When you run a site, in particular an e-commerce site, it’s your duty to make sure that transactions happen securely and that the knowledge of your customers and purchasers aren’t compromised. Your WordPress site’s database shops non-public knowledge, bodily and digital addresses, bank card main points, transaction logs, and a lot more, and you’re liable for the safety and integrity of all this information.
Safety isn’t synonymous with inviolability. There’s no such factor as absolute safety at the Web, particularly in relation to open-source instrument. Then again, there are lots of safety features that you’ll be able to take to attenuate dangers of breaches, knowledge robbery, and different roughly severe harm on your site or infrastructure. Understand that, in line with the GDPR, the Knowledge Controller is liable for making sure that knowledge processing complies with the GDPR and knowledge coverage rules.
The knowledge controller determines the needs for which and the method during which non-public knowledge is processed. So, in case your corporate/group comes to a decision ‘why’ and ‘how’ the non-public knowledge will have to be processed, it’s the knowledge controller. Staff processing non-public knowledge inside your company do with the intention to satisfy your duties as knowledge controller.
A safety flaw in a site can put an organization’s existence in peril. Who would wish to entrust their bank card main points to an insecure site? And what harm would outcome on your logo’s recognition in case your consumers’ knowledge had been stolen and used for illicit functions?
Briefly, at the identical point as efficiency, safety is a mission-critical element for a a hit e-commerce site and industry. With this in thoughts, on this article, we’ve amassed an inventory of safety features and ultimate practices that each e-commerce proprietor will have to undertake with the intention to stay aggressive in native and world markets and keep away from severe felony legal responsibility and harm to their on-line industry.
13 main safety dangers for e-commerce web sites
In step with the 2020 Trustwave International Safety File, conventional brick-and-mortar shops and e-commerce environments are probably the most uncovered industries to cybersecurity dangers, with about 24% of the full safety incidents in 2019.
This leads us to believe the significance of safety for e-commerce web sites, to find out the threats that loom over an internet industry, and the measures that e-commerce web site homeowners will have to take to safe their consumers’ transactions and knowledge.
To higher perceive the movements and ultimate practices an internet industry proprietor will have to undertake to safe their web sites and e-stores, we first want to perceive probably the most unhealthy threats to e-commerce web sites.
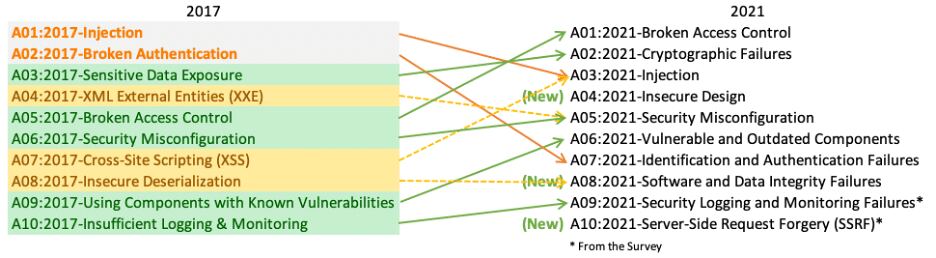
In line with the OWASP Best 10 Internet Software Safety Dangers, we compiled the next non-exhaustive listing of probably the most in style threats that e-commerce web sites have to stand as of late.
1. Malware and Ransomware
There are lots of sorts of malware and other ranges of safety threats. Hackers use them to hack gadgets and scouse borrow knowledge. Malware could cause critical financial harm and may also ruin a whole corporate.
Even if the effects would possibly not all the time be so dire, your consumers would possibly obtain the mistake message “The web site forward incorporates malware” or “Misleading web site forward” or the like, and this will have an effect on your web site’s visibility in SERPs and harm your logo symbol significantly.
Ransomware is a sub-species of malware. Briefly, ransomware hijacks a tool or site, denying get entry to to its information till the sufferer can pay a ransom for the decryption key.
Because of the excessive chance {that a} malware assault will have on an e-commerce site, scanning your e-commerce web site continuously for malware infections is essential for your small business.
Test Out Our Video Information to Malware
2. Phishing
Phishing is one of those social engineering assault utilized by cybercriminals to unfold malware — typically via emails.
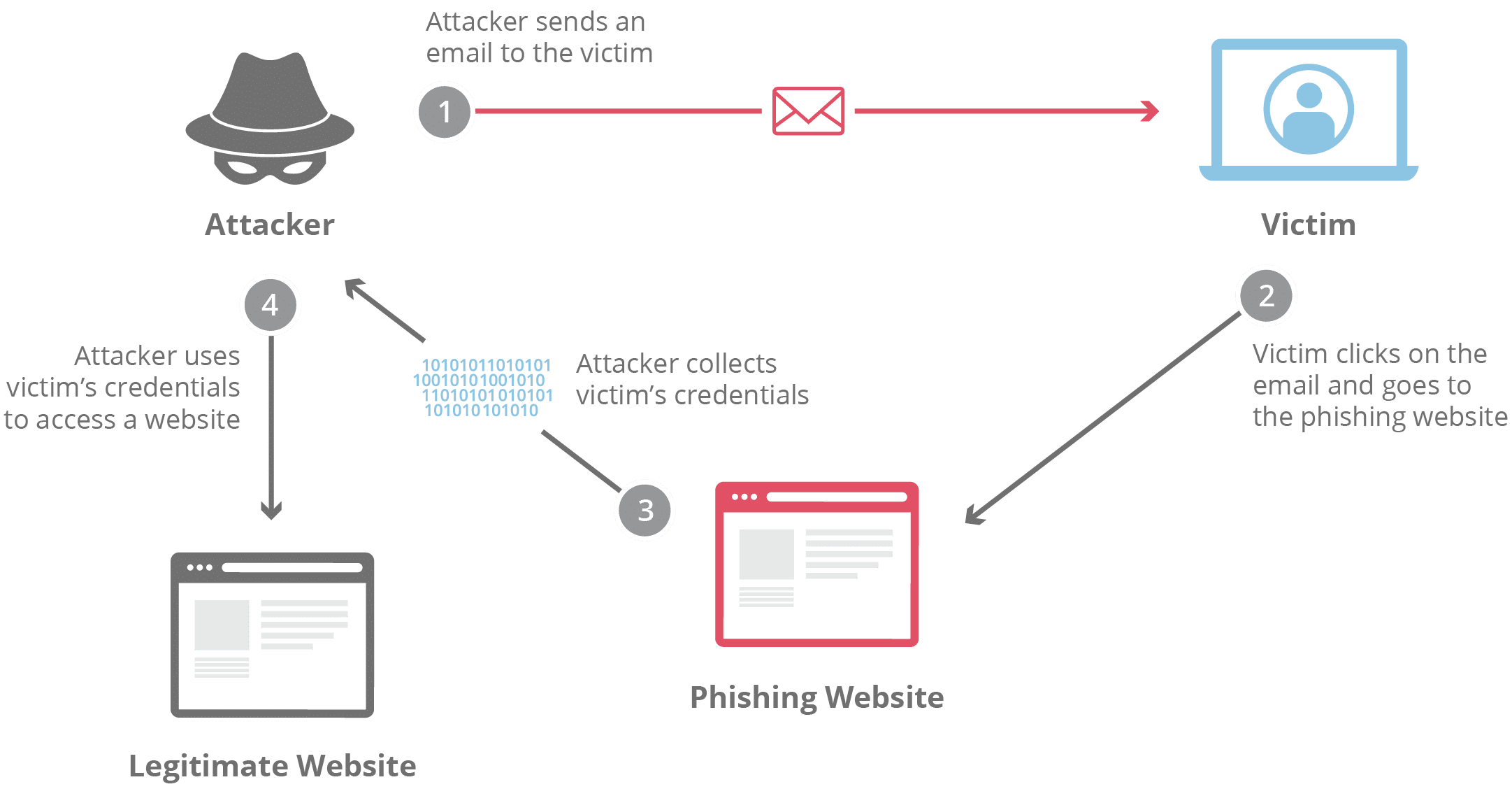
It refers to an try to scouse borrow delicate knowledge corresponding to usernames, passwords, bank card or checking account main points, or different essential knowledge to make use of or promote with malicious intent. In most cases, this sort of assault is carried via unsolicited mail and different varieties of fraud emails or quick messages.
