So, you’re staying secure at house. However are you staying secure whilst operating from house? There are some necessary work at home safety guidelines we want to move over to successfully stay your information secure.
Running from house is non violent and amusing. It’s been round for many years however has received momentum since the current global pandemic started.
The difficulty is, operating from house additionally brings cybersecurity dangers, particularly for small companies that don’t have a right kind IT infrastructure. Workers who lack safety consciousness may cause quite a lot of hurt to themselves and their employers.
Right here at Kinsta, we’ve been absolutely faraway from the start and always have openings for the ones in search of faraway paintings.
That’s why on this complete information, we’re going that will help you know about the commonest cybersecurity dangers that you need to face whilst operating from house. We’ll additionally percentage necessary work at home safety guidelines that will help you keep secure as you do your paintings on-line.
Stay studying!
6 Commonplace Paintings From House Safety Dangers
Sooner than we bounce into the tips about staying secure on-line whilst operating from house, let’s first check out the average sorts of cyberattacks on faraway employees.
1. Phishing Scams
Some of the greatest cyber threats to faraway staff is phishing attacks. Even if phishing scams originated within the mid-Nineteen Nineties, they’re nonetheless fashionable to nowadays and feature grow to be extra subtle with the development of era.
Phishing is one of those cyberattack that targets at stealing confidential information akin to bank card numbers, checking account main points, and login credentials (e.g. usernames, passwords, and private identity numbers). No longer best does phishing immediately hurt you as a person/worker, but it surely additionally items a safety possibility on your group/employer.
So, how does phishing paintings?
The attacker poses as a relied on entity to trap the objective sufferer into clicking on a malicious hyperlink most often despatched via an e mail or textual content message. When the recipient opens the inflamed hyperlink, they unwittingly set up malware or even ransomware on their units.
Whilst the commonest form of phishing scams is completed by the use of e mail, many phishers use different approach of an infection, together with SMS (smishing), voice-based scams (vishing), social media-based threats, and even via USB flash drives.
With the unfold of COVID-19, phishers are making the most of the pandemic to hold out cyberattacks via emails that comprise hyperlinks claiming to have necessary details about the virus.
frame a.novashare-ctt{show:block;background:#00abf0;margin:30px auto;padding:20px 20px 20px 15px;colour:#fff;text-decoration:none!necessary;box-shadow:none!necessary;-webkit-box-shadow:none!necessary;-moz-box-shadow:none!necessary;border:none;border-left:5px forged #00abf0}frame a.novashare-ctt:hover{colour:#fff;border-left:5px forged #008cc4}frame a.novashare-ctt:visited{colour:#fff}frame a.novashare-ctt *{pointer-events:none}frame a.novashare-ctt .novashare-ctt-tweet{show:block;font-size:18px;line-height:27px;margin-bottom:10px}frame a.novashare-ctt .novashare-ctt-cta-container{show:block;overflow:hidden}frame a.novashare-ctt .novashare-ctt-cta{go with the flow:proper}frame a.novashare-ctt.novashare-ctt-cta-left .novashare-ctt-cta{go with the flow:left}frame a.novashare-ctt .novashare-ctt-cta-text{font-size:16px;line-height:16px;vertical-align:heart}frame a.novashare-ctt .novashare-ctt-cta-icon{margin-left:10px;show:inline-block;vertical-align:heart}frame a.novashare-ctt .novashare-ctt-cta-icon svg{vertical-align:heart;top:18px}frame a.novashare-ctt.novashare-ctt-simple{background:0 0;padding:10px 0 10px 20px;colour:inherit}frame a.novashare-ctt.novashare-ctt-simple-alt{background:#f9f9f9;padding:20px;colour:#404040}frame a.novashare-ctt.novashare-ctt-simple-alt:hover,frame a.novashare-ctt.novashare-ctt-simple:hover{border-left:5px forged #008cc4}frame a.novashare-ctt.novashare-ctt-simple .novashare-ctt-cta,frame a.novashare-ctt.novashare-ctt-simple-alt .novashare-ctt-cta{colour:#00abf0}frame a.novashare-ctt.novashare-ctt-simple-alt:hover .novashare-ctt-cta,frame a.novashare-ctt.novashare-ctt-simple:hover .novashare-ctt-cta{colour:#008cc4}
2. Vulnerable Passwords
Vulnerable passwords are any other main safety possibility and a doorway for hackers to wreak havoc for workers and firms, particularly small- to medium-sized companies. Would you consider that it takes just one susceptible password for attackers to breach a complete community?
