As the worldwide pandemic unfold, international locations international had to enter lockdown to stay the virus from spreading. Many firms have been left and not using a different possibility than to shift to on-line paintings.
Operating remotely has its advantages — workers spend much less time commuting and are extra productive. However there also are primary safety demanding situations.
Staff who don’t take the essential precautions can compromise delicate knowledge and go away their corporate at risk of cyber assaults.
This article is going to quilt very important cybersecurity practices for far off groups to observe that may safeguard your corporate towards cyberattacks.
1. Determine a Cybersecurity Coverage
IT groups most often deal with cybersecurity within the place of work. However keeping up knowledge safety turns into tougher with a disbursed group of workers.
In keeping with Verizon’s Information Breach Investigations Record, 85% of knowledge breaches happen as a result of human error. An estimated 36% concerned phishing — an assault the place an e mail or message seems reputable however tips sufferers into revealing private knowledge.
So how are you able to give protection to your company towards such assaults?
Get started via organising a cybersecurity coverage. This file outlines the foundations and security features that every one workers will have to observe.
Cybersecurity insurance policies must quilt the next:
- Applicable use of e mail
- Connecting to public Wi-Fi networks
- Growing robust passwords
- Enabling two-factor authentication
- Dealing with buyer knowledge
- The usage of detachable media
Define the protection protocols that you are expecting workers to agree to. As an example, if far off staff want to get admission to client information, they will have to perceive the stairs they want to take first.
Require all workers to study and signal the cybersecurity coverage, whether or not they’re running remotely or no longer. You should definitely periodically revisit the coverage and replace it when essential.
2. Make Use of VPNs
A part of the attraction of working remotely is the versatility it supplies. Staff can get their paintings accomplished at house or pass to their native cafe for a transformation of surroundings.
But if workers hook up with a public Wi-Fi community, there’s a big safety chance. If the relationship level isn’t safe, hackers can intercept knowledge that passes in the course of the community and thieve confidential knowledge.
In spite of those dangers, 26% of web customers have logged in to a piece e mail account, and 19% have despatched a piece file over public Wi-Fi.
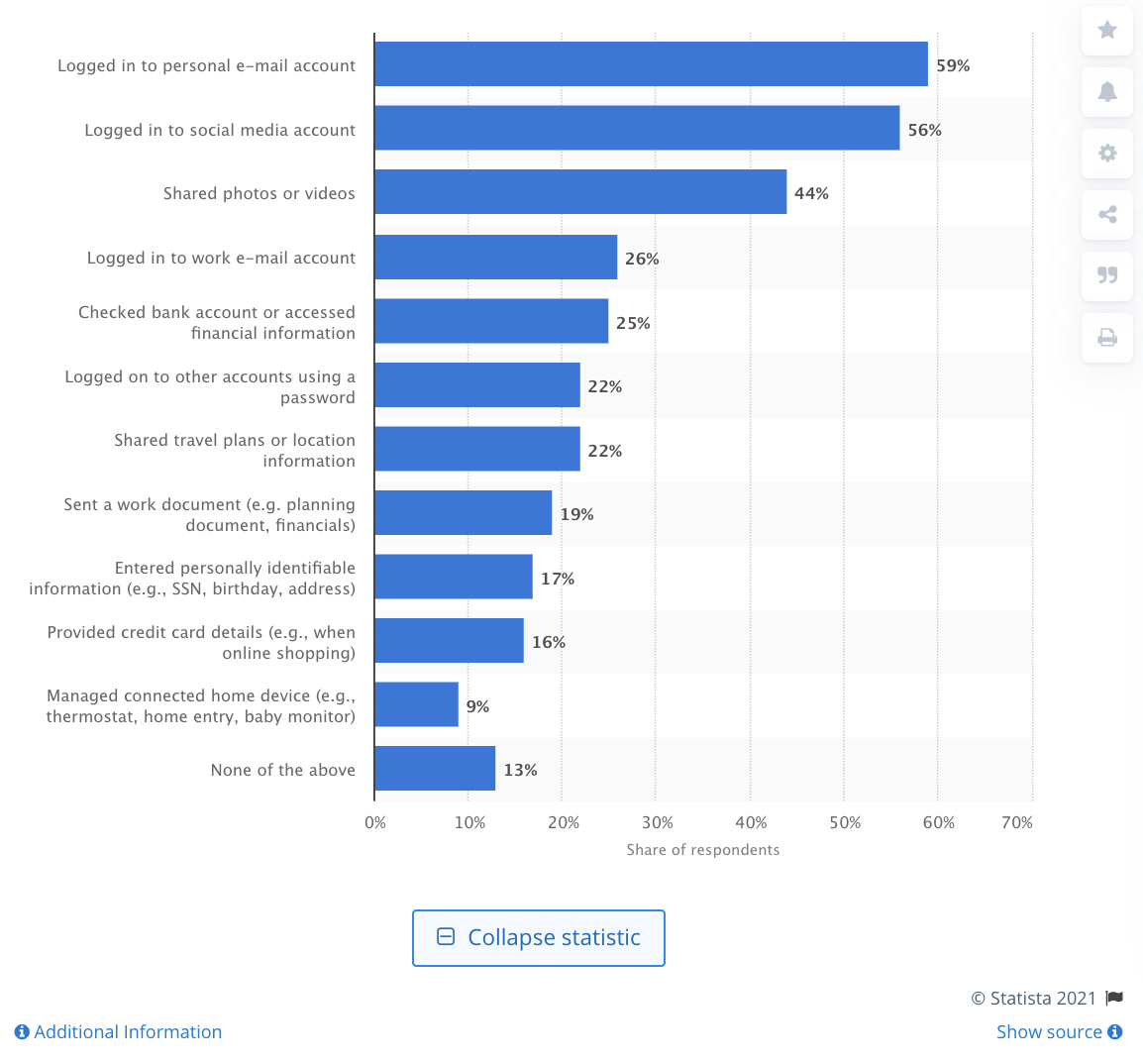
One answer is to use digital personal networks or VPNs — a carrier that may determine a safe and encrypted tunnel between a person’s instrument and the web.
