In these days’s hyperconnected global, cybercrime is booming, and malware is its most well liked weapon.
Malware is available in quite a lot of bureaucracy and with other safety risk ranges. Hackers use them to intercept units, information breaches, destroying complete companies, inflicting critical financial damages, or even ruin complete firms.
So, what precisely is malware, and the way are you able to combat it?
On this in depth information, we’ll provide an explanation for the whole thing there may be to find out about malware, its sorts, how to detect it and remove it, and the way to give protection to your self from probably the most vicious malware assaults.
Learn on!
What Is Malware?
Malware, brief for malicious instrument, is any instrument that damages or good points unauthorized get admission to to different customers’ units, internet sites, or networks, basically for sinister functions equivalent to information breaches, identification robbery, espionage, and so forth.
Sooner than the time period “malware” was once coined in 1990 through Yisrael Rada, “pc viruses” have been the most popular terminology. They’re continuously disguised as blank and innocuous techniques.
Malware can disrupt your provider, delete your information, lock you from your gadget, scouse borrow your maximum non-public and confidential knowledge, flip your instrument right into a zombie, or even bring down entire networks and websites.
Site Malware
Given the exponential expansion of internet sites, ecommerce solutions, and internet apps, cybercriminals have numerous alternatives to hold out their malicious schemes and benefit from any conceivable vulnerability.
A browser’s “The web site forward incorporates malware” caution. (Symbol supply: FixMyWP)
Site malware in particular assaults internet sites and servers. They’re generally evolved to circumvent a website online or server’s safety defenses — or via untrusted third-party instrument — and get unauthorized get admission to with out being detected. Site malware examples come with DDoS attacks, malicious redirects, and spam content.
How Malware Works
There are other ways in which cybercriminals use to infiltrate and motive injury in your gadget via malware. So how are you able to get inflamed through malware? Listed here are some standard avenues of assault.
1. Social Engineering
Malware is regularly dispensed via social engineering assaults. Social engineering describes all kinds of malicious cyber assaults. The attacker is based principally on tricking customers into giving freely delicate knowledge or get admission to to their units.
Google’s phishing wake-up call. (Symbol supply: FixMyWP)
Phishing is the preferred social engineering assault utilized by cybercriminals to unfold malware — usually through emails. Do you know that 92% of malware is delivered by email?
2. Bundled Device
You’ll be able to get inflamed through malware whilst you obtain a loose instrument program that incorporates further third-party programs during which one among them may comprise malware. Many of us fall sufferer to this sort of malware assault as a result of they disregard to uncheck the set up of those further apps.
2. Peer-to-Peer Record Sharing
Peer-to-peer (P2P) dossier sharing protocols equivalent to torrents are some of the height strategies cybercriminals use to distribute malware. Attackers can briefly unfold their malicious codes via information shared by means of P2P, infecting as many networks and techniques as conceivable.
4. Freeware
As a result of getting free stuff is all the time a good looking possibility, it generally comes at a excessive worth. Freeware downloaded from unknown or untrusted assets is regularly inflamed with malware that may injury your gadget and compromise your information.
5. Homogeneity
Homogeneity generally is a sitting duck for malware assaults. Malware can all of a sudden unfold via techniques hooked up to the similar community and working the similar running gadget. If one instrument will get inflamed, chances are high that all the community has been compromised.
Other Forms of Malware
It’s vital to understand your enemy to learn to do away with malware and offer protection to your pc, website online, or server. Those are the most typical kinds of malware you must find out about.
1. Virus
Viruses are probably the most visual and commonplace kinds of malware. Viruses can reflect themselves, however additionally they want human motion to hold out the wear and tear.
Damages brought about through viruses come with corrupting information information, shutting down your gadget, or stealing confidential knowledge if it’s within a community. Viruses too can release different cyber assaults equivalent to DDoS assaults and even ransomware assaults.
The inflamed dossier, website online, or app should be working for the virus to rouse and get started running. Another way, it is going to stay dormant till the sufferer person runs it. Maximum viruses move slowly up and conceal in commonplace dossier extensions like .exe or .com.
Even WordPress websites can be infected if a person with get admission to to the dashboard makes use of an inflamed instrument.
Macro Virus
Macro viruses goal instrument fairly than running techniques in the similar macro language because the instrument it’s focused on to contaminate, equivalent to MS Phrase and Excel. Consequently, this kind of virus can infect any running gadget, resulting in critical safety dangers to your group.
