Disbursed Denial-of-Carrier (DDoS) assaults are certainly one of a web site’s maximum difficult threats. The collection of DDoS assaults continues to upward thrust yearly.
The This fall 2023 DDoS risk document via Cloudflare says that the corporate spotted a 117% year-over-year building up in network-layer DDoS assaults and general higher DDoS job focused on retail, cargo, and public family members internet sites all over and round Black Friday and the vacation season.
This displays that the collection of DDoS assaults is rising as they’re used towards companies and governmental establishments to salary cyber assaults. As an example, Cloudflare reported an building up in DDoS assaults following the beginning of the Israel-Hamas battle.
How DDoS assaults paintings
DDoS assaults can strike at any time and purpose to weigh down a server, carrier, or community with over the top Web site visitors, disrupting customary operations.
DDoS attackers regularly use botnets — compromised pc networks, referred to as “zombies” or “bots.” Those bots are normally inflamed with malware and regulated remotely via the attacker.
When the attacker initiates a DDoS assault, they command all of the bots within the botnet to ship an enormous quantity of requests to the objective server or community. This overwhelming inflow of site visitors exceeds the server’s capability to maintain valid requests, inflicting a slowdown or entire outage.
There are 3 forms of DDoS assaults:
- Quantity-based assaults — Those are the commonest forms of DDoS assaults. They target to saturate the bandwidth of the centered website or community. Ways come with UDP floods, ICMP floods, and different spoofed-packet floods.
- Protocol assaults —Those assaults eat server sources or intermediate conversation apparatus like firewalls and cargo balancers. Examples come with SYN (synchronize) message floods, fragmented packet assaults, and the outsized packets utilized in ping-of-death assaults.
- Software layer assaults — Those are probably the most subtle and stealthy DDoS assaults, focused on explicit packages or products and services. They generate legitimate-looking requests however in huge volumes, making distinguishing between valid site visitors and assault site visitors exhausting. Examples come with HTTP floods and Slowloris assaults, which may also be efficient at decrease request volumes than usual HTTP floods via holding server connections open.
The best way to save you DDoS assaults
Fighting DDoS assaults calls for a strategic and multi-layered way. Through combining quite a lot of strategies, you’ll be able to successfully safeguard your community and packages.
Listed below are 5 strategies that may assist save you DDoS assaults:
1. Enforce community and alertness coverage
Get started via proscribing the collection of requests a person could make for your server inside a selected period of time. As an example, should you run a web-based retailer, you’ll be able to configure your server to permit most effective 10 requests in line with 2d from any person. This is helping save you a unmarried consumer from overwhelming your server with too many requests without delay.
Subsequent, use a internet software firewall (WAF). A WAF acts like a safety checkpoint, examining incoming site visitors and blockading damaging requests whilst letting valid ones thru. For example, should you’re the usage of Cloudflare, its WAF can clear out malicious site visitors in accordance with recognized assault patterns. Steadily updating your WAF laws is a very powerful to stay alongside of new threats.
Moreover, deploy intrusion detection and prevention methods (IDPS). Those methods are like safety cameras to your community, looking at for suspicious job and routinely blockading the rest damaging. As an example, Snigger is a well-liked open-source IDPS that detects and stops assaults.
2. Leverage scalable and allotted infrastructure
The use of scalable and allotted infrastructure is helping set up and mitigate the have an effect on of DDoS assaults. Anycast community routing is a smart methodology. Consider you’ve gotten a well-liked weblog with readers everywhere the arena. Anycast routing directs incoming site visitors to a couple of knowledge facilities, so should you’re hit with numerous site visitors, it will get unfold out throughout other places, lowering the weight on any unmarried server.
Load balancers are every other great tool. They act like site visitors law enforcement officials, directing incoming site visitors to a couple of servers so no unmarried server will get crushed. For example, AWS Elastic Load Balancing can routinely distribute site visitors throughout a number of Amazon EC2 circumstances.
Content material Supply Networks (CDNs) like Akamai’s or Cloudflare’s too can play a large position. CDNs retailer copies of your web site’s content material on servers world wide. If site visitors spikes, the CDN can maintain it via serving content material from a couple of places, lowering the weight to your major server.
3. Use specialised DDoS coverage products and services
Specialised DDoS coverage products and services are like hiring a private bodyguard to your web site. Those products and services incessantly observe your site visitors and use complex tactics to filter out damaging site visitors. As an example, products and services like Cloudflare’s DDoS coverage or AWS Defend can discover and mitigate assaults in genuine time.
