Has your WordPress website online been hacked?
Hackers will steadily set up a backdoor to verify they are able to get again in even after you protected your website online. Until you’ll take away that backdoor, there’s no preventing them.
On this article, we’ll display you how you can discover a backdoor in a hacked WordPress website and attach it.
The best way to Inform if Your Web site Has Been Hacked
In case you are operating a WordPress website, then you want to take safety significantly. That’s as a result of internet sites are attacked a median of 44 instances on a daily basis.
You’ll be able to be told best possible practices to stay your website protected in our ultimate WordPress security guide.
However what in case your website has already been hacked?
Some signs your WordPress site has been hacked come with a drop in website online site visitors or efficiency, added unhealthy hyperlinks or unknown recordsdata, a defaced house web page, an incapacity to log in, suspicious new consumer accounts, and extra.
Cleansing up a hacked website online can also be extremely painful and hard. We take you in the course of the procedure step-by-step in our novice’s information to fixing your hacked WordPress site. You will have to additionally make sure to scan your site for any malware that the hackers left.
And don’t omit to near the backdoor.
A wise hacker is aware of that you simply’ll ultimately blank up your website online. The very first thing they may do is set up a backdoor, so they are able to sneak again in after you protected the entrance door on your WordPress website online.
What Is a Backdoor?
A backdoor is code added to a website online that permits a hacker to get right of entry to the server whilst closing undetected, and bypassing the traditional login. It lets in a hacker to regain get right of entry to even after you in finding and take away the exploited plugin or vulnerability on your website online.
Backdoors are the next move of a hack after the consumer has damaged in. You’ll be able to find out how they are going to have executed that during our information on how WordPress sites get hacked and how to prevent it.
Backdoors steadily continue to exist WordPress upgrades. That implies your website will stay inclined till you in finding and attach each backdoor.
How Do Backdoors Paintings?
Some backdoors are merely hidden admin usernames. They let the hacker log in as standard by way of typing a username and password. Since the username is hidden, you’re now not even mindful that any person else has get right of entry to on your website online.
Extra advanced backdoors can permit the hacker to execute PHP code. They manually ship the code on your website online the usage of their internet browser.
Others have a complete fledged consumer interface that permits them to ship emails as your WordPress hosting server, execute SQL database queries, and a lot more.
Some hackers will go away multiple backdoor record. When they add one, they are going to upload any other to make sure their get right of entry to.
The place Are Backdoors Hidden?
In each case we’ve discovered, the backdoor was once disguised to appear to be a WordPress record. The code for backdoors on a WordPress website are maximum repeatedly saved within the following places:
- A WordPress theme, however almost certainly now not the the only you’re these days the usage of. Code in a theme isn’t overwritten whilst you replace WordPress, so it’s a excellent position to position a backdoor. That’s why we propose deleting all inactive subject matters.
- WordPress plugins are any other excellent position to cover a backdoor. Like subject matters, they’re now not overwritten by way of WordPress updates, and plenty of customers are reluctant to improve plugins.
- The uploads folder might include masses or hundreds of media recordsdata, so it’s any other excellent position to cover a backdoor. Bloggers virtually by no means test its contents as a result of they simply add a picture after which use it in a publish.
- The wp-config.php record accommodates delicate knowledge used to configure WordPress. It’s some of the extremely focused recordsdata by way of hackers.
- The wp-includes folder accommodates PHP recordsdata required for WordPress to run correctly. It’s any other position that we discover backdoors as a result of maximum website online homeowners don’t test to look what the folder accommodates.
Examples of Backdoors We’ve Discovered
Listed below are some examples of the place hackers have uploaded backdoors. In a single website we wiped clean up, the backdoor was once within the wp-includes folder. The record was once known as wp-user.php, which appears to be like blameless sufficient, however that record doesn’t in truth exist in an ordinary WordPress set up.
In any other example, we discovered a PHP record named hi.php within the uploads folder. It was once disguised because the Hi Dolly plugin. What’s unusual is that the hacker put it within the uploads folder as an alternative of the plugins folder.
We’ve additionally discovered backdoors that don’t use the .php record extension. One instance was once a record named wp-content.previous.tmp, and we’ve additionally discovered backdoors in recordsdata with a .zip extension.
