We communicate so much about how your WordPress web site’s safety isn’t a set-and-forget job. It wishes consistent and vigilant tracking from you, and the task may also be daunting.
In eventualities the place it’s a must to track the safety of a couple of web sites, the Kinsta API may also be one among your key equipment. That is very true the place you arrange a variety of unconnected websites. In those eventualities, you’ll need the automation and visibility the API can provide you with.
On this submit, we’ll discover the use of the Kinsta API for higher safety. The primary focal point will likely be blocking off IPs and tracking their results the use of the quite a lot of endpoints to be had. First, despite the fact that, we will have to believe the tough job of website safety control.
The demanding situations of managing your web site’s safety
As probably the most fashionable content material control gadget (CMS) on the earth, WordPress is a main goal for hackers and malicious actors. On account of this, WordPress is scorching on its core safety.
Whilst the numbers glance just right on paper – round 3 % of websites have some more or less an infection or blocklisted assets – this doesn’t imply you will have to calm down. If truth be told, there are many threats to believe with regards to your WordPress web site:
- Brute pressure assaults
- SQL injection
- Pass-site scripting (XSS)
- Malware infections
- Disbursed Denial of Carrier (DDoS) assaults
Given the complicated array of assaults, managing the safety of a unmarried WordPress website may also be difficult sufficient. Then again, while you’re accountable for a couple of websites, that complexity and scope multiplies. A community of websites will all the time desire a provide and proactive solution to safety tracking. That is even more difficult when you arrange a batch of websites with none connection.
As such, an effective and efficient option to track and safe each and every website you take care of may have mega price. Kinsta may give this to each and every buyer.
How the Kinsta API can improve your website’s safety
Without reference to the plan you’re on, each and every Kinsta buyer has get admission to to the overall Kinsta API. This tough software allows you to engage along with your websites in various programmatic tactics. Many various endpoints are to be had that ‘hook into’ facets of our webhosting, this means that you’ve gotten a robust option to deal with safety for your entire websites.
The Kinsta API allows you to automate quite a lot of security-related duties, and there are many related endpoints:
- Throughout the Web site Equipment, you’ll fetch and replace IPs for your blocklist.
- There’s an endpoint to have a look at and arrange your website’s error and get admission to logs.
- You’ll be able to take hold of analytics from every of your websites due to a handful of endpoints that fetch metrics on efficiency.
Whilst you’ll in finding those equipment throughout the MyKinsta dashboard, there are many the explanation why we provide a programmatic possibility, too. In some ways, the Kinsta API provides you with a number of benefits over the dashboard:
- Automation. You’re in a position to automate safety duties by means of writing scripts or the use of third-party equipment. It will save time and scale back handbook mistakes.
- Bulk operations. The API allows you to perform safety duties on a couple of websites without delay. For those who’re a part of an company otherwise you broaden WordPress web sites for a residing, this facet will likely be helpful.
- Integration. For those who already use a collection of safety equipment you favor, the Kinsta API will permit you to combine them into your setup. This permits you to change into your safety provision into one thing distinctive on your website.
Sufficient communicate, despite the fact that – let’s get into the nuts and bolts of the use of the Kinsta API to paintings with IP addresses. We’ll get started with easy duties and take a look at complicated programs later.
Enforcing IP restrictions with the Kinsta API
Some of the simple tactics to strengthen your website’s safety is thru IP restriction. This permits you to lower the pinnacle off the snake and forestall get admission to on your website altogether. The primary get advantages this is brute pressure assault mitigation.
Whilst the MyKinsta dashboard allows you to paintings along with your blocklist, the Kinsta API has better flexibility if you wish to have it. Let’s believe a state of affairs the place you’re a WordPress company managing a couple of Jstomer websites on one among our Kinsta Company plans.
The use of the Kinsta API to limit IP addresses
First, you’ll have an inventory of IP addresses you need to limit. Our documentation has a few strategies for this, comparable to the use of analytics to root out addresses, making plenty of uncached requests in a little while span.