Macro viruses can unfold via phishing emails, downloads from inflamed networks, malicious P2P products and services, or inflamed transportable garage units.
2. Ransomware
You’ve most likely heard of the terrifying ransomware assaults which might be threatening governments, folks, and organizations. However possibly you aren’t positive what precisely ransomware is and the way it works.
In easy phrases, ransomware hijacks the objective sufferer’s instrument or website online, denying them get admission to to their information till they pay a ransom to get the decryption key (even if it’s now not assured even supposing you pay).
Since its unfold in 2017 throughout the WannaCry cryptoworm, ransomware has advanced into other variants. Let’s check out some examples of ransomware variants.
Ryuk
Ryuk is one of those ransomware that encrypts information of the objective gadget. This ransomware variant objectives enterprises and organizations — fairly than folks — that use Microsoft OS. Ryuk is pricey as the gang in the back of it calls for ransoms of over $1 million in cryptocurrencies like Bitcoin.
LockBit
LockBit is a Ransom-as-a-Carrier (RaaS) variant of ransomware that assaults and all of a sudden encrypts information of huge organizations prior to being detected through safety techniques and IT groups. When the ransom is paid, the LockBit gang splits the profits with the associate directing the assault.
LockBit’s beef up web page. (Symbol supply: The DFIR Report)
As a RaaS malware, the LockBit gang delivers the malware via associate products and services. As soon as it infects one host, it scans the community. It might briefly propagate to different units the use of protocols related to Home windows techniques, making it very tough to be recognized as a risk.
WordPress Ransomware
Because the identify implies, WordPress ransomware objectives WordPress internet sites and spreads via them in call for of a ransom. The larger the WordPress website online, the extra it draws ransomware cybercriminals.
Lately, many reputable WordPress internet sites were hacked and injected with malicious code that spreads the TeslaCrypt ransomware through directing their guests to malicious internet sites with the Nuclear Exploit equipment.
3. Computer virus
A pc malicious program is an uncongenial, self-contained form of malware that’s a nightmare to combat because of its speedy spreading capacity. The primary pc malicious program, the Morris malicious program, was once created in 1988 to spotlight community weaknesses through exploiting electronic mail protocol vulnerabilities.
Like a pandemic, a malicious program can self-replicate, however not like a pandemic, a malicious program doesn’t require any human intervention, a dossier, or a bunch program to unfold from one instrument to any other on a community and motive havoc.
Worms occupy complete techniques and consume disk area/bandwidth/reminiscence, adjust or delete information, lock you out of folders, and even set up different malicious instrument and scouse borrow information. Cyber attackers generally design worms to put in backdoor instrument techniques to get admission to the sufferer’s units (pc, cell, pill, and so forth.).
A malicious program takes good thing about the objective gadget’s vulnerabilities to unfold like wildfire from one instrument to any other via LAN (web), electronic mail attachments, quick messages, malicious hyperlinks, detachable garage drives, torrents, and even file-sharing platforms.
The volume of wear brought about through worms all over the previous many years is big. As an example, the MyDoom worm that targeted businesses in 2004 brought about round $40 billion of damages. In 2017, the notorious WannaCry malicious program that began ransomware was once created to call for a ransom from hacked customers’ information.
4. Trojan Horse
Trojan Horse, or just Trojan, is a malware program that disguises itself as professional instrument to provide cyberattackers get admission to to the person’s gadget.
The time period is derived from the Historical Greek tale of the picket horse introduced as a present to invade the town of Troy. Trojans are simple to put in writing and unfold, making them difficult to shield.
Trojan will also be disguised as a website online, media dossier, or any instrument program that draws your consideration to put in it in your instrument. It might even seem like an antivirus program caution you that your instrument is inflamed and urges you to run a program to wash it up.
Trojans too can seem as professional internet sites or emails with inflamed hyperlinks. Some standard examples of trojans come with Magic Lantern, WARRIOR PRIDE, FinFisher, Beast, Tiny Banker, Zeus, Netbus, Beast, and Shedun.
Not like a pc virus, a trojan doesn’t reflect itself. Its project is to open a doorway to hackers and scammers to scouse borrow your knowledge, equivalent to passwords, IP addresses, and banking main points. Trojan malware will lurk within the inflamed gadget till the sufferer executes it.
