Ultimate 12 months, I won an e mail from my “financial institution” alerting me to suspicious process on my account. The structure and emblem matched different respectable communications I had won from the financial institution, and I used to be naturally alarmed.
However a couple of issues simply didn’t upload up. As an alternative of the use of my title, it addressed me as “Pricey valued buyer.” After that, I used to be meant to ensure my account main points, which appeared opposite to financial institution safety recommendation. The brightest pink flag, although, was once the e-mail deal with that didn’t fit the financial institution’s area.
Scammers have transform moderately sensible. Equipment like generative AI have made it simple for them to imitate the branding, tone, or even the writing taste of respectable corporations.
However there are nonetheless telltale indicators that permit you to determine a phishing strive. Right here, I’ll speak about those indicators and proportion phishing e mail examples that would idiot someone.
What’s a phishing e mail?
A phishing e mail is one of those on-line rip-off that methods recipients into offering delicate data, corresponding to login credentials, bank card numbers, or non-public id main points.
As an example, right here’s an e mail that Debbie Moran, advertising supervisor at RecurPost, won:
Cybercriminals design those emails to seem as though they arrive from professional resources — banks, respectable companies, or well known corporations to create a way of urgency or worry to urged fast motion.
The scammer then makes use of the stolen data to devote fraud or id robbery, get entry to the sufferer’s monetary accounts, make unauthorized purchases, and even release additional phishing assaults towards others.
The Other Kinds of Phishing Emails
Phishing emails are available all sizes and styles, every designed to milk a selected vulnerability or state of affairs.
Every form of phishing e mail exploits particular human characteristics, corresponding to consider, worry, or interest. Listed here are some commonplace sorts, with phishing e mail examples of ways they could glance.
Spear Phishing
Spear phishing objectives particular folks or organizations thru extremely customized emails. Attackers use data amassed from social media or different resources to make the message appear professional.
As an example, right here’s an e mail that Phan Sy Cuong, PR specialist at Superior Reason, the dad or mum emblem of WPBeginner, won. On the time the corporate’s workers won this, they had been running with some other corporate for worker insurance coverage.
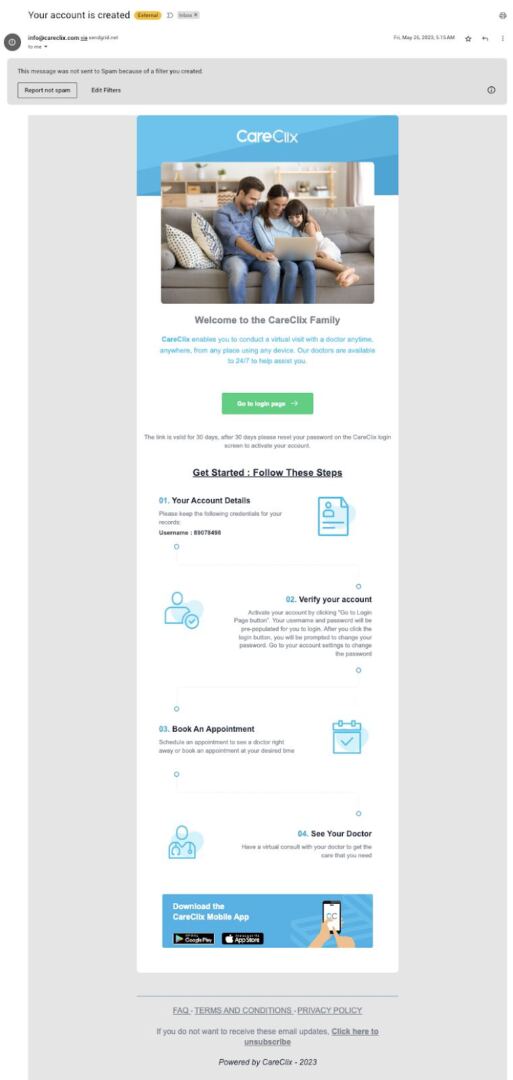
Whilst the design was once skilled sufficient to idiot folks, the great factor is the corporate had assessments and balances.
“On every occasion one thing abnormal pops up, we all the time be in contact in our corporate channel to test if someone’s receiving the similar factor or immediately with the only in fee — on this case, it was once the HR supervisor — to verify it’s one thing from our corporate,” says Cuong.
In keeping with Cuong, the workforce all the time receives a heads-up if one thing is coming. “We had been additionally briefed concerning the insurance coverage we had been in contact with ahead of, so we stated that the only within the e mail wasn’t proper,” Cuong says.
