Contents
TL;DR
In November 2018, the Web Engineering Activity Drive (IETF) met in Bangkok, and a brand new Internet Draft used to be followed. The QUIC delivery protocol, an HTTP/2 successor, used to be renamed to HTTP/3. HTTP/3 builds on UDP, and is already being utilized by distinguished cyber web firms comparable to Google and Fb. In case you’re the use of Chrome and connecting to a Google provider, you’re almost certainly already the use of QUIC.
The brand new model of the HTTP protocol advantages from the bare-metal, low-level UDP protocol, and defines most of the new options that have been in earlier variations of HTTP on the TCP layer. This offers some way of fixing constraints inside the present cyber web infrastructure.
The primary effects are promising, and when the Web Draft through IETF expires, in June 2019, we will be able to be expecting HTTP/3 to be promoted as a brand new, 3rd era HTTP usual.
Nonetheless on the lookout for that best possible WordPress host?
-
Absolutely controlled -
Safe like Citadel Knox
-
Loose migrations
-
Final velocity
-
Day by day backups
-
Google Cloud Platform
- HTTP/3 Is Coming
- What is HTTP/3 – In Layman’s Terms
- A Bit of Background – It Started with HTTP/2
- Internet Protocol (IP)
- Understanding the Role of TCP and UDP
- QUIC and HTTP/3
HTTP/3 Is Coming
Some say that the internet trade’s starvation for extra velocity and decrease latency is handiest matched through Google Chrome’s starvation for extra RAM.
In 2016, we published an article about HTTP/2, a typical that, according to W3Techs, these days has round a 34% international adoption fee. And consistent with Can I use, it’s additionally supported through all trendy internet browsers. But right here we’re, writing a piece of writing concerning the subsequent model of the protocol, HTTP/3.
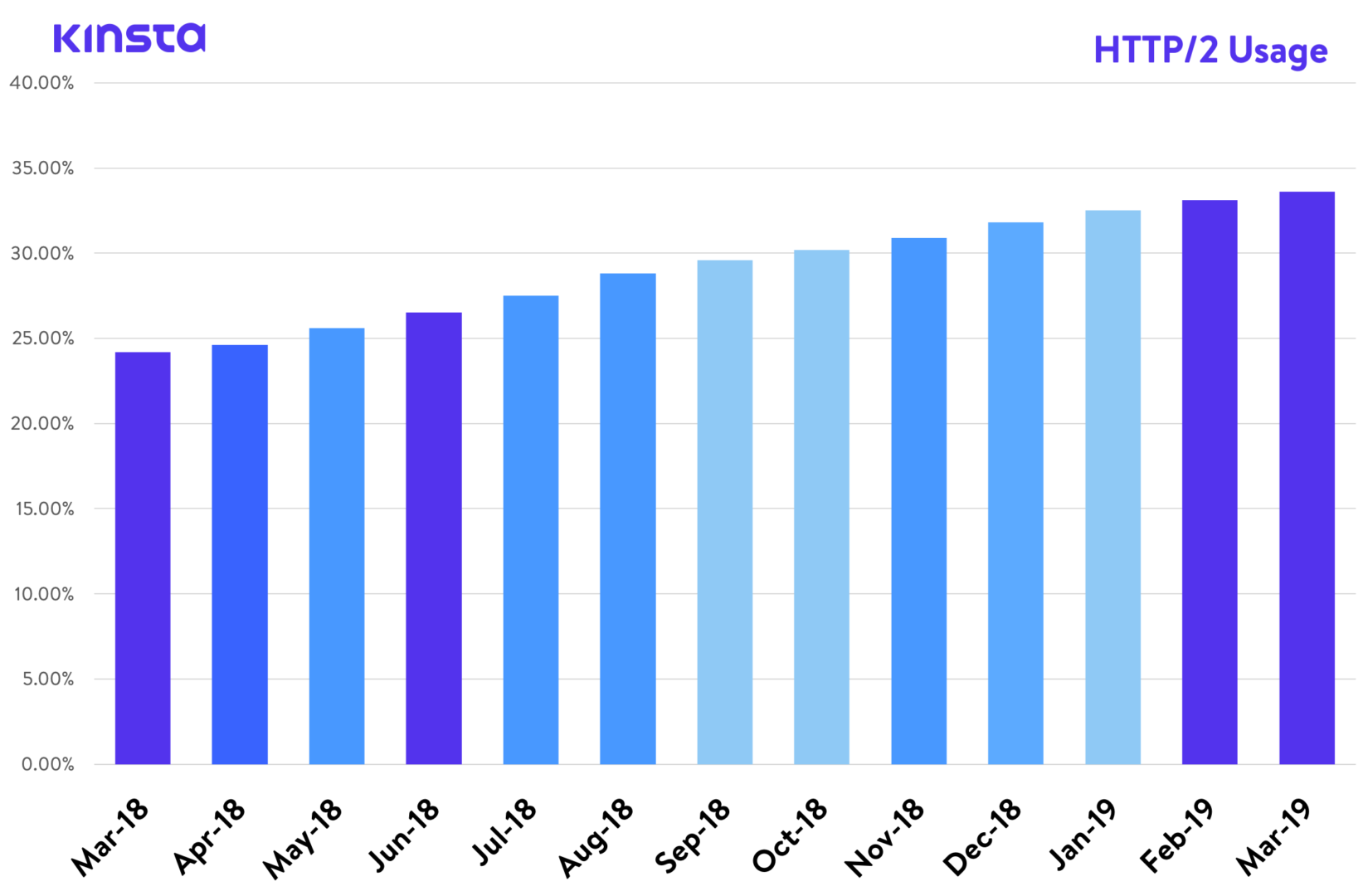
HTTP/2 Utilization
HTTP/3 is, on the time of this writing, an IETF Internet-Draft or ID, because of this that it’s these days into consideration for an upcoming cyber web usual through the Internet Engineering Task Force – a world cyber web requirements frame, in control of defining and selling agreed upon cyber web protocol requirements, comparable to TCP, IPv6, VoIP, Internet of Things, and so on.