3. DDoS assaults
DDoS is the fast time period for dispensed denial of carrier. That is one of those assault that floods a site with a lot of requests to crush the server with over the top Web site visitors and take the site down. The outcome is that your web site is going offline, and the bandwidth prices building up dramatically. This may additionally reason the suspension of your web hosting account.
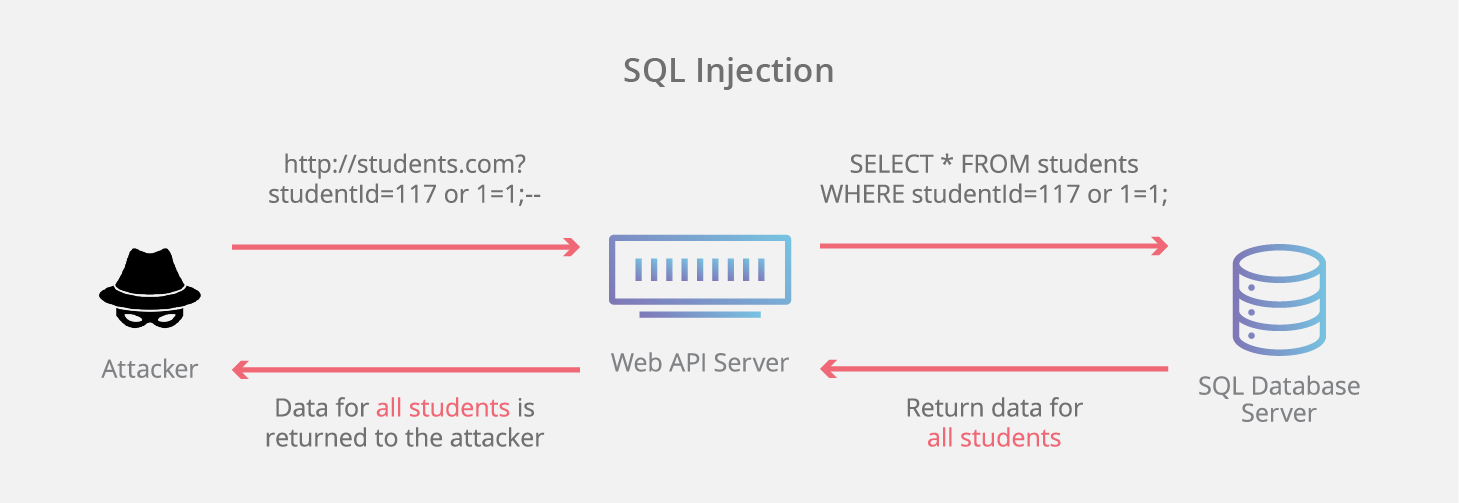
4. SQL injection
SQL injection is one of those assault carried out by means of a malicious actor who tries to inject SQL statements right into a internet utility. If the assault is a hit, they’ll be capable to get entry to your web site database and skim, alter, or take away knowledge.
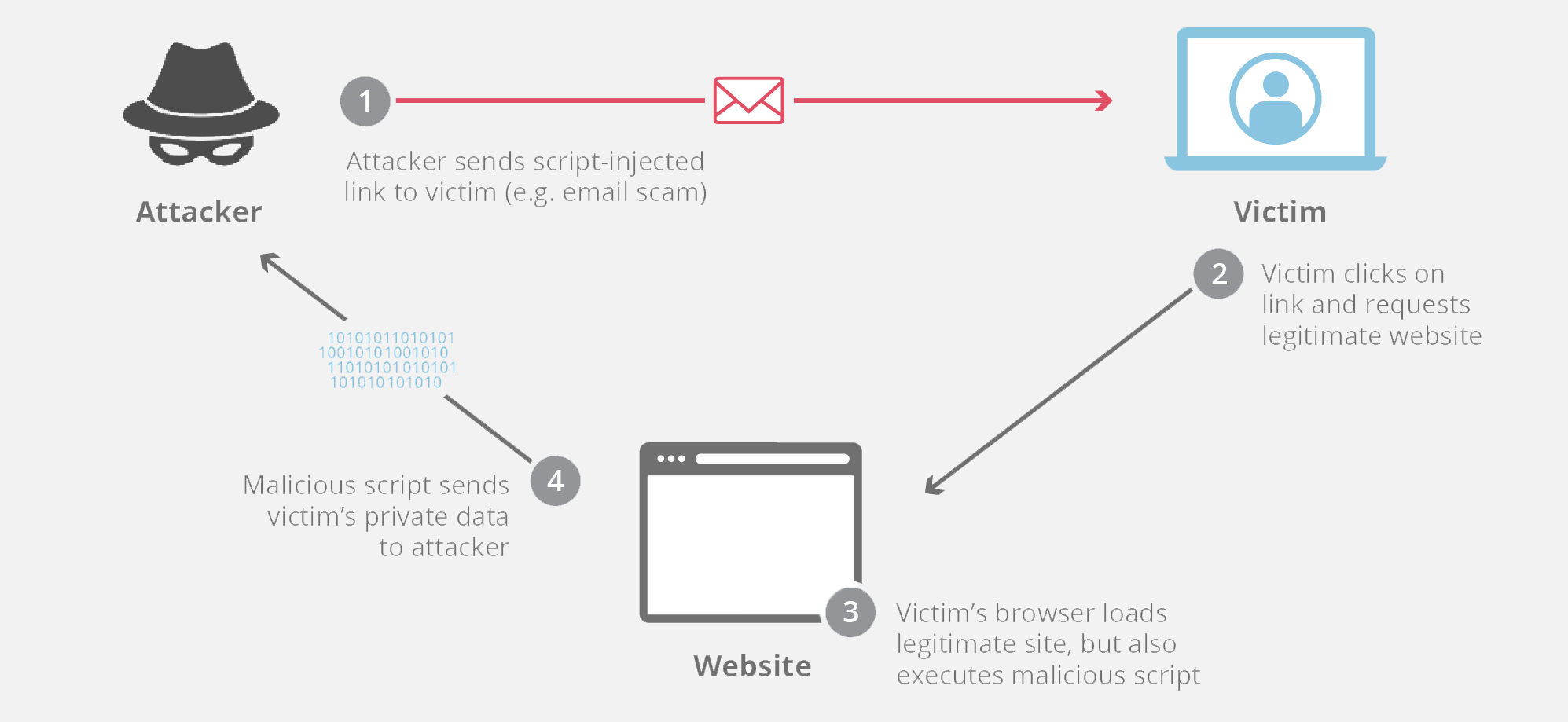
5. Move-site scripting
Move-Website online Scripting (XSS) is one of those assault the place any person attaches malicious code onto a site to be completed on web page load. The injection occurs on a consumer’s browser and generally targets to scouse borrow delicate knowledge.
6. Guy-in-the-middle assaults
A person-in-the-middle (MitM) or on-path assault is a cyberattack the place any person puts in the course of verbal exchange between two gadgets (corresponding to a internet browser and a internet server) aiming to clutch knowledge and/or impersonate one of the crucial two brokers with malicious intent.