Whaling
A whaling assault is a spear phishing assault that makes a speciality of high-profile objectives like CEOs, CFOs, or different senior executives. The purpose is normally to thieve delicate data from the corporate or to start up fraudulent monetary transactions.
As an example, the accounting division on the cybersecurity corporate Heimdal won this sequence of emails.
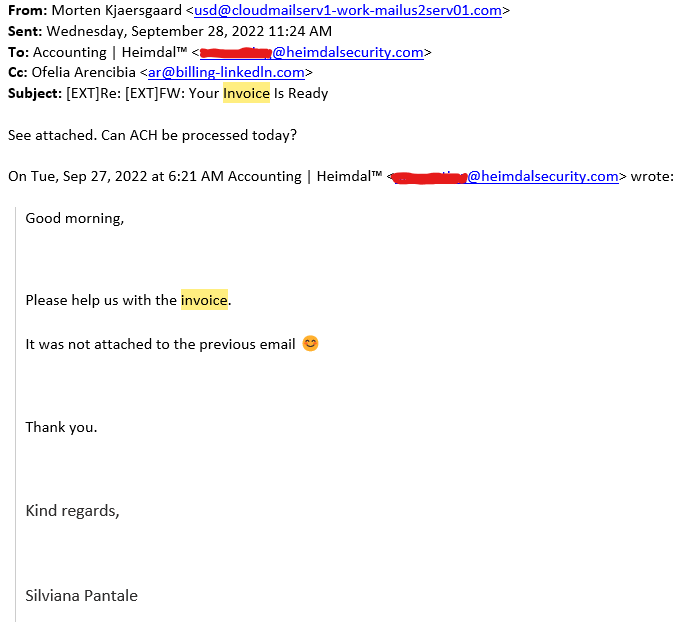
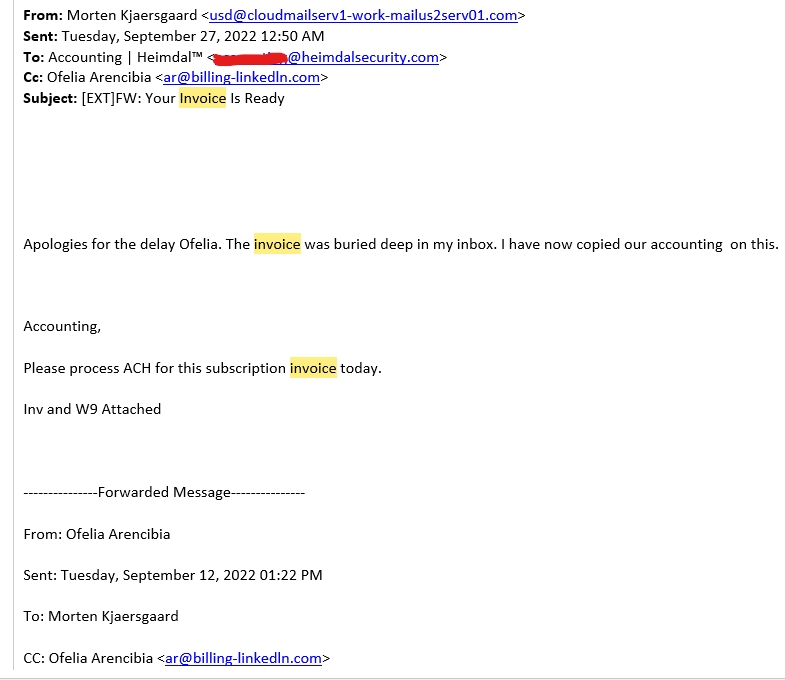

The attacker created two e mail addresses, despatched more than one emails between them, and forwarded them to the corporate’s accounting division. It’s a pleasing trick to create a sequence of emails you ahead for cost.
Valentin Rusu, the pinnacle of study at Heimdal, provides how whaling particularly is “an overly bad development since present safety methods paintings in keeping with a flaw in grammar, suspicious e mail, suspicious hyperlinks, and intent.”
When an e mail doesn’t have any problems like that, a cybersecurity corporate like Heimdal provides consumers a private, adapted neural community that learns from their knowledge and adapts to their e mail conduct.
Rusu provides an instance. As an incident reaction supervisor, Rusu says, it’s commonplace to obtain many malicious URLs and attachments. On the other hand, this isn’t commonplace conduct for a finance division.
