Managing shopper websites at scale calls for occupied with infrastructure safety in techniques past merely putting in safety plugins or imposing sturdy passwords.
Whilst you host dozens or loads of WordPress websites, the internet hosting structure turns into a safety attention that may both give protection to your whole portfolio or put it in peril.
Conventional shared internet hosting helps to keep prices down, however it additionally signifies that websites proportion the similar record gadget, procedure area, and community stack. As such, when one web site on a shared server is compromised, the malware can unfold to different websites.
The hidden safety dangers of shared internet hosting environments
Every web site on a shared internet hosting server makes use of a portion of the server’s CPU, RAM, and garage. This is sensible for internet hosting suppliers from a price standpoint and helps to keep buyer costs available.
Alternatively, from a safety standpoint, there are vulnerabilities that scale with the collection of websites you set up. The core factor facilities on useful resource sharing. Document permissions and consumer isolation can give some coverage, however those are software-level controls that may be exploited. Finally, phishing assaults, malware, and ransomware stay the main threats to any web site.
Figuring out ‘lateral unfold’ and ‘cross-contamination’ can lend a hand explain the hazards:
- Lateral unfold refers to malware transferring from one compromised gadget to different methods inside of the similar community or setting.
- Pass-contamination occurs when a safety factor affecting one web site spreads to different websites sharing the similar infrastructure.
When you set up shopper portfolios, saving cash the usage of shared internet hosting can also be horny. Alternatively, a unmarried shopper’s old-fashioned plugin or vulnerable password can pose a danger to your whole internet hosting setup.
Whilst you issue within the time spent tracking for threats and getting better from safety incidents throughout more than one websites, the worth drops.
How malware spreads between websites on shared servers
The precise nature of any cross-site contamination is determined by how the internet hosting supplier implements consumer separation and record permissions. Even so, the basic downside stays constant throughout maximum shared internet hosting setups: those environments create assault surfaces the place compromised accounts can get entry to different customers’ information thru misconfigured permissions or prone scripts.
The pathways for cross-site an infection come with:
- PHP scripts learn information from different consumer directories when permissions are configured incorrectly.
- Shared transient directories permit malware to unfold between websites.
- Server-level vulnerabilities permit processes from one web site to impact others.
- Compromised consumer accounts achieve get entry to to neighboring directories thru shared useful resource swimming pools.
Kinsta buyer Bookswarm came upon this factor whilst managing loads of shopper websites on a shared internet hosting platform. They discovered that the combined server setup created safety complications along somebody web site compromises. The structure intended that “an assault on one was once an assault on others.”
This additionally creates an operational burden as you wish to have consistent tracking to catch compromises ahead of they unfold. If one web site presentations indicators of an infection, it’s important to take a look at each different web site at the similar server. Incident reaction turns into a portfolio-wide workout moderately than an remoted repair.
The blacklist contamination downside
Shared IP addresses create some other layer of chance in conventional shared internet hosting. When more than one websites proportion the similar IP, in addition they proportion the similar recognition within the eyes of e-mail suppliers, search engines like google and yahoo, and safety services and products.
As a result of a unmarried compromise may end up in all the IP cope with being blacklisted, each web site on that IP suffers from a number of cascading issues:
- Electronic mail deliverability drops throughout your whole portfolio when one compromised web site triggers junk mail filters akin to Spamhaus.
- Search engines like google and yahoo flag the shared IP as suspicious, negatively affecting ratings for all related websites.
- Safety services and products and firewalls block requests from the IP, breaking capability for websites unrelated to the unique compromise.
- Consumer websites lose accept as true with signs when safety equipment affiliate the shared IP with malicious job.
The restoration procedure from IP blacklisting calls for a coordinated effort together with your internet hosting supplier. You wish to have to spot which web site brought about the issue, blank it up, after which request removing from more than a few blacklists. Right through this procedure, all websites at the shared IP proceed to revel in the effects.