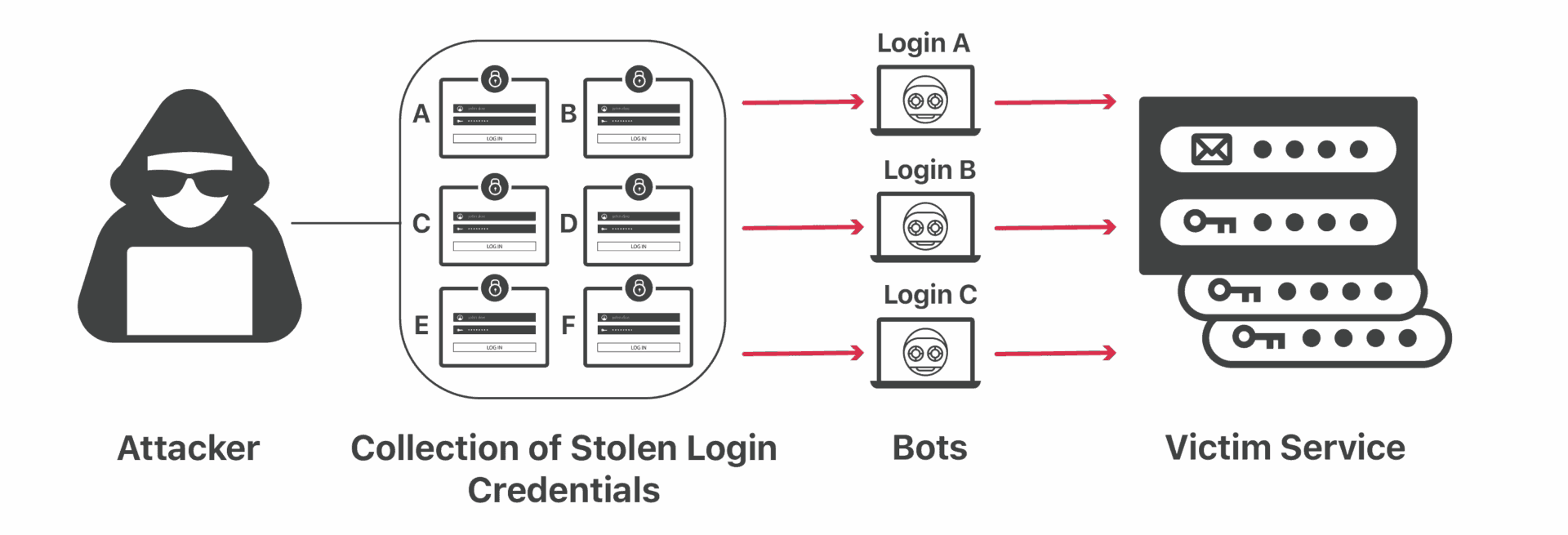
7. Credential stuffing
Credential Stuffing is a cyberattack the place the attacker makes use of credentials acquired from a knowledge breach on a carrier or site to log into a distinct carrier or site. This type of assault is a commonplace chance for pros operating from house and faraway corporations.
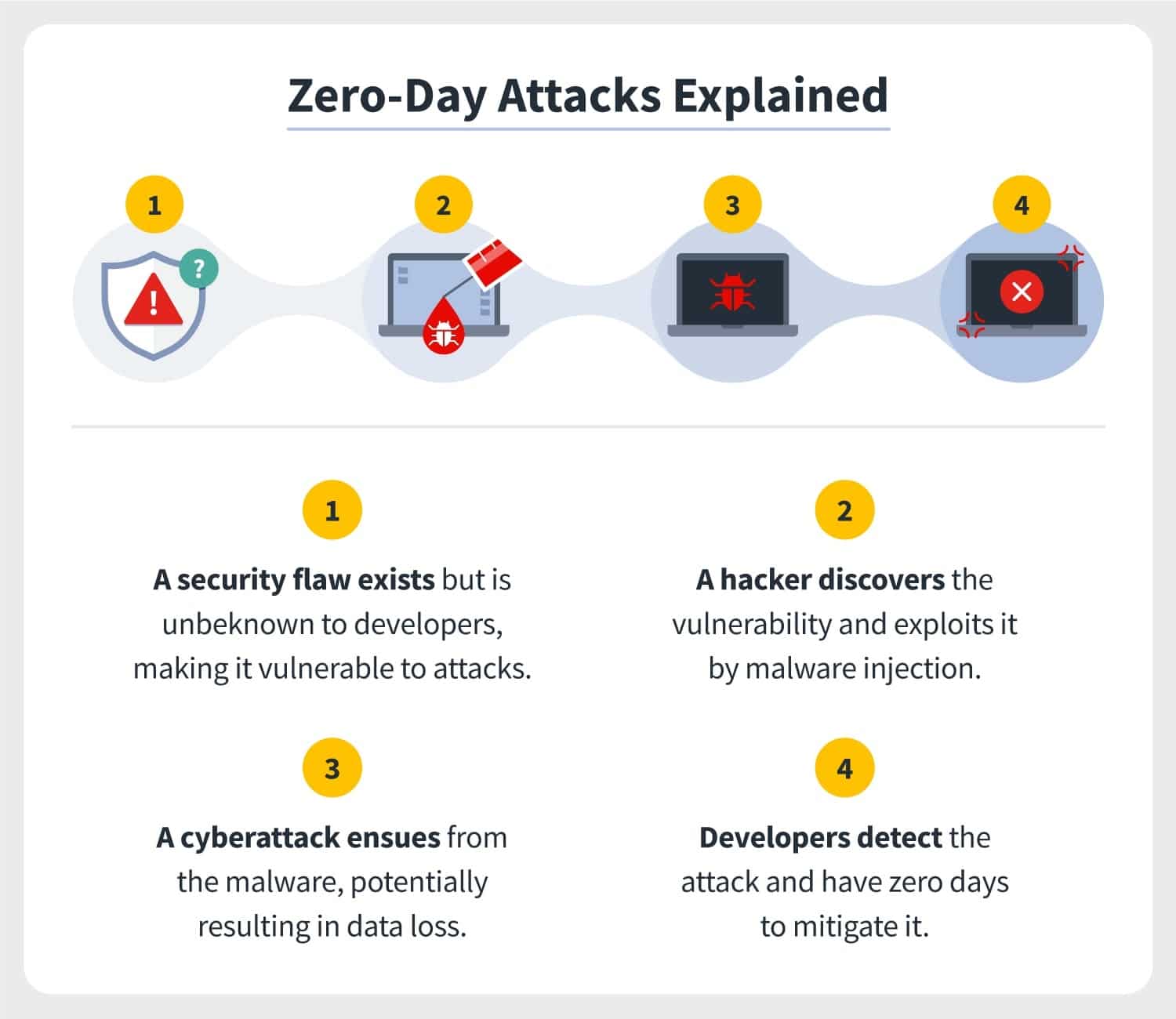
8. 0-day exploits
A zero-day exploit is an unresolved or prior to now unknown safety vulnerability that has no repair in position. 0-day method that you’ve 0 days to mend the problem earlier than it reasons severe harm to your small business.
9. E-skimming
E-skimming or virtual skimming is the insertion of malicious instrument right into a store’s site aiming to scouse borrow cost knowledge all through checkout. That is sometimes called Magecart assault.