“This implies you’ll’t create an e mail product that works for each state of affairs, so we constructed a customized neural community. This non-public AI learns from corporate emails and detects conduct that doesn’t are compatible the patterns,” Rusu says.
Pharming
Pharming redirects customers from professional web pages to fraudulent ones by means of DNS hijacking or poisoning to gather non-public and monetary data. The assault isn’t email-based, but it surely’s incessantly paired with phishing emails.
Instance: An e mail out of your “financial institution” asking you to log in on your account by means of a equipped hyperlink, which then leads you to a faux banking website online that appears similar to the true one.
Clone Phishing
Clone phishing comes to making a just about similar replica of a up to now despatched e mail however with malicious hyperlinks or attachments. The attacker would possibly declare to be resending the e-mail because of a failed supply strive or updating the content material.
As an example, right here’s an e mail imitating a FedEx supply notification e mail.
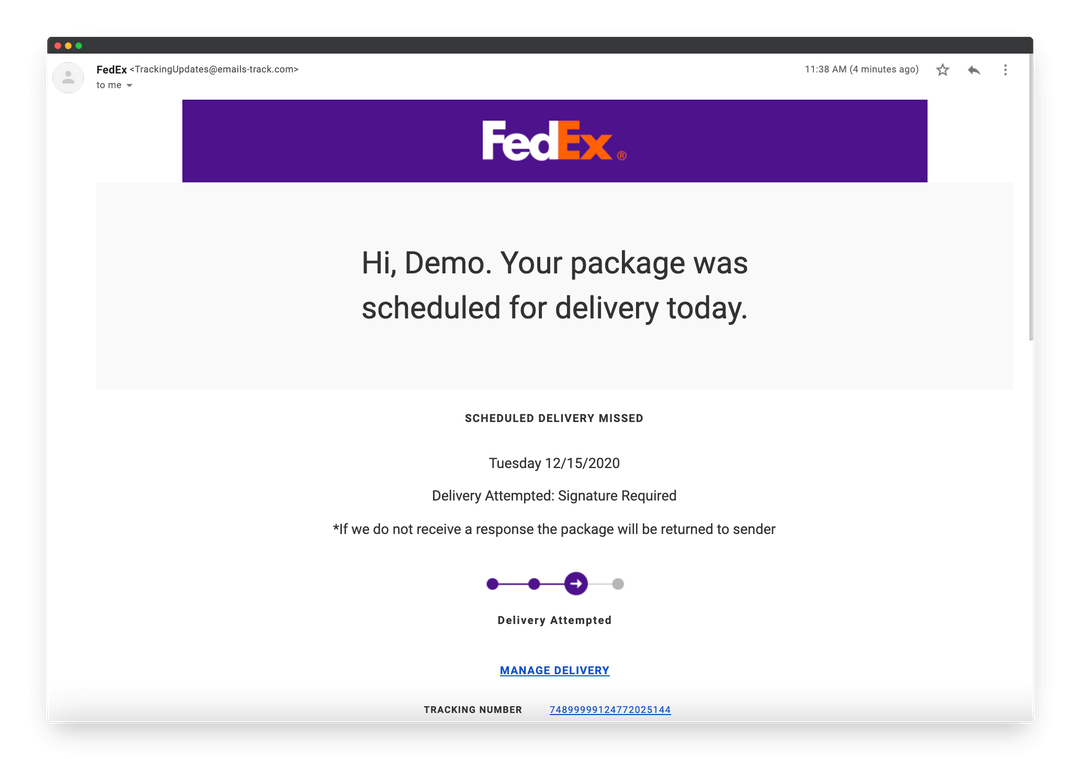
Vishing (Voice Phishing)
Vishing, or voice phishing, makes use of telephone calls as a substitute of emails to rip-off sufferers. It’s value citing as it incessantly enhances e mail phishing.
As an example, a voicemail or direct name claiming to be out of your financial institution, mentioning suspicious process in your account and asking you to name again the use of the equipped quantity, which ends up in a scammer.