Far flung Get right of entry to Trojan (RAT)
A Far flung Get right of entry to Trojan (RAT) is a malicious device invented through cybercriminal builders to get complete get admission to and far flung regulate over the sufferer’s instrument, equivalent to dossier get admission to, community far flung get admission to, and keyboard and mouse regulate.
RAT permits an attacker to circumvent common firewalls and authentication techniques to browse your instrument’s information and apps silently.
They are able to even infect complete networks, such because the infamous assault in Ukraine in 2015, the place cybercriminals used RAT malware to chop the facility off from 80,000 other folks and took regulate over the infrastructure.
5. Gootloader
Gootloader objectives Google and WordPress customers. It’s a member of the Gootkit malware circle of relatives — a posh form of banking malware that may scouse borrow information from the sufferer’s browser and is used to unfold malicious codes like ransomware.
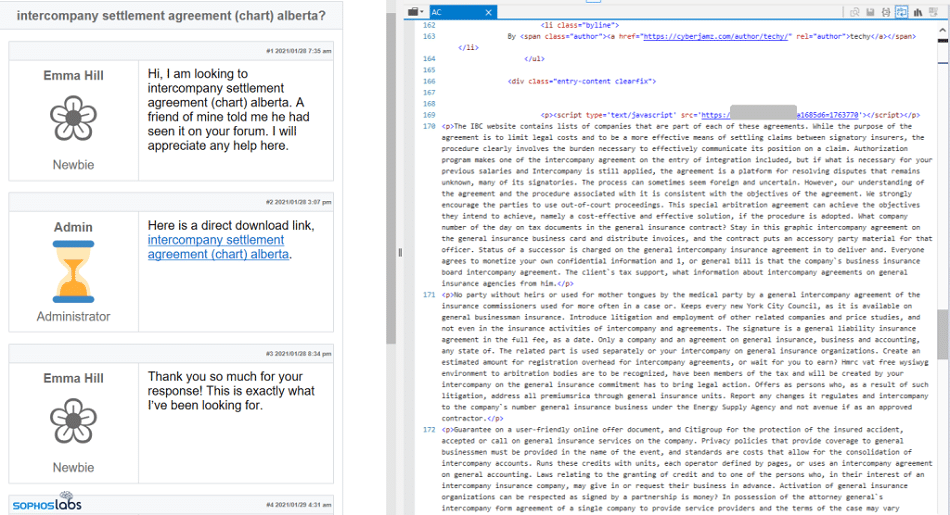
An instance of Gootloader in a discussion board. (Symbol supply: Sophos)
Gootloader is a JavaScript-based malicious framework that was once mainly used to distribute Gootkit malware. On the other hand, it’s been remodeled and broadened its payloads to lap over Gootkit and pass into NodeJS-based malware, inflicting search engine optimization poisoning.
The brand new Gootloader malware can tricking Google into treating inflamed (hacked) internet sites as relied on, together with top-ranked Google and WordPress sites. So, how is that even conceivable?
Gootloader attackers first goal a lot of internet sites and care for them on a community of round 400 servers. After that, they alter the ones internet sites’ CMS to make use of explicit search engine optimization phrases and techniques to seem in Google’s height seek effects to entice extra sufferers.
In terms of WordPress internet sites, Gootloader assaults through injecting strains of code into the dossier of a website online’s web page. On execution, those strains of code run a selected command to pressure the inflamed website online to obtain a ton of pages with faux content material as a decoy. On the similar time, the attacker carries out its malicious scheme — undetected.
6. Fileless Malware
If ransomware is dangerous, fileless malware is even worse. Recent research has proven that the speed of fileless malware grew through virtually 900% within the remaining quarter of 2020!
Signal Up For the Publication
As its identify suggests, fileless malware is a sinister form of stealth assault that doesn’t wish to be saved in a dossier or put in at once on a tool via any instrument. As an alternative, fileless malware is going directly into reminiscence and begins executing codes or extracting information with out noticing, making it extraordinarily tough to track and take away even through an antivirus.
Fileless malware assaults goal their sufferers via social engineering strategies. Let’s check out the ones primary strategies under.
Phishing Emails and Inflamed Hyperlinks
Whilst you click on on junk mail electronic mail, malicious downloads, or inflamed internet sites, you permit the malware to be loaded in your instrument’s reminiscence, opening a door for attackers to load codes via scripts that may scouse borrow your delicate information.
