverage header and limit get entry to via domain names, that you wish to have so as to add your personal subdomains as nicely.
12. Use WordPress Safety Plugins
And naturally, we need to give some WordPress safety plugins some mentions. There are a large number of nice builders and firms available in the market which give nice answers to assist higher give protection to your WordPress web site. Listed below are a few them.
Kinsta has {hardware} firewalls, energetic and passive safety, by-the-minute uptime exams and ratings of alternative complex options to forestall attackers from getting access to your information. If, in spite of our absolute best efforts, your web site is compromised we’ll repair it free of charge.
Listed below are some conventional options and makes use of of the plugins above:
- Generate and pressure robust passwords when developing consumer profiles
- Pressure passwords to run out and be reset frequently
- Consumer motion logging
- Simple updates of WordPress safety keys
- Malware Scanning
- Two-factor authentication
- reCAPTCHAs
- WordPress safety firewalls
- IP whitelisting
- IP blacklisting
- Record changelogs
- Track DNS adjustments
- Block malicious networks
- View WHOIS knowledge on guests
A vital characteristic that many safety plugins come with a checksum software. What this implies is they investigate cross-check your WordPress set up and search for changes at the core recordsdata as supplied via WordPress.org (by the use of the API). Any adjustments or changes to those recordsdata may just point out a hack. You'll be able to additionally use WP-CLI to run your own checksum.
Some other nice plugin the merits an honorable point out is the WP Security Audit Log plugin. That is superior for the ones of you running on WP multisite or just multi-author websites. It is helping be certain consumer productiveness and shall we directors see the whole lot this is being modified; similar to logins, password adjustments, theme adjustments, widget adjustments, new put up creations, WordPress updates, and many others.
It’s an entire WordPress activity log resolution. As of penning this the WP Safety Audit Log plugin has over 80,000+ energetic installs with a 4.7 out of 5-star score.

Safety audit log viewer
It additionally has further top rate add-ons similar to e mail notifications, consumer classes control, seek, and stories. Take a look at those further WordPress security plugins that may assist lock out the dangerous guys.
13. Harden Database Safety
There are a pair techniques to raised the safety in your WordPress database. The primary is to use a suave database identify. In case your web site is known as volleyball methods, via default your WordPress database is in all probability named wp_volleyballtricks. By way of converting your database identify to a few extra difficult to understand it is helping give protection to your web site via making it harder for hackers to spot and get entry to your database main points. The oldsters over at WPMUDEV wrote up a perfect little instructional on how to change your database name on present installs.
A 2d advice is to make use of a distinct database desk prefix. By way of default WordPress makes use of wp_. Converting this to one thing like 39xw_ will also be a lot more safe. Whilst you set up WordPress it asks for a desk prefix (as observed beneath). There also are techniques to change the WordPress table prefix on present installations.

WordPress desk prefix – img src: jatinarora
14. At all times Use Safe Connections
We will be able to’t tension sufficient how vital it's to make use of safe connections! Make certain that your WordPress host it taking precautions similar to providing SFTP or SSH. SFTP or Safe Record Switch Protocol (often referred to as SSH report switch protocol), is a community protocol used for report transfers. This can be a extra safe manner vs usual FTP.
We best support SFTP connections at Kinsta to verify your information stays protected and encrypted. Maximum WordPress hosts additionally normally use port 22 for SFTP. We take this a step additional right here at Kinsta and each web site has a randomized port which will also be discovered to your MyKinsta dashboard.
