Browser cookies are very important for WordPress web sites. They deal with login periods, permit shape submissions, and enhance key person interactions. When those tiny information packets fail to paintings correctly, you’ll be able to stumble upon irritating mistakes that can lock you out of admin panels, ruin touch paperwork, or create never-ending redirect loops.
One of the crucial commonplace cookie-related issues is the ‘cookies are blocked’ error. It steadily seems abruptly, occasionally after a regimen trade in your web site.
This information supplies sensible, actionable answers for solving the ‘cookies are blocked’ error in WordPress, together with pointers for resolving different connected cookie problems.
Figuring out WordPress cookies and the way they paintings
WordPress depends on cookies for authentication and consultation control. Whilst you log into the admin dashboard, it units authentication cookies to make sure your identification on next web page quite a bit. With out them, WordPress can’t deal with login states or keep in mind person personal tastes.
Listed here are commonplace WordPress cookies:
wordpress_[hash]. Shops authentication main points for the WordPress admin display screen.wordpress_logged_in_[hash]. Signifies login standing and person identification.wp-settings-{time}-[UID]. Saves private dashboard personal tastes.comment_author_[hash]. Recollects commenter knowledge.
Cookie-related mistakes generally happen when PHP sends output prior to WordPress units its headers. This untimely output prevents right kind cookie transmission and triggers quite a lot of problems, similar to:
- Login screw ups with the ‘cookies are blocked’ message.
- Consultation timeout mistakes all through shape submissions.
- Redirect loops when getting access to the
wp-adminweb page. - Remark paperwork shedding user-submitted information.
Figuring out this habits is helping establish cookie issues. Maximum problems stem from timing conflicts the place code runs too early prior to WordPress has a possibility to set cookies.
The right way to troubleshoot the ‘Cookies are blocked because of sudden output’ error
The mistake signifies that one thing is sending information to the browser prior to WordPress has a possibility to set its cookies. Solving it calls for a scientific take a look at to spot the supply of this untimely output.
Chances are you’ll see this mistake within the following eventualities:
- After you edit theme information or
wp-config.php. - Following plugin installations or updates.
- When migrating websites between servers.
- After enhancing PHP configurations.
Let’s stroll via commonplace reasons and how you can repair them.
Take a look at for whitespace in PHP information
Search for clean traces or areas prior to the hole tag or after the final ?> tag in key information, particularly in wp-config.php.
There are many techniques to do that: Protected Document Switch Protocol (SFTP), WordPress’ personal record editor (if you'll be able to get admission to it), and extra:
Even a unmarried area can cause this mistake:
// WRONG (Observe the distance prior to opening tag)
For the final tag, it’s standard to overlook it fully for natural PHP information:
// GOOD (Little need for a final tag)
outline('WP_DEBUG', true);
/* That is all, prevent enhancing! */
require_once(ABSPATH . 'wp-settings.php');
// PROBLEMATIC (A final tag with possible trailing whitespace)
outline('WP_DEBUG', true);
/* That is all, prevent enhancing! */
require_once(ABSPATH . 'wp-settings.php');
?> It’s a easy catch that may clear up myriad cookie issues.
Scan for Byte Order Mark (BOM) characters
BOM characters are invisible markers that some textual content editors upload to information, and they may be able to intrude with cookie dealing with in WordPress. It is a easy encoding factor you'll be able to repair along with your code editor or command line.
In maximum editors, you’ll to find the record encoding choice within the standing bar or menu. Make certain the record is stored as UTF-8 with out BOM.
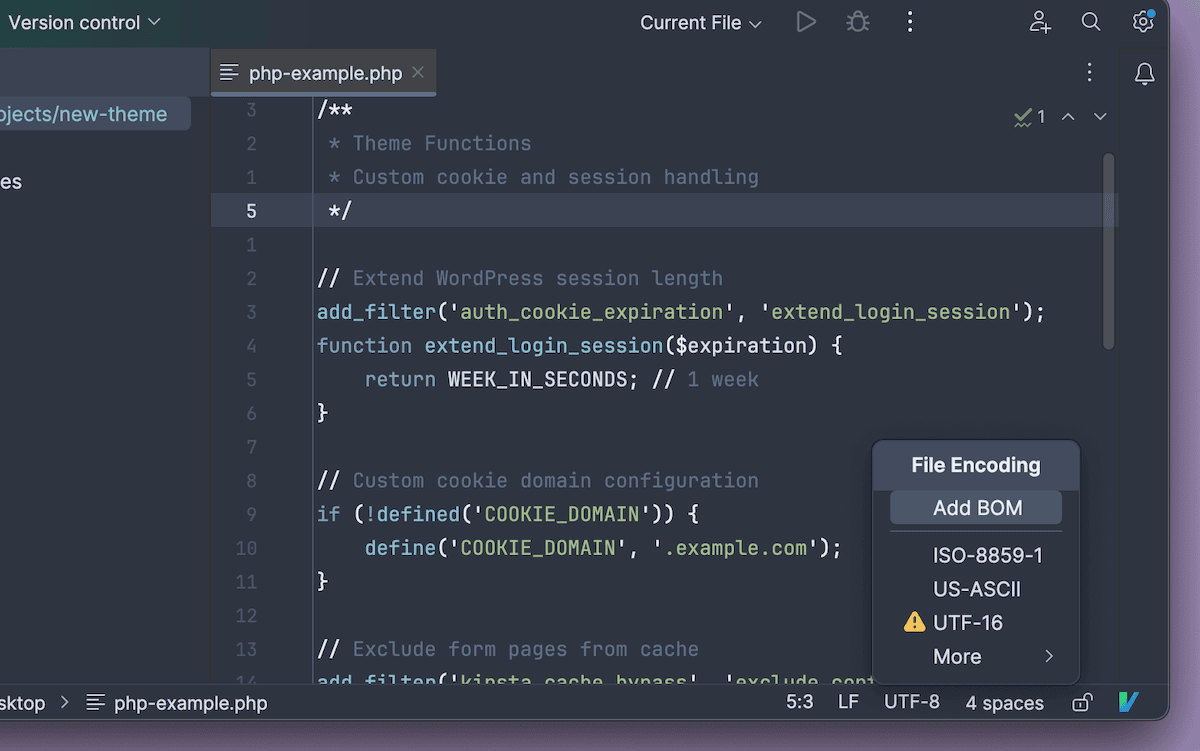
You'll additionally stumble on BOM characters with the command line:
# Take a look at for BOM in PHP information
to find . -type f -name '*.php' -exec record {} ; | grep "with BOM"To mend them, open every flagged record and re-save it with UTF-8 (with out BOM) decided on.