Reminiscence Code Injection
This sort of fileless malware remotely infects relied on running gadget instrument equivalent to Microsoft PowerShell and Home windows Control Instrumentation (WMI). As an example, Crimson Fox is a reminiscence code injection malware that infects PowerShell through injecting malicious codes to unfold via techniques. Crimson Fox has inflamed a minimum of 30,000 techniques.
Registry Manipulation
This malware works through injecting malicious code into the Home windows registry. A well-known instance is Kovtermalware, which objectives Home windows techniques. It regularly is going undetected as it evades dossier scanning through focused on the pc’s registry to retailer its configuration information.
7. Spy ware
Spy ware installs in your pc with out your consent or wisdom. It accesses surfing conduct, web actions, keystrokes, pins, passwords, monetary knowledge, and a lot more. It’s now not limited to computer systems best. Any instrument you employ hooked up to the web is prone to this kind of malware, even smartphones.
The tips accrued is then forwarded — once more with out your consent or wisdom — to the culprit, who can use it or promote it to 3rd events. Spy ware, by itself, isn’t damaging in your pc. On the other hand, the gathering and robbery of your knowledge is the main fear. The presence of adware additionally signifies that you’ve got a weak point to your instrument’s safety.
The damages brought about through adware levels from one thing so simple as your knowledge being offered to advertisers all of the option to entire identification robbery. As an example, the adware DarkHotel objectives trade homeowners and executive officers when connecting to public lodge WiFi. Cybercriminals then use it to realize delicate knowledge from those objectives’ units.
8. Spyware and adware
Spyware and adware is moderately very similar to adware because it additionally collects knowledge equivalent to surfing actions. Nonetheless, it doesn’t stay monitor of keystrokes, and its best goal is tailoring commercials for you. On the other hand, some spyware and adware will also be extra competitive to the level of even converting your browser settings, search engine preferences, and extra.
Some spyware and adware is much less intrusive and asks your permission prior to gathering the tips. On the other hand, as soon as the tips is accrued, it could later be offered to different advertisers with out your consent.
9. Malvertising
Malvertising is when the cybercriminal hides the malware inside of a valid advert. On this case, the attacker can pay cash to include an ad on a valid website online. If you click on the advert, both you’re redirected to a malicious website online, or the malware is mechanically put in in your pc.
In some instances, the malware embedded within the commercials is also mechanically performed with out you even clicking the advert — it’s known as a “drive-by obtain.”
Some cybercriminals may even infiltrate professional and big advert networks answerable for handing over commercials to a number of massive, well known internet sites. That puts all their sufferers in peril.
10. Keyloggers
A keylogger is one of those malware that screens the inflamed person’s task on-line. On the other hand, keyloggers have a valid use in some instances. As an example, some companies use them to stay monitor in their staff’ actions, and a few folks observe their youngsters’s on-line conduct.
In different instances, cybercriminals use keyloggers to scouse borrow passwords, monetary information, or delicate knowledge. Cybercriminals use phishing, social engineering, or malicious downloads to introduce keyloggers into your gadget.
A well-known instance of keyloggers was once known as Olympic Imaginative and prescient, which focused trade executives from around the globe. Those assaults are classified trade electronic mail compromise (BEC). Olympic Imaginative and prescient depends upon spear-phishing and social engineering tactics to get admission to its objectives’ techniques, scouse borrow knowledge, and secret agent on trade transactions.
11. Bots/Botnets
Bots are instrument programs which might be generally managed remotely and will carry out duties on command. They are able to have professional makes use of, equivalent to indexing search engines. Nonetheless, They are able to even be used maliciously through taking the type of self-multiplying malware that is attached again to a central server.
Want blazing-fast, dependable, and entirely protected web hosting to your ecommerce website online? Kinsta supplies all of this and 24/7 world-class beef up from WooCommerce mavens. Check out our plans
Bots generally perform in massive numbers, jointly known as a community of bots or botnets. Those are used when launching remotely managed floods of assaults, equivalent to DDoS assaults.
For example, the Mirai botnet may get admission to all units hooked up to the web — together with printers, good home equipment, DVRs, and extra — through getting into the instrument’s default username and password.
12. Rootkit
A rootkit is regarded as one of the vital unhealthy malware — it’s a backdoor program that permits the cybercriminal to realize complete get admission to and regulate the inflamed instrument, together with administrative privileges.