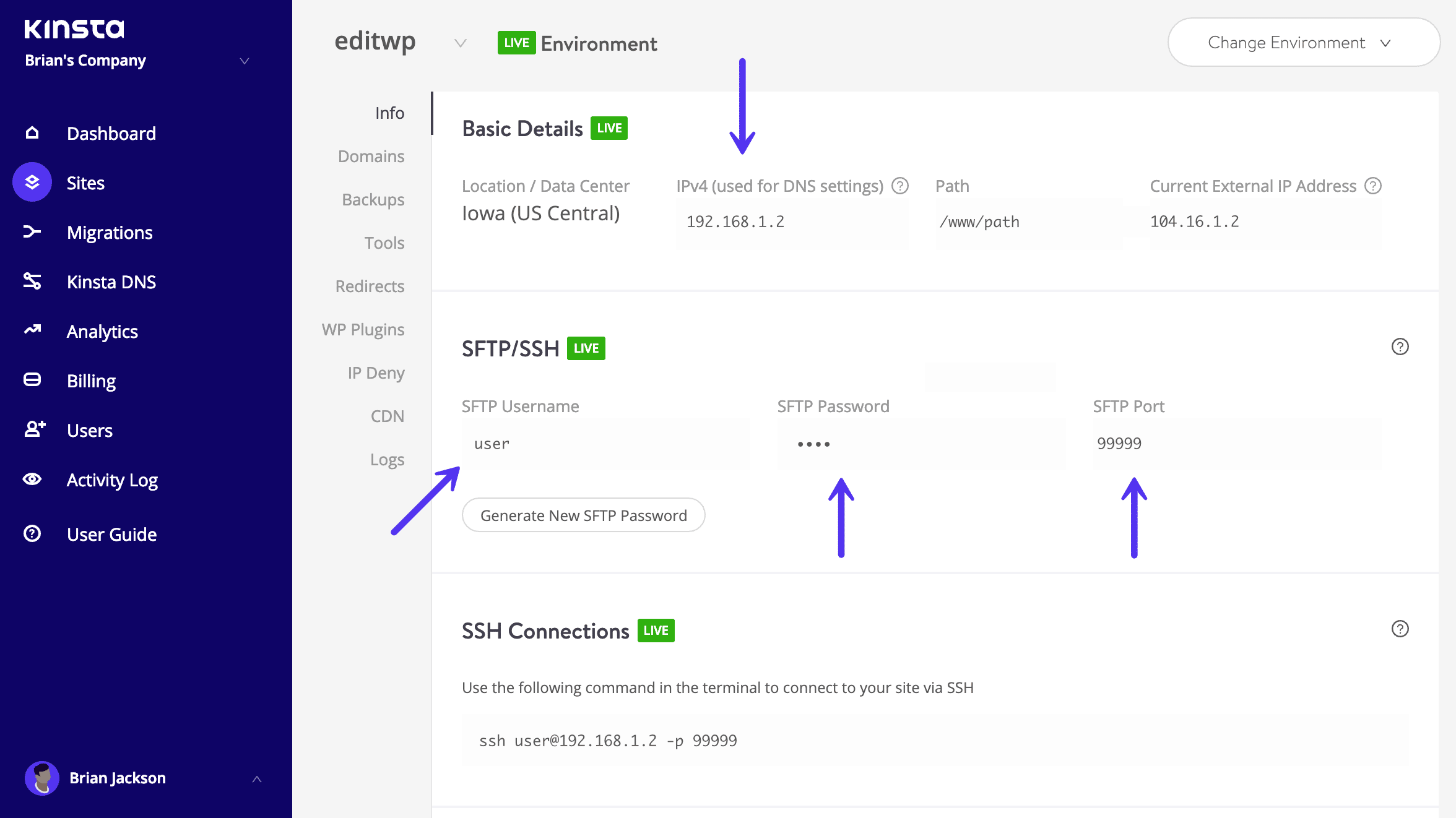
SFTP knowledge
It’s additionally vital to be sure that your house router is setup accurately. If anyone hacks your house community they might achieve get entry to to all forms of knowledge, together with perhaps the place your vital details about your WordPress web site(s) is saved. Listed below are some easy guidelines:
- Don’t allow faraway control (VPN). Conventional customers by no means use this option and via maintaining it off you'll stay from exposing your community to the outdoor international.
- Routers via default use IPs within the vary similar to 192.168.1.1. Use a distinct vary, similar to 10.9.8.7.
- Allow the easiest point of encryption in your Wifi.
- IP white-list your Wifi in order that best other people with the password and sure IP can get entry to it.