Even if numerous firms put money into cybersecurity to fight safety threats and knowledge breaches, susceptible passwords utilized by staff make it simple for hackers to get get right of entry to not to best their non-public computer systems but additionally trade information.
The 2020 Verizon Data Breach Investigations Report printed that 81% of the whole information breaches have been because of the usage of susceptible passwords. That’s a whopping share.
Attackers use many alternative easy methods to hack passwords, akin to credential stuffing, dictionary assaults, brute-force assaults, and rainbow desk assaults. Let’s in short duvet what every of those is.
Credential Stuffing
This is without doubt one of the maximum commonplace assaults utilized by hackers by means of operating database lists of breached login credentials mechanically towards the objective web page login. In this sort of assault, hackers depend on many customers make use of the similar passwords and password permutations.
Dictionary Assault
This can be a form of password-guessing assault the place hackers use a dictionary of regularly used phrases ceaselessly observed in passwords. People who use actual phrases or words of their passwords are extremely liable to this sort of assault.
Brute Drive Assault
That is any other form of password-guessing assault during which hackers publish as many password mixtures (letters, numbers, and emblems) as conceivable till a password is sooner or later cracked.
Rainbow Desk Assault
This hacking assault makes use of a rainbow hash desk that accommodates the values used to encrypt passwords and passphrases. It’s very similar to a dictionary assault, however hackers use a desk as an alternative of a listing of phrases.
3. Unsecured WiFi Networks
Whilst operating from house has its perks, for those who’re attached to an unsecured WiFi community — akin to public WiFi networks to be had in cafes, eating places, motels, libraries, co-working areas, or airports — this may create safety issues for you and your employer.
A public WiFi community is sort of a Disneyland for hackers and cybercriminals: It lets them simply hack into units to thieve your own information and identification.
Hackers use some in style ways to assault your laptop or smartphone whilst you’re the usage of an unsecured WiFi community. Let’s speak about a few them.
Gadget-in-the-Center (MITM) Assault
That is an eavesdropping assault the place a hacker can intercept the information transmitted between a shopper (your instrument) and the server you’re attached to. The attacker then has the facility to keep up a correspondence with you via pretend web pages or messages to thieve your data. Public WiFi networks are commonplace goals as they’re both poorly encrypted or no longer encrypted in any respect.
Evil Dual Assault
This can be a form of MITM cyberattack during which hackers benefit from poorly encrypted or unencrypted WiFi networks (most often public WiFi/hotspots) to arrange a faux WiFi community with a faux (evil dual) get right of entry to level. Whenever you sign up for this pretend community, you unwittingly percentage your entire data with the hacker.
4. The use of Private Units for Paintings
Whilst some organizations supply their staff with units for faraway paintings, maximum firms nonetheless permit their staff to make use of their non-public units (e.g. laptops, desktops, pills, and smartphones). The end result? A rising selection of safety and knowledge breaches.
When staff work at home the usage of their non-public units, they ceaselessly don’t believe that those units aren’t according to their corporate’s IT infrastructure, nor do they percentage the similar security features. That’s why non-public units are extra liable to cyber threats.
Additionally, staff who work from home the usage of their non-public units can talk over with any web page they would like and set up any apps or instrument techniques that would possibly differently be blocked by means of an employer for safety causes, making them a very simple goal for malicious actions and hackers.
5. Malware and Viruses
Malware and viruses have grow to be very subtle, developing severe issues for companies and people, particularly all through those tricky occasions of the pandemic. Deficient security features and reckless worker behaviors result in the spread of malware and viruses.
Wait — aren’t malware and viruses the similar factor?
The solution isn’t any. Whilst viruses are one of those malware, no longer all malware is an epidemic.
Malware is a collective time period for any malicious instrument created to contaminate and reason injury to the host machine or its person. There are various kinds of malware, together with viruses, worms, trojan, ransomware, spyware and adware and spyware and adware, and scareware.