Smishing (SMS Phishing)
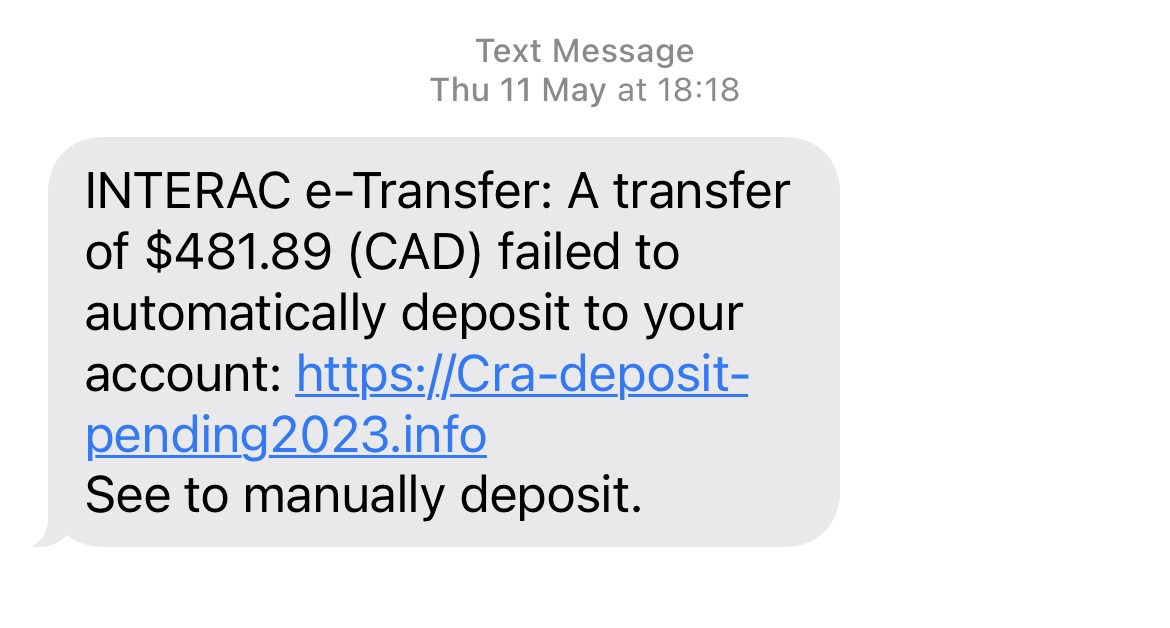
Smishing is very similar to phishing however makes use of SMS texts. It directs customers to malicious web pages or asks them to offer non-public data by means of textual content.
As an example, right here’s a meant e mail from the Canadian Earnings Company that’s attractive me to click on the press with a promise of $400.
Spot a Phishing E mail
Phishing emails have transform truly subtle, particularly since GenAI gear like ChatGPT have made it moderately simple to create customized phishing emails in seconds.
In truth, right here’s an instance from Valentin the use of ChatGPT for a similar:

Frightening, isn’t it? In keeping with Proofpoint’s 2023 State of the Phish document, round 45% of folks don’t know a well-known corporate emblem doesn’t make an e mail protected.
To extend your probabilities of being secure towards such emails, glance out for those six indicators:
1. Suspicious E mail Addresses
You’ve won an e mail that appears love it’s from an organization .
However take a more in-depth have a look at the sender’s e mail deal with and if it’s a jumble of letters or refined misspellings (like “amaz0n.com”), that’s a pink flag. Reputable corporations have e mail addresses that fit their domains.
Reputable corporations additionally don’t use public domain names like @gmail.com, @outlook.com, @yahoo.com, or some other loose e mail carrier for respectable communications.
In case you obtain an e mail claiming to be from a credible corporate but it surely’s despatched from the sort of public domain names, be cautious.
This element is a key indicator in distinguishing between a real e mail and a possible phishing strive.
2. Grammar and Spelling Errors
Ever cracked open an e mail and noticed a typo or two? Positive, all of us make errors, however a message riddled with grammar mistakes and spelling slip-ups indicators a major problem.
Glance out for typos, bizarre grammar, and sentences that don’t sound correct. Additionally, stay a watch out for awkward phraseology or misuse of commonplace phrases — problems like “Pricey valued buyer, verify id through click on underneath.”
Actual companies have proofreaders and spellcheck gear for his or her emails as a result of they know errors don’t make the most productive influence.
3. Unfamiliar Greetings or Signal-offs
If an e mail begins with “Pricey Buyer” or some generic time period as a substitute of your title, it may well be a rip-off. The similar is going for bizarre or overly formal sign-offs. It will glance formal, but it surely’s additionally an indication that the sender doesn’t in fact know you.
Reputable corporations you do industry with have your title of their database. The similar is going for his or her sign-offs too. Stiff sign-offs, like a proper “Cordially” out of your supposedly informal carrier supplier or an abrupt “Thanks” without a follow-up main points, are pink flags.