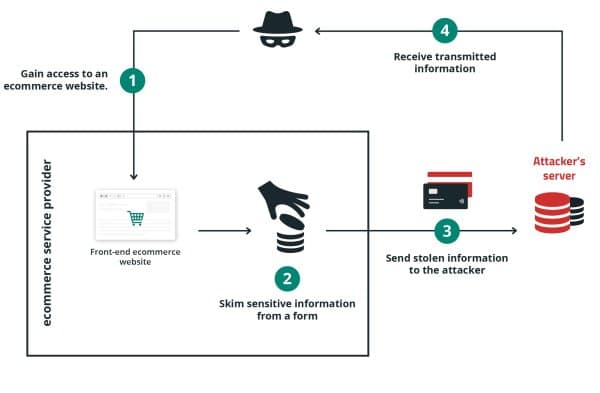
10. Brute pressure assaults
A brute pressure assault is a trial-and-error means used to decode delicate knowledge corresponding to login credentials, API keys, and SSH credentials. As soon as a password has been compromised, it may be used to get entry to different products and services if you happen to use the similar credentials on a couple of web sites. (See credential stuffing.)
The use of robust passwords, enabling multi-factor authentication programs, and the usage of a strong password supervisor are all ultimate practices fighting this type of cyberattacks.
11. Backdoors
A backdoor supplies a solution to bypass an authentication or encryption method to routinely log right into a site, instrument, or carrier. As soon as a site or carrier has been breached, a malicious actor can create their very own backdoors to get entry to your site, scouse borrow knowledge, and doubtlessly ruin all your web site.
12. Social Engineering assaults
Social engineering assaults are specifically unhealthy as a result of they exploit traits of human nature: accept as true with in others, lack of know-how, discomfort in contravening an order, utilitarianism, and so forth. The foundation of social engineering is the mental manipulation of folks for the aim of disclosure of confidential knowledge corresponding to passwords, checking account main points, and fiscal knowledge.
The most typical channels used to accomplish this type of assault are emails, chat, telephone calls, social networks, web sites, and others. The attacker can then use that knowledge to behavior different forms of exploits corresponding to Move-Website online Request Forgery.
Test Out Our Video Information To Perceive All About CSRF Assaults
13. Provide Chain Assaults
In most cases, with a provide chain assault, a cyber attacker infiltrates malicious code right into a dealer’s instrument to be dispensed with an replace.
Even if they don’t seem to be as in style as different backdoor assaults, provide chain assaults had been not too long ago detected on a number of WordPress plugins.
9 ultimate practices to safe your e-commerce site
Securing a site is usually a tricky job if you happen to don’t have the best equipment and talents, however it doesn’t must be a role for devoted engineers. The primary factor is to pay attention to the spaces of vulnerability and train your self and your workforce on the most productive practices for securing your e-commerce site from the most typical threats.
Your job is twofold: at the one hand, you’re liable for securing WordPress and WooCommerce, resolve who can get entry to the platform, the plugins to be put in, the cost gateway, the authentication method, and the entirety associated with WordPress, plugin, and theme repairs. Alternatively, you want a safe and state of the art infrastructure. That is the place the standard of your internet web hosting carrier is available in.
Certain, your internet web hosting supplier can not prevent from any more or less threats. There are safety movements that you just and handiest you, as a web site proprietor, can take. However a safe web hosting carrier that takes your web site’s safety significantly can lend a hand so much. Listed below are the principle security-related options to search for in a contemporary internet web hosting carrier.
1. Make a selection a state of the art web hosting infrastructure
The selection of the web hosting infrastructure is essential on your site safety, your logo recognition, and, ultimately, the good fortune of your small business. You might have different types of carrier to choose between, they usually range significantly on the subject of infrastructure and products and services equipped:
- Shared web hosting
- Devoted web hosting
- VPS web hosting
- Cloud web hosting
- Controlled WordPress web hosting
For an e-commerce site, depending on a safe infrastructure is the most important. When you care about your small business, a shared web hosting isn’t an choice for you because it would possibly not ensure the minimal safety requirements for a a hit e-commerce site.
Devoted web hosting may also be extremely custom designed and optimized for safety however would possibly require SysAdmin abilities that can be arduous to search out for a small or medium-sized industry.
In case you want keep an eye on over your web hosting however you don’t have nice technical wisdom and/or sources, chances are you’ll go for a Digital Non-public Server (VPS) web hosting, which puts someplace within the center between shared web hosting and devoted web hosting. However a VPS could have a couple of cons: It may well be not able to maintain excessive site visitors ranges or spikes and function remains to be suffering from different web sites at the server.
A cloud web hosting carrier is also a just right choice for you because it generally has a number of safety features in position to safe your web sites. Then again, it may be arduous to configure and organize if you happen to don’t have the essential abilities.
A controlled WordPress and WooCommerce web hosting provides you with peace of thoughts since you aren’t liable for server configuration and optimization, and you’ve got specialised fortify carrier and simplified web site set up and upkeep.
A cloud-based controlled WordPress web hosting carrier merges some great benefits of each worlds, combining the high-speed and safe infrastructure of cloud products and services with the convenience of use of controlled WordPress web hosting products and services.
Kinsta web hosting infrastructure and technical stack
At Kinsta, we consider we’ve created the quickest and maximum safe controlled WordPress web hosting answer to be had as of late on most sensible of the Google Cloud Platform.
We offer C3D and C2 compute-optimized VMs on all plans, from Starter to Endeavor and past, within the areas the place they’re to be had. We additionally benefit from Google safe infrastructure, which incorporates an enterprise-level firewall to clear out malicious site visitors earlier than it hits your site.
As well as, we’ve constructed a quick and safe technical stack in keeping with Nginx, MariaDB, PHP 8.3, LXD bins, and our integration of Cloudflare Endeavor, which supplies further safety, together with a firewall, DDoS coverage, and a lot more. This stack is to be had for all our purchasers, irrespective of their plans.
We use Linux bins (LXC) and LXD to orchestrate them on most sensible of the Google Cloud Platform (GCP), making sure whole isolation for each and every person WordPress web site. On Kinsta, your site doesn’t proportion sources with some other site, together with different web sites to your account.
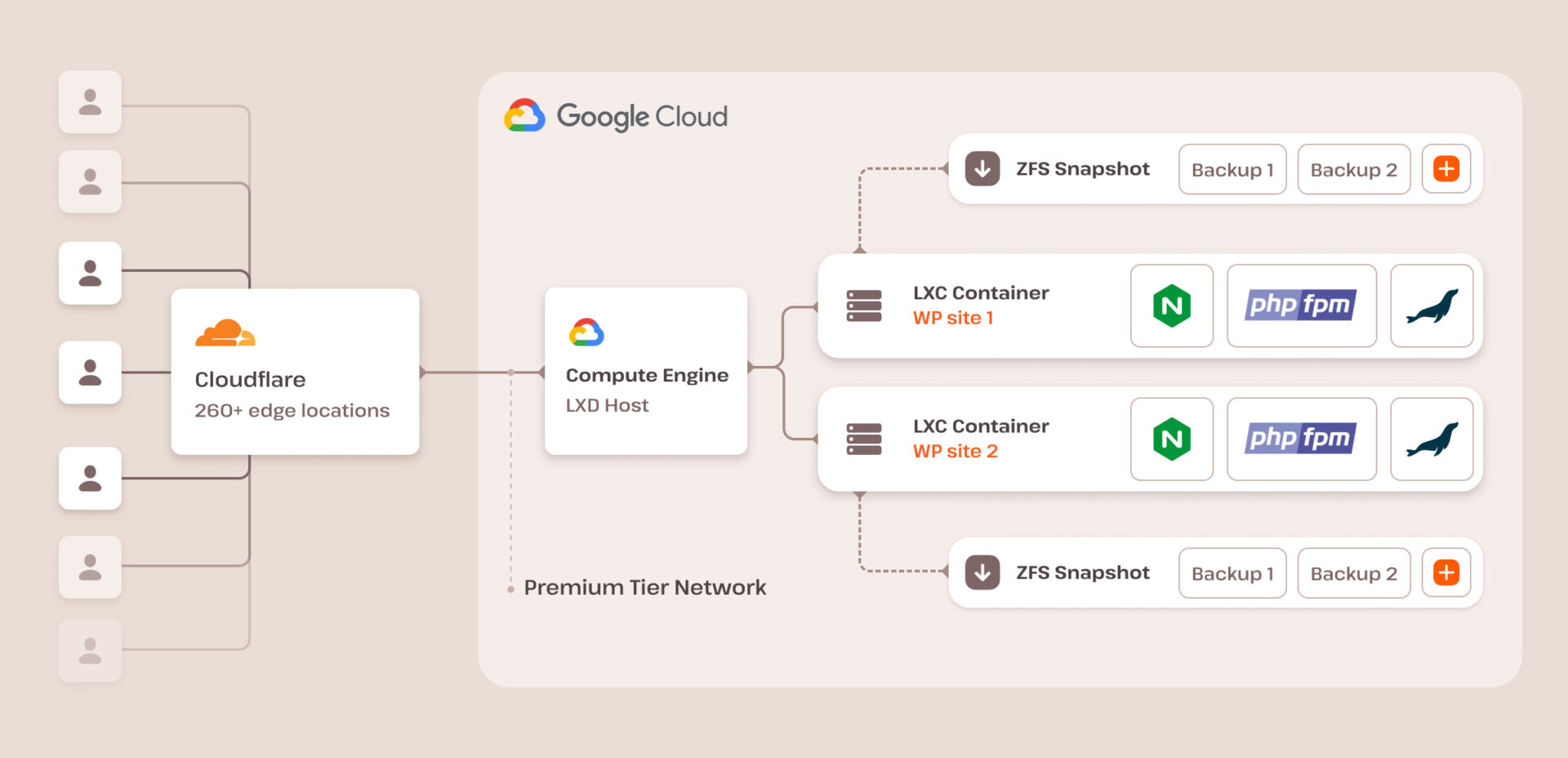
Take a look at this submit to be informed extra about our state of the art remoted container era.