A pc virus is one of those malware created to copy itself and unfold to a couple of units as broadly as conceivable via inflamed web pages, programs, emails, detachable garage units, and networking routers, similar to a organic virus. The purpose of a pc virus is to reason as a lot hurt as conceivable with out the person’s wisdom. It will probably simply unfold via servers and smash web pages.
6. Unencrypted Document Sharing
Should you assume malware, viruses, and hackers are unhealthy, unsecured dossier sharing is similarly unhealthy or even riskier for faraway operating.
Far flung staff would possibly inadvertently put important trade information in peril via deficient practices. Sharing recordsdata via unencrypted emails makes it as simple as taking pictures fish in a barrel for hackers to intercept the ones emails and thieve data.
The use of reasonable and poorly secured cloud dossier sharing akin to non-public cloud storage drives is any other possibility issue. As well as, staff who use peer-to-peer (P2P) file-sharing pose a risk to their corporate since any person can get get right of entry to to information recordsdata on their units, together with hackers.
Flash drives can be unhealthy if inflamed with malware as they are able to simply bypass community safety. It will get worse if an worker units their machine to autorun a flash force, which permits malicious content material.
Paintings From House Safety Tricks to Give protection to Your Information
Right here’s our roundup of the most productive cybersecurity guidelines for safe operating from house. Be sure you talk over with your employer first to make sure that you just’re each at the identical web page.
1. Put money into Just right Safety Instrument
There are a lot of safety instrument manufacturers available on the market that lend a hand protect you from cybersecurity threats. These kind of instrument programs offer protection to your units towards a variety of various kinds of threats on the identical time.

Antivirus signal. (Symbol supply: Pixabay)
This present day, there’s a mess of instrument for various kinds of assaults, together with antiviruses, antimalware, hacking strive blockers, and DDoS defense. Some techniques are unfastened whilst others are paid, with costs ranging between reasonable ($2) and costly ($120) relying at the coverage options they provide.
However, as cyber threats are steadily evolving and turning into more potent to circumvent this instrument, it’s higher to head for the paid variations as they’re most often extra complete and come with extra powerful security measures to fight vicious threats.
Take into accout that what separates dependable safety instrument from a deficient one is the frequency of its updates. In different phrases, if the instrument steadily updates itself, that suggests it’ll at all times bear in mind every time a brand new risk is presented to the pc international.
2. Separate Paintings Units from Private Units
Should you’re operating from house, it’s preferable to make use of two separate units for paintings and private use. On this case, if one instrument will get compromised by means of an undesirable risk, the opposite received’t be affected.
This doesn’t best move to your computer systems, however for any instrument attached to the web that’s open to exterior dangers. This comprises your laptop, your cellular instrument, your pill, and so on. It even applies to different units like moveable garage gadgets.
Should you don’t have already got separate units, then we strongly counsel you’re making the alternate. Some employers supply their staff with devoted paintings units, particularly all through the present pandemic. If so with you, you then’ll don’t have any downside.
Some other necessary step we propose is to at all times stay separate however continuously updated backups of your necessary paintings recordsdata. On this case, you’ll use your own units only for the sake of those backups — excluding, in fact, if this data is very confidential.
3. Stay Running Gadget As much as Date
Maximum main working methods have their very own protection gear such as firewalls to forestall sure threats from affecting your instrument. Like with safety instrument, those gear want to be continuously up to date to stay consistent with newly presented threats.
Those gear are up to date with the updating of the working machine. That’s why it’s extremely advisable to at all times stay your working methods up-to-the-minute on your entire units.
Maximum working methods provide the solution to both have the updates happen mechanically or manually. We advise you stay it set to the automated solution to have updates happen once they’re to be had.
Some other necessary pointer is to make certain that the working machine you’re the usage of is 100% unique. That is extra commonplace with Microsoft Home windows than different working methods, as some other folks set up a duplicate of Home windows with no need the right kind activation key required to stay all its integrated safety gear operating correctly.
4. Stay Instrument As much as Date
Instrument updates aren’t restricted on your OS — it’s additionally an important to stay all of the instrument and techniques you utilize for your units up-to-the-minute continuously, particularly the ones techniques that depend on connecting to the web to paintings.
This comprises, however isn’t restricted to, your browsers and communique techniques (Zoom, Skype, Whatsapp Messenger, and so on.). A majority of these techniques most often have their very own integrated security features, which, like all safety instrument, require common updates to stand any newly presented threats.