Determine plugin output problems
A vintage manner of understanding any WordPress error is to deactivate all plugins in the course of the WordPress admin display screen or rename the plugins folder:
# Rename plugins folder to deactivate all plugins
mv wp-content/plugins wp-content/plugins_backupIf the mistake disappears, you'll be able to reactivate plugins one at a time to spot the perpetrator. Not unusual plugin problems come with plugins that echo their output prior to headers debug messages that show all through initialization, and suboptimal plugin activation routines.
Read about theme record implementations
Some other standard WordPress error repair is to modify to a default WordPress theme (like Twenty Twenty-4) to peer if the mistake resolves. If it does, investigate cross-check your present theme’s purposes.php record for untimely output:
// WRONG (Output prior to headers)
The straightforward answer here's to verify all code is inside a serve as fairly than ‘free’ inside the record.
Resolving ‘Cookies are blocked or no longer supported via your browser’ mistakes
This model of the cookie error issues to browser-side problems fairly than server issues. In contrast to the ‘sudden output’ error, this factor calls for a unique (much less technical) troubleshooting method.
Google Chrome
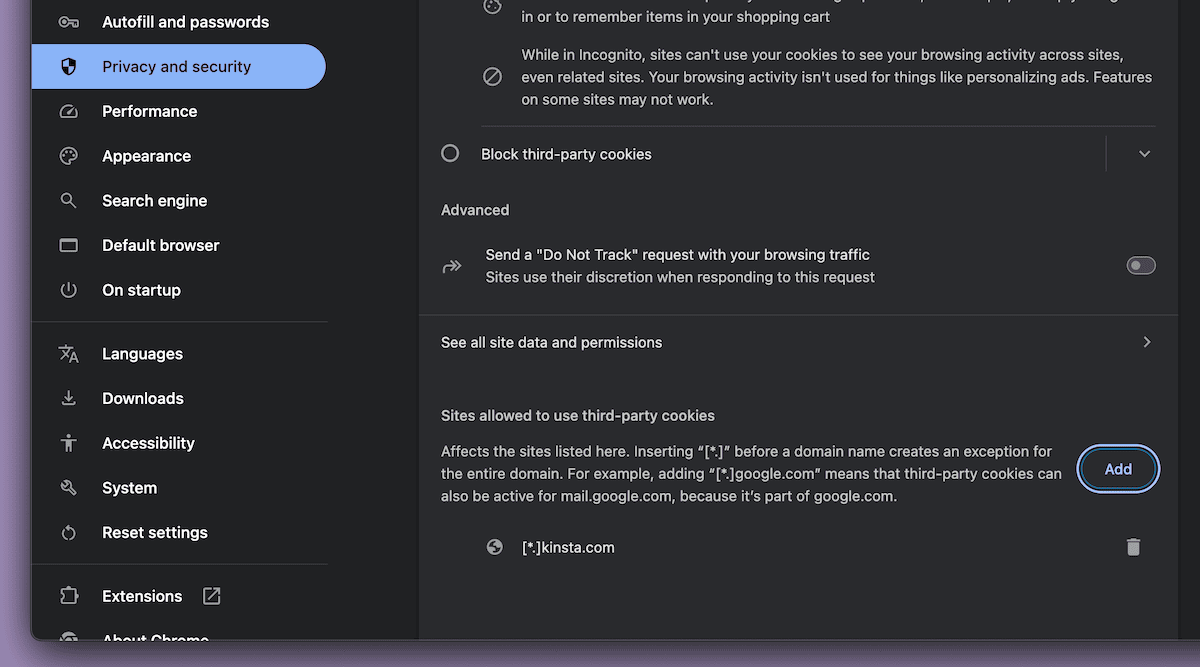
For Google Chrome, move to Settings > Privateness and safety > 3rd-party cookies and:
- Click on Upload subsequent to Websites allowed to make use of third-party cookies.
- Input your area (e.g., [*.]yourdomain.com).
- Allow Together with third-party cookies in this web site.