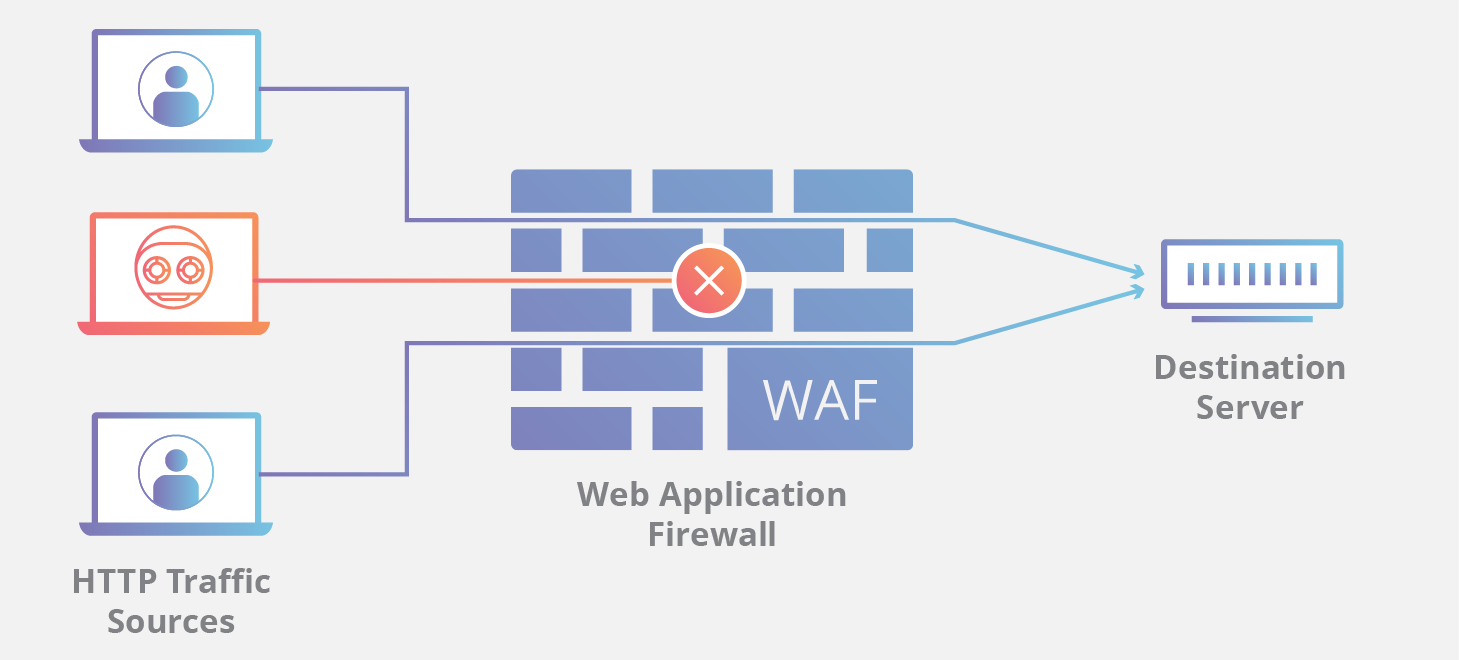
2. Use a internet utility firewall
A internet utility firewall (WAF) is a defend that filters out malicious connections from attaining your site and assists in keeping your WordPress site safe.
Direct connection between two computer systems at the Web, corresponding to your laptop and a internet server, isn’t safe if you happen to don’t put a firewall within the center. A malicious actor would possibly infect your site with some more or less malware or release a DDoS assault.
That is the place a internet utility firewall is available in. It scans each unmarried connection request on your site and blocks doubtlessly malicious get entry to makes an attempt.
A WAF is the most important to your site, whether or not you’re a first-time blogger or a a hit entrepreneur. With e-commerce web sites, the usage of a internet utility firewall is essential as a result of an unprotected site is a straightforward catch for hackers and different malicious actors.
With no internet utility firewall, a hacker can simply take keep an eye on of your web site, alternate login credentials, scouse borrow or ruin knowledge, smash it, and carry out any kind of illicit actions. Probably, it might wipe out your web site completely. As well as, your site could be extra liable to DDoS and brute pressure assaults.
To give protection to your site with a WAF, you don’t want to set up and configure further instrument to your server. A number of cloud-based choices, corresponding to Cloudflare, Sucuri, and WordFence, may also be arrange to your server in couple of minutes.
All web sites hosted by means of Kinsta are secure by means of Cloudflare
Along with the IP-based coverage that we offer with the Google Cloud Platform firewall, all web sites hosted by means of Kinsta take pleasure in our Cloudflare integration, which incorporates an enterprise-level internet utility firewall with customized rulesets and loose DDoS coverage.
Because of our Cloudflare integration, you don’t want to arrange a WAF manually as a result of your web site is routinely secured at the back of Cloudflare’s firewall, irrespective of the plan you subscribe to.
3. Set up an SSL certificates
SSL is a protocol used to encrypt and authenticate the knowledge despatched between a shopper utility and a internet server. When you run an e-commerce site, an SSL certificates is essential to your site and your small business as it guarantees knowledge encryption, site authentication, knowledge integrity, and consumer accept as true with.
As well as, an SSL certificates improves seek engine rating as a result of search engines like google and yahoo favor SSL-encrypted websites. If you wish to have a possibility to be indexed on Google’s first web page, you want a legitimate SSL certificates with HTTPS encryption.
SSL certificate on Kinsta
In case your site is hosted by means of Kinsta, you don’t want to take care of the entire technical intricacies that an SSL generally calls for. Our purchasers can benefit from our Cloudflare integration, which incorporates computerized SLL certificate for all WordPress web sites. This comprises wildcard SSL certificate, which means that that your SSL additionally covers any subdomains in relation to your major area. And if you have already got one, you’ll be able to additionally set up your customized SSL certificates.