Those suppliers have powerful international infrastructures that may maintain even the biggest assaults. It’s like having a crew of safety mavens continuously looking at over your web site.
4. Observe and reply to site visitors anomalies
Maintaining a tally of your site visitors is a very powerful. Use real-time site visitors research gear to identify the rest ordinary. As an example, your webhosting supplier may provide analytics that mean you can observe site visitors patterns and discover anomalies. In the event you see a surprising spike in site visitors from a unmarried supply, it might point out a DDoS assault.
Arrange rate-based signals to inform you when site visitors exceeds sure limits. For example, in case your same old site visitors is 100 requests in line with minute and jumps to ten,000 requests, you’ll get an alert. Gear like Datadog mean you can arrange those signals and observe your site visitors in genuine time.
5. Enforce powerful get admission to regulate and common audits
In any case, regulate who can get admission to your community. Enforce IP blocklisting to dam recognized malicious IP addresses and IP allowlisting to permit most effective relied on addresses. As an example, you’ll be able to configure your server to dam site visitors from IP addresses flagged for malicious job prior to now.
Habits common safety audits to search out and connect vulnerabilities. That is like having a regimen scientific check-up to be sure you are in just right form. Gear like Nessus mean you can scan your community for possible weaknesses and make sure your defenses are up-to-date.
How Kinsta prevents DDoS assaults
Your webhosting supplier can play a key position in protective your website from DDoS assaults. In truth, should you use a just right webhosting supplier, they will have to maintain all of the DDoS prevention tactics indexed above.
At Kinsta, we’re dedicated to mitigating all DDoS assaults on our platform. We enforce powerful safety features to forestall those assaults, notify you in an instant if an assault happens, and lend a hand in keeping off them. Moreover, we take day-to-day automated backups of your WordPress website to make sure your knowledge is secure.
To come up with a clearer image, we requested a few of our Safety, DevOps, and SysOps engineers at Kinsta how we save you DDoS assaults. They’d so much to percentage.
Bettering Kinsta safety thru Cloudflare integration
A a very powerful element of our effort to supply our shoppers with the best possible point of safety is our Top class-Tier integration with Cloudflare. This strategic integration permits us to successfully maintain and mitigate DDoS assaults, making sure uninterrupted carrier and enhanced coverage for our customers.
Statistics supplied via the DevOps crew display that throughout the closing 30 days (April 22 – Would possibly 23, 2024), we’ve served a staggering 75.51 billion requests thru Cloudflare. Out of those, 3.3 billion had been mitigated via Cloudflare’s Internet Software Firewall (WAF), making sure that possible threats by no means succeed in our shoppers.
We additionally won signals for 200 DDoS assaults, all of that have been routinely mitigated via Cloudflare. One of the important assaults we confronted lately used to be again in March, with a top of 318,930 requests in line with 2d, which we treated seamlessly with Cloudflare.
Those numbers spotlight how powerful our safety features are, demonstrating the continual coverage we offer to our shoppers and showcasing the price of our Top class Cloudflare integration.
Traditionally, prior to our integration with Cloudflare, we needed to set up all assaults manually. If an assault wasn’t too intense, shall we SSH into load balancers (LBs) and analyze site visitors the usage of gear like tcpdump and Wireshark. In keeping with our findings, we might ban explicit IPs or create centered iptables laws and GCP firewall laws to mitigate the assault.
We additionally briefly resized LB circumstances to maintain the weight and tweaked quite a lot of kernel settings. Over the years, we computerized many of those processes, working scripts to set and unset iptables laws and kernel parameters as wanted. If an assault used to be too intense, we cloned LBs and multiplied circumstances to distribute the weight.
As assaults was extra common and complicated, we built-in Cloudflare into our webhosting infrastructure to make sure our shoppers’ websites had been secure and sound. We in an instant began noticing fewer assaults achieving our servers.
Kinsta’s present DDoS mitigation infrastructure
Lately, we now have probably the most absolute best webhosting infrastructures to fend off DDoS assaults, due to integrated gear, a devoted crew, and our integration with Cloudflare.