As you’ll see, hackers can take very inventive approaches when hiding a backdoor.
Usually, the recordsdata had been encoded with Base64 code that may carry out all varieties of operations. For instance, they are able to upload unsolicited mail hyperlinks, upload further pages, redirect the primary website to spammy pages, and extra.
With that being stated, let’s check out how you can discover a backdoor in a hacked WordPress website and attach it.
The best way to Discover a Backdoor in a Hacked WordPress Web page and Repair It
Now you recognize what a backdoor is and the place it could be hidden. The tough phase is discovering it! After that, cleansing it up is as simple as deleting the record or code.
1. Scan for Probably Malicious Code
The best way to scan your website online for backdoors and vulnerabilities is with a WordPress malware scanner plugin. We advise Securi as it helped us block 450,000 WordPress attacks in 3 months, together with 29,690 backdoor comparable assaults.
They provide a free Sucuri Security plugin for WordPress that allows you to scan your website online for not unusual threats and harden your WordPress safety. The paid version features a server aspect scanner that runs as soon as every day and appears for backdoors and different safety problems.
Be informed extra in our information on how to scan your WordPress site for potentially malicious code.
2. Delete Your Plugins Folder
Looking via your plugin folders on the lookout for suspicious recordsdata and code is time eating. And since hackers are so sneaky, there’s no ensure you’ll discover a backdoor.
The most productive factor you’ll do is delete your plugins listing, after which reinstall your plugins from scratch. That is the one solution to know needless to say that there are not any backdoors for your plugins.
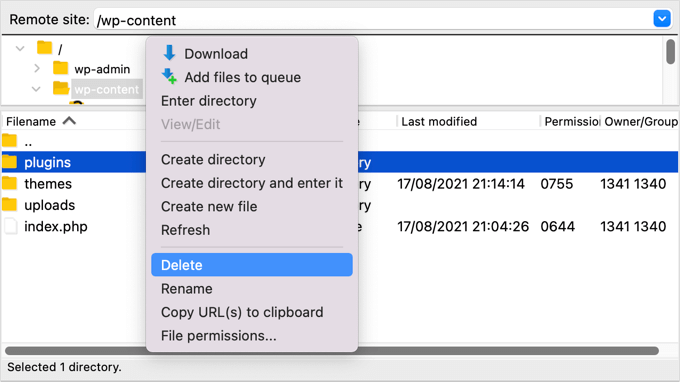
You’ll be able to get right of entry to your plugins listing the usage of an FTP client or your WordPress host’s record supervisor. When you haven’t used FTP ahead of, then you might wish to see our information on how to use FTP to upload files to WordPress.
It is important to use the device to navigate on your website online’s wp-content folder. As soon as there, you will have to proper click on at the plugins folder and make a choice ‘Delete’.
3. Delete Your Topics Folder
In the similar approach, as an alternative of spending time on the lookout for a backdoor amongst your theme recordsdata, it’s higher simply to delete them.
After you delete your plugin folder, merely spotlight the subject matters folder and delete it in the similar approach.
You don’t know whether or not there was once a backdoor in that folder, but when there was once, it’s long gone now. You simply stored time and also you eradicated an additional level of assault.
Now you’ll reinstall any subject matters that you want.
4. Seek the Uploads Folder for PHP Recordsdata
Subsequent, you will have to have a look in the course of the uploads folder and make certain that there are not any PHP recordsdata within.
There’s no excellent reason why for a PHP record to be on this folder as it’s designed to retailer media recordsdata equivalent to pictures. When you discover a PHP record there, then it will have to be deleted.
Just like the plugins and subject matters folders, you’ll in finding the uploads folder within the wp-content folder. Throughout the folder you’ll in finding a couple of folders for each and every 12 months and month you will have uploaded recordsdata. It is important to test each and every folder for PHP recordsdata.
Some FTP shoppers be offering equipment that may seek the folder recursively. For instance, in the event you use FileZilla, then you’ll proper click on the folder and make a choice ‘Upload recordsdata to queue’. Any recordsdata present in any subdirectories of the folder can be added to the queue within the backside pane.