From right here, you’ll start to use the Kinsta API to limit them. First off, you need to use the Environments endpoint to fetch an inventory of websites. This will likely come with each your reside and staging websites:
const siteId = 'YOUR_site_id_PARAMETER';
const resp = anticipate fetch(
`https://api.kinsta.com/v2/websites/${siteId}/environments`,
{
approach: 'GET',
headers: {
Authorization: 'Bearer '
}
}
);
const knowledge = anticipate resp.textual content();
console.log(knowledge);
Subsequent, you’ll use the Denied IPs endpoint to make a GET request that returns your present blocklist in JSON structure. The reaction will come with an array of blocked IP items:
{
- "surroundings": [
"id": "abc123",
"ip-list": [
"192.168.1.1",
]
}
}
The related PUT request will permit you to upload an IP on your blocklist, for which you’ll wish to specify the surroundings ID:
const resp = anticipate fetch(
`https://api.kinsta.com/v2/websites/equipment/denied-ips`,
{
approach: 'PUT',
headers: {
'Content material-Kind': 'utility/json',
Authorization: 'Bearer '
},
frame: JSON.stringify({
environment_id: '54fb80af-576c-4fdc-ba4f-b596c83f15a1',
ip_list: ['127.0.0.1']
})
}
);
const knowledge = anticipate resp.json();
console.log(knowledge);
A a success addition will go back a 200 reaction code, together with outcome: null inside a JSON document. It’s essential additional automate all of the procedure with a script or software so as to run it every time it’s a must to replace the blocklist once more.
Tracking web site process with the Kinsta API
Enforcing preventive safety features comparable to IP restrictions is superb, however it’s additionally a very powerful to observe your website’s process for attainable safety threats. You’ll be able to glance out for a variety of key signs for every of your websites:
- Abnormal visitors patterns or quantity spikes
- The frequency of any failed login makes an attempt
- Common suspicious person conduct
- Inconsistent website efficiency or atypical downtime patterns.
The MyKinsta dashboard can ship you real-time notifications and indicators on many facets of your website. This will let you step into motion when there’s a possible safety factor.
The Kinsta API has a number of endpoints that permit you to retrieve and glance over your website’s logs and extra. You’ll additionally be capable of arrange computerized tracking and alerting programs if you want that’s distinctive on your wishes.
Discovering malicious process with website logs and metrics
Let’s believe a state of affairs the place your company wishes to observe suspicious process on a person Jstomer website. There are a couple of approaches you’ll take for proactive tracking the place you don’t have a notification as a kick off point.
Once more, you’ll wish to fetch your record of environments, because the endpoints require an ID. After you have this, you’ll check out the logs endpoint. The request has two required fields:
file_nameaccepts a string containing theerror,get admission to, orkinsta-cache-perflogs.strainsallows you to specify the collection of strains the request returns from the log, which should be underneath 20,000.
This will let you determine whether or not there’s a explanation why for fear. The deeper insights, due to the metrics endpoint, can lend a hand fill within the blanks. The metrics you select to have a look at is determined by the particular scenario.
As an example, you’ll take a look at bandwidth to be sure to aren’t being hit with a coordinated assault on a website. The question parameters permit you to set a time-frame get started and finish level, in addition to an period time. The JSON go back provides you with bandwidth main points for the particular website:
{
"app": {
"identification": "54fb80af-576c-4fdc-ba4f-b596c83f15a1",
"display_name": "my-app",
"metrics": {
"time-frame": {
"get started": "1679587045511",
"finish": "1679587045511"
},
"bandwidth": [
{
"time": "1679587045511",
"price": "price"
}
…There are many different metrics to be had, such because the collection of HTTP requests according to minute and the reasonable reaction time. Your task is to have a look at those metrics and the knowledge throughout the logs to spot any suspicious process or attainable safety threats.