In your paintings units, it’s additionally necessary to simply set up the techniques you in truth want for paintings and stay all different techniques akin to video games, streaming apps, and so on for your non-public units. This pairs with the “separate paintings units from non-public units” tip that we mentioned previous.
5. Protected Your WiFi Community
These days, nearly each and every house makes use of a wi-fi web community, or WiFi, as an alternative of a stressed out ethernet cable. As you realize, to connect with the community calls for a password, which you created when putting in place your router. This password is a significant factor in figuring out whether or not your own home web community is safe or no longer.
The least destructive results of your community being penetrated is your web velocity slowing down as a number of undesirable units are attached to it and the usage of it. On the other hand, extra severe problems can happen, like cybercrimes being dedicated by means of different events the usage of your network, which shall be traced again to you.
If in case you have a nosey neighbor with some techy talents, there’s at all times a possibility of them working out your password and penetrating your community. That’s why it’s necessary to have a fancy password, however no longer so complicated that you find yourself forgetting it your self.
Signal Up For the E-newsletter
It doesn’t finish there. You will have to additionally alternate your password every so often to stay it much more safe. In the end, don’t overlook to put in your firmware updates incessantly to give protection to your community from any new vulnerabilities.
Should you’re operating off of a public community (espresso area, lodge, and so on.), it’s advisable that you select to stay your instrument invisible at the community (take a look at your sharing choices when connecting to the community).
6. Use a VPN
A virtual private network (VPN) is perfect identified for bypassing geolocations on-line to get right of entry to streaming web pages which are blocked in sure places all over the world. On the other hand, VPNs are extensively utilized for safety causes. For example, they encrypt your connection and secures your entire surfing information from undesirable breachers.
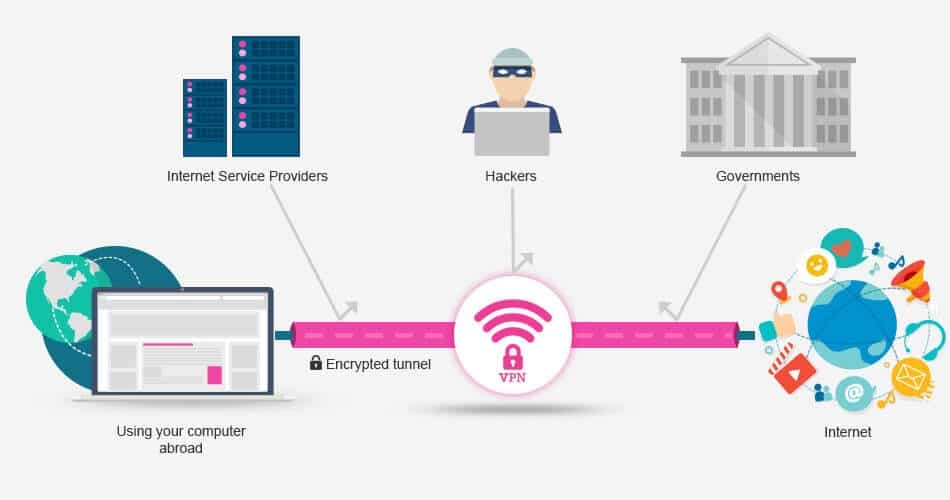
How a VPN works. (Symbol supply: Stream Telly)
Whilst you hook up with a VPN, as an alternative of your information going throughout the web provider supplier’s (ISP) servers, it is going throughout the VPN’s corporate servers. On this procedure, your IP is modified, thereby hiding your true on-line identification.
There are a lot of VPN names available on the market lately, and they all serve the similar goal, roughly. On the other hand, there are a couple of key components to believe when selecting the proper VPN for you.
First off, you should make certain that the VPN you select in truth works for your nation, as a number of international locations block the use of a VPN. You’ll be able to to find out by means of asking the VPN’s buyer give a boost to earlier than subscribing.
Different components come with the degrees of encryption the VPN helps (L2TP, OpenVPN, and so on.) and the quantity and places of its servers. The extent of encryption can decide whether or not or no longer a VPN is safe sufficient. Many VPNs lately give a boost to multiple encryption levels, that are appropriate for various eventualities.