Microsoft Edge
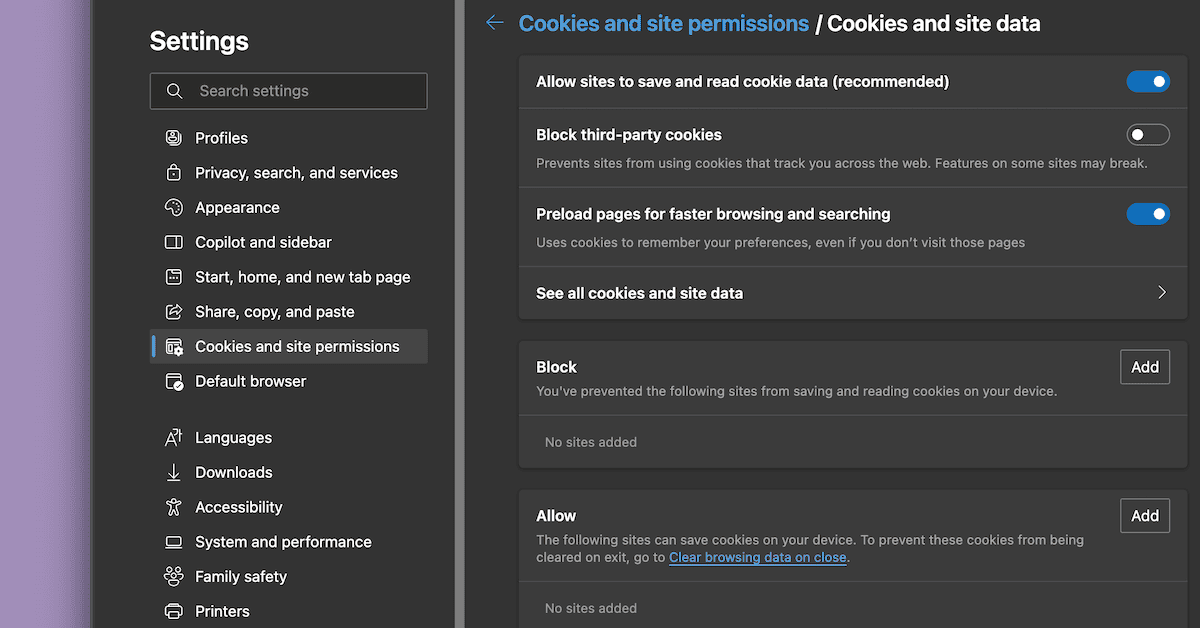
With Microsoft Edge, those choices are inside the Cookies and web site permissions settings web page:
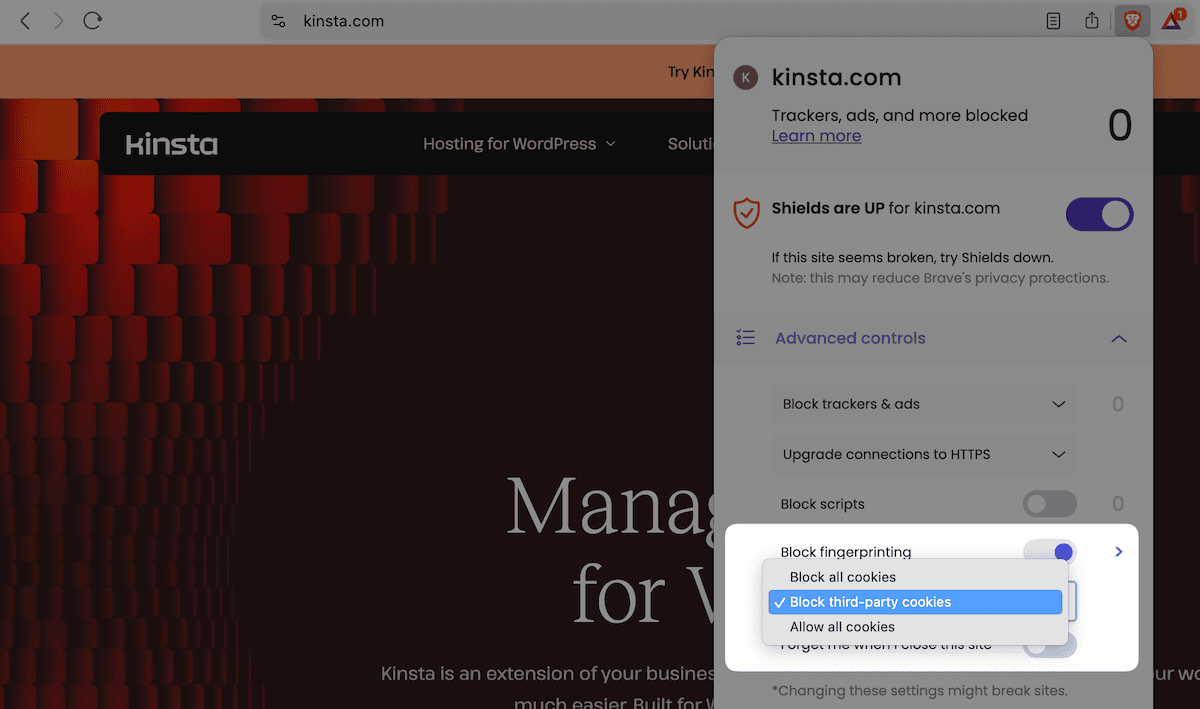
Courageous
For Courageous, you'll be able to click on at the Defend icon within the deal with bar, open up the Block third-party cookies drop-down menu, and make a choice the choice you want:
Firefox
For Firefox, get admission to cookie settings via Settings > Privateness and Safety > Cookies and Web page Information:
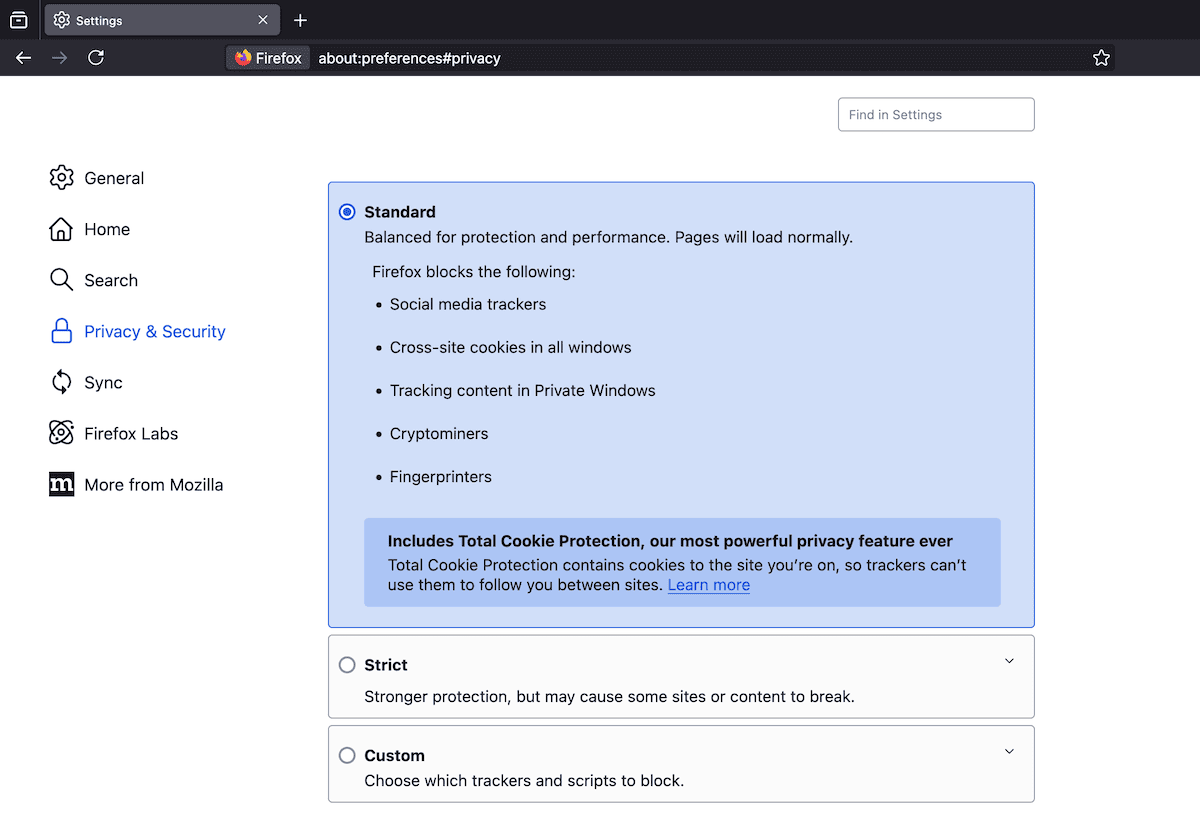
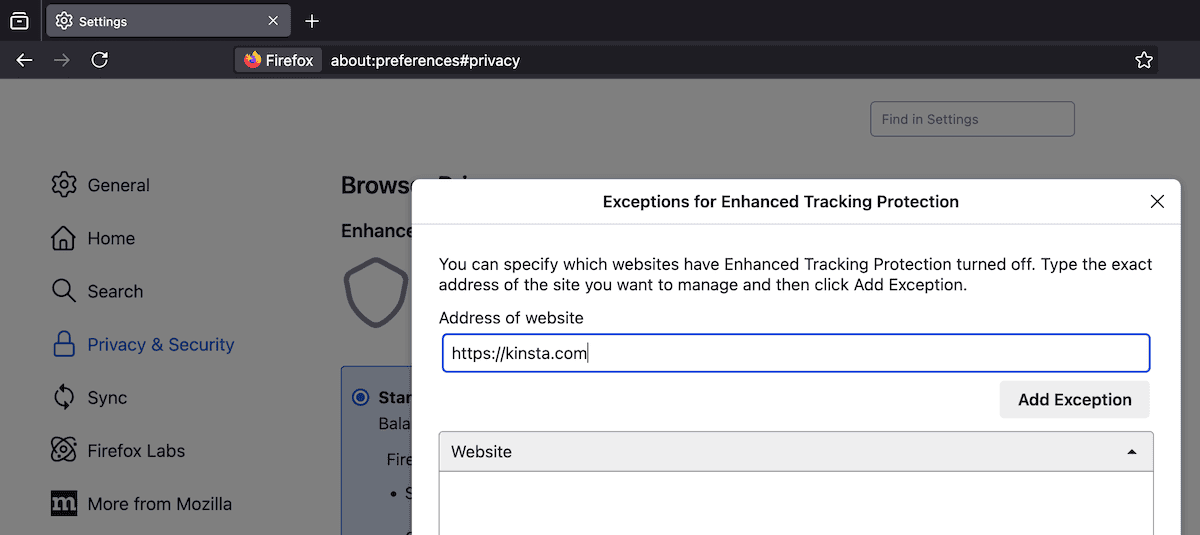
Same old mode is just right for balanced privateness and capability. For particular web site exceptions, click on the Organize Exceptions button and upload your WordPress web site’s URL:
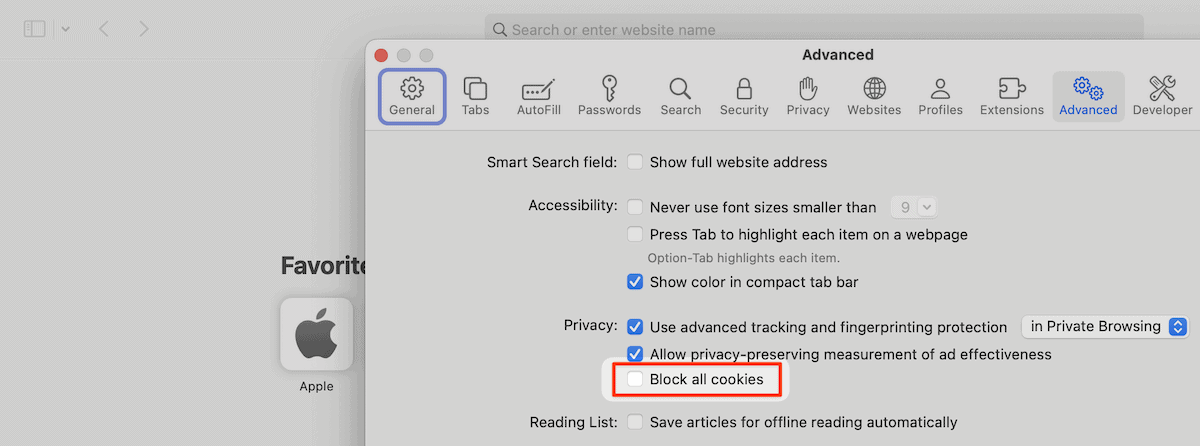
Safari
Safari has an choice inside its Settings > Complicated display screen. This provides a Block all cookies choice, which you must uncheck:
In brief, irrespective of the browser you select, there will likely be an choice inside its settings to modify the way it handles cookies.
Safety plugin interference
Your WordPress safety plugins can occasionally put in force competitive cookie insurance policies that intrude along with your setup. There are 3 commonplace war issues to test:
- WAF (Internet Software Firewall) laws that block cookies.
- Consultation control that overrides WordPress’ defaults.
- Geographic restrictions that impact cookie supply.
Chances are you'll already perceive if a safety plugin is the reason for a ‘cookies are blocked’ error when you briefly deactivate your plugins. If a safety plugin is a possible motive, you'll be able to alter settings fairly than disable it. For instance:
// Instance: Whitelist WordPress admin cookies in a safety plugin
add_filter('security_plugin_allowed_cookies', serve as($cookies) {
$cookies[] = 'wordpress_logged_in_*';
$cookies[] = 'wordpress_sec_*';
$cookies[] = 'wp-settings-*';
go back $cookies;
});On the other hand, the simpler method is to touch the plugin’s developer and verify whether or not there’s one thing they may be able to do. The principle level is that you need to stay a safety plugin energetic, as no longer having one may just do extra hurt than just right.
