Are you searching for a option to assist toughen WordPress safety and doubtlessly make a bit cash?
A WordPress computer virus bounty program is usually a nice are compatible. It’s a chance for builders and “moral hackers” to assist establish doable WordPress vulnerabilities, toughen safety, and receives a commission for his or her efforts.
We individually like some of these tasks as a result of they display us that WordPress is desirous about safety. And that’s why we proceed to make use of it for all of our industry internet sites.
On this article, we’ll discover how the WordPress computer virus bounty program works, the way it differs from conventional computer virus reporting, and the way it guarantees WordPress stays safe and strong. We’ll additionally proportion some guidelines for buying began as a moral WordPress hacker.
Here’s a fast review of the subjects we’ll quilt on this article.
- What Is a Malicious program Bounty Program?
- How Does The WordPress Malicious program Bounty Program Paintings?
- What is the Distinction Between the Malicious program Bounty Program and Reporting Insects in WordPress?
- Why Does WordPress Use a Malicious program Bounty Program?
- Advantages of Malicious program Bounty Techniques for Aspiring Builders
- Malicious program Bounty Techniques for WordPress Plugins and Topics
- Getting Began with WordPress Malicious program Bounty Techniques
- Bonus Sources: WordPress Safety Guides
What Is a Malicious program Bounty Program?
A computer virus bounty program is an initiative the place builders and “moral hackers” are rewarded for locating and reporting safety problems in device.
Those systems assist device platforms establish and connect doable problems earlier than hackers can misuse them for malicious functions.
Right here’s the way it works: A platform units up a program with transparent regulations and pointers outlining the insects they’re searching for.
Members, ceaselessly referred to as “moral hackers,” take a look at the platform and record any vulnerabilities. If the record is legitimate, the platform rewards them with cash, popularity, or different incentives.
Similar Submit: Most sensible Causes Why WordPress Websites Get Hacked
Malicious program bounty systems aren’t distinctive to WordPress. Maximum large tech firms, together with Google, Fb, and Microsoft, have their very own computer virus bounty systems.
Those systems have helped make their device extra safe whilst developing alternatives for moral hackers international.
Mainly, computer virus bounty systems create a win-win state of affairs. Builders toughen their device’s safety whilst individuals acquire treasured enjoy and rewards.
💡 Repair Your Hacked WordPress Website online and Keep Protected!
Cleansing up a hacked WordPress website online can also be extraordinarily tough. Let our depended on professionals restore your hacked WordPress website and proactively support your defenses towards long run threats.
How Does The WordPress Malicious program Bounty Program Paintings?
The WordPress computer virus bounty program is designed to spot and connect doable safety vulnerabilities earlier than they may be able to affect hundreds of thousands of customers.
Those vulnerabilities come with problems that might compromise the integrity, confidentiality, or availability of WordPress internet sites. For example, the next problems are thought to be serious safety vulnerabilities:
- Compromised get admission to: When any person manages to get unauthorized get admission to to a WordPress website online.
- Move-site scripting XSS: A hacking methodology that permits any person to sneakily upload doubtlessly unhealthy code to WordPress internet sites.
- SQL injections: A computer virus within the device that might permit hackers to inject knowledge into the WordPress database.
By way of partnering with moral hackers and builders, WordPress guarantees its platform stays safe and faithful.
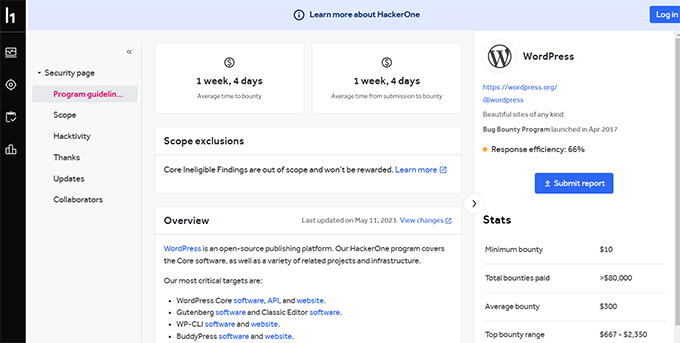
The respectable WordPress computer virus bounty program is hosted on HackerOne, the place safety researchers can publish their findings.