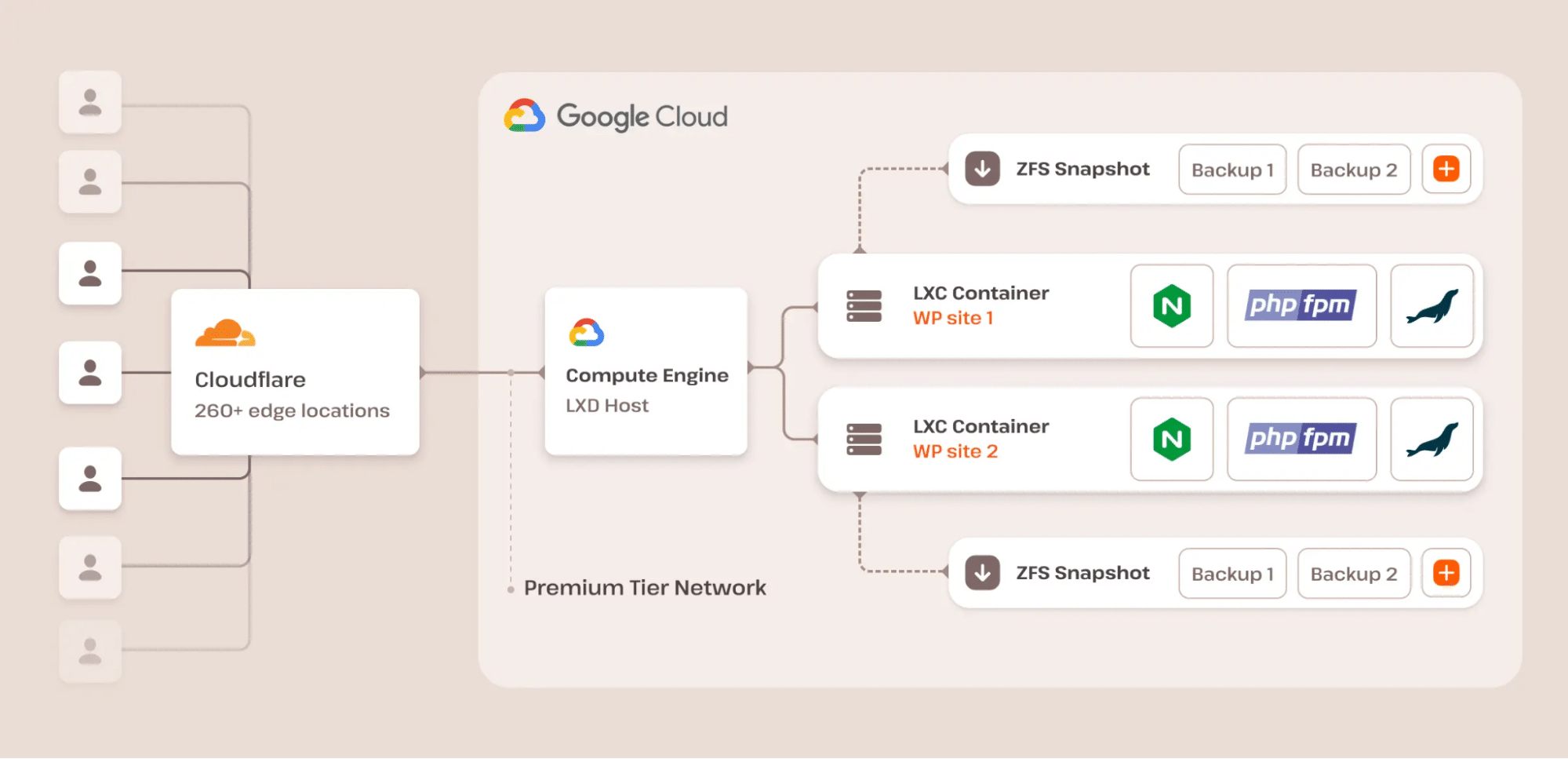
After integrating with Cloudflare, we successfully eradicated low-level sync flood assaults as a result of all of our internet site visitors is routed thru Cloudflare. This offers DDoS coverage (layers 3, 4, and seven) to dam undesirable TCP/UDP connections originating from explicit IP addresses or networks on the fringe of our community.
Moreover, we use the Google Cloud Platform (GCP) firewall to safeguard our community from possible assaults that immediately hit our infrastructure.
Kinsta supplies a completely controlled WAF with frequently up to date customized rulesets and configurations, making sure steady coverage towards the most recent threats.
Moreover, we make use of an automatic characteristic that continuously detects brute pressure assaults to your website’s /wp-login.php trail. We then block those actors from our infrastructure, additional strengthening our safety features.
How we mitigated an enormous DDoS assault for a monetary consumer
Not too long ago, a monetary corporate made up our minds to transport to Kinsta as their new webhosting supplier. Little did we all know, they had been in the midst of an enormous DDoS assault on their earlier host. After going reside at Kinsta, the customer’s web site used to be in an instant bombarded with tens of millions of requests from quite a lot of IP addresses, inflicting important disruption.