The quantity and places of the VPN servers decide whether or not or no longer you’ll discover a shut sufficient server on your geolocation to have the benefit of sooner connection speeds. The nearer the server, the quicker the relationship velocity is.
VPNs include a number of security measures. One helpful function you could come by means of is the kill transfer. The aim of that is to dam your web connection altogether within the case that, for any reason why, your VPN connection drops impulsively. This saves your units from being uncovered all through this connection drop.
Different VPNs be offering browser extensions and apps for various units and working methods (Home windows, Mac, iOS, Android, Linux, and so on.). In some instances, you’ll even arrange your own home router to glue immediately throughout the VPN, thereby securing all units attached to the community on the identical time.
7. Bodily Safety
When operating out of your corporate’s place of job, it’s no longer your duty to stay your units bodily safe from robbery. There’s most often safety personnel caring for that for you, despite the fact that in some instances, you can be required to fasten your place of job or laptop earlier than leaving.
The similar thought applies at house, however the causes are other. On the place of job, it’s best you and your tech-savvy personnel strolling round, however at house, there are kids, pets, kin, and even pals. We’re no longer implying that you’ll’t accept as true with them or that they’ll deliberately impact your paintings units, however you continue to want to stay your information secure from undesirable fiddling.
This will also be achieved by means of retaining your entire work-related units and pieces (paperwork, recordsdata, and so on.) locked in a separate room — or, whilst you’re no longer the usage of them, stay them locked in a secure cabinet or any place that best you’ll get right of entry to.
8. Use a Protected Browser and Seek Engine
We already know that popular browsers and serps, akin to Google and Bing, accumulate your information for their very own promoting functions. That is regarding with regards to your paintings, as you’re most likely coping with delicate data.
Don’t get us fallacious — we’re no longer implying that those serps are unhealthy! However with regards to your paintings, it’s higher to be secure than sorry. That’s why it’s advantageous to make use of them for your on a regular basis non-public lifestyles, but it surely’s most well-liked to make use of a more private alternative when operating.
There are a number of search engine alternatives that serve that goal. The preferred one is DuckDuckGo. No longer best does it have a seek engine that collects very minimum information, but it surely additionally has its personal browser for cellular units that bears the similar privateness thought.
In contrast to maximum serps, DuckDuckGo doesn’t accumulate any data that provides away your on-line identification. As an alternative, it permits you to browse the web with no person profile, which turns out to be useful to steer clear of personalised commercials or seek effects.
9. Again Up Your Information
There are a number of components that may reason you to lose your information, and that’s why retaining separate however steadily up to date backups are probably the most necessary tips about our checklist. There are two primary techniques to stay backups: bodily backups and cloud backups.
Bodily backups are the extra conventional manner that comes to retaining a backup of your information on a separate exhausting force or, extra ideally, a transportable exhausting force. How ceaselessly you replace your backups relies most commonly for your workload. In different phrases, the extra paintings you do, the extra widespread backups are required (e.g. day-to-day backups, weekly backups, and so on.).
In contrast to bodily garage drives, cloud storage is according to faraway servers you’ll get right of entry to from any instrument anyplace on this planet. You’ll be able to additionally percentage this get right of entry to together with your coworkers, staff, or employers. As well as, the danger of the garage unit being broken and inflicting a lack of information is a long way lower than with bodily garage drives that you just stay with you.
These days, a lot of cloud garage services and products are to be had, all of which range in capability availability, options, and worth. The preferred of those services and products are Google Pressure, Dropbox, Microsoft OneDrive, Apple iCloud Pressure, and IDrive.
Our recommendation? Put money into a extremely safe cloud garage strategy to safeguard your information, and take note to secure yourself on the cloud.
Uninterested in subpar degree 1 WordPress website hosting give a boost to with out the solutions? Check out our world-class give a boost to staff! Check out our plans
10. Use Encrypted Document Sharing
All main working methods lately include a integrated encryption device that permits you to encrypt all of the recordsdata at the instrument. On the other hand, you must permit it your self, as this device isn’t activated by means of default. It’s extra necessary to encrypt the recordsdata shared between you and your coworkers/staff/employers.
Those recordsdata are out there by means of a lot of events (the folk you’re sharing them with), and therefore they’re on the possibility of being uncovered to unwanted breaches.