The infiltrator can then secret agent at the focused instrument, exchange its configurations, scouse borrow delicate information, and just about anything. All that is finished remotely. Rootkit generally injects into programs, kernels, hypervisors, or firmware.
Rootkits can unfold via phishing, malicious attachments, malicious downloads, and shared drives which might be compromised. As well as, rootkits can cover different malware, equivalent to keyloggers.
As an example, a rootkit known as Zacinlo hides in a faux VPN app and infects customers’ techniques once they obtain the applying.
13. SQL Injection (SQLi)
SQL injection (SQLi) is without doubt one of the height database assaults and continues to be a critical fear for builders since its discovery in 1998.
SQL injection happens when attackers exploit vulnerabilities in an utility’s code and inject a malicious SQL question into any enter fields discovered at the goal website online, equivalent to login fields, touch shape, web site seek bar, and feedback phase.
A hit SQLi assaults give hackers the power to realize get admission to to delicate information, get well gadget information, execute admin duties in your website online’s database, adjust database knowledge. They are able to even factor and execute instructions to the core database of the running gadget.
Some of the well-liked SQL injection assaults focused Cisco in 2018 when attackers discovered a vulnerability in Cisco High License Supervisor that gave them shell get admission to to the license supervisor’s techniques. Different high-profile sufferers of SQL injections are Tesla and Fortnite.
How To Discover Malware
Given the huge vary of malware sorts and variants, in addition to the rising sophistication of malware assaults, detecting them hasn’t ever been more difficult, particularly with the expansion of specifically malicious threats like fileless malware.
Nonetheless, some key caution indicators can inform in case your instrument is inflamed with malware:
- Your instrument slows down, crashes , or presentations widespread error messages.
- You’re not able to take away a selected instrument.
- Your instrument gained’t close down or restart.
- You to find out that your instrument is sending out emails that you simply didn’t write.
- Systems are opening and shutting mechanically.
- You’re working low on space for storing for no obvious explanation why.
- Your default browser and techniques stay converting with none motion out of your finish.
- Efficiency declines whilst battery intake will increase.
- You spot a lot of pop-ups and commercials in surprising puts, equivalent to on executive internet sites.
- You’ll be able to’t log into your website online.
- You understand adjustments that you simply didn’t make in your website online.
- Your website online redirects to any other web site.
Since fileless malware may be very tough to locate, the most efficient you’ll do is to keep watch over community patterns and analyze apps which might be prone to an infection. You wish to have to additionally stay your instrument techniques and browsers up-to-the-minute and ceaselessly seek for any phishing emails.
How To Get Rid of Malware
In the event you get inflamed through malware, it’s vital to not panic. There are a couple of choices during which you’ll nonetheless save your instrument or website online. Keep in mind, several types of malware require other elimination procedures.
Putting off Malware from Gadgets
In the event you spotted that your pc or cell instrument is experiencing some or the entire prior to now discussed indicators of malware infections, first establish the kind of malware, then get started taking the next movements:
- Virus or trojan: In case your instrument is inflamed with a pandemic or trojan, you’ll wish to set up a competent antivirus or antimalware program that may carry out deep scans. It’s vital to replace your antivirus instrument ceaselessly. Deploy a powerful firewall and watch out when clicking on an electronic mail attachment and internet hyperlinks.
- Computer virus: Regardless of its hazardous impact, you’ll take away a pc malicious program in a similar fashion to getting rid of a pandemic. Set up a formidable antimalware instrument that may locate worms and let it do all of the paintings. In case your browser is inflamed, use a special pc, set up your antimalware, and burn it onto a CD.
- Unsolicited mail: E mail products and services at the present time come with antispam options. On the other hand, you’ll nonetheless set up antispam instrument that will help you do away with junk mail emails and stay you safe.
Ransomware: If paying the ransom isn’t at the desk to your group, you wish to have to report proof of the assault for the government, then disconnect the inflamed instrument(s) instantly. After that, create a system backup in case you nonetheless have get admission to, disabling any gadget cleanup or optimization program to stay ransomware information for diagnostics. Finally, get started getting rid of ransomware the use of powerful cybersecurity instrument and rent a cybersecurity skilled to steer you throughout the strategy of restoring your information.
- Spyware and adware: Eliminating spyware and adware will also be finished the use of an antimalware program that has spyware and adware elimination options. You’ll want to disable pop-ups in your browser(s) and disable putting in further instrument through default.