It’s an open frame which unites the internet trade and facilitates dialogue concerning the path of the cyber web.
These days, the ID section of HTTP/3 is the final section ahead of proposals are promoted to the extent of RFC-s, or Request-for-Feedback, which we will be able to believe, for all intents and purposes, legitimate cyber web protocol definitions. Then are then applied through all primary cyber web gamers.
Which means that HTTP/3 is to change into an legitimate usual as soon as the draft expires later this yr (June 2019).
What’s HTTP/3 – In Layman’s Phrases
HTTP/3 is the 3rd model of the Hypertext Switch Protocol (HTTP), in the past referred to as HTTP-over-QUIC. QUIC (Fast UDP Web Connections) used to be to start with evolved through Google and is the successor of HTTP/2. Corporations comparable to Google and Fb have already been the use of QUIC to hurry up the internet.
A Little bit of Background – It Began with HTTP/2
At Kinsta we’re obsessive about squeezing each and every final millisecond from our stack, whether or not it’s benefiting from the newest version of PHP, handing over records over Google Cloud Platform’s top class tier community, or caching belongings on our HTTP/2 CDN.
HTTP/2 introduced some critical enhancements with non-blocking downloads, pipelining, and server push which has helped us conquer some boundaries of the underlying TCP protocol. It allowed us to reduce the choice of request-response cycles and handshakes.
HTTP/2 made it conceivable to push a couple of useful resource in one TCP connection – multiplexing. We additionally were given extra flexibility within the ordering of static downloads, and our pages at the moment are not constrained through a linear development of the downloads.
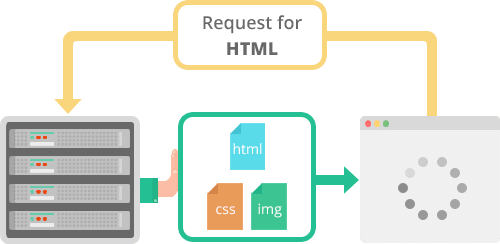
HTTP/2 push
In apply, because of this now one massive javascript useful resource does no longer essentially equivalent a choke level for all of the different static assets ready their flip.
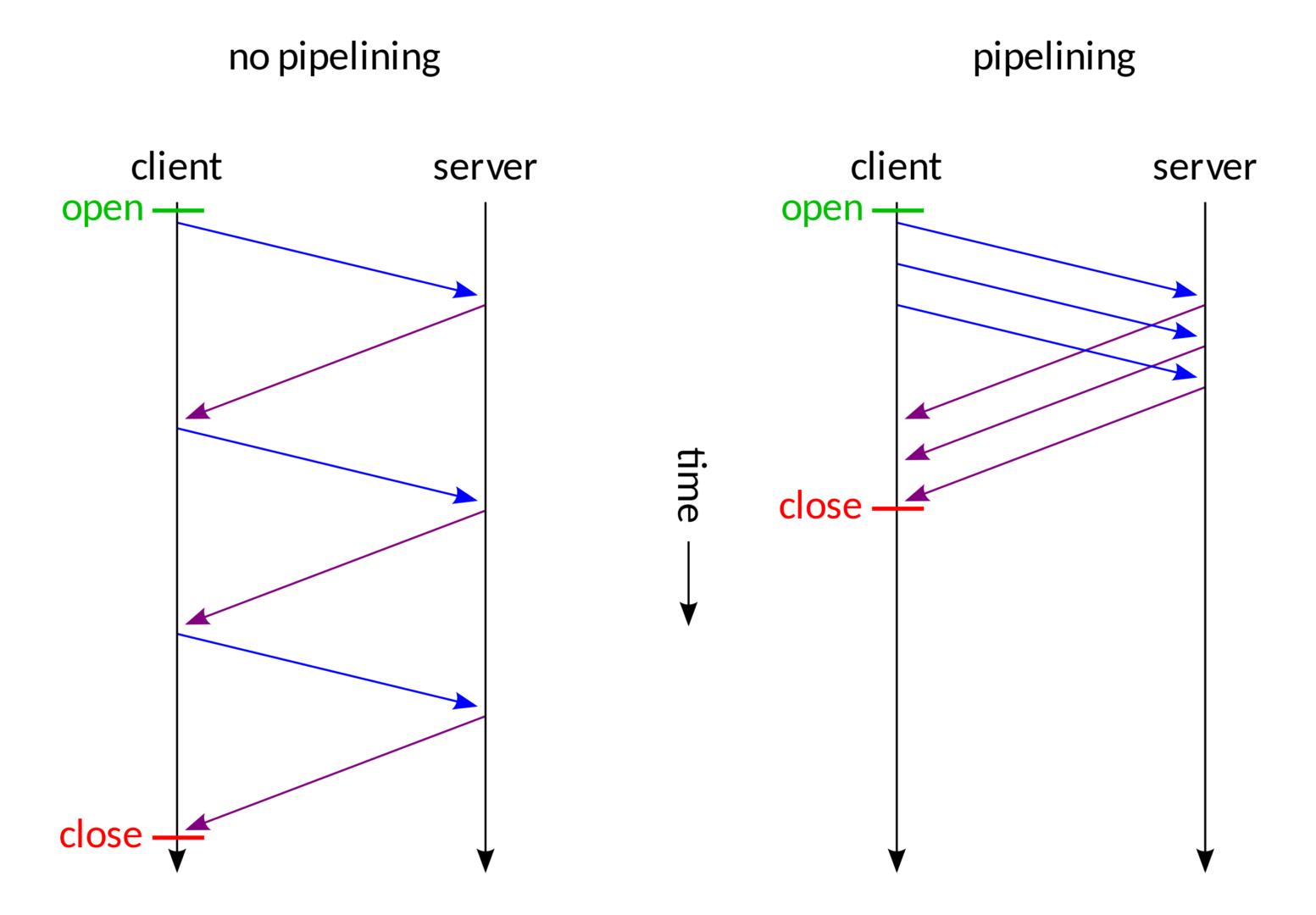
No pipelining vs pipelining (Symbol supply: Wikipedia, Creator Mwhitlock)
Upload to those issues HTTP/2’s header HPACK compression and default binary structure of knowledge switch, and we have now, in lots of circumstances, a considerably extra environment friendly protocol.