If you wish to have visualization, that is the place the Kinsta APM can turn out to be useful:
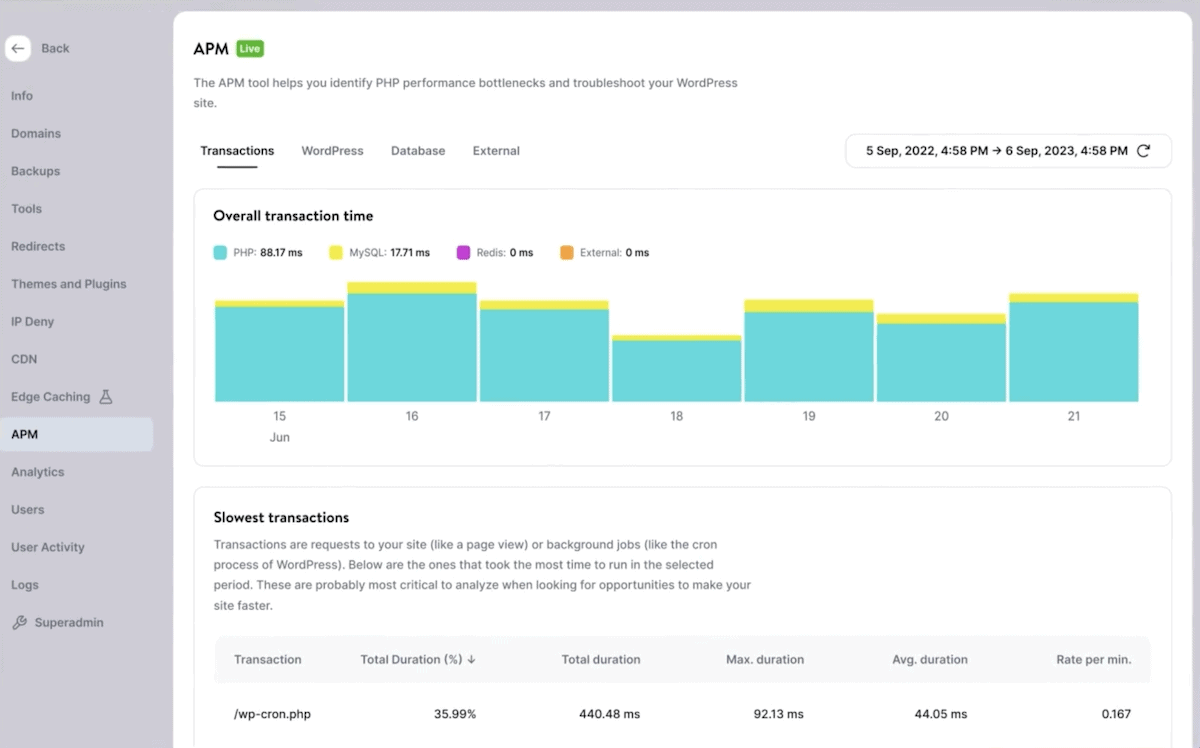
Combining all of Kinsta’s equipment—the API, MyKinsta dashboard, and APM—you’ll hit upon and reply to attainable safety problems temporarily and reduce the danger of everlasting harm on your website and its popularity.
Automating safety escalation the use of the Kinsta API and MyKinsta
Automating your safety workflow can provide your responses extra potency and mobilization. Whilst proactive tracking is the best option to stay your websites safe, every now and then a reactive way is vital.
That is every other space the place computerized notifications turn out to be useful. While you obtain a notification from Kinsta, you’ll spring into motion to get to the bottom of the problem. Then again, not like different safety duties, the Kinsta API isn’t a part of the triage this time.
As an alternative, MyKinsta will likely be your information. The Kinsta documentation covers the website tracking notifications at your disposal. There are masses to be had, comparable to website downtime, DNS mistakes, and a lot more.
On the level you determine a risk for your website, you’ll then name at the Kinsta API to deal with the malicious customers. This may well be including IPs to a block record or checking at the backups you’ve gotten in position in case the worst occurs.
There are a few GET requests that can assist you uncover what backups there are. For those who’re lacking one, you’ll make a POST request to start out a handbook backup. It’ll best require the surroundings ID and a reputation for the backup:
const envId = 'YOUR_env_id_PARAMETER';
const resp = anticipate fetch(
`https://api.kinsta.com/v2/websites/environments/${envId}/manual-backups`,
{
approach: 'POST',
headers: {
'Content material-Kind': 'utility/json',
Authorization: 'Bearer '
},
frame: JSON.stringify({
tag: 'my-awesome-backup'
})
}
);
const knowledge = anticipate resp.json();
console.log(knowledge);
The Kinsta API may also permit you to repair a backup. If truth be told, it’s essential to conceive a method that retrieves your website logs, assesses your metrics, makes a backup given your particular parameters and regulations, blocks incoming malicious IPs, after which restores a backup at some degree the place the assaults chill out.
Ceaselessly track the website’s process and iterate for your safety procedure in response to the insights won from the Kinsta API and MyKinsta.
Via automating your safety escalation procedure, you’ll reply to threats extra temporarily and reduce the possible have an effect on of safety incidents for your website.