The extent of encryption that top rate VPN suppliers like ExpressVPN supply makes it just about unattainable for any person to trace your on-line actions or view your knowledge.
Make certain that workers go away their VPN on always to make certain that connections are at all times safe.
3. Use Sturdy and Safe Passwords
A not unusual means hackers use to get admission to accounts and thieve knowledge is brute force attacks — making an attempt other combos of passwords till they wager it appropriately.
Passwords act as a primary defensive line towards unauthorized get admission to.
In case your password is “12345,” hackers gained’t have any issues cracking it. A robust password makes it considerably tougher for any person to brute power their manner into your account.
Train far off staff at the significance of the use of robust passwords throughout all their accounts and gadgets. This may lend a hand save you hackers from having access to corporate knowledge.
Sturdy passwords have the next traits:
- No less than 8 characters (extra is healthier)
- A mix of uppercase and lowercase letters
- Inclusion of numbers and particular characters (e.g., @#&$)
Remember to emphasize the significance of the use of other passwords throughout all accounts.
One survey discovered that 39% of on-line customers use the similar passwords for various accounts. A unmarried leak of login credentials for one account can put others in danger.
Imagine the use of a password supervisor. This may make it more straightforward for far off groups to get admission to accounts with no need to keep in mind complicated passwords.
4. Permit Two-Issue Authentication
Even robust passwords aren’t utterly bullet-proof. Hackers can nonetheless get admission to an account if an information breach finds an worker’s username and password.
Two-factor authentication (2FA) provides an additional layer of safety via requiring additional info like a verification code. With out this code, customers can’t get admission to an account even supposing they input the right kind username and password.
The usage of 2FA is valuable at limiting unauthorized get admission to. Sending an SMS code to a restoration telephone quantity blocked 100% of computerized bots and 76% of centered assaults.
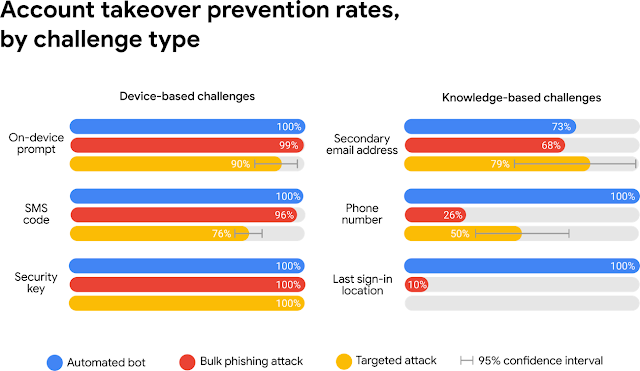
Having to look ahead to and input a verification code would possibly appear to be a minor inconvenience, nevertheless it a ways outweighs the dangers of cybercriminals gaining unauthorized access to an organization account.
Firms can use platforms like spores.app for various duties. Putting in place 2FA might be a lot more straightforward if in case you have one tool that does the entirety.
But when your corporate depends upon many cloud-based products and services and collaboration gear, make sure to arrange 2FA on they all. Use tool like Google Authenticator to generate verification codes.
5. Factor Paintings Units
An very important a part of HR management is putting in workers with the suitable programs and bringing them on top of things. IT groups then configure gadgets and set up antivirus tool to give protection to towards viruses.