Cloudflare SSL certificate come without charge for all our purchasers, irrespective of their plan.
For a more in-depth view of Kinsta WordPress SSL certificate, take a look at our on-line medical doctors.
Test Out Our Video Information to Opting for the Proper SSL Certificates for Your Website online
4. Use safe SFTP and SSH connections
To accomplish a handbook backup of your WordPress site or manually add a plugin or theme, you want to get entry to the web site’s filesystem by means of an FTP consumer. An FTP consumer generally helps each FTP and SFTP connections, however you will have to handiest depend on SFTP, that makes use of a safe channel to switch information over SSH. This makes a large distinction with usual FTP connections.
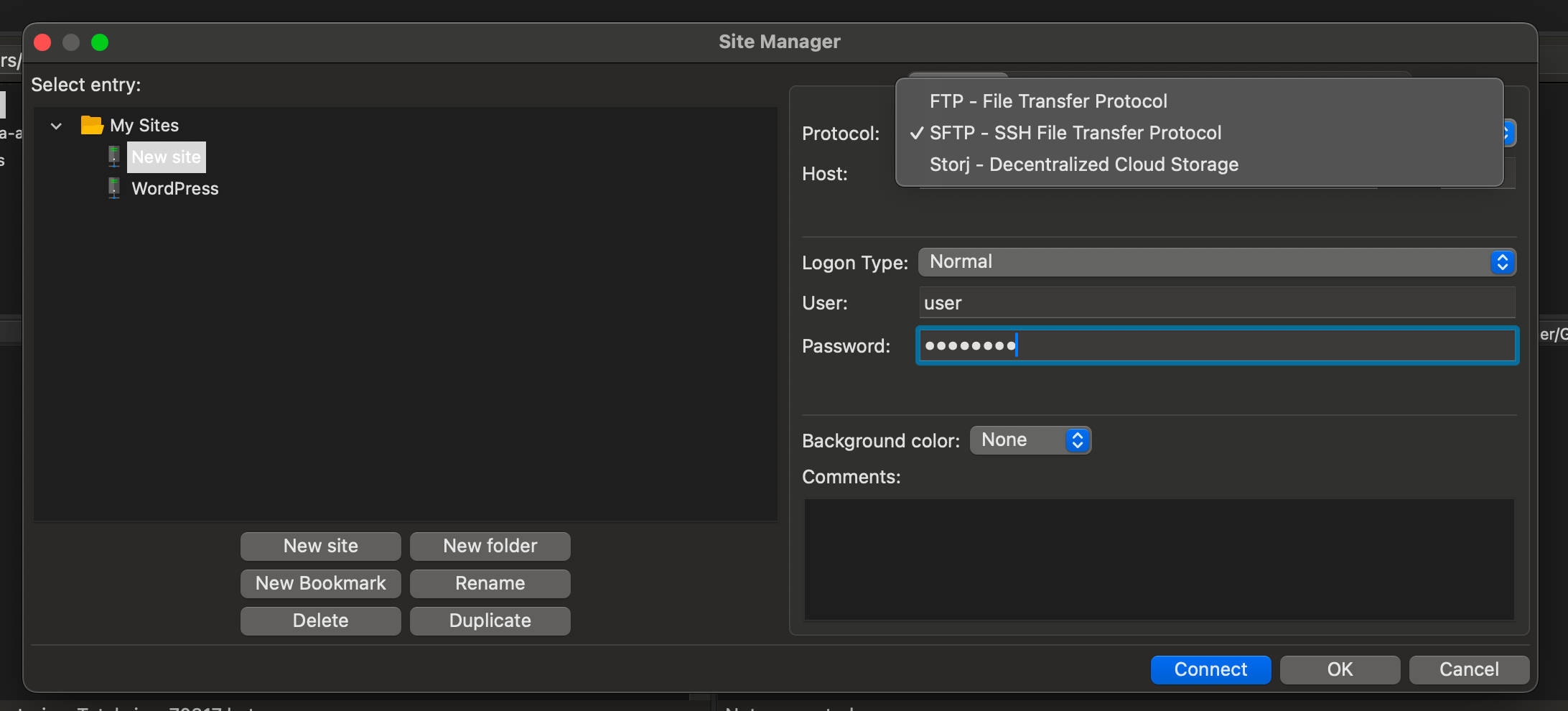
Kinsta handiest helps SFTP/SSH connections
As a result of SFTP is a extra safe means, Kinsta handiest helps SFTP connections.
SFTP/SSH main points are to be had for your MyKinsta dashboard beneath WordPress Websites > Sitename > Setting > Information.
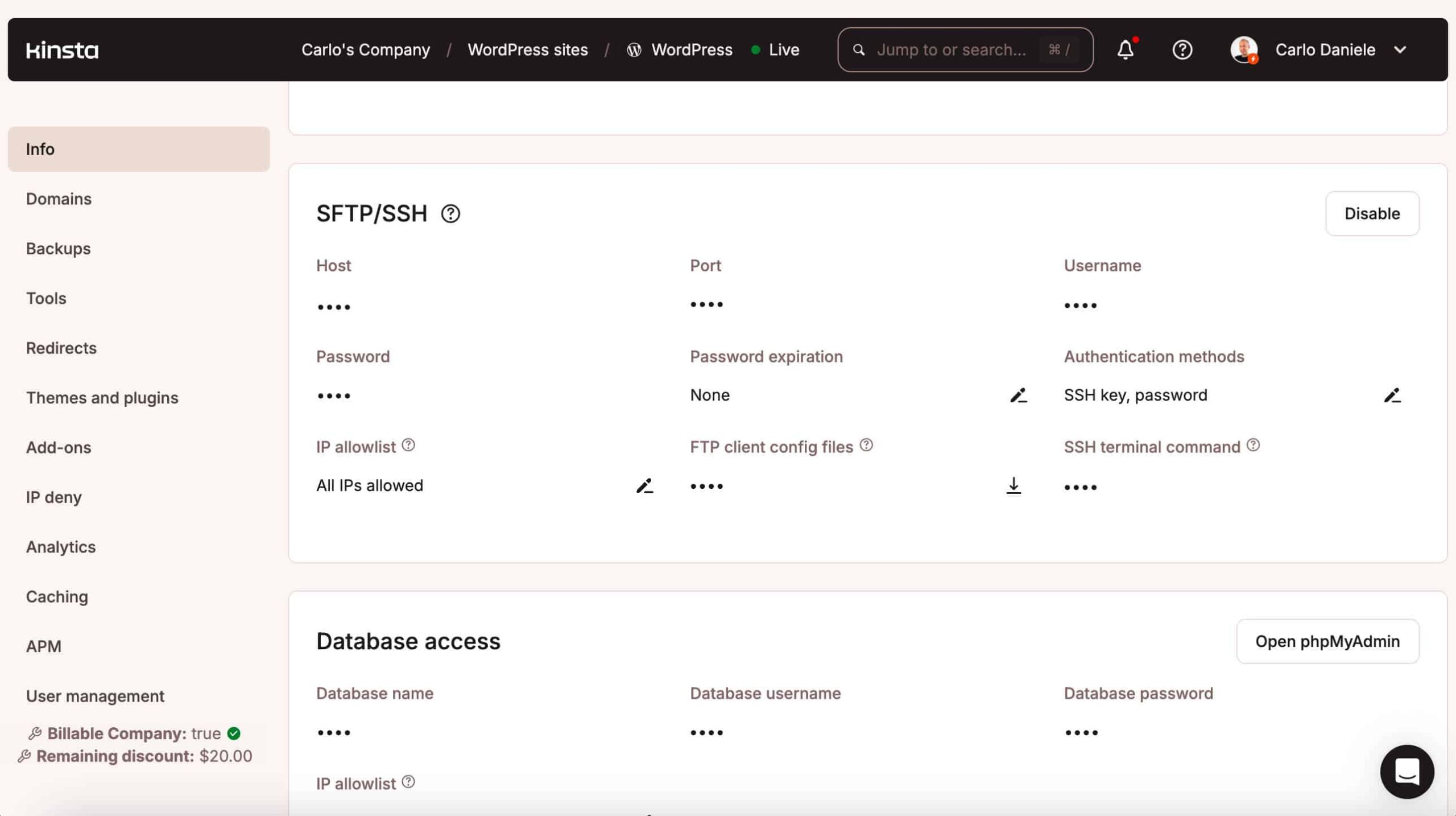
You will have to by no means use similar login credentials throughout a couple of products and services and site environments. Because of this, on Kinsta, each and every unmarried site atmosphere – staging or manufacturing – has distinctive database and SFTP/SSH get entry to credentials.