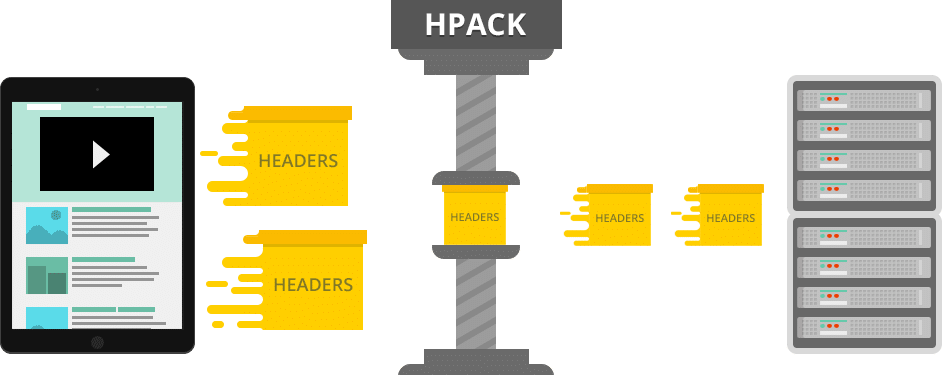
HTTP/2 HPACK compression
Primary browser implementations made it a demand for web pages to enforce encryption – SSL – so that you could take advantage of HTTP/2 – and from time to time this incurred a computation overhead that rendered velocity enhancements unnoticeable. There have been even some circumstances the place customers reported slowdown after transitioning to HTTP/2.
Let’s simply say that the early days of adoption of this model weren’t for the vulnerable of middle.
The NGINX implementation additionally lacked the server-push characteristic, depending on a module. And NGINX modules aren’t your standard Apache drop-in modules that you’ll simply reproduction – NGINX must be recompiled with those.
Whilst a few of these problems are solved now, if we have a look at all the protocol stack, we see that the principle constraint lies on a decrease point than HTTP/2 dared to challenge.
To elaborate this, we will be able to dissect these days’s cyber web protocol stack from its backside layer to the highest. If you wish to be told extra concerning the background of HTTP/2, be certain to try our ultimate HTTP/2 guide.
Web Protocol (IP)
The Web Protocol (IP) defines the bottom-part of all the cyber web topology. It’s the a part of the cyber web stack this is, we will be able to safely say, truly no longer negotiable with out converting the whole thing, together with changing all the {hardware} infrastructure, from routers to servers or even the machines of finish customers.
So, whilst the protocol overhaul could also be due, any such far-reaching enterprise isn’t at the horizon right now, basically as a result of we haven’t get a hold of a viable, groundbreaking, but backward-compatible choice.
Beneath it, there may be link layer – the a part of the protocol which is “naked metallic” in an effort to say.
On an aspect observe, a resounding case for an entire overhaul will also be noticed from the velocity with which creators of IPFS (interplanetary report gadget) controlled to near an ICO investment that made them 250 mil USD inside one month.
We will hint the beginnings of the IP protocol again to 1974, to a paper revealed through the Institute of Electrical and Electronics Engineers and authored through Vint Cerf and Bob Cahn. It detailed packets being despatched over a community, routing them throughout IP addresses, and numerically outlined addresses of nodes in a community/networks. The protocol outlined the structure of those packets, or datagrams – its headers and payload.
After the RFC 760 definition from 1980, the IETF settled with the definition broadly used to this present day, in its Request For Comments 791. That is the fourth model of the protocol, however let’s imagine it’s the primary manufacturing model.

Web Protocol (Symbol supply: RFC791)
It makes use of 32-bit addresses, which units constraint to the choice of addresses to round 4 billion. This limitation is the reason for the thriller of why non-business cyber web customers get “dynamic IP addresses” through their ISPs, and a static IP is regarded as an “added worth” and incessantly topic to further fees.