Just right practices for enforcing API-driven safety features
On every occasion you employ an API, you’re exposing facets of your website to the open internet. On account of this, it’s crucial to apply some conventional and accredited practices to make sure the safety and integrity of your website and knowledge.
There are a couple of key pointers to remember right here. Before everything, you will have to all the time use safe authentication strategies every time you get admission to an API. This may well be an API key, OAuth tokens, or one thing else. Kinsta supplies an API key authentication endpoint for this goal:
const resp = anticipate fetch(
`https://api.kinsta.com/v2/validate`,
{
approach: 'GET',
headers: {
Authorization: 'Bearer '
}
}
);
const knowledge = anticipate resp.textual content();
console.log(knowledge);
Understand that you shouldn’t reveal your API credentials in client-side code or public model keep watch over repositories. That is the place you would have to glance into what your programming language of selection gives. As an example, Python calls from a constants.py module, and PHP makes use of OpenSSL and different modules to give protection to delicate knowledge.
There are a few different vital issues to make, too:
- Knowledge dealing with. Whilst you retrieve delicate knowledge in the course of the Kinsta API, be sure to deal with and retailer that knowledge in a safe means. You’ll additionally need to apply accredited practices for knowledge encryption, get admission to keep watch over, and compliance with any privateness rules.
- Common checking out and updating. Your checking out procedure will have to be steady, and that is one thing you’ll reach with the Kinsta API, too. Those consistent and steady exams and updates be sure that your website and its safety stay efficient towards evolving threats.
After all, following the main of least privilege is near-mandatory while you arrange any degree of get admission to on your workforce or third-party products and services. In a nutshell, best grant the minimal degree of get admission to every person or provider calls for to accomplish duties. What’s extra, overview and revoke any needless permissions regularly.
Reporting on IP restrictions and process tracking
For Jstomer website safety control, it’s nice apply – and as just right as a very powerful – to supply common and clear reporting on how efficient your technique is. Your purchasers deserve to stick within the loop concerning the steps you’re taking to give protection to their websites and the result of your efforts. This is helping to construct agree with and show the price of what you be offering.
As such, you’ll need to be sure that the experiences you ship give as a lot knowledge on your purchasers as conceivable. Kinsta can permit you to pull from a variety of metrics and insights for every particular person website:
- The collection of blocked IP addresses.
- Developments in suspicious process, comparable to failed login makes an attempt or atypical visitors patterns.
- Your website efficiency and uptime metrics. Those may also be indicative of attainable safety problems.
After all, you’ve gotten a lot more to be had. Even so, it’s vital to give those insights in one of the best ways on your purchasers. Listed below are a couple of recommendations on what to incorporate:
- The movements you’ve taken in accordance with recognized threats, comparable to website backups or safety patches.
- Use knowledge visualization equipment to give transparent, out there, and comprehensible knowledge on a website’s safety. Graphs, charts, and dashboards can lend a hand your purchasers stand up to hurry at the present safety provision, and whether or not your efforts are efficient.
- You will have to glance to supply context and explanations for the knowledge you provide. It’s a mistake to think that your purchasers may have a deep technical working out of safety ideas. As an alternative, use undeniable language and supply examples to lend a hand them clutch the importance and gravitas of the metrics and tendencies you’re reporting on.
Total, be offering transparency about any demanding situations or boundaries you come across with the website’s safety. For tough threats or problems, it’s a legitimate thought to be prematurely about it and provide an explanation for what you’re doing to fortify.
That is the place providing suggestions for additional safety enhancements may also be useful. Those will come out of your insights and research. As an example, it would come with ideas for extra safety features, comparable to enforcing two-factor authentication or updating out of date plugins.
Abstract
The Kinsta API has various scope for a mess of website duties. In the case of safety, despite the fact that, it’s a successful option to stay your website and customers secure. It allows you to automate duties comparable to retrieving logs, checking for atypical process, and blocking off IPs mechanically.
We adore the compelling and robust way of hooking the API up with different apps and equipment. This fashion, you’ll have an entire programmatic approach of securing your website. Coupled with the visualization choices in the course of the Kinsta APM, your website can stay secure for a very long time to return.
How do you want to make use of the Kinsta API to control your website’s safety? Please percentage your ideas and insights within the feedback phase under!
The submit Proscribing IPs and tracking process the use of the Kinsta API gave the impression first on Kinsta®.
WP Hosting