We’re no longer pronouncing that encrypting your recordsdata will utterly save you unhealthy actors from getting their arms for your information, but it surely’ll indisputably lower their probabilities very much. And even though they do get right of entry to the ideas, it’ll be encrypted, which can make it tricky to use.
11. Set Up Two-Issue Authentication
Two-factor authentication (2FA) is a fairly new safety measure that many services and products are turning to to additional safe customers’ accounts. It calls for an extra verification step to both check in to an account or carry out a transaction (like monetary services and products).
For example, whilst you take a look at to shop for one thing on-line the usage of your bank card, some card services and products require you to go into a one-time password (OTP) that’s despatched on your telephone by the use of textual content message. To finish your transaction, you should then input this code to finish your acquire as one of those safety verification. This is helping to forestall unauthorized transactions.
A identical manner is utilized in many instances, akin to whilst you overlook your password and want to reset it. Some services and products follow this system by means of default, whilst others provide the solution to make the most of or disable it.
On every occasion triggered, it’s extremely advisable to agree to make use of 2FA to additional safe your entire accounts.
12. Use Robust Passwords
Whether or not for your telephone or laptop, you need to use extremely unpredictable passwords that best you’ll take note. They don’t should be lengthy, however they do should be as complicated as conceivable. Correct password control is without doubt one of the maximum necessary work at home safety guidelines you’ll obtain.

A powerful password accommodates a couple of other personality sorts. (Symbol supply: Pixabay)
This implies they will have to, at a minimal, comprise each numbers and letters. Your passwords will have to comprise a mixture of uppercase letters, lowercase letters, numbers, and non-alphanumeric characters (query marks, ampersand symbols, and so on.).
Even if we propose having extremely complicated passwords for your entire accounts, you shouldn’t move so complicated that you find yourself forgetting the passwords you place.
It’s additionally necessary to steer clear of the usage of a unmarried password for your entire accounts. If a couple of passwords are too tricky to bear in mind, you’ll at all times use a password manager.
A competent password supervisor is helping you place up robust passwords throughout all accounts and makes it simple to publish your login credentials to any web site — all with out you having to bear in mind your passwords your self. Those managers additionally facilitate the method of periodically updating your passwords.
Password managers can be utilized on a private or company degree, serving to your entire staff stay their accounts safe and circumventing the danger of a number of staff inflicting a knowledge breach by means of making use of susceptible passwords.
13. Watch Out for Phishing Websites
This one would possibly appear rudimentary: Don’t click on on suspicious hyperlinks.
Sounds clear-cut, proper?
Smartly, it’s somewhat extra complicated than that. We’re certain by means of now you received’t fall for the Nigerian prince scam email, however phishers lately are turning into a lot sneakier.
Whilst operating, you will have to best click on on hyperlinks associated with paintings and from relied on assets. If an e mail appears to be like suspicious in any respect, don’t open it. And for those who’re desirous about one thing you won, akin to a hyperlink claiming to comprise necessary COVID-19 data, take a look at with relied on assets first (e.g. WHO, CDC, and so on.).It’s additionally necessary to discover ways to establish a safe web page.
In case your paintings calls for analysis and skimming unknown web pages, don’t be tempted by means of the other commercials displayed on the ones web pages. Simply stick with your goal data and go away the web page.
14. Lock Your Units
This recommendation is going for each your smartphone and your laptop. On every occasion you’re no longer the usage of them, at all times stay them locked with a password. Some telephones lately even use fingerprint popularity for unlocking along with passwords. Others use patterns, facial popularity, and a number of other different strategies.
Once we labored in places of work, we have been at all times required to fasten our place of job computer systems once we weren’t provide to forestall unauthorized get right of entry to and our paintings data from being compromised.
This additionally applies when at house, however for various causes. For example, whilst you’re no longer operating, you wouldn’t need your youngsters getting access to your laptop and messing up your paintings. Be sure you use robust passwords when locking your units.
15. Use More than one E mail Addresses
Identical to the usage of separate units for paintings and private use, the similar is going for e mail addresses. Having a separate e mail account to your paintings and any other to your non-public use is necessary to steer clear of any of the accounts being affected if the opposite turns into compromised in any respect.