They’re rationing.
It wasn’t lengthy till it used to be discovered that 32-bit addresses aren’t sufficient, and the dearth used to be looming, such a lot of RFCs had been revealed seeking to maintain this. Even if those answers are widely used today, and are a part of our day-to-day lives, it’s almost certainly protected to mention those quantity to hacks.
Internet Protocol version 6 or IPv6 got here to be able to deal with those boundaries, together with to regularly be followed over the former model. It used to be made a Draft Usual file for the IETF in 1998, and used to be raised to an Web Usual in 2017.
Whilst IPv4 deal with area used to be restricted through its 32-bit deal with duration, IPv6 usual used to be given 128 bits, or 3.4 * 10 ^ 38 conceivable addresses. This must be sufficient to final us for reasonably a while.
In keeping with Google and IPv6 connectivity amongst its customers, IPv6 adoption is simply over 25% as of March 2019.
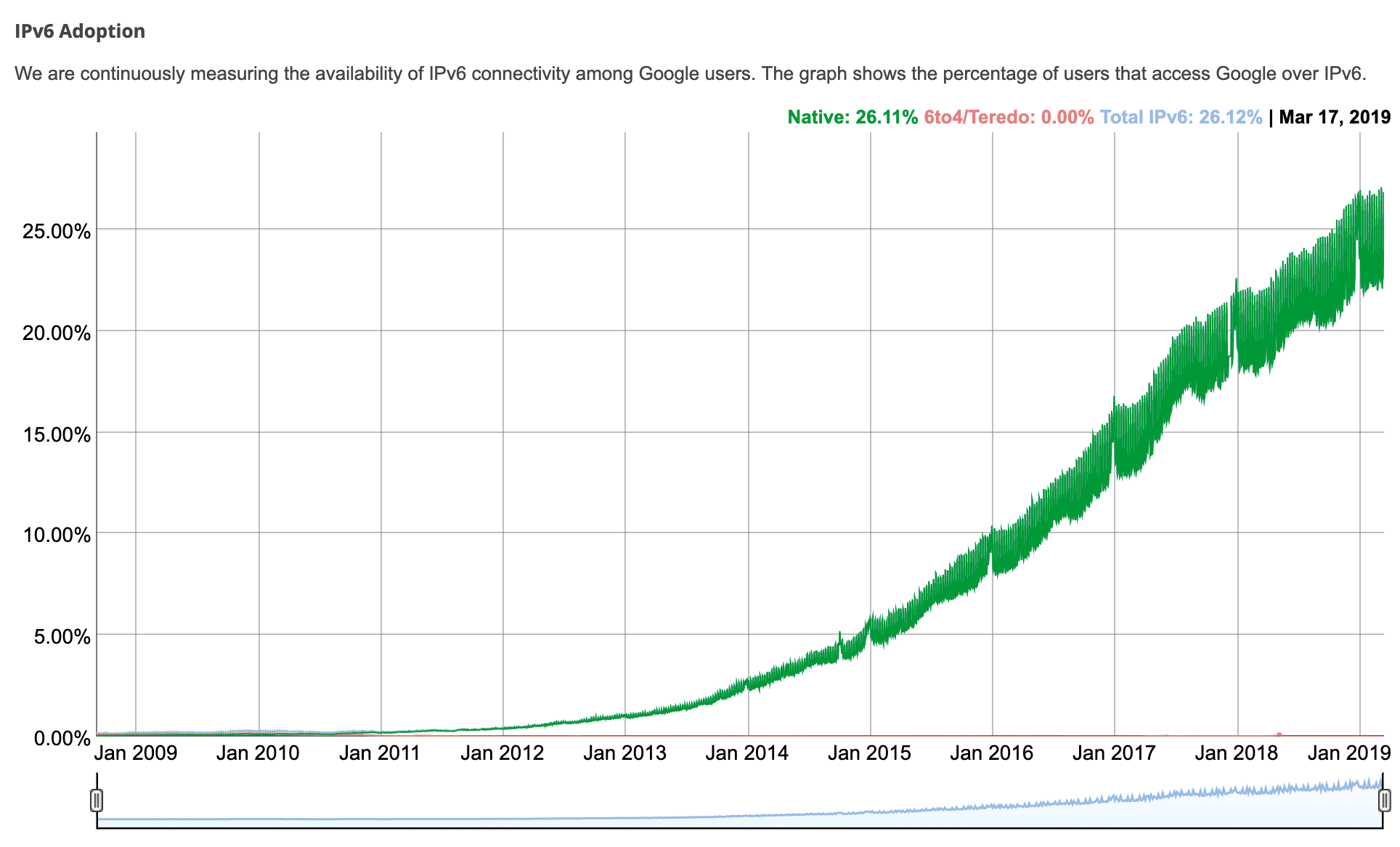
IPv6 adoption
IP is a rudimentary layer of the cyber web stack, defining most elementary issues, with out promises of supply, records integrity, or the ordering of transmitted packets. By itself it’s unreliable. The header structure of IPv4 supplies for header checksum, which the transmission nodes use to make sure the integrity of the header. This makes it other from the IPv6 model, which is dependent upon the hyperlink layer beneath, enabling it to be quicker..