Server configuration have an effect on
Now and again, server settings can masquerade as browser problems. You'll take a look at some server-side configurations to unravel this, such because the PHP consultation settings to your php.ini record:
consultation.cookie_secure = On ; Just for HTTPS websites
consultation.cookie_httponly = On ; Prevents JavaScript get admission to
consultation.cookie_samesite = Lax ; Move-site request coverage
You'll additionally take a look at internet server headers that would possibly impact cookies. For Nginx servers (Kinsta’s selection), glance to make sure any cookie-related headers:
# Instance Nginx configuration
location ~ .php$ {
fastcgi_param HTTP_COOKIE $http_cookie;
fastcgi_pass_header Set-Cookie;
}If you'll be able to’t get admission to your Nginx configuration information and use Kinsta’s WordPress webhosting, the Kinsta enhance crew can assist. The crew too can take a look at your server-level configs when you be afflicted by redirect loops.
The right way to repair WordPress login redirect loops
Redirect loops create a irritating cycle through which WordPress assists in keeping redirecting between the login web page and the admin dashboard with out a success person authentication. This normally occurs when authentication cookies fail to persist between requests.
WordPress tests for legitimate authentication cookies after login. If the take a look at fails, it redirects customers again to the wp-login.php web page.
To unravel this sort of factor, permit WordPress debugging and track your debug.log record to spot redirect patterns and cookie states all through authentication makes an attempt.
Take a look at WordPress URL settings
The commonest explanation for redirect loops is a distinction between the house and web site URL inside WordPress’ settings:
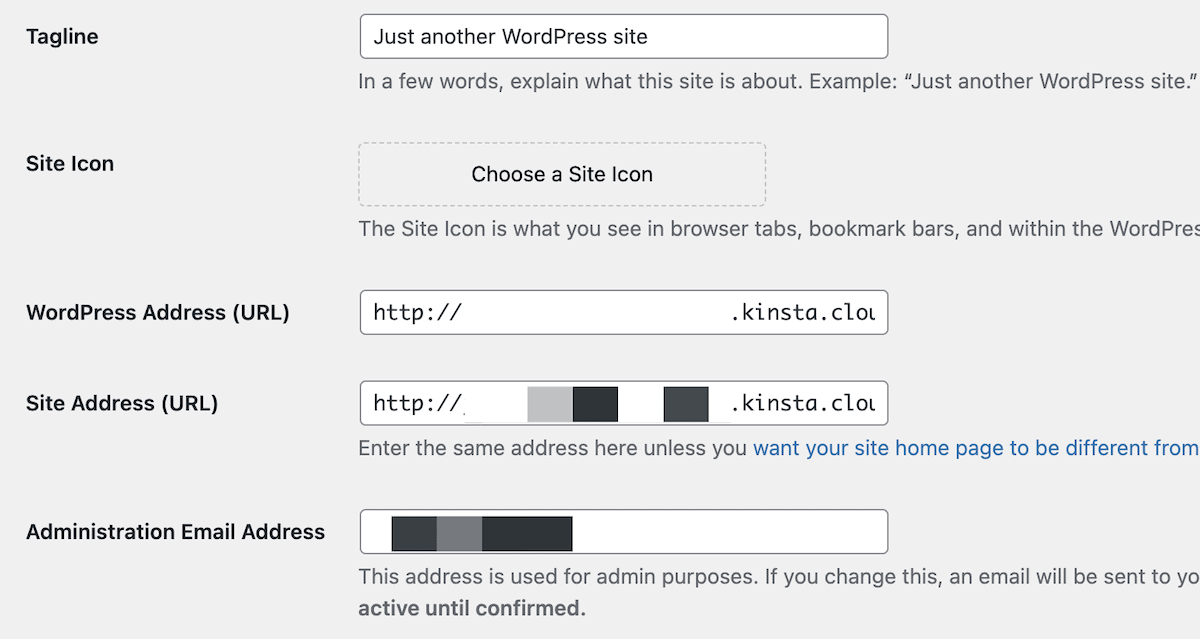
In brief, those want to be a precise fit. You'll do it in the course of the WordPress backend or trade the values in wp-config.php:
outline('WP_HOME', 'https://kinsta.com');
outline('WP_SITEURL', 'https://kinsta.com');You must make certain that each values use an identical protocols (HTTP as opposed to HTTPS) and domain names (without or with www) right here. Combined content material warnings too can motive cookie mistakes, which relate in your SSL settings. Checking and solving blended content material mistakes is a breeze.
Outline the cookie area explicitly
When WordPress creates authentication cookies, it wishes to grasp the precise area scope for the ones cookies to serve as correctly.
With out particular configuration, WordPress makes an attempt to decide the ‘cookie area’ itself, which will fail in advanced webhosting setups, subdomain installations, or when the use of non-standard area configurations.
To unravel the problem, you'll be able to upload particular cookie area settings to wp-config.php:
// For normal domain names
outline('COOKIE_DOMAIN', 'kinsta.com');
// For subdomains wanting mum or dad area cookies
outline('COOKIE_DOMAIN', '.kinsta.com');
// For particular subdirectory installations
outline('ADMIN_COOKIE_PATH', '/');
outline('COOKIEPATH', '/');
outline('SITECOOKIEPATH', '/');Those settings will likely be important if WordPress runs in subdirectories, when you organize Multisite networks, or in case your web site operates throughout a couple of subdomains.
The cookie area will inform the browser which portions of your web site can learn and write particular cookies. This will likely make login patience and consultation control extra constant.
The right way to clear up ‘consultation expired’ mistakes in WordPress paperwork
Consultation expiration mistakes can also be irritating whilst you try to publish paperwork, specifically on touch pages, checkout processes, and multi-step paperwork. Those mistakes happen when WordPress nonces expire or when consultation cookies fail to deal with a state between shape show and submission.