- Stay the firmware in your router up-to-the-minute.
And at all times watch out when logging into your WordPress web site in public places. Bear in mind, Starbucks isn't a safe community! Take precautions similar to verifying the community SSID sooner than you click on attach. You'll be able to additionally use a third social gathering VPN provider similar to ExpressVPN to encrypt your web visitors and conceal your IP deal with from hackers.
15. Test Record and Server Permissions
Record permissions on each your set up and internet server are the most important to beefing up your WordPress safety. If permissions are too free, anyone may just simply achieve get entry to on your web site and wreak havoc. Then again, in case your permissions are too strict this might ruin capability in your web site. So you will need to have the proper permissions set around the board.
Record Permissions
- Learn permissions are assigned if the consumer has rights to learn the report.
- Write permissions are assigned if the consumer has rights to write or regulate the report.
- Execute permissions are assigned if the consumer has the rights to run the report and/or execute it as a script.
Listing Permissions
- Learn permissions are assigned if the consumer has the rights to get entry to the contents of the known folder/listing.
- Write permissions are assigned if the consumer has the rights so as to add or delete recordsdata which might be contained within the folder/listing.
- Execute permissions are assigned if the consumer has the rights to get entry to the true listing and carry out purposes and instructions, together with the facility to delete the information inside the folder/listing.
You'll be able to use a loose plugin like iThemes Security to scan the permissions in your WordPress web site.

WordPress report permissions scan
Listed below are some conventional suggestions for permissions on the subject of report and folder permissions in WordPress. See the WordPress Codex article on changing file permissions for a closer clarification.
- All recordsdata will have to be 644 or 640. Exception: wp-config.php will have to be 440 or 400 to forestall different customers at the server from studying it.
- All directories will have to be 755 or 750.
- No directories will have to ever be given 777, even add directories.
16. Disable Record Enhancing in WordPress Dashboard
Numerous WordPress websites have more than one customers and directors, which may make WordPress safety extra difficult. A very dangerous follow is to provide authors or participants administrator get entry to, however sadly, it occurs at all times. It is very important give customers the proper roles and permissions in order that they don’t ruin the rest. As a result of this, it may be really helpful to easily disable the “Look Editor” in WordPress.
Maximum of you could have most definitely been there at one level or any other. You cross to briefly edit one thing within the Look Editor and abruptly you're left with a white screen of death. It is far better to edit the report in the community and add it by the use of FTP. And naturally, in absolute best follow, you will have to be checking out such things as this on a building web site first.
WordPress look editor
Additionally, if your WordPress site is hacked the first thing they could do is attempt to edit a PHP report or theme by the use of the Look Editor. This can be a fast method for them to execute malicious code in your web site. In the event that they don’t have get entry to to this from the dashboard, initially, it will probably assist save you assaults. Position the next code to your wp-config.php report to take away the ‘edit_themes’, ‘edit_plugins’ and ‘edit_files’ features of all customers.
outline('DISALLOW_FILE_EDIT', true);
17. Save you Hotlinking
The idea that of hotlinking may be very easy. You to find a picture at the Web someplace and use the URL of the picture at once in your web site. This symbol will likely be displayed in your website online however it's going to be served from the unique location. That is in truth robbery as it's the usage of the hotlinked web site’s bandwidth. This may now not appear to be a large deal, however it would generate a large number of additional prices.
The Oatmeal is a smart instance. The Huffington Publish hotlinked a caricature of his which consisted of more than one pictures and it racked up a whopping $1,000+ invoice.

Hotlinking invoice
Save you Hotlinking in Apache
To forestall hotlinking in Apache merely upload the next code on your .htaccess report.
RewriteEngine on
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} !^http(s)?://(www.)?yourdomain.com [NC]
RewriteRule .(jpg|jpeg|png|gif)$ http://dropbox.com/hotlink-placeholder.jpg [NC,R,L]The second one row defines the allowed referrer – the web site this is allowed to hyperlink to the picture at once, this will have to be your precise website online. If you wish to permit more than one websites you'll reproduction this row and substitute the referrer. If you wish to generate some extra complicated regulations, check out this htaccess hotlink protection generator.