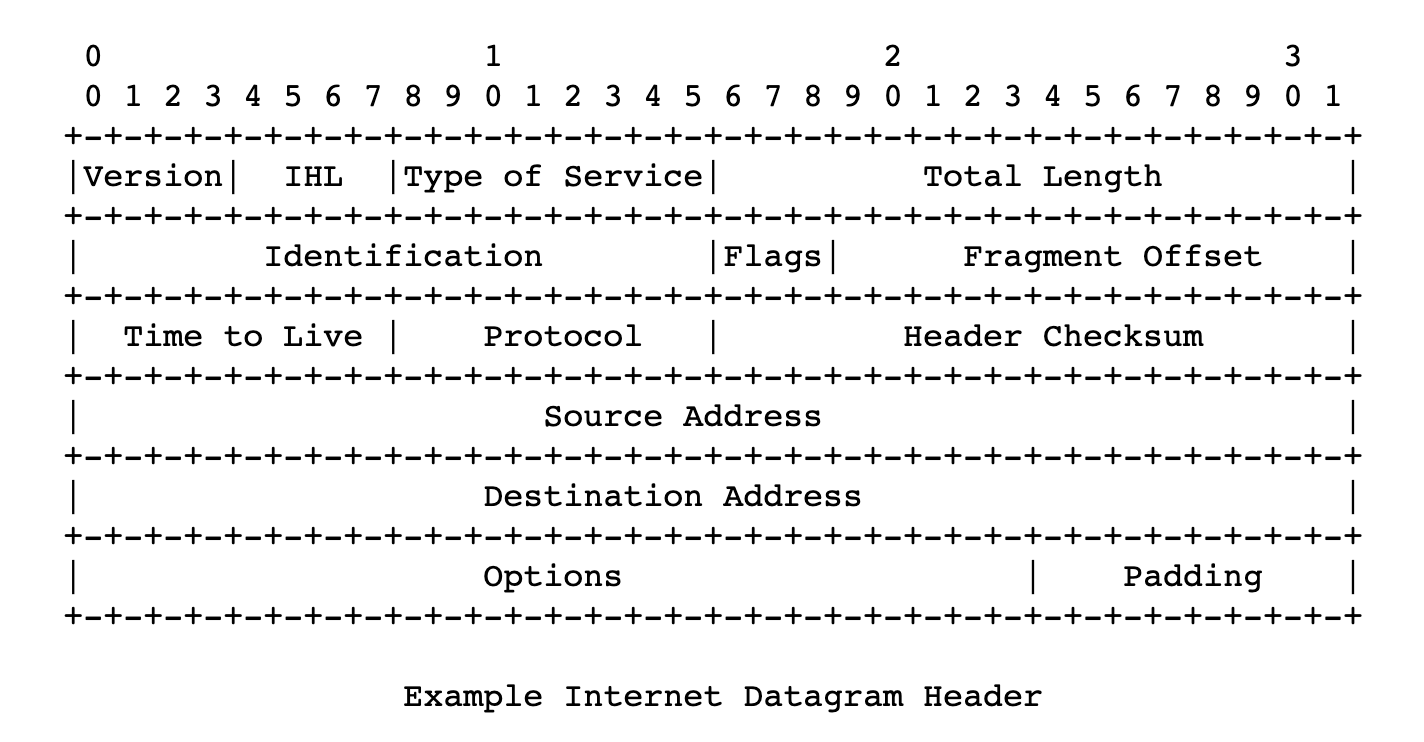
Web Datagram Header (Symbol supply: RFC791)
Working out the Function of TCP and UDP
Now it’s time to discover the place HTTP/3 suits in with TCP and UDP.
TCP
Whilst IP is the underlying layer of all of our on-line communications these days, TCP (Transmission Control Protocol) is the next point a part of the cyber web protocol suite, offering reliability this is wanted for the internet, mail, report switch (FTP) – for utility layers/protocols of the cyber web.
This contains multi-step connection status quo, with handshakes, confident order of packets, and retransmission of misplaced packets. It supplies comments (Acks) of supply to the sender and so forth. There could also be checksum computation to come across mistakes.
A lot of these issues point out a large number of steps that make TCP a competent protocol, making it a basis of probably the most infamous cyber web products and services we use these days.
Its specification dating back to 1974 (RFC 675) and 1981 (RFC 793) hasn’t modified considerably to this present day.
The reliability that TCP supplies doesn’t, on the other hand, come with no price. The overhead of all of the roundtrips required through handshakes, supply feedbacks, ordering promises, and checksums that may be thought to be vulnerable and redundant. It has made TCP a bottleneck of the trendy protocol stack. HTTP/2 has reached a plateau of velocity enhancements that may be accomplished on best of TCP.
Converting the TCP in any really extensive means isn’t a simple enterprise, since the protocol is, as a part of the TCP/IP stack that is going again all of the strategy to the ’70s. It’s deeply embedded into working programs, tool’s firmware, and so on.
UDP
UDP (User Datagram Protocol) could also be one of the crucial portions of the Web Protocol Suite, with its specification relationship again to 1980 (RFC 768).
It’s, because the title suggests, a datagram-based connectionless protocol. Because of this there are not any handshakes and there are not any assurances of ordering or supply. Which means that any conceivable steps for making sure supply, records integrity, and different issues are left to the appliance layer. Which means that an utility construction on best of UDP can cherry-pick methods it’ll make use of relying at the concrete case, or it may well perhaps leverage components of the link layer, like checksums, to keep away from overhead.