Within the interim, you may have to provide an explanation for on your purchasers why their e-mail stopped running or why their web site were given flagged, although they adopted optimum WordPress safety practices. The basis motive strains again to infrastructure selections that exact web site house owners haven’t any regulate over. All of this ongoing repairs takes time clear of shopper paintings and construction tasks.
Container-level isolation for WordPress internet hosting
Web site isolation addresses lots of the basic issues of shared internet hosting. For instance, Kinsta runs every web site in its personal remoted container with devoted sources. This implies every WordPress web site will get its personal container that incorporates the whole thing had to run: Linux, NGINX, PHP, and MySQL.
The isolation occurs on the working gadget point thru two core mechanisms:
- Namespaces supply every container with its personal view of gadget sources. A procedure working in a single container can not see or engage with processes in some other container.
- Keep an eye on teams (‘cgroups’) put into effect useful resource limits and make sure every container has get entry to to its devoted allocation of CPU and RAM.
What’s extra, PHP threads in your WordPress web site can not see or engage with processes from different websites. This kernel-level separation prevents eventualities the place one web site’s compromised procedure makes an attempt to get entry to sources belonging to different websites.
Community stacks function independently inside of every container, too. Every web site has its personal community interface and IP dealing with. This isolation extends thru all the stack and gets rid of the noisy neighbor downside that plagues shared internet hosting.
When one web site studies a site visitors spike or runs resource-intensive operations, it most effective impacts that web site’s container. The devoted useful resource allocation method different websites proceed working with their complete allocation irrespective of what occurs in different places at the infrastructure.
How container isolation prevents malware lateral unfold
When a web site will get compromised in a containerized setting, the malware remains confined inside of that container. This separation prevents compromised processes from having access to different packing containers thru a number of mechanisms:
- Document methods stay remoted, so malware can not unfold by way of exploiting shared directories or transient information.
- Procedure namespaces save you malicious code from scanning or interacting with processes in different packing containers.
- Community isolation limits the facility of compromised websites to scan or assault neighboring websites.
- Reminiscence areas keep totally separate, combating buffer overflow assaults from crossing container barriers.
If the web site is hosted on Kinsta, our tracking methods can come across the compromised container in an instant and reply whilst different websites to your portfolio proceed to function.
Verifying true isolation vs advertising claims
Now not all internet hosting suppliers put into effect container isolation in the similar manner. Some use the time period “remoted” to explain comfortable limits on useful resource utilization whilst nonetheless working more than one websites in shared environments. Figuring out what constitutes authentic container-level isolation is helping you overview your internet hosting choices and steer clear of the safety dangers that include deceptive advertising.
True container isolation method every web site runs in its personal working gadget namespace with devoted sources that can’t be accessed by way of different websites. When you’re searching for a brand new internet hosting supplier, there are a few issues of center of attention:
- Does every web site get its personal container with devoted CPU and RAM allocations that different websites can not get entry to?
- Are record methods totally separated on the kernel point the usage of namespaces moderately than simply user-level permissions?
- What occurs to different websites when one container will get compromised or studies a site visitors spike?
- Which containerization era does the host use (LXC, LXD, Docker), and the way does it put into effect isolation?
- Can the host supply technical documentation about its isolation mechanisms and structure?
The variation between comfortable limits and difficult isolation issues for each safety and function. Cushy limits may prohibit how a lot CPU a web site can use, however they function inside of a shared setting the place one web site’s processes can nonetheless engage with others. Onerous isolation with devoted sources method every web site operates in a fully separate setting the place neighboring websites can not get entry to its sources or be suffering from its actions.
Technical verification strategies
Searching for technical specs that element the containerization era will let you perceive to what stage a number has wisdom concerning the underlying structure. For example, suppliers the usage of LXC, LXD, Docker, or equivalent applied sciences will have to be capable of describe the particular isolation mechanisms they put into effect.
Compliance certifications akin to SOC 2 Kind II and ISO 27001 point out that safety practices were audited by way of impartial events. Those certifications require documented safety controls and common checking out, which gives extra assurance than advertising claims by myself. Kinsta maintains each certifications and undergoes common audits to make sure that isolation mechanisms paintings as marketed.