Pieces integrated in this system’s scope are:
- Core WordPress device
- The WordPress.org website online (together with all subdomains)
- GlotPress (the interpretation supervisor utilized by the WordPress Translations challenge)
- Legitimate WordPress plugins (plugins indexed at the WordPress.org profile)
- *.WordCamp.org (all WordCamp internet sites)
- The WordPress Basis
- bbPress Core (a sister challenge of WordPress that provides boards to internet sites)
This system’s respectable scope web page supplies a complete checklist of what’s integrated. This checklist guarantees that researchers focal point on spaces important to the WordPress ecosystem’s safety.
The WordPress safety group in moderation opinions all studies. Legitimate submissions are rewarded in line with the severity of the problem. Rewards rely at the vulnerability’s affect, starting from public popularity to financial payouts.
Moreover, WordPress makes use of computer virus bounty systems throughout explicit trying out stages, such because the WordPress 6.4 Beta Malicious program Bounty Program. Those efforts be sure that new options and updates are completely vetted earlier than free up.
What’s the Distinction Between the Malicious program Bounty Program and Reporting Insects in WordPress?
WordPress encourages customers to record insects to assist toughen the platform. Alternatively, there’s a transparent distinction between reporting insects during the WordPress computer virus bounty program and the use of the computer virus reporting pointers defined within the Core Guide.
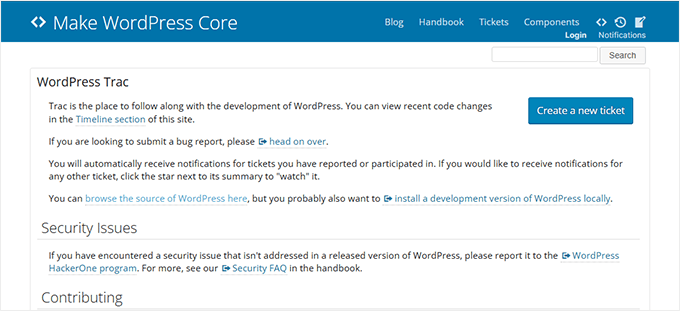
The computer virus bounty program focuses particularly on safety vulnerabilities. In case you find a doable factor that might compromise a website online’s safety, comparable to unauthorized get admission to or knowledge leaks, you will have to record it during the computer virus bounty program.
This guarantees the WordPress safety group handles the problem and, if legitimate, rewards accordingly.
Then again, the Core Guide pointers are designed to record normal insects in WordPress core, plugins, or subject matters.
Those come with problems like damaged options, surprising habits, or compatibility issues. Whilst those insects are necessary to handle, they don’t normally pose a safety chance and aren’t eligible for rewards during the computer virus bounty program.
Why Does WordPress Use a Malicious program Bounty Program?
A computer virus bounty program permits WordPress to proactively establish and deal with safety vulnerabilities, ensuring that the platform stays strong and safe.
WordPress powers greater than 43% of all internet sites on the web, together with big-name manufacturers, executive internet sites, or even best universities.
With hundreds of thousands of internet sites depending on WordPress, safety is all the time a best precedence. One benefit of being open-source device is that the code in the back of WordPress is to be had to any person.
As extremely fashionable internet device, WordPress supply code is already reviewed completely by means of volunteers, large firms, and its personal very huge person base.
Alternatively, there may be nonetheless a possibility that any person with malicious intent may in finding suave techniques to compromise the device.
Similar Submit: The Historical past of WordPress
One of the crucial largest benefits of the computer virus bounty program is the involvement of the worldwide safety neighborhood.
By way of encouraging moral hackers and builders to check the platform, WordPress advantages from numerous views and talents that assist discover problems that conventional trying out may omit.