As a result of UDP is in style similar to TCP, it makes it conceivable to succeed in enhancements with out requiring huge trade of firmware on all of the gadgets hooked up to the cyber web, or vital adjustments within the working programs.
Deployment of latest protocols is hampered through many firewalls, NATs, routers and different middle-boxes that handiest permit TCP or UDP are deployed between customers and the servers they wish to achieve. – HTTP/3 explained
This thread on Hacker News can lend a hand us start to perceive the reasoning at the back of construction the brand new HTTP model on best of the present community stack, reasonably than reinventing it (even supposing there may be extra to it than that).
UDP packet structure specification is reasonably minimum, it’s header is composed of the supply port, vacation spot port, duration, in bytes, of packet header and packet records, and checksum. Checksum can be utilized to make sure data-integrity each for header and information a part of the packet.
Checksum is non-compulsory when the underlying protocol layer is IPv4, and necessary with IPv6. Up to now, UDP has been used for VoIP programs, video streaming, DNS gadget, and DHCP protocol.
QUIC and HTTP/3
QUIC (Fast UDP Web Connections) used to be first deployed through Google in 2012. It redefines barriers of community layers, depending on lower-level UDP protocol, redefining handshakes, reliability options, and security measures in “user-space,” heading off the desire for upgrading kernels of internet-wide programs.
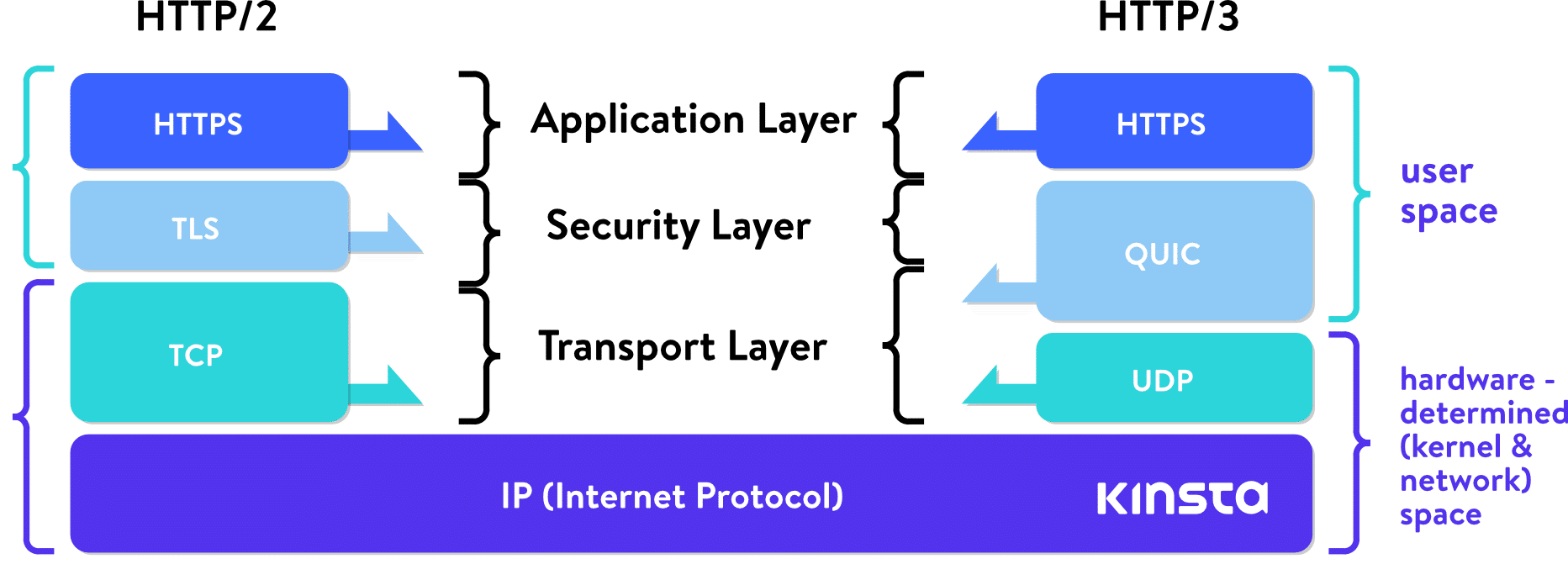
HTTP/2 stack vs HTTP/3 stack
Similar to with HTTP/2, an development which used to be spearheaded through Google’s SPDY or fast, HTTP/3 will once more construct on those achievements.
Whilst HTTP/2 did give us multiplexing, and mitigate head-of-line-blocking, it’s constrained through TCP. You’ll be able to use a unmarried TCP connection for more than one streams multiplexed in combination to switch records, but if a type of streams suffers a packet loss, the entire connection (and all its streams) are held hostage, in an effort to say, till TCP does its factor (retransmits the misplaced packet).
Which means that all of the packets, despite the fact that they’re already transmitted and ready, within the buffer of the vacation spot node, are being blocked till the misplaced packet is retransmitted. Daniel Stenberg in his book on http/3 calls this a “TCP-based head of line block.” He claims that, with 2% packet loss, customers will do higher with HTTP/1, with six connections to hedge this possibility.
QUIC isn’t constrained through this. With QUIC construction at the on connectionless UDP protocol, the idea that of connection does no longer elevate the constraints of TCP and screw ups of 1 circulation don’t have to persuade the remaining.