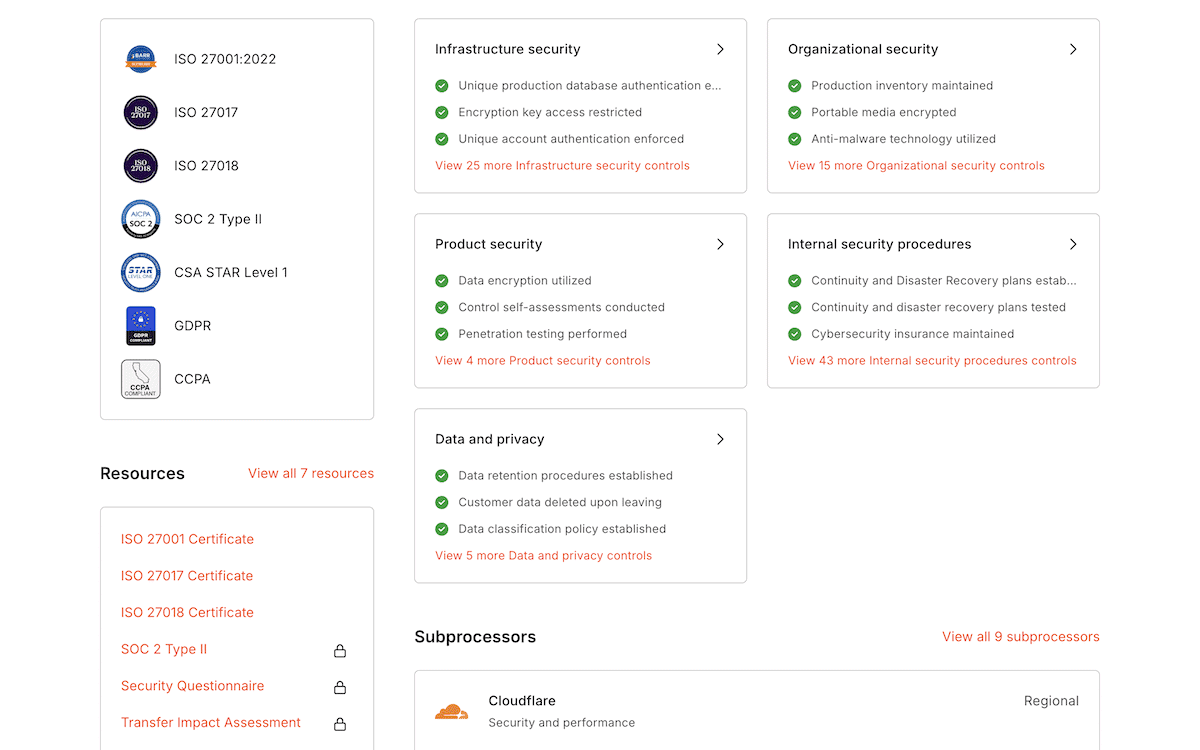
When you get to make use of the host thru a tribulation duration, you’ll be able to additionally test how its isolation works in a couple of other ways, akin to tracking useful resource intake throughout more than one websites at the similar server, or having a look at what occurs all the way through CPU-intensive operations for a person web site.
With Kinsta, this type of hands-on validation is conceivable all the way through your first month for free of charge.
Figuring out what web site isolation method in your internet hosting technique
Moving from shared internet hosting to an remoted container structure can exchange the basic safety posture of your whole WordPress portfolio for the easier, or even the way in which you manner infrastructure control at scale.
Throughout more than one shopper websites on shared internet hosting, the chance of no less than one web site experiencing a safety incident approaches near-certainty. The true query turns into whether or not that incident remains contained to a unmarried web site or creates cascading issues throughout your whole portfolio.
For companies and groups managing many WordPress websites, internet hosting is in the long run a portfolio-level chance choice. When you’re searching for infrastructure designed in particular for managing websites at scale, Kinsta provides answers adapted for companies and high-volume WordPress environments.
The put up What occurs when one web site will get hacked on shared internet hosting? seemed first on Kinsta®.
WP Hosting