At the day of the website’s migration, the whole lot looked to be going easily prior to going reside. We helped them with a WordPress theme factor, they usually started pointing their DNS to Kinsta. Alternatively, in a while after, they spotted bizarre bandwidth statistics of their MyKinsta analytics and reached out to us, frightened in regards to the ordinary site visitors.
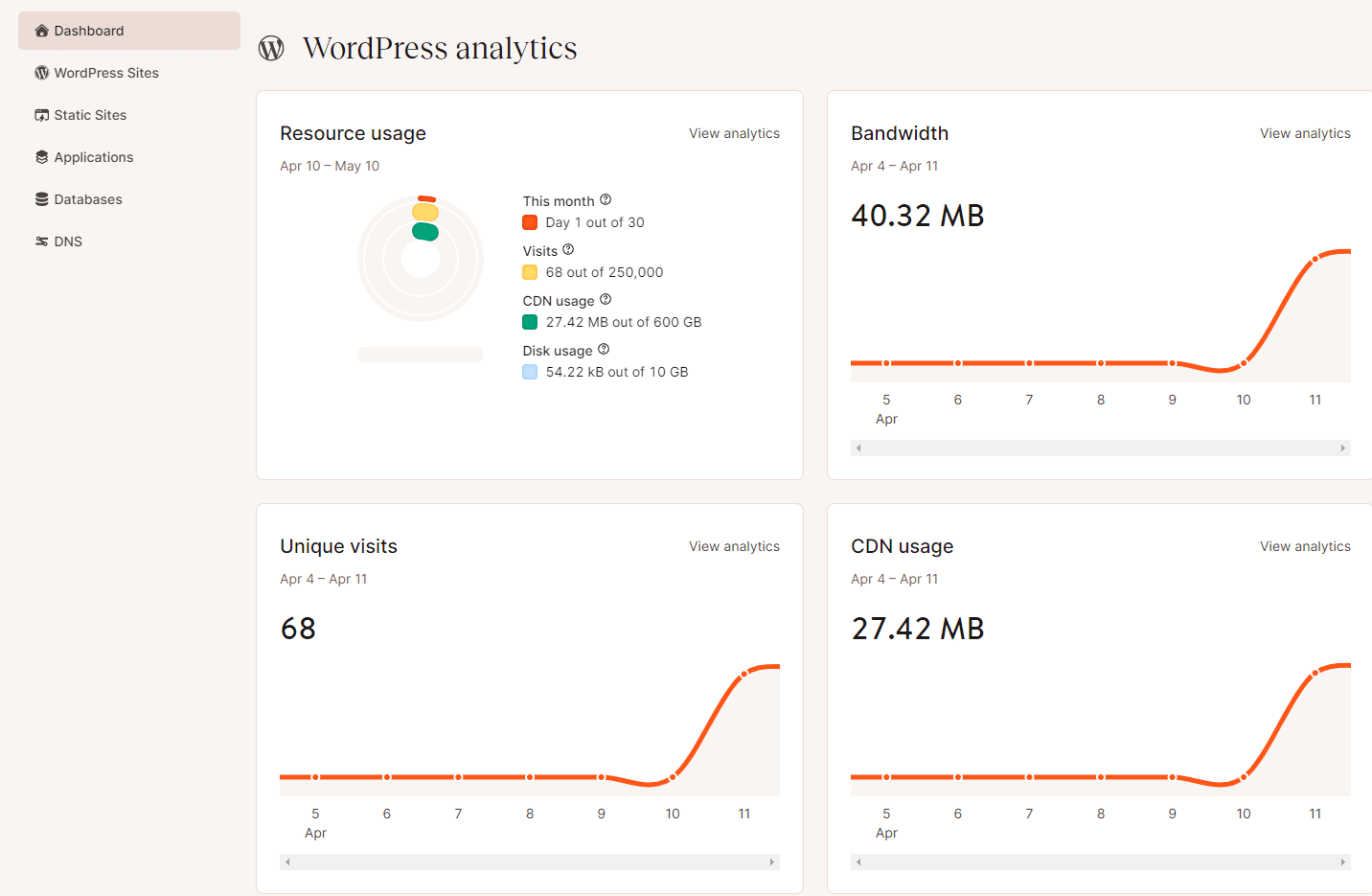
Our SysOps crew temporarily jumped into motion, confirming {that a} DDoS assault used to be certainly taking place. The customer shared that that they had skilled identical issues of their earlier host however hadn’t discovered it used to be because of a DDoS assault. They’d was hoping transferring to Kinsta would remedy their efficiency problems.