As Lucas Pardue from Cloudflare put it:
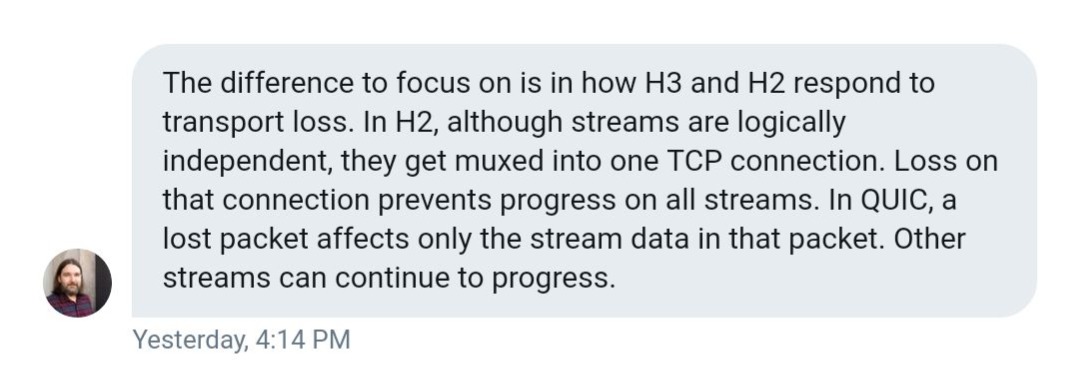
Lucas Pardue on HTTP/3
With a focal point on UDP streams, QUIC achieves multiplexing with no need to piggyback on one TCP connection. QUIC builds its connection on the next point than TCP. New streams inside QUIC connections aren’t pressured to look ahead to the others to complete. QUIC connections additionally take pleasure in disposing of TCP handshake overhead, which reduces latency.
People at Cisco made an interesting video explaining TCP’s 3-way handshake.
Whilst QUIC does away with TCP reliability options, it makes up for it above the UDP layer, offering retransmitting of packets, ordering and so forth. Google Cloud Platform introduced QUIC support for his or her load balancers in 2018 and noticed an development in imply web page load time through 8% globally, and as much as 13% in areas the place latency is upper.
Between Google Chrome, YouTube, Gmail, Google’s seek and different products and services, Google used to be in a position to deploy QUIC on a pleasing chew of the cyber web, with out looking forward to IETF. Google’s engineers declare that during 2017, 7% of the cyber web site visitors used to be already carried out over QUIC.
Google’s model of QUIC used to be eager about simply HTTP delivery, the use of HTTP/2 syntax. Other folks from IETF (the ones in control of standardizing QUIC), made up our minds that IETF model of QUIC must be capable of delivery extra than simply HTTP. In the intervening time, on the other hand, any paintings on non-HTTP protocols over QUIC is on hang.
Yet one more factor IETF’s operating team made up our minds is that the standardized model goes to make use of TLS 1.3 encryption as an alternative of Google’s customized resolution. TLS 1.3, in comparison to the older variations, additionally contributes to protocol velocity, as its handshakes require fewer roundtrips.
Presently, Google continues to make use of its personal model of QUIC in its product, whilst directing it’s building efforts towards the IETF requirements. Many of the different cyber web gamers are construction on best of the IETF model (the 2 fluctuate in every other sides beside encryption).
If we open Chrome Dev Gear, and cargo a few of Google’s merchandise, like Gmail, within the Protocol column of the Community tab, we will be able to see a large number of assets being loaded by means of Google’s model of the QUIC protocol. This could also be the case for Google’s merchandise like Analytics, Google Tag Supervisor, and so on.
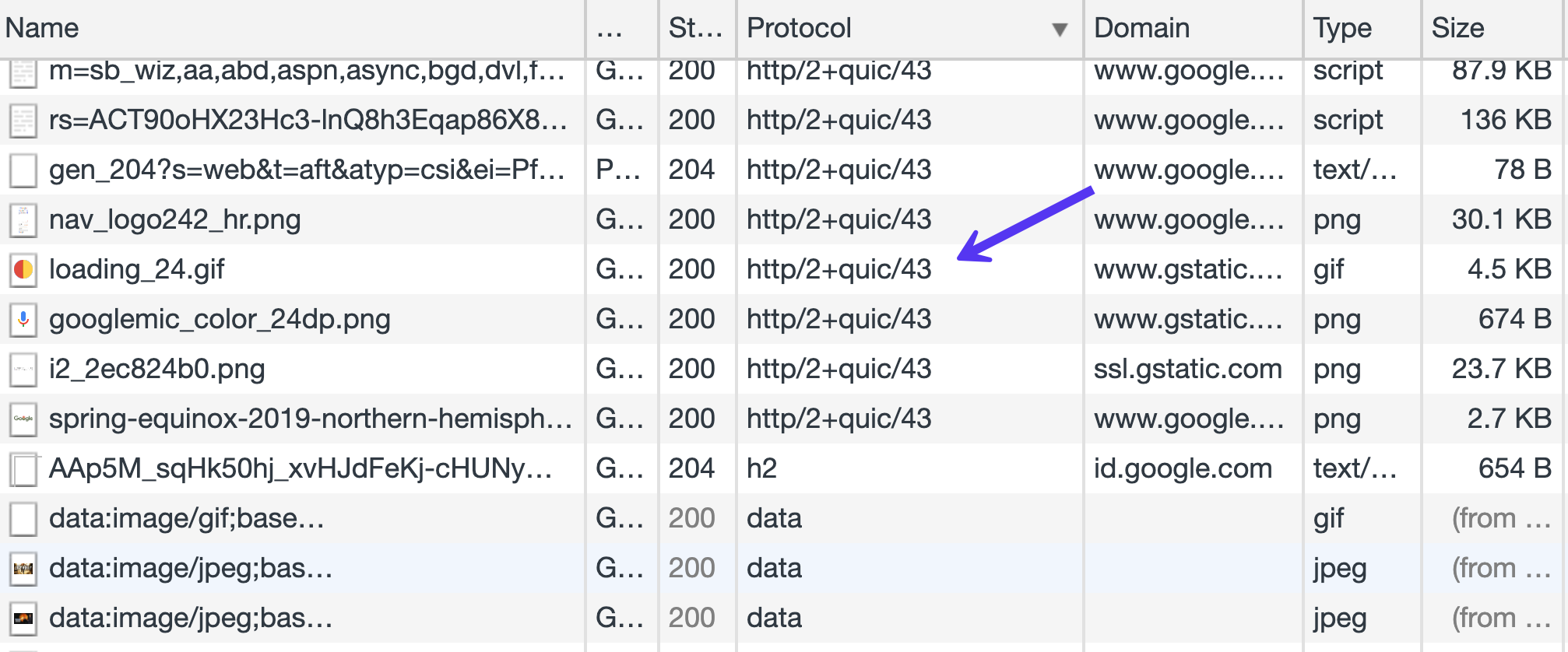
Google provider QUIC
Cloudflare just lately revealed a very extensive update concerning the standardization growth.