This proactive manner additionally is helping WordPress construct agree with with the general public. Customers and companies really feel assured realizing the platform takes safety severely and works actively to toughen it.
For builders, it’s a chance to give a contribution to WordPress, which is without doubt one of the largest open-source device tasks on this planet.
Advantages of Malicious program Bounty Techniques for Aspiring Builders
Taking part in a computer virus bounty program is an unbelievable studying alternative for aspiring builders. Right here’s what it will let you reach.
- Discover real-world demanding situations and toughen your coding talents.
- Be informed the significance of cybersecurity and easy methods to save you vulnerabilities.
- Know how internet sites and packages paintings by means of trying out them for problems.
- Broaden talents to suppose like a hacker and establish safety gaps.
- Exhibit your experience by means of reporting vulnerabilities and incomes popularity.
- Construct your portfolio and acquire credibility within the developer neighborhood.
- Open doorways to profession alternatives in cybersecurity and construction.
Even though you don’t discover a vulnerability instantly, trying out and exploring will let you acquire helpful enjoy.
It’s now not with regards to rewards; it’s about rising as a developer, contributing to the WordPress ecosystem, and making the internet more secure for everybody.
Malicious program Bounty Techniques for WordPress Plugins and Topics
Certainly one of WordPress’s largest benefits is its huge ecosystem of plugins. Over 59,000 of them are within the unfastened WordPress.org plugin listing by myself.
Many smaller WordPress plugins depend at the WordPress plugin evaluation group to accomplish a safety evaluation. Moral hackers can divulge problems to the plugin evaluation group and not using a financial praise or acknowledgment.
As well as, third-party safety platforms like Patchstack and Wordfence run computer virus bounty systems with rewards.
Those platforms then responsibly divulge the problem to the plugin authors and supply them sufficient time to free up a repair.
Because of this it’s tremendous necessary to stay your WordPress plugins present by means of putting in updates once they’re to be had.
Getting Began with WordPress Malicious program Bounty Techniques
Getting eager about WordPress computer virus bounty systems is a wonderful option to give a contribution to the platform whilst bettering your talents and incomes rewards. Platforms like HackerOne, Patchstack, and Wordfence are nice beginning issues for builders and moral hackers.
In case you’re concerned about securing WordPress plugins and subject matters, then various builders welcome computer virus studies via their strengthen channels or boards.
Taking part in third-party computer virus bounty systems too can mean you can record vulnerabilities responsibly whilst incomes popularity or rewards.
Listed below are some fast tricks to get began:
- Get yourself up to speed with this system scope and regulations earlier than beginning.
- All the time apply accountable disclosure practices when reporting insects.
- Use equipment like browser developer consoles and vulnerability scanners for trying out.
- Center of attention on studying and bettering, despite the fact that your studies aren’t straight away approved.
- Sign up for developer communities to proportion reviews and be told from others.
Whether or not you’re a seasoned developer or simply getting began, collaborating in computer virus bounty systems is a rewarding option to develop your talents and make the internet more secure for everybody.
Bonus Sources: WordPress Safety Guides
Listed below are a couple of further sources to toughen WordPress safety on your internet sites:
- How one can Carry out a WordPress Safety Audit (Whole Tick list)
- The Final WordPress Safety Information – Step-by-Step
- eCommerce Safety Guidelines: How one can Protected Your WordPress Retailer
- Maximum Commonplace WordPress Mistakes and How one can Repair Them
- Necessary Tricks to Give protection to Your WordPress Admin House (Up to date)
We are hoping this newsletter helped you recognize the position of computer virus bounty systems and the way they give a contribution to creating WordPress a safe platform. You might also need to see our information on developing safe touch bureaucracy or be told easy methods to again up your WordPress website.
In case you appreciated this newsletter, then please subscribe to our YouTube Channel for WordPress video tutorials. You’ll additionally in finding us on Twitter and Fb.
The put up What Is a WordPress Malicious program Bounty Program? (& How one can Get Concerned) first seemed on WPBeginner.
WordPress Maintenance