To handle the placement, our SysOps crew labored with Cloudflare to mitigate the assault. We applied a customized Cloudflare WAF rule to problem suspicious site visitors and supply additional coverage.
All through this era, the web site remained out there when examined via our beef up crew. Alternatively, the customer reported problems on cell, which we later traced again to a DNS propagation factor brought about via an previous AAAA report.
Through the tip of the day, the assault had subsided. Cloudflare’s controlled DDoS rulesets treated the majority of the malicious site visitors, routinely mitigating over 516 million requests. Our customized WAF rule supplied further safety, making sure the customer’s website remained operational.
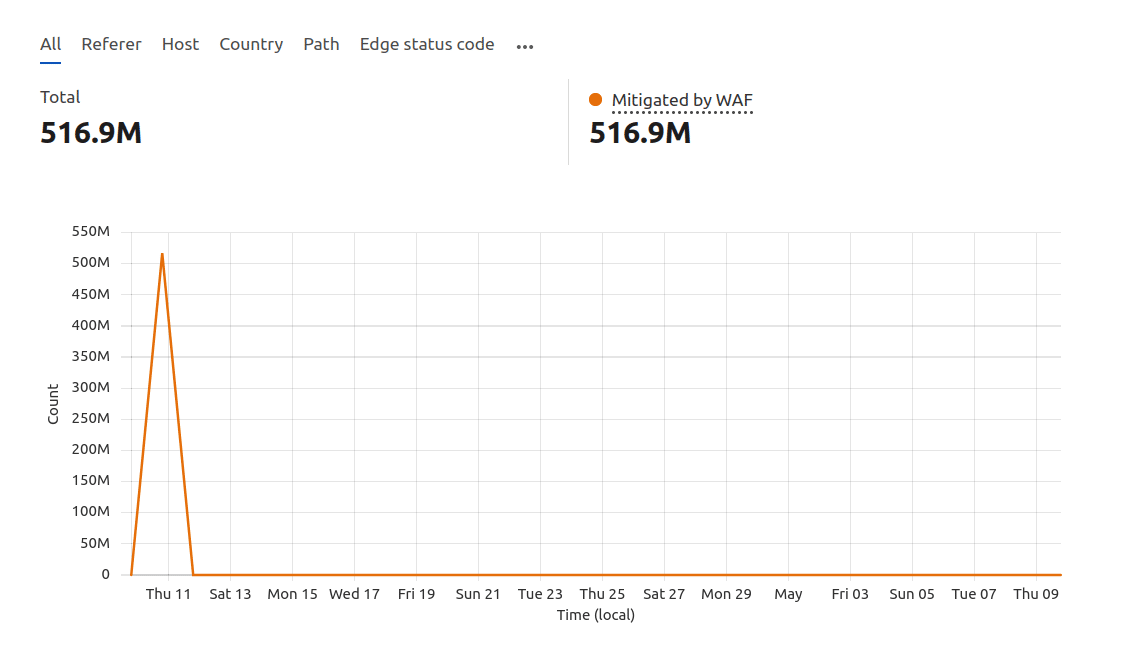
In simply 27 mins, we mitigated an assault with a mean request fee of 350,000 in line with 2d. This demonstrates how an excellent webhosting supplier can save you DDoS assaults thru powerful tracking, knowledgeable beef up, and complex safety features.
From monitoring bandwidth and analytics within the MyKinsta dashboard to enticing with beef up groups, having mavens customise WAF laws, and leveraging a forged infrastructure, a competent webhosting supplier like Kinsta can fend off maximum assaults and stay your website safe.
Abstract
This newsletter has explored the way you and a high quality internet webhosting corporate can paintings in combination to mitigate DDoS assaults, making sure your website stays safe and operational.
Past DDoS assaults, Kinsta’s infrastructure gives powerful coverage towards all kinds of cyber assault. Each website on our platform runs in an remoted device container, making sure 100% privateness and no shared device or {hardware} sources, even between your individual websites.
We leverage the Google Cloud Platform’s top rate tier, making sure your knowledge’s safe shipping over Google’s well-provisioned, low-latency, international community. With this, you have the benefit of a safety fashion advanced over 15 years, securing most sensible merchandise like Gmail and Google Seek.
How do you save you DDoS assaults? We’d love to listen to from you. Percentage with us within the feedback segment.
The submit The best way to save you DDoS assaults: pointers from safety mavens seemed first on Kinsta®.
WP Hosting