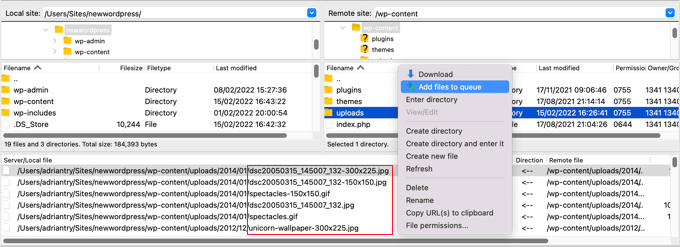
You’ll be able to now scroll in the course of the record on the lookout for recordsdata with the .php extension.
Then again, complex customers who’re accustomed to SSH can write the next command:
in finding uploads -name "*.php" -print
5. Delete the .htaccess Report
Some hackers might upload redirect codes on your .htaccess file that may ship your guests to another website online.
The use of an FTP shopper or record supervisor, merely delete the record out of your website online’s root listing, and it’ll be recreated mechanically.
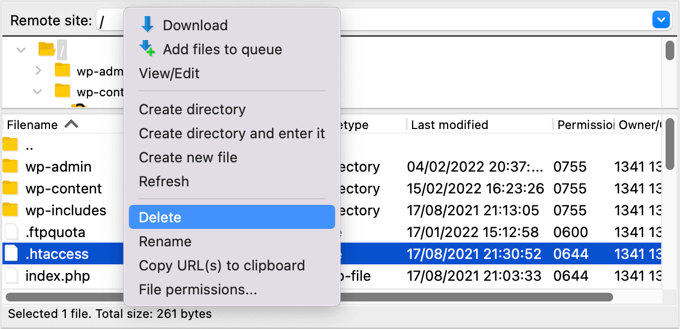
If for some reason why it isn’t recreated, then you definately will have to cross to Settings » Permalinks for your WordPress admin panel. Clicking the ‘Save Adjustments’ button will save a brand new .htaccess record.
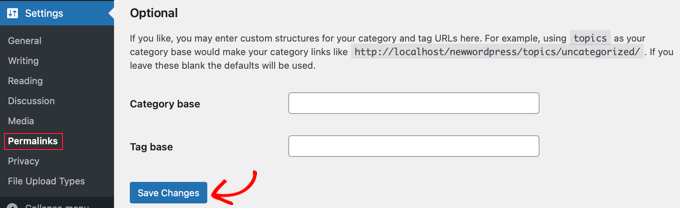
6. Test the wp-config.php Report
The wp-config.php file is a core WordPress record that accommodates knowledge that permits WordPress to be in contact with the database, the safety keys to your WordPress set up, and developer choices.
The record is located for your website online’s root folder. You’ll be able to view the record’s contents by way of deciding on the Open or Edit choices for your FTP shopper.
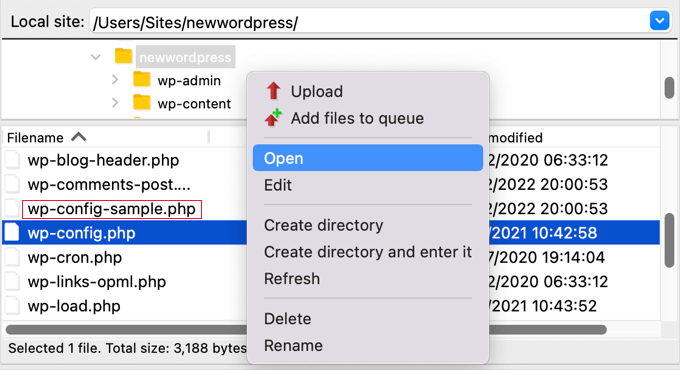
Now you will have to take a look at the contents of the record in moderation to look if there may be anything else that appears misplaced. It could be useful to match the record with the default wp-config-sample.php record which is situated in the similar folder.
You will have to delete any code that you simply’re positive doesn’t belong.
7. Repair a Web site Backup
In case you have been making common backups of your website online and are nonetheless involved that your website online isn’t totally blank, then restoring a backup is a superb answer.
It is important to totally delete your website online after which repair a backup that was once taken ahead of your website online was once hacked. This isn’t an possibility for everybody, however it’ll go away you 100% assured that your website is protected.
For more info, see our novice’s information on how to restore WordPress from backup.
The best way to Save you Hacks within the Long run?