Those tokens expire after a suite length — for WordPress, that is normally 24-48 hours — regardless that the real validity window is shorter for safety causes.
You'll optimize your PHP consultation settings for dealing with paperwork in the course of the php.ini record to your server:
; php.ini changes
consultation.gc_maxlifetime = 3600 ; 1 hour
consultation.cookie_lifetime = 0 ; Till browser closes
consultation.cache_expire = 180 ; 3 hoursYou may also to find caching conflicts on the subject of your paperwork. Web page caching can steadily motive consultation mistakes when serving stale nonces. You'll upload the next in your theme’s purposes.php record:
// Upload this in your theme's purposes.php record
// Exclude shape pages from cache
serve as exclude_form_pages_from_cache($bypass) {
// Touch shape pages
if (is_page(array('touch', 'quote-request'))) {
go back true;
}
// WooCommerce checkout
if (function_exists('is_checkout') && is_checkout()) {
go back true;
}
go back $bypass;
}
add_filter('kinsta_cache_bypass', 'exclude_form_pages_from_cache');In case you get in contact with Kinsta enhance, the crew can upload exclusions to the Nginx cache for you.
Running with particular shape capability
Among the best method for combating consultation expired mistakes specializes in 3 confirmed answers: cache exclusions, consultation extension, and plugin-specific configurations.
WooCommerce checkout paperwork can also be at risk of consultation problems as a result of they deal with cart information and person knowledge throughout a couple of pages. WooCommerce makes use of its consultation control machine:
// Upload this in your theme's purposes.php record
// Prolong WooCommerce consultation period
add_filter('wc_session_expiration', serve as() {
go back 7 * DAY_IN_SECONDS; // 7 days as an alternative of default 2 days
});
// Make sure WooCommerce pages bypass cache
add_action('init', serve as() {
if (function_exists('is_cart') && (is_cart() || is_checkout() || is_account_page())) {
if (!outlined('DONOTCACHEPAGE')) {
outline('DONOTCACHEPAGE', true);
}
}
});Multi-step and AJAX paperwork steadily enjoy consultation problems because of caching conflicts. A competent generic method works throughout maximum shape plugins:
// Upload this in your theme's purposes.php record
// Prolong WordPress nonce lifetime globally
add_filter('nonce_life', serve as() {
go back 12 * HOUR_IN_SECONDS; // 12 hours as an alternative of 24 hours for higher reliability
});
// Exclude pages with paperwork from cache via URL trend
serve as exclude_form_urls_from_cache($bypass) {
$request_uri = $_SERVER['REQUEST_URI'];
// Not unusual shape web page patterns
if (strpos($request_uri, '/touch') !== false ||
strpos($request_uri, '/quote') !== false ||
strpos($request_uri, '/software') !== false ||
isset($_POST['action'])) { // Any AJAX shape submission
go back true;
}
go back $bypass;
}
add_filter('kinsta_cache_bypass', 'exclude_form_urls_from_cache');Gravity Paperwork supplies essentially the most dependable consultation control amongst touch shape plugins:
// Upload this in your theme's purposes.php record
// Prolong incomplete submission garage time
add_filter('gform_incomplete_submissions_expiration_days', serve as($days) {
go back 7; // Stay incomplete submissions for 7 days as an alternative of 30
});
// Exclude Gravity Paperwork AJAX from cache
add_action('init', serve as() {
if (isset($_POST['gform_ajax']) || (isset($_GET['page']) && $_GET['page'] === 'gf_entries')) {
if (!outlined('DONOTCACHEPAGE')) {
outline('DONOTCACHEPAGE', true);
}
}
});On the subject of shape consultation control and resolving cookie mistakes, chances are you'll no longer have a hook or filter out to paintings with. The most productive method is to touch the developer at once to establish your choices.
The right way to save you and troubleshoot WordPress cookie mistakes
One of the crucial proactive techniques to stop cookie mistakes in your WordPress web site is via following established coding requirements. Your number one activity is to set cookies prior to any output reaches the browser. You'll do that via checking the header standing prior to atmosphere cookies:
// At all times take a look at headers_sent() prior to atmosphere cookies
if (!headers_sent()) {
setcookie('custom_cookie', $worth, time() + 3600, COOKIEPATH, COOKIE_DOMAIN);
}You'll seize any unintentional output prior to you ship headers via buffering. That is precious when operating with third-party code that would possibly echo content material:
// Use output buffering for protection
ob_start();
// Your theme/plugin code that would possibly produce output
ob_end_flush();
Correct hook timing permit you to set cookies on the suitable level within the WordPress lifecycle. As an example, the init motion fires after WordPress quite a bit however prior to sending headers, which is perfect:
// Correct plugin initialization timing
add_action('init', serve as() {
// Cookie operations right here, no longer previous
if (!is_admin()) {
wp_set_auth_cookie($user_id);
}
});Your server-level PHP settings can have an effect on cookie habits. That is the place you'll be able to additional configure your php.ini record to regulate how PHP handles periods, set output buffering, and put in force cookie safety:
; Really helpful php.ini settings with explanations
output_buffering = 4096 ; Captures unintentional output prior to headers
consultation.cookie_secure = On ; Forces HTTPS-only cookies for safety
consultation.cookie_httponly = On ; Prevents JavaScript get admission to to cookies
consultation.cookie_samesite = Lax ; Protects towards CSRF assaults
consultation.use_strict_mode = On ; Prevents consultation fixation assaultsNginx configuration at once impacts how cookies glide between WordPress and guests’ browsers. Since Kinsta makes use of Nginx as its internet server, that is any other house of optimization for cookie-related problems. Necessarily, you’ll want to set an abundant buffer measurement so Nginx can procedure the information prior to dealing with headers.
Greater buffer sizes save you Upstream despatched too large header mistakes that may happen with advanced WordPress websites the use of a couple of plugins. When those buffers are too small, Nginx would possibly truncate headers or fail to procedure cookies correctly.
Safety headers on the Nginx point additionally supply an extra layer of coverage for all cookies set via your WordPress web site.