Save you Hotlinking in NGINX
To forestall hotlinking in NGINX merely upload the next code on your config report.
location ~ .(gif|png|jpe?g)$ {
valid_referers none blocked ~.google. ~.bing. ~.yahoo yourdomain.com *.yourdomain.com;
if ($invalid_referer) {
go back 403;
}
}
Save you Hotlinking on CDN
If you're serving your pictures from a CDN then the setup could be moderately other. Listed below are some assets with well-liked CDN suppliers.
18. At all times Take Backups
Backups are the only factor we all know they want however don’t at all times take. Lots of the suggestions above are security features you'll take to raised give protection to your self. However regardless of how safe your web site is, it's going to by no means be 100% protected. So you need backups in case the worst occurs.
Maximum controlled WordPress internet hosting suppliers now supply backups. Kinsta has 5 various kinds of backups, together with automated backups that with the intention to leisure simple at evening. You'll be able to even one-click repair your web site.
WordPress backups
In case your host doesn’t have backups there are some well-liked WordPress services and products and plugins which you'll use to automate the method.
WordPress Backup Services and products
WordPress backup services and products generally have a low per 30 days charge and retailer your backups for you within the cloud.
- VaultPress (from the Automattic group, now a part of Jetpack)
- CodeGuard
- BlogVault
WordPress Backup Plugins
WordPress backup plugins can help you grasp your backups by the use of FTP or combine with an exterior garage supply similar to Amazon S3, Google Cloud Garage, Google Pressure, or Dropbox. We extremely suggest going with an incremental resolution so it makes use of fewer assets.
19. DDoS Coverage
DDoS is one of those DOS assault the place more than one programs are used to focus on a unmarried gadget inflicting a Denial of Provider (DoS) assault. DDoS assaults are not anything new – in keeping with Britannica the primary documented case dates again to early 2000. Not like anyone hacking your web site, all these assaults don’t most often hurt your web site however relatively will merely take your web site down for a couple of hours or days.
What are you able to do to give protection to your self? Some of the absolute best suggestions is to make use of a credible third social gathering safety provider like Cloudflare or Sucuri. If you're working a industry it will probably make sense to put money into their top rate plans.

DDoS coverage from Cloudflare and Sucuri
Their complex DDoS coverage can be utilized to mitigate DDoS assaults of all paperwork and sizes together with the ones that concentrate on the UDP and ICMP protocols, in addition to SYN/ACK, DNS amplification and Layer 7 assaults. Different advantages come with hanging you in the back of a proxy which is helping to cover your beginning IP deal with, even if it isn't bulletproof.
Be sure that to try our case find out about on how to stop a DDoS attack. We had a shopper with a small e-commerce web site working Simple Virtual Downloads which were given over 5 million requests to a unmarried web page inside 7 days. The web site normally best generated between 30-40 MB an afternoon in bandwidth and a pair hundred guests in step with day. However all of a sudden, the web site immediately went to between 15-19 GB of information switch an afternoon! That’s an building up of 4650%. And Google Analytics confirmed no further visitors. So that isn't excellent.