Making sure knowledge safety is more straightforward to control when workers are running within the place of work with work-issued gadgets. On the other hand, a possible danger to the corporate’s safety happens when far off workers use their private gadgets to get admission to paintings recordsdata.
Whilst the corporate would possibly observe positive safety protocols, there’s no option to know if far off workers observe the similar procedures with their very own computer systems.
One option to cope with those considerations is to factor paintings gadgets to far off workers. Then, have your IT crew configure and safe the ones gadgets earlier than issuing them out.
Routers provide every other safety vulnerability.
Maximum routers include a default username and password. For those who don’t trade those credentials, hackers can log in and get admission to delicate knowledge.
Have far off staff trade the password for his or her routers. This may occasionally sound evident, however one survey discovered that 18% of respondents didn’t trade the administrator password on their routers.
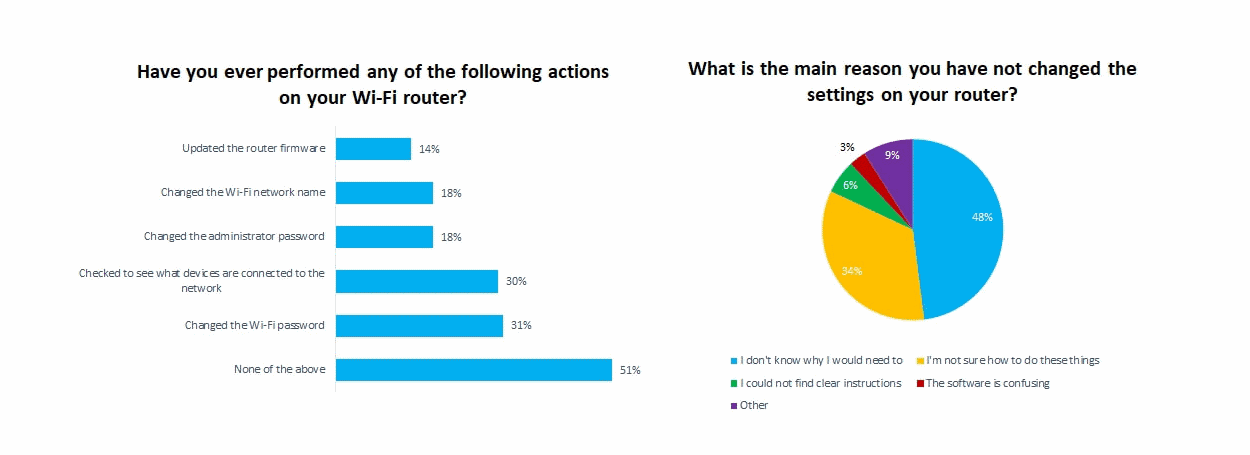
There are different security features that far off groups can take.
Those come with updating the router’s firmware and switching to Wi-Fi Secure Get admission to II (WPA2), a safety same old that encrypts knowledge over wi-fi networks.
6. Create Common Backups
Information loss can disrupt a company’s operations and reason massive monetary losses.
Regardless of what number of precautions you’re taking, your corporate continues to be vulnerable to cyberattacks. Hackers would possibly find a new exploit, or an worker would possibly make a easy mistake.
Your corporate will have to have an efficient restoration device in position, which comes to developing widespread backups of essential recordsdata.
Cybersecurity professionals suggest the “3-2-1 rule” for knowledge backups. This rule states that you simply must:
- Stay a minimum of 3 copies of your knowledge. This prevents a unmarried incident like fires or a {hardware} failure from destroying all of your knowledge. Remember to stay a couple of copies of your backups, whether or not it’s via data center infrastructures, cloud garage, arduous drives, and so forth.
- Retailer backup copies in two codecs. The commonest option to backup knowledge is via the use of an exterior arduous force. The issue, despite the fact that, is that {hardware} can fail through the years. Use a minimum of two several types of garage to your backup copies.
- Stay one reproduction offsite. Storing backups in a single location isn’t a good suggestion for evident causes. Stay a minimum of one reproduction offsite, both within the cloud or every other location (each can be higher).
Protecting common backups protects towards treasured knowledge loss.
Remember to again up essential knowledge a couple of instances every week. For those who ever want to get better knowledge, you’ll be able to at all times repair a backup.
Conclusion
Extra other people these days are running remotely. It’s a pattern that can most probably proceed as extra firms include versatile paintings choices to retain and draw in skill.
The versatility that running from house supplies is without a doubt interesting. However it additionally comes with a number of demanding situations with regards to preserving networks safe.
Observe the cybersecurity practices described right here to give protection to towards cyberattacks and supply a extra safe atmosphere for far off workers.
The submit 6 Essential Cybersecurity Practices for Remote Teams seemed first on Torque.
WordPress Agency