WordPress debug logging
Debug logging can display you WordPress’s inside operations, however the usual error messages don’t include sufficient knowledge for troubleshooting. The debug log can seize the entire context:
// Debugging in wp-config.php with strategic logging
outline('WP_DEBUG', true);
outline('WP_DEBUG_LOG', true);
outline('WP_DEBUG_DISPLAY', false);
outline('SCRIPT_DEBUG', true); // Makes use of non-minified scripts for higher debugging
outline('SAVEQUERIES', true); // Tracks database queries that would possibly impact periods
// Customized cookie logging to track execution glide
add_action('init', serve as() {
if (outlined('WP_DEBUG') && WP_DEBUG) {
error_log('=== Cookie Debug Get started ===');
error_log('Cookie state: ' . print_r($_COOKIE, true));
error_log('Headers despatched: ' . (headers_sent($record, $line) ? "Sure at $record:$line" : 'No'));
error_log('Request URI: ' . $_SERVER['REQUEST_URI']);
error_log('=== Cookie Debug Finish ===');
}
});This captures your complete image of a cookie error. The SCRIPT_DEBUG consistent forces WordPress to make use of non-minified JavaScript and CSS information, which makes it more straightforward to spot interfering scripts. SAVEQUERIES will observe all database queries that can assist you establish database problems on the subject of the consultation.
Browser developer equipment inspection
Fashionable browser DevTools permit you to debug cookie problems in genuine time. The Community tab finds the precise headers being despatched and won, whilst the Software/Garage tab displays present cookie states.
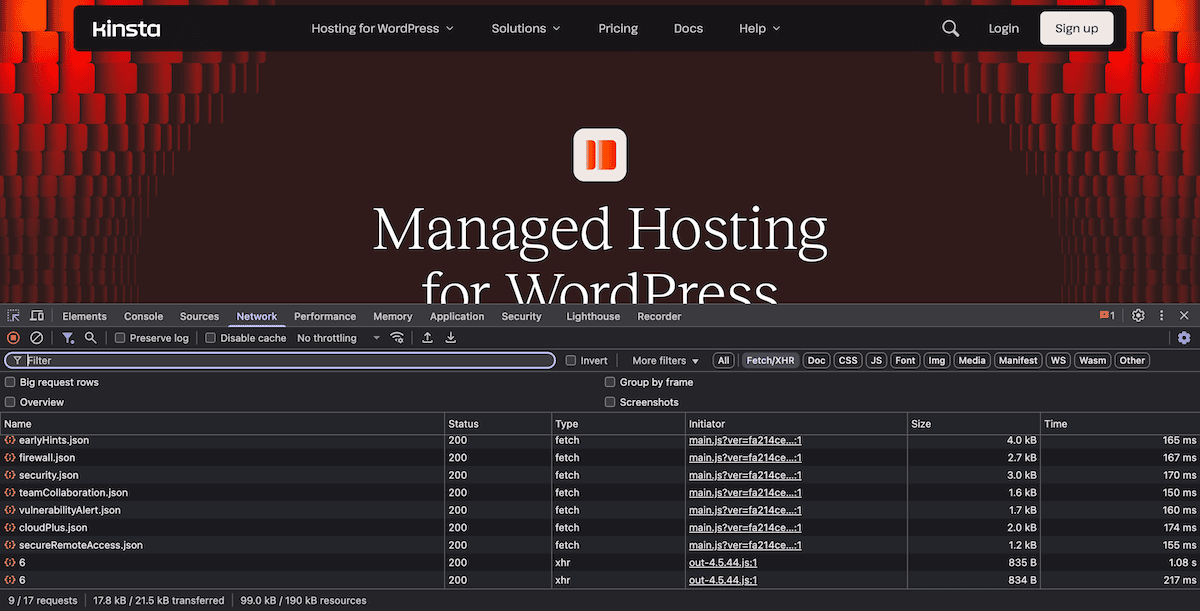
The use of the console offers you a programmatic solution to examine and manipulate cookies all through your troubleshooting:
// Create an in depth cookie file
console.desk(file.cookie.break up(';').map(c => {
const [name, value] = c.trim().break up('=');
const decoded = decodeURIComponent(worth);
go back {
call,
worth: decoded,
period: worth.period,
encoded: worth !== decoded
};
}));
// Observe cookie adjustments in real-time
const cookieObserver = new MutationObserver(() => {
console.log('Cookie trade detected:', new Date().toISOString());
console.log('New state:', file.cookie);
});
// Stay up for any DOM adjustments that would possibly cause cookie updates
cookieObserver.follow(file.documentElement, {
subtree: true,
attributes: true,
characterData: true
});This will likely disclose the timing problems that motive cookie mistakes. For instance, the Community tab displays if Set-Cookie headers arrive too overdue within the reaction, whilst the Software tab will show present cookie values, domain names, paths, and expiration instances.
The MutationObserver method caches dynamic cookie adjustments that would possibly happen via JavaScript. This will likely mean you can establish client-side code this is interfering with WordPress cookies.
Question Observe integration
To move past WordPress debugging and logging, you'll be able to use Question Observe. For cookie debugging, it finds when headers are despatched and which code triggers untimely output:
// Customized Question Observe collector for complete cookie debugging
elegance QM_Collector_Cookies extends QM_Collector {
public $identity = 'cookies';
public serve as procedure() {
// Seize present cookie state
$this->information['cookies'] = $_COOKIE;
// Determine the place headers have been despatched
$this->information['headers_sent'] = headers_sent($record, $line);
$this->information['output_location'] = $record . ':' . $line;
// Monitor output buffer standing
$this->information['ob_level'] = ob_get_level();
$this->information['ob_status'] = ob_get_status(true);
// Document WordPress motion series
$this->information['current_action'] = current_action();
$this->information['did_action'] = array(
'init' => did_action('init'),
'wp_loaded' => did_action('wp_loaded'),
'template_redirect' => did_action('template_redirect')
);
}
}
// Check in collector with Question Observe
add_filter('qm/creditors', serve as($creditors) {
$creditors['cookies'] = new QM_Collector_Cookies();
go back $creditors;
});This practice collector plugs into Question Observe and provides a devoted panel for debugging cookies. It doesn’t simply display the state of cookies — it offers you complete context round possible problems.