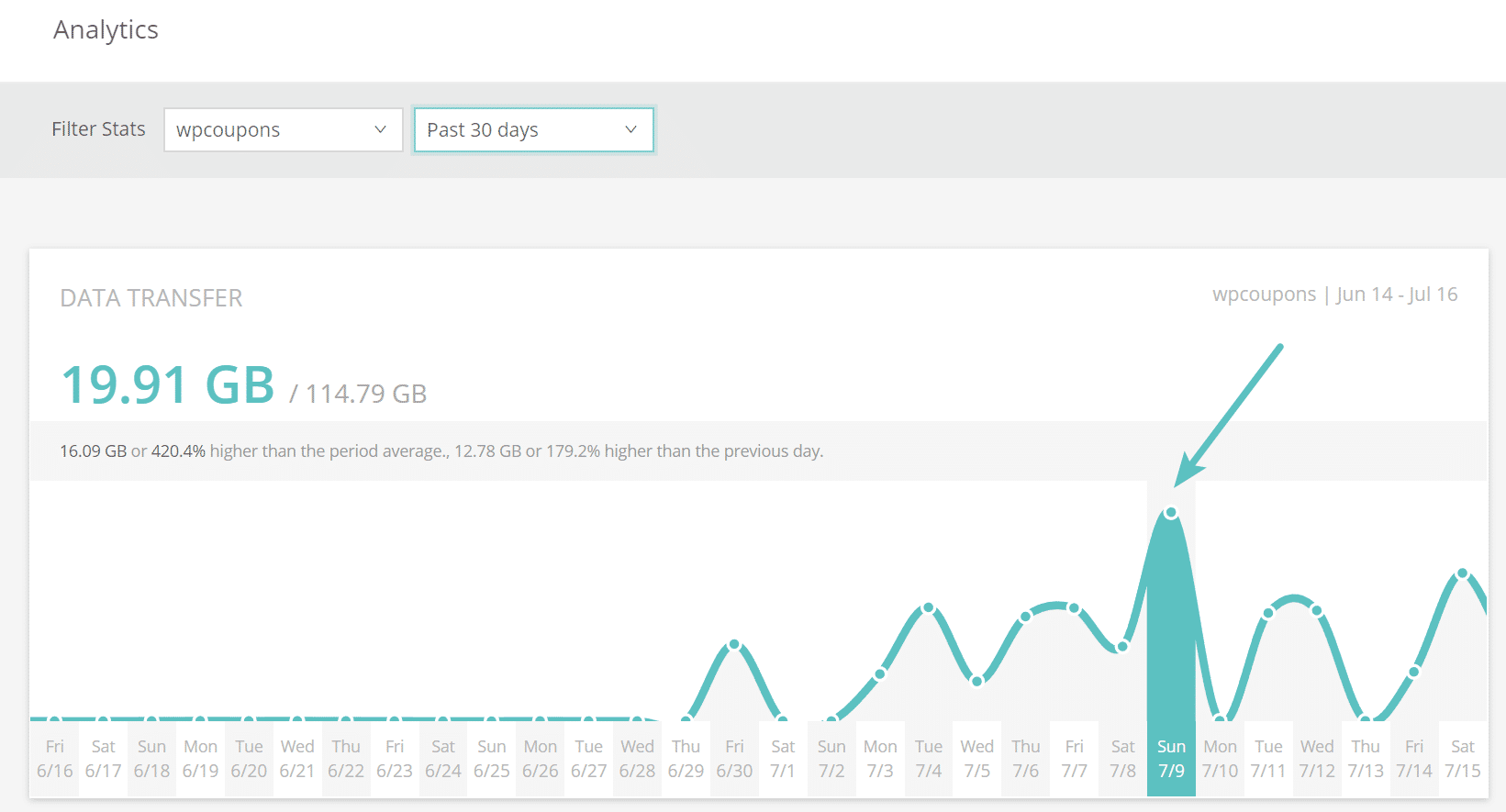
Prime bandwidth from DDoS assault
The buyer implemented Sucuri’s web application firewall on their web site and the entire bandwidth and requests immediately dropped at the web site (as observed beneath) and there hasn’t been a unmarried factor since. So certainly a excellent funding and time saver in case you are working into problems like those.