4. Suspicious Hyperlinks or Attachments
One of the crucial trickiest portions of coping with phishing emails is sketchy hyperlinks and attachments. Click on on them unintentionally, and also you may well be introducing malware on your pc.
All the time test the URL ahead of clicking. If the e-mail says it’s out of your financial institution however the hyperlink issues someplace bizarre (like a random collection of characters or a website online that doesn’t fit the financial institution’s exact URL), that’s your cue to again away.
Additionally, a commonplace trick is to ship a report that says to be an bill, a receipt, or a “must-see” be offering. However the second you open it, it is advisable to be letting malware or an epidemic stroll throughout your device.
The important thing? Hover over hyperlinks to peer the place they’re truly taking you (with out clicking!). And if there’s an attachment you weren’t anticipating, achieve out to the sender thru a unique channel to verify it’s respectable.
5. Requests for Non-public Knowledge
No respected corporate will ask for delicate data by means of e mail. Regardless of how respectable an e mail appears, be mindful this — authentic organizations don’t ask for delicate main points like passwords, bank card numbers, or Social Safety numbers by means of e mail.
As an example, an e mail would possibly say, “We’ve spotted suspicious process in your account. Please verify your password to protected your account.” It’s a entice. Actual banks and firms have protected processes for dealing with those scenarios, and so they unquestionably don’t contain sending delicate data into the e-mail void.
Right here’s what you do: By no means, ever respond with your individual data. In case you’re even a little bit bit involved, cross immediately to the supply. Log into your account throughout the respectable website online or name the respectable touch quantity.
6. Pressing or Threatening Language
Ever gotten an e mail that makes your center skip a beat?