It additionally makes you glance extra skilled, particularly for those who’re a freelancer coping with other shoppers. Let’s be fair. We’ve all been at that position of getting an embarrassing non-public e mail cope with at one level in our lifestyles. This was once amusing when the usage of it for social media or college, however that’s a special tale in a piece surroundings.
It doesn’t should be simply an account for paintings and any other for private use. You’ll be able to have a number of other accounts for various functions. For example, you’ll have an account for paintings, any other for funds (banks, cash transfers, and so on.), one for social media, and one for all different non-public makes use of.
The extra accounts you utilize, the extra safe you’ll be. On the other hand, be sure to not overdo it and finally end up forgetting passwords, the e-mail addresses themselves, or getting puzzled about which email address is ready for which goal.
16. Permit Far flung Wipe
This selection is not only helpful to your paintings units but additionally to your non-public units. Maximum working methods lately include a function that allows you to wipe their complete garage remotely. This turns out to be useful in case your instrument is misplaced or stolen to stay your entire information from falling into the fallacious arms.
Sooner than enabling this option or the usage of it, just remember to have up to date backups on a separate instrument or cloud-based (as prior to now discussed). In case your instrument will get misplaced or stolen and this option is enabled, as soon as the instrument is grew to become on and attached to the web, you’ll be capable to delete all of the information on it from another instrument, from anyplace on this planet.
17. Watch Out for 3rd-Birthday celebration Apps
For sure no longer all of the apps you utilize for paintings are created by means of your corporate, and also you most likely depend on a couple of third-party apps. You’ll be able to’t at all times make sure that if those apps, or third-party provider suppliers, are taking the similar safety precautions as you, and so it’s extremely advisable to make certain that the apps you utilize are devoted.
The easiest way to understand if those apps are secure to make use of or no longer is to view their safety rankings on overview web pages. It’s like doing a background take a look at for a possible consumer or business partner. There are a lot of well known web pages in the market which are specialised in all these opinions.
18. Permit Get right of entry to Keep watch over
Get right of entry to keep watch over is a basic component of information safety, most significantly with faraway operating. It’s a solution to make sure that staff are certainly who they are saying they’re. Relating to operating from house, logical get right of entry to keep watch over will have to be a most sensible precedence.
Via logical get right of entry to keep watch over, we seek advice from putting in place an automatic machine that may keep watch over a person’s talent to get right of entry to the corporate’s machine assets akin to networks, programs, and databases. The machine can mechanically establish, authenticate, and authorize customers making an attempt to get right of entry to it.
Via just about proscribing get right of entry to to an organization’s information, you’ll safe your enterprise and decrease cybersecurity threats like information breaches and knowledge leaks.
19. Flip Off Community Title Broadcasting
When putting in place your WiFi community at house, you’ll select to have the community identify visual for any person that has the WiFi grew to become on on their instrument or have it invisible, and to glue, the person has to kind within the identify of the community (turning off community identify broadcasting).
If anyone with unhealthy intentions can’t see your community, they received’t attempt to hack it. Step one to hacking a community is with the ability to see this community. If that function is grew to become off, the danger of it being hacked decreases very much.
20. IT Strengthen and Cyber Safety Coaching for Workers
A phrase to the smart: Don’t skip your corporate’s cybersecurity training. That is so necessary, particularly in case your corporate has shifted to operating remotely from house.
Firms should no longer forget about offering helpful cybersecurity coaching periods for his or her staff in the event that they wish to stay their trade afloat all through those exhausting occasions. As an worker, it’s necessary to wait the ones safety periods and observe your corporate’s cybersecurity insurance policies to give protection to your self and your corporate from any destructive cyber threats.
Abstract
To wrap up, organizations and staff should take work at home safety dangers very severely.
Even if operating from house has confirmed to achieve success, extra productive, and extra handy, with out taking right kind cybersecurity measures, it will possibly transform an actual nightmare for workers and companies.
On the other hand, for those who observe the safety guidelines mentioned above, you’ll revel in a secure and environment friendly faraway operating enjoy.
Were given any questions left about learn how to stay your information secure whilst operating from house? Let’s speak about this within the feedback phase!
The submit 20 Work from Home Security Tips to Protect Your Data in 2021 seemed first on Kinsta.
WP Hosting