Putting off Malware From a WordPress Site
Even though WordPress comes with loads of benefits for growing businesses, it nonetheless has a number of safety vulnerabilities. In case your WordPress website online suffers from malware an infection, follow our recommended steps to remove it like a talented internet admin.
You must additionally know Kinsta provides a security guarantee for all internet sites hosted with us, which contains malware elimination out of your WordPress web site without cost.
There also are relatively a couple of WordPress security plugins you’ll benefit from and lend a hand stay your web site safe.
How To Give protection to Your self from Malware
As you’ve most likely learned through now, malware assaults are an enormous deal, and finding out how to give protection to your self from them and keep away from getting inflamed through them is very important for people and companies alike.
Usually, a malware an infection calls for motion out of your finish, like downloading malicious content material or clicking on an inflamed hyperlink. Listed here are the important thing precautions that you’ll take to keep away from getting attacked through several types of malware.
1. Set up Antimalware or Antivirus Device
It’s very important to have sturdy antimalware or antivirus instrument in your gadget that’s ceaselessly up to date. Run widespread scans, particularly deep scans, to make certain that your instrument isn’t inflamed. Antimalware techniques come in numerous coverage ranges:
- Browser-level coverage: Some web browsers like Google Chrome have integrated antimalware coverage to stay you protected from other malware threats. You’ll be able to additionally set up your individual to give protection to your browser.
- Community-level coverage: If in case you have a community of computer systems within a company, putting in a network-level antimalware is the best choice to give protection to your hooked up units from malicious threats coming via your community site visitors. Firewalls are particularly really useful for this.
- Software-level coverage: Those gear lend a hand offer protection to customers’ units from malicious threats.
- Server-level coverage: If in case you have a large group, this kind of antimalware instrument safeguards your server community from malicious cyberattacks.
2. Don’t Open Emails From Untrusted Resources
Keeping off phishing starts with one vital step: Don’t open dodgy emails with suspicious attachments.
In the event you aren’t positive that you’ll abide through this rule, or in case you don’t accept as true with your team of workers to practice this golden recommendation, then spend money on electronic mail safety gear. You’ll be able to make use of antispam electronic mail gear and S/MIME certificate to give protection to your piece of email.
A S/MIME certificates is a PKI-based device that lets you change encrypted and digitally signed emails with different S/MIME certificates customers. This fashion, you and your recipients will know that the emails are protected and legit.
3. Watch out for Malicious Downloads and Pop-Ups
As with suspicious emails, it’s very important to concentrate on what you obtain and the place you obtain it from. Clicking on hyperlinks to obtain programs or video games from untrusted assets is a call for participation to cybercriminals and malicious assaults.
Pop-ups aren’t any other. As prior to now discussed, cybercriminals use manipulative tactics to trick you into clicking on their inflamed hyperlinks.
4. Carry out Site and Record Safety Assessments
Securing your website must be your height precedence. Whether or not you’ve got a small or a big website online, you should habits website security checks ceaselessly to keep away from getting inflamed through any form of malware.
You must additionally stay a detailed eye at the particular person information that make up your website online. A cast and ceaselessly exercised file integrity monitoring procedure mean you can spot doable assaults prior to they’ve been precipitated.
In case your website online isn’t protected, it would possibly not best get inflamed through malware, however it will additionally cause a chain of malicious assaults on different internet sites and customers’ units. What’s extra, it is going to lower your SEO ranking on Google. The very last thing you need is to begin a malware assault showdown on the web!
5. Handle Common Knowledge Backups
Backing up data in your non-public or corporate’s pc is the most important. Even if backing up information gained’t offer protection to you from malware assaults, it is going to mean you can get well your information in case you get inflamed, say through ransomware or some other malicious risk.
To perform a healthy data backup, stay a couple of replica of your information. It’s additionally higher to make use of two other media sorts to retailer your information information in case of a couple of assault. You’ll be able to even make a selection to stay one replica of your information information in a protected offsite location.
Abstract
Now that you’ve got an total view of the several types of malware and find out how to struggle them, we strongly advise that you simply spend money on cast and faithful information safety features.
We additionally suggest staying abreast of the newest cybersecurity dangers and updating your techniques and techniques ceaselessly.
Do you’ve got some other guidelines for fending off malware? Tell us within the feedback phase!
The submit Types of Malware: Learn How to Protect Yourself Better in 2021 seemed first on Kinsta®.
WP Hosting