“Fast motion required!” or “Your account has been compromised!” — sounds lovely pressing, proper? However that’s precisely what phishers need. They use pressing or threatening language to make you react with out considering.
As an example, chances are you’ll see words like, “Your account password has expired, replace now ahead of you lose get entry to on your account” or “Try to ship your package deal unsuccessful. Please replace your data inside the subsequent 24 hours.”
Reputable organizations don’t in most cases scare you into motion — they reassure.
As an alternative, achieve out to the corporate immediately the use of touch data you in finding thru respectable channels, no longer e mail. When somebody’s pushing you arduous to behave rapid, it’s most definitely as a result of they don’t need you to suppose an excessive amount of about what you’re doing or visit someone else.
Phishing Emails I May Have Fallen For (And Why I In the end Didn’t)
I’ve noticed a number of convincing phishing e mail examples that can have conned me if no longer for a couple of an important pink flags. Right here, I’ll proportion a few of the ones shut calls and give an explanation for why I in the long run didn’t fall for them.
PayPal
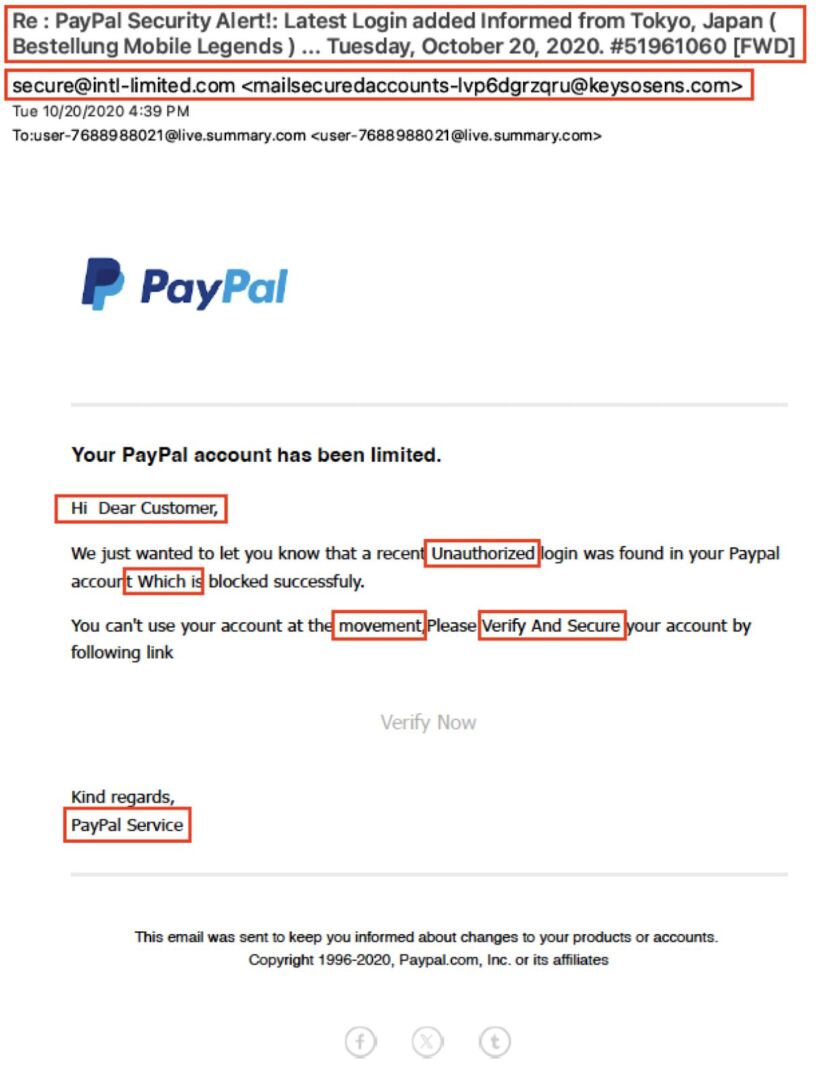
In the beginning look, the e-mail nails PayPal’s branding with the colour scheme and emblem to indicate authenticity at a look. However nearer inspection confirmed a lot of spelling mistakes like “through following hyperlink,” “successfuly,” and “on the motion.”
The greeting was once additionally no longer non-public (“Hello expensive buyer”), which deviates from PayPal’s usual conversation taste. Plus, the sign-off (“PayPal carrier”) lacks the professionalism anticipated from the corporate.
Netflix
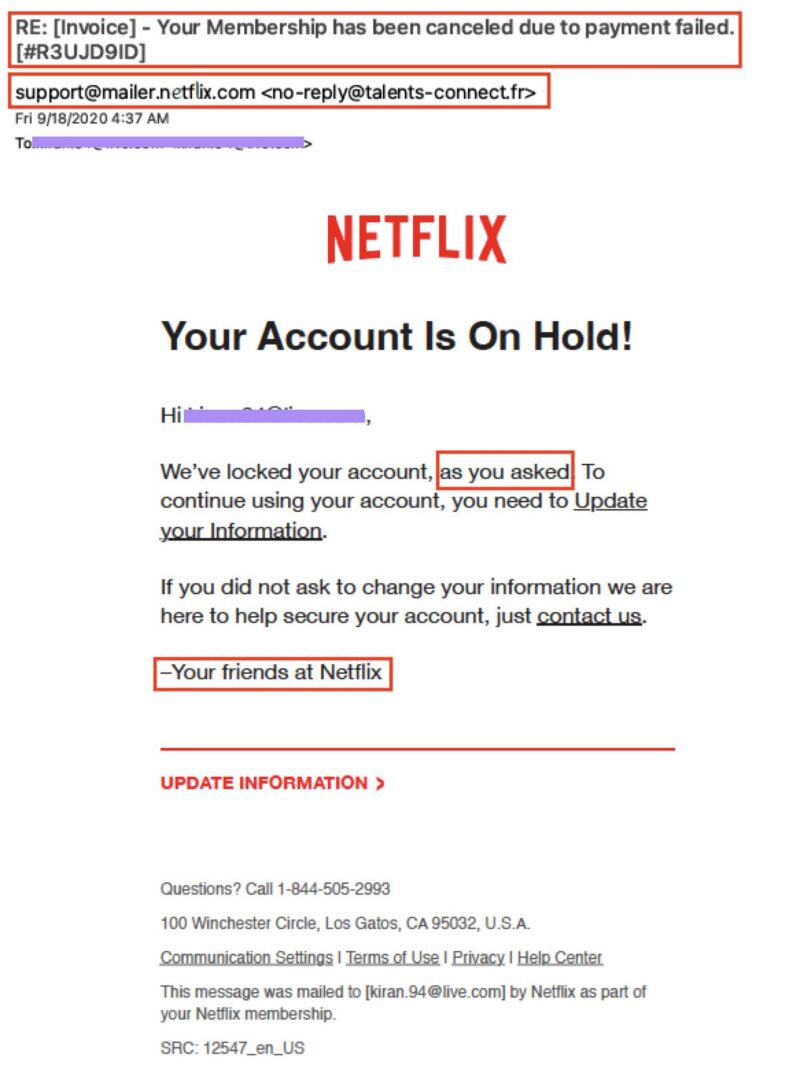
The topic line for this e mail mentioned, “Your Club has been canceled because of cost failed,” which immediately grabbed my consideration.