Now that you simply’ve wiped clean up your website online, it’s time to beef up your website’s safety to stop hacks sooner or later. It doesn’t pay to be affordable or apathetic relating to website online safety.
1. Steadily Backup Your Web site
When you don’t already make common backups of your website online, then nowadays is the day to start out.
WordPress does now not include a integrated backup answer. On the other hand, there are a number of nice WordPress backup plugins which let you mechanically backup and repair your WordPress website online.
UpdraftPlus is without doubt one of the best possible WordPress backup plugins. It lets you setup automated backup schedules and can allow you to repair your WordPress website if one thing unhealthy occurs.
Be informed extra in our information on how to backup and restore your WordPress site with UpdraftPlus.

2. Set up a Safety Plugin
You’ll be able to’t in all probability observe the entirety that is going to your website online whilst you’re busy operating on what you are promoting. That’s why we propose you use a security plugin like Sucuri.
We advise Sucuri as a result of they’re excellent at what they do. Primary publications like CNN, USA As of late, PC International, TechCrunch, The Subsequent Internet, and others agree. Plus, we depend on it ourselves to stay WPBeginner protected.
3. Make WordPress Login Extra Safe
It’s additionally vital that you’re making your WordPress login extra protected. One of the best ways to start out is to enforce the use of strong passwords when customers create an account to your website online. We additionally suggest you start using a password manager utility like 1Password.
The following factor you will have to do is add two-factor authentication. This may increasingly offer protection to your website online towards stolen passwords and brute force attacks. It implies that although a hacker is aware of your username and password, they nonetheless received’t be capable to log in on your website online.
In spite of everything, you will have to limit login attempts in WordPress. WordPress lets in customers to go into passwords as again and again as they would like. Locking a consumer out after 5 failed login makes an attempt will considerably scale back a hacker’s probability of figuring out your login main points.
4. Give protection to Your WordPress Admin House
Protective the admin space from unauthorized get right of entry to lets you block many not unusual safety threats. Now we have an extended record of tips about how you can keep WordPress admin safe.
For instance, you’ll password protect the wp-admin directory. This provides any other layer of coverage to an important access level on your website online.
You’ll be able to additionally limit access to the admin area to the IP addresses utilized by your workforce. That is in a different way to fasten out hackers who uncover your username and password.
5. Disable Theme and Plugin Editors
Do you know that WordPress comes with a integrated theme and plugin editor? This simple textual content editor lets you edit your theme and plugin recordsdata immediately from the WordPress dashboard.
Whilst that is useful, it may possibly lead doable safety problems. For instance, if a hacker breaks into your WordPress admin space, then they are able to use the integrated editor to achieve get right of entry to to your entire WordPress knowledge.
After that, they are going to be capable to distribute malware or release DDoS attacks out of your WordPress website online.
To beef up WordPress safety, we propose removing the built-in file editors completely.
6. Disable PHP Execution in Positive WordPress Folders
Via default, PHP scripts can also be run in any folder to your website online. You’ll be able to make your website online extra protected by way of disabling PHP execution in folders that don’t want it.
For instance, WordPress by no means must run code saved for your uploads folder. When you disable PHP execution for that folder, then a hacker received’t be capable to run a backdoor although they effectively uploaded one there.
7. Stay Your Web site As much as Date
Each new model of WordPress is more secure than the former one. Each time a safety vulnerability is reported, the core WordPress workforce works diligently to unlock an replace that fixes the problem.
Which means in the event you don’t seem to be maintaining WordPress up-to-the-minute, then you’re the usage of device with recognized safety vulnerabilities. Hackers can seek for internet sites operating the older model and use the vulnerabilty to achieve get right of entry to.
That’s why you should always use the latest version of WordPress.
Don’t simply stay WordPress up-to-the-minute. You want to just remember to additionally stay your WordPress plugins and themes present.
We are hoping this educational helped you learn to in finding and attach a backdoor in a hacked WordPress website online. You might also wish to be told how to move WordPress from HTTP to HTTPS, or take a look at our record of WordPress errors and how to fix them.
When you favored this newsletter, then please subscribe to our YouTube Channel for WordPress video tutorials. You’ll be able to additionally in finding us on Twitter and Facebook.
The publish How to Find a Backdoor in a Hacked WordPress Site and Fix It first seemed on WPBeginner.
WordPress Maintenance