5. Use supported variations of PHP
Every PHP model is generally supported for 2 years. Best supported variations obtain efficiency and safety updates, so the usage of unsupported PHP variations reduces efficiency and will increase the chance of safety vulnerabilities.
As of August 2024, the formally supported variations of PHP are PHP 8.1, 8.2, and eight.3.
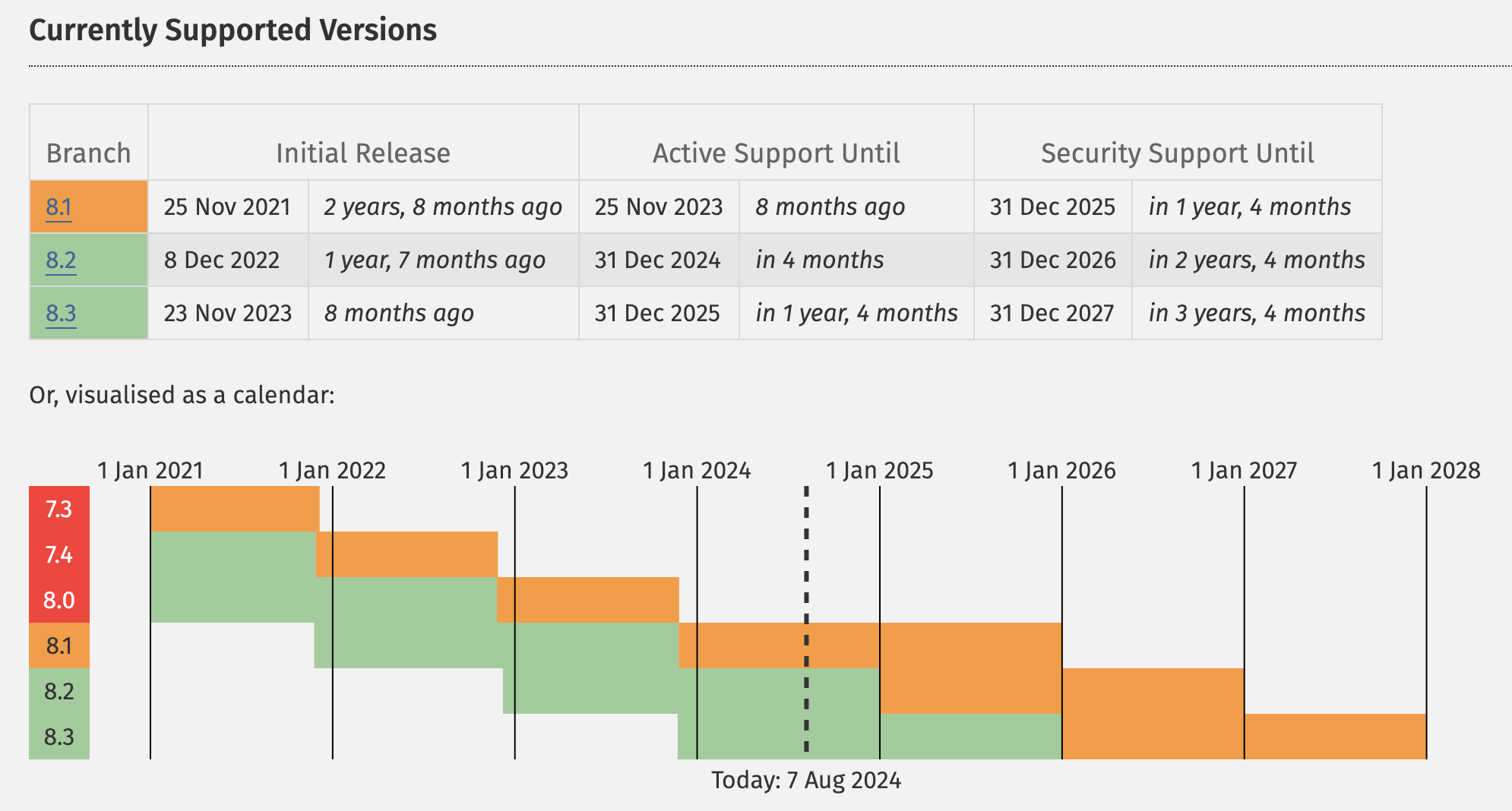
On the time of this writing, all PHP variations prior to eight.1 don’t obtain safety updates. Which means in case you are the usage of PHP 8.0 or previous, your web site is uncovered to safety flaws that is probably not mounted.
WordPress core is constructed with PHP. Plugins also are in keeping with PHP, and WooCommerce isn’t any exception. In case your e-commerce is in keeping with WordPress, the usage of a supported PHP model is essential to the good fortune of your on-line retailer.
Along with progressed safety, the latest variations of PHP be offering higher efficiency. It’s worthwhile to achieve a spice up in web site pace by means of merely upgrading to the newest PHP model.
Kinsta handiest permits supported PHP variations
This will require further building effort if you happen to use customized plugins that aren’t suitable with supported PHP variations. Then again, our major duty is to make sure most safety to your web sites and our complete infrastructure. Because of this, Kinsta does no longer mean you can use unsupported PHP variations.