However the content material of the e-mail contradicted this message, claiming, “We’ve locked your account, as you requested.” This inconsistency was once a transparent warning call.
Aside from this, the last statement, “Your mates at Netflix,” appeared surprisingly casual for respectable Netflix conversation.
Probably the most telling signal of a phishing strive, alternatively, was once the sender’s e mail deal with: [email protected], a website distinctly unrelated to Netflix. Those indicators made it lovely glaring this e mail was once a phishing strive.
Apple
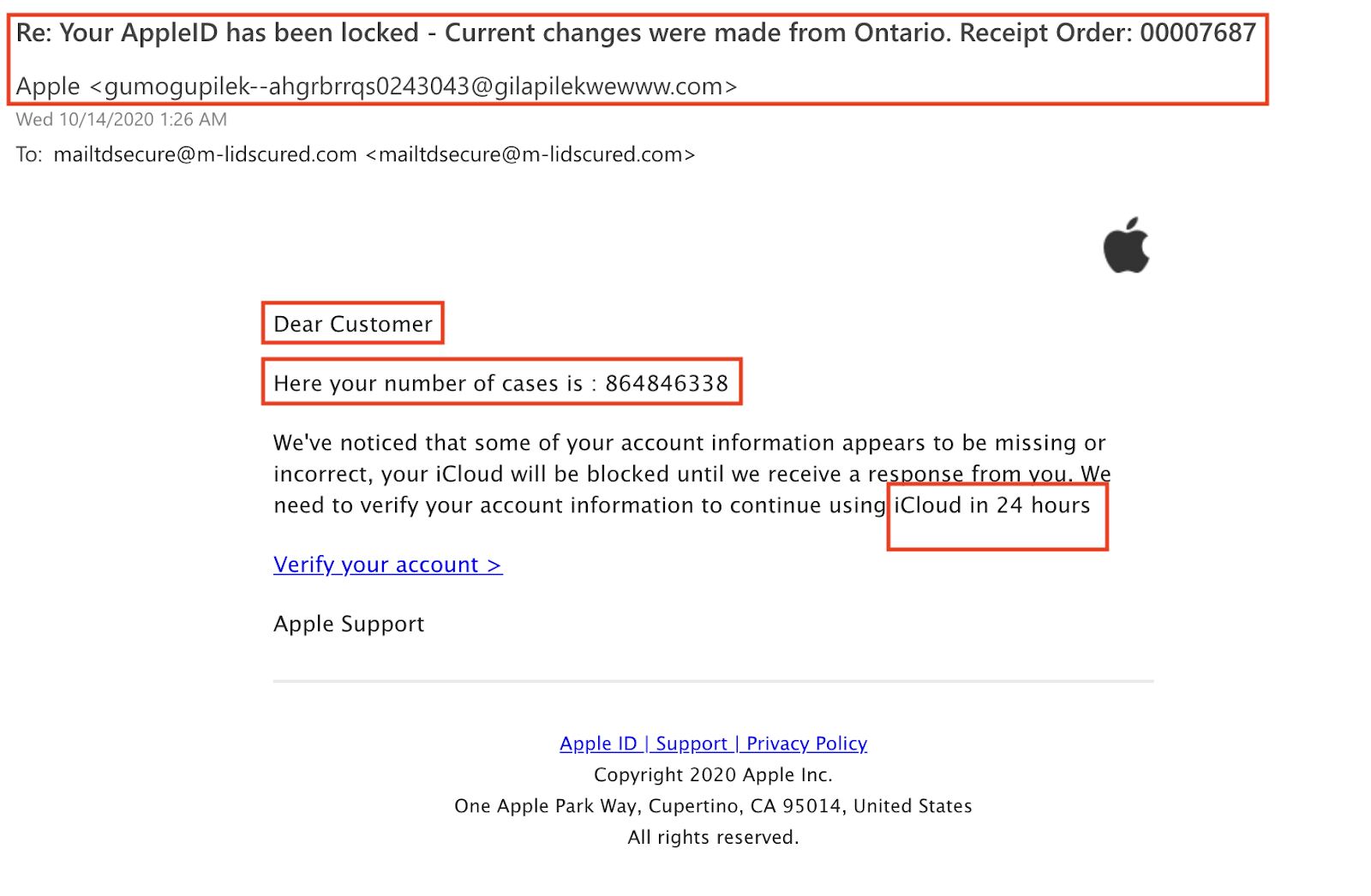
I were given an e mail that appeared so much love it was once from Apple, with the fitting emblem and the whole thing. The greeting was once the primary pink flag — addressed to “Pricey Buyer” as a substitute of my title.