Whilst UDP does supply QUIC and HTTP/3 some inherent benefits, it additionally brings some demanding situations. TCP has been the mainstream protocol for years, whilst UDP has no longer, so working programs and the tool stack for it, normally, isn’t as optimized. Because of this, there may be a lot upper CPU load/necessities with QUIC, through some estimates, two times up to with HTTP/2.
Optimizations move deep right down to the kernel of working programs, and different routers and devices firmware. This Red Hat tuning guide would possibly shed extra gentle at the matter for the ones extra technically vulnerable.
Lets say that QUIC makes an attempt to re-engineer TCP options on best of a extra minimum, and extra versatile protocol.
QUIC connections, which we discussed previous, mix TLS and delivery handshakes. As soon as established, they’re recognized through distinctive CIDs (connection IDs). Those IDs persist throughout IP adjustments and will lend a hand to safe uninterrupted downloads on, for instance, a transfer from 4G to WiFi. That is related, specifically as a result of increasingly cyber web site visitors is carried out on cell gadgets. Questions would possibly rise up whether or not this component is conceived through Google to facilitate higher user-tracking throughout other connections and cyber web suppliers.
TLS is necessary, and is supposed to make it onerous for gadgets within the center to tamper with, or sniff the site visitors. This is why it isn’t uncommon to peer firewall suppliers and distributors like Cisco seeing the UDP protocol as an issue, and to supply techniques to disable it. It’s more difficult for middlemen to check out and supervise or filter out QUIC site visitors.
QUIC streams are despatched over QUIC connections, uni-direction or bi-directional. Streams have IDs, that determine the initiator, and whether or not the circulation is uni-directional or bi-directional, and in addition serve in-stream flow-control.
Whilst QUIC is a transport-layer protocol, HTTP is the layer above that, an application-layer protocol, or utility protocol.
Since backward-compatibility is of the maximum significance, the IETF promoted implementation of HTTP/3 will come with the previous model (HTT1 or HTTP/2) within the reaction. It’ll come with a header which informs the customer that HTTP/3 is to be had, at the side of port/host knowledge, as described in RFC 7838.
That is other from HTTP/2, through which delivery will also be negotiated inside the TLS handshake. However since IETF has all however followed QUIC-based HTTP/3 as the following usual, we will be able to be expecting internet shoppers to look forward to HTTP/3 strengthen increasingly. It’s conceivable for shoppers to cache records from earlier HTTP/3 connections, and to glue at once (zero-round-trip, or 0-RTT) on next visits to the similar host.
Abstract
There are those that suppose that, with HTTP/2 usual no longer being followed but absolutely, it can be too early to push for HTTP/3 (model 3). It is a legitimate level, however, as we discussed, this protocol has already noticed wide-scale exams and implementations. Google started trying out it as early as 2015, in addition to Fb in 2017.
Since then, different gamers have joined the standardization efforts, comparable to Akamai and Mozilla. On the final IETF hackathon in November 2018, the checklist of attendees confirmed passion in QUIC through firms comparable to Fb, Apple, Google, Mozilla, NetApp, and LiteSpeed Tech. There have been some promising tests, and it looks as if LiteSpeed may well be the primary primary server supplier with a functioning HTTP/3 server. Cloudflare could also be these days working QUIC in beta.
In a while after this, QUIC used to be renamed to HTTP/3 in IETF’s Internet Draft. It’ll expire on the finish of June 2019, and we will be able to be expecting the RFC, or the overall usual someday in July.
This yr can be thrilling, as we will be able to be expecting to peer the transfer through primary tool distributors to enforce the brand new usual. We’ll without a doubt be sharing extra about this and the way it affects Kinsta customers going ahead.
The put up What Is HTTP/3 – Lowdown on the Fast New UDP-Based Protocol seemed first on Kinsta Managed WordPress Hosting.
WP Hosting