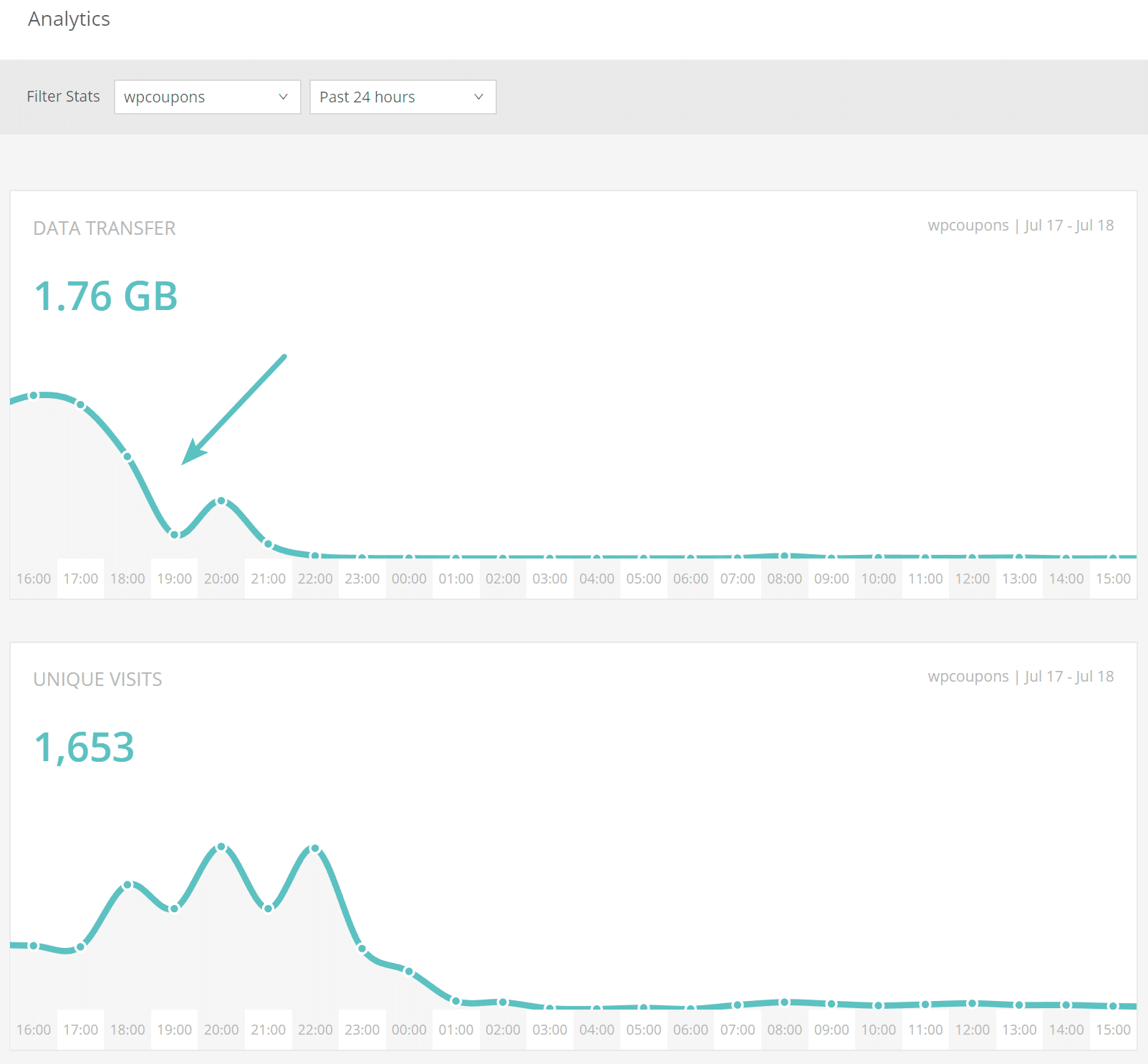
Added Sucuri internet utility firewall
Abstract
As you'll see, there are a large number of techniques you'll harden your WordPress safety. The use of suave passwords, maintaining core and plugins up-to-the-minute, and opting for a safe controlled WordPress host are only some that may stay your WordPress web site up and working safely. For plenty of of you, your WordPress web site is your each your enterprise and source of revenue, so it’s vital to take a little time and put in force one of the vital safety absolute best practices discussed above, faster relatively than later.
Have any vital WordPress safety guidelines that we ignored? If this is the case be happy to tell us beneath within the feedback.
The put up WordPress Security – 19 Steps to Lock Down Your Site seemed first on Kinsta Managed WordPress Hosting.
WP Hosting