The e-mail discussed discrepancies in my account data, threatening to dam my iCloud get entry to if no longer resolved inside of 24 hours. Phishing makes an attempt use this urgency to trick folks into responding briefly and no more cautiously.
It gave me a case quantity, although I hadn’t contacted Apple relating to the rest, so it was once inappropriate. Plus, the topic line mentioned my AppleID being locked and discussed adjustments made out of Ontario, which didn’t fit the remainder of the e-mail’s tale.
These items didn’t upload up: the bizarre greeting, the push to mend my account, the case quantity out of nowhere, and the mismatched topic line. All of them pointed to the e-mail no longer truly being from Apple.
Amazon
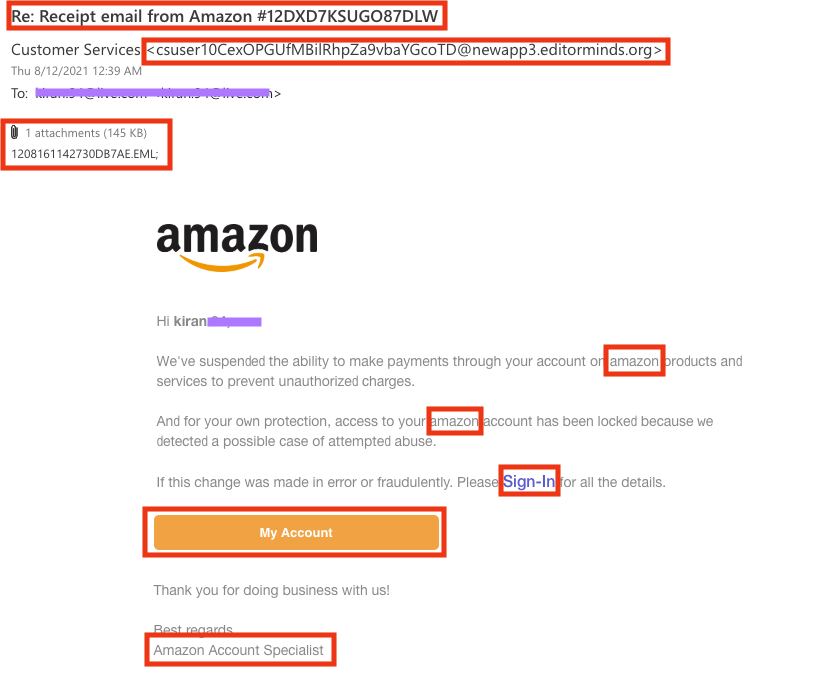
I latterly won an e mail from Amazon that, in the beginning look, gave the impression to be from the corporate. The branding appeared correct and paired Amazon’s colour scheme and emblem. There have been a couple of discrepancies, although.
The sender’s e mail deal with was once a nonsensical mixture of letters and numbers. There was once additionally an hooked up report (which is already a pink flag) with a random, meaningless title that showed the e-mail’s illegitimacy.
The e-mail additionally tried to personalize the message the use of my e mail deal with quite than my title.
Plus, the usage of “amazon” with out correct capitalization, a call-to-action categorized “My Account” that appeared out of context, and a clumsy last statement, “Thanks for doing industry with us!”, all contributed to the belief that this e mail was once a phishing strive.
Phishing No Extra
Scammers are sensible, and so they use numerous gear to make emails that glance original and convincing. However those gear and makes an attempt are all the time in keeping with human creativeness.
They prey on feelings — worry, urgency, interest — to urged fast, unthinking movements. Spotting the patterns, like pressing language, requests for private data, or hyperlinks that don’t moderately fit the meant sender’s website online, may also be your first defensive line.
Finally, teach your self and supplement your wisdom with gear like unsolicited mail filters, antivirus instrument, and e mail verification to give protection to your individual data from falling into the incorrect fingers.
![]()

![→ Download Now: The Beginner's Guide to Email Marketing [Free Ebook]](https://wpfixall.com/wp-content/uploads/2021/07/53e8428a-29a5-4225-a6ea-bca8ef991c19.png)