You’ll additionally see whether or not output buffering is energetic and what point it’s at. On best of that, the motion series pinpoints precisely the place in WordPress’s execution glide the issue is occurring.
Plugin war solution
Automatic trying out can catch insects on the subject of cookies prior to they succeed in manufacturing. Unit assessments will test that your code units cookies as it should be and handles edge instances correctly.
Systematic plugin trying out will display up conflicts with out the everyday guide deactivation. Automating the method will save troubleshooting time and provide you with a definitive resolution about which plugins motive cookie problems:
// Automatic plugin war trying out with detailed reporting
serve as test_plugin_conflicts() {
$active_plugins = get_option('active_plugins');
$problematic_plugins = array();
// Create a trying out serve as particular in your factor
$test_cookie_function = serve as() {
// Transparent any present output
ob_clean();
// Try to set a check cookie
if (!headers_sent()) {
setcookie('test_cookie', 'worth', time() + 3600, '/');
go back true;
}
go back false;
};
foreach ($active_plugins as $plugin) {
// Deactivate unmarried plugin
deactivate_plugins($plugin);
// Transparent any cached information
wp_cache_flush();
// Check cookie capability
if ($test_cookie_function()) {
$problematic_plugins[] = $plugin;
error_log("Plugin inflicting cookie factor: " . $plugin);
}
// Reactivate plugin
activate_plugins($plugin);
}
// Generate detailed file
if (!empty($problematic_plugins)) {
error_log("=== Cookie Struggle Record ===");
error_log("Problematic plugins: " . implode(', ', $problematic_plugins));
error_log("General conflicts discovered: " . rely($problematic_plugins));
}
go back $problematic_plugins;
}Right here, the code assessments every plugin in isolation to stop false positives from plugin interactions. The cache flush guarantees blank trying out prerequisites for every plugin, and the detailed reporting is helping you prioritize which plugins to switch or reconfigure.
How Kinsta permit you to unravel WordPress cookie mistakes
Kinsta’s caching machine is designed to paintings with WordPress websites, and via extension, its cookies. In contrast to many generic hosts, Kinsta implements clever exclusions to keep away from problems with login periods or e-commerce carts. For instance:
- Kinsta’s cache machine robotically bypasses caching for logged-in customers in response to WordPress authentication cookies.
- Buying groceries cart cookies from WooCommerce and Simple Virtual Downloads are excluded from caching to verify right kind cart habits.
This implies you received’t face the average factor the place caching prevents cookies from operating correctly. The machine intelligently serves cached content material to nameless guests whilst making sure logged-in customers and shoppers see customized, uncached content material.
The MyKinsta dashboard offers you some basic settings for dealing with cookies, however the APM Software can also be an asset when resolving cookie mistakes.
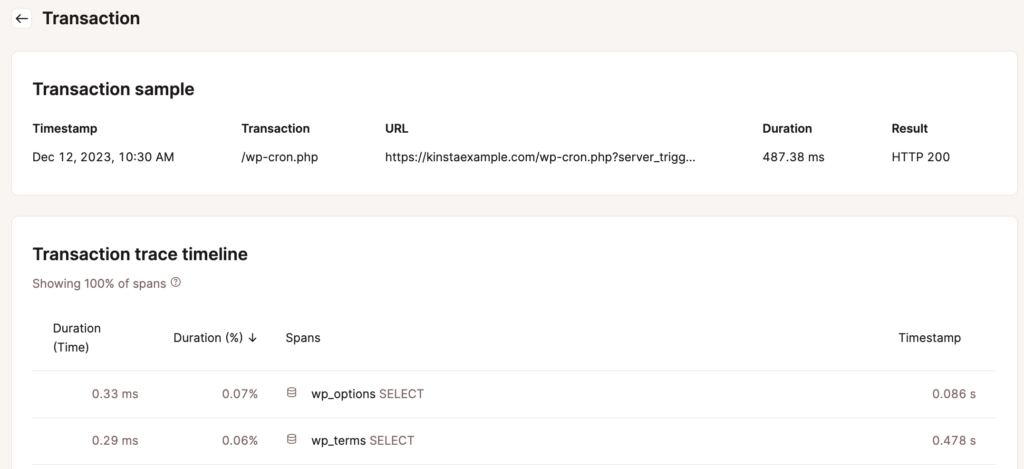
You have got a couple of techniques to track for cookie-related problems right here:
- Uptime tests to stumble on authentication issues.
- Error logging that captures cookie-related warnings.
- Efficiency metrics that disclose cookie-dependent slowdowns.
In case you mix this with Kinsta’s efficiency optimization, you've gotten a powerful surroundings the place cookie mistakes infrequently happen, and once they do, they’re more straightforward to unravel.
Past this, Kinsta’s enhance crew can help with extra advanced cookie configurations. For instance:
- Putting in customized cache exceptions for particular cookie patterns.
- Configuring server settings to optimize cookie dealing with.
- Troubleshooting edge instances similar to Multisite cookie domain names.
The crew too can suggest plugin answers appropriate with Kinsta’s surroundings, and steer you clear of the ones answers no longer fitted to Kinsta’s webhosting.
Abstract
The ‘cookies are blocked’ error in WordPress will stem from quite a lot of resources, however maximum percentage commonplace answers. There are some systematic troubleshooting steps you'll be able to apply to place issues proper in your web site:
- Take away whitespace and BOM characters from PHP information.
- Configure right kind browser cookie settings.
- Deal with server-side consultation control.
- Exclude shape pages from caching.
- Put into effect right kind construction practices if vital.
Kinsta’s controlled webhosting surroundings simplifies many of those demanding situations via clever caching, staging environments, and specialised enhance.
If you wish to do away with cookie mistakes completely, Kinsta’s infrastructure can care for cookie control complexities robotically. It additionally supplies equipment for customized configurations when you wish to have them.
The put up The right way to repair the ‘cookies are blocked’ error (and different commonplace WordPress cookie mistakes) seemed first on Kinsta®.
WP Hosting