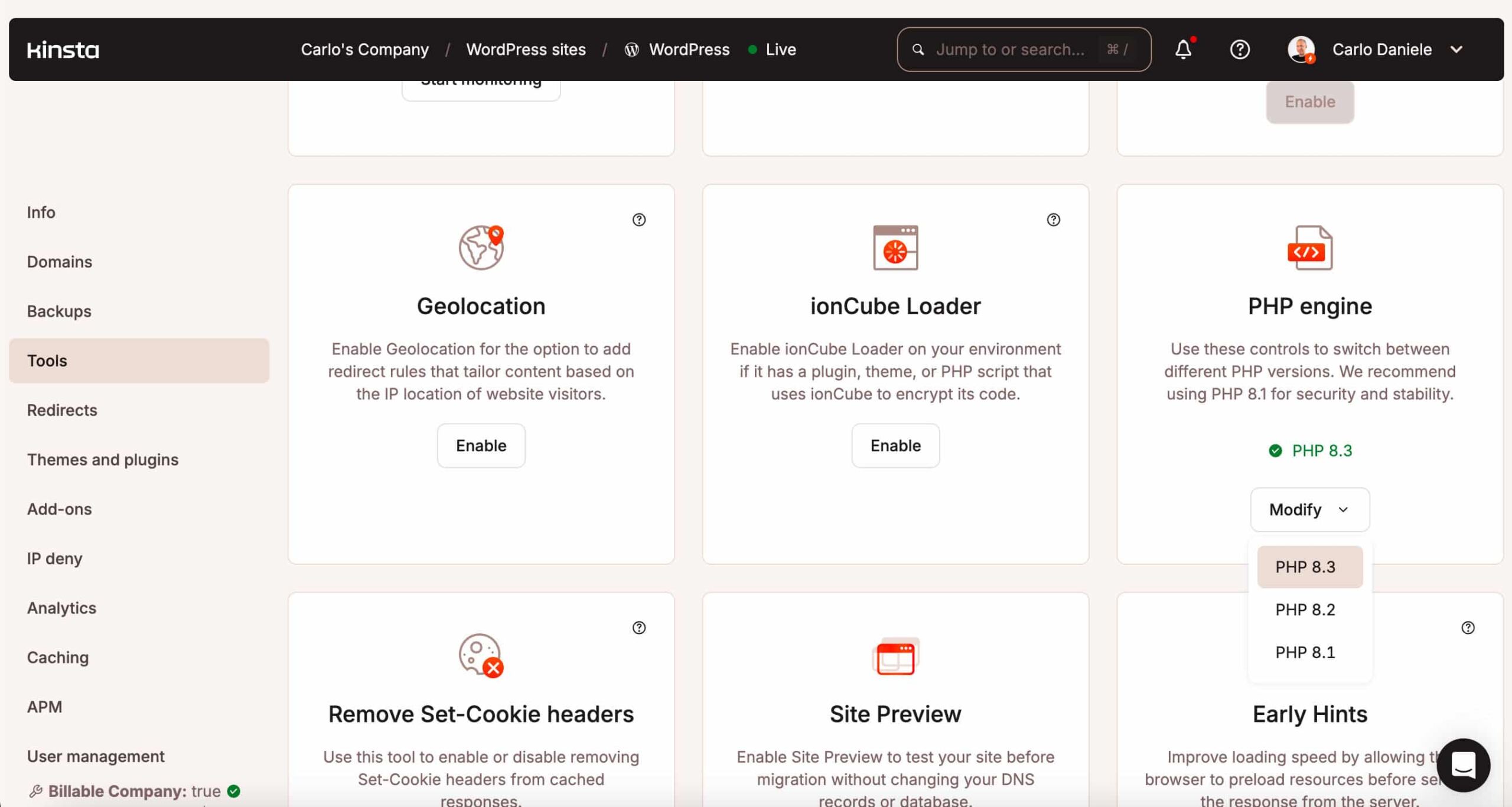
Kinsta purchasers can alternate the PHP model in their WordPress site in MyKinsta. Navigate on your web site config segment and choose Gear from the left menu. Scroll down the web page and to find PHP engine. Click on at the Regulate button and choose the PHP model to your site.
6. Permit two-factor authentication
The use of robust passwords to safe your site and web hosting account will not be sufficient to safe your e-commerce site. The use of a multi-factor authentication method is strongly really useful.
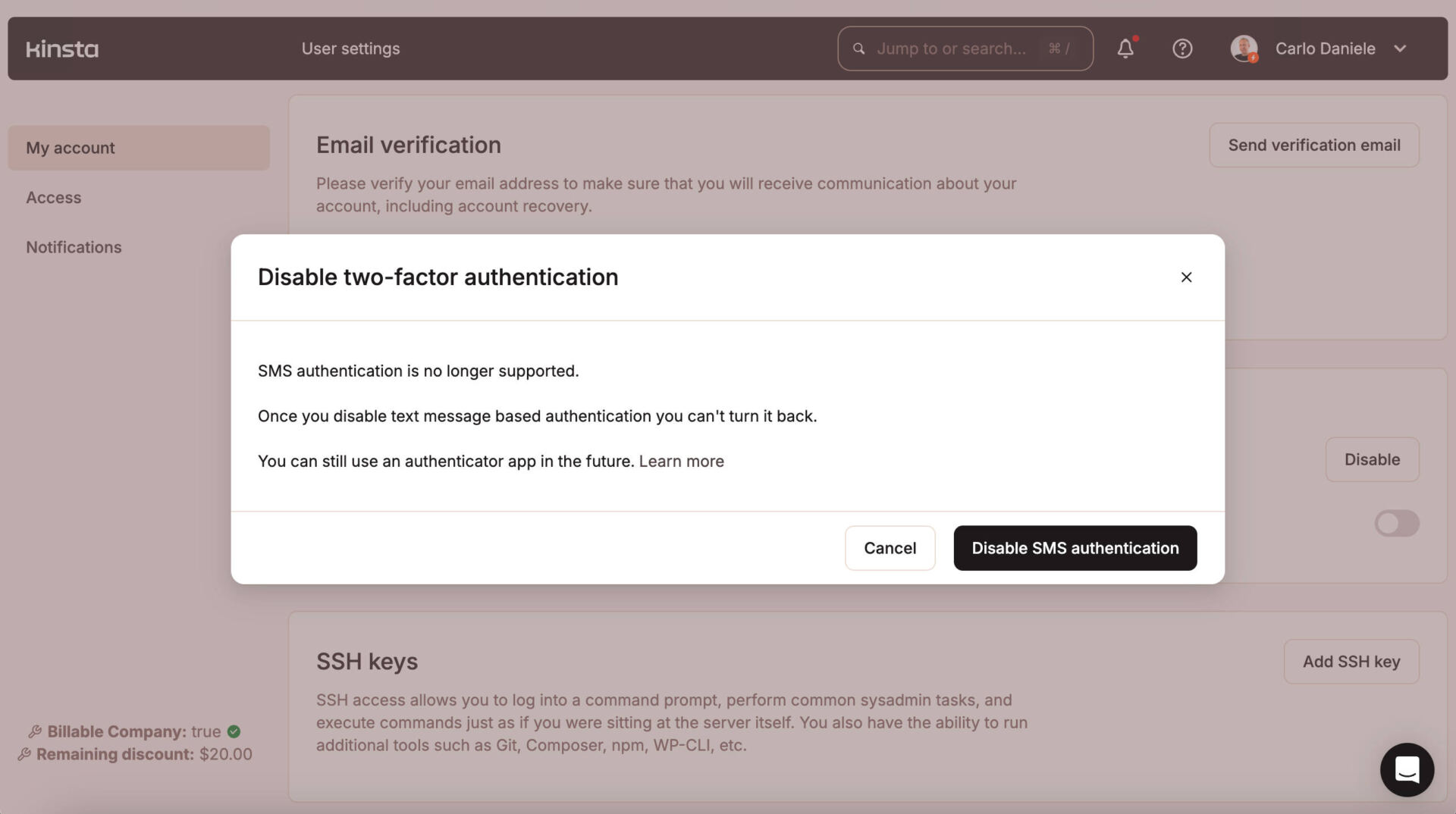
Multi-factor authentication is an authentication method the place the consumer gaining access to the carrier is needed to provide two or extra proofs in their identification. This may also be executed in several tactics: Biometrics corresponding to fingerprints, an authenticator app, an electronic mail, an SMS, a {hardware} token, and extra.
With regards to your e-commerce site, you will have to implement authentication safety by means of enabling two-factor authentication (2FA) on each your web hosting carrier and your WordPress site.
Permit 2FA with Kinsta
Along with the usage of a powerful password for MyKinsta, we suggest enabling two-factor authentication and asking all customers for your corporate to do the similar. With 2FA enabled, all MyKinsta login makes an attempt would require an extra verification code from an authenticator app (e.g., Google Authenticator) to your telephone or password control app.
To permit 2FA in MyKinsta, click on to your identify within the most sensible proper nook and choose Consumer settings. In My Account, scroll the web page right down to the segment Two-factor authentication. Click on at the toggle button and scan the QR code for your authenticator app, input the 6-digit code you spot within the app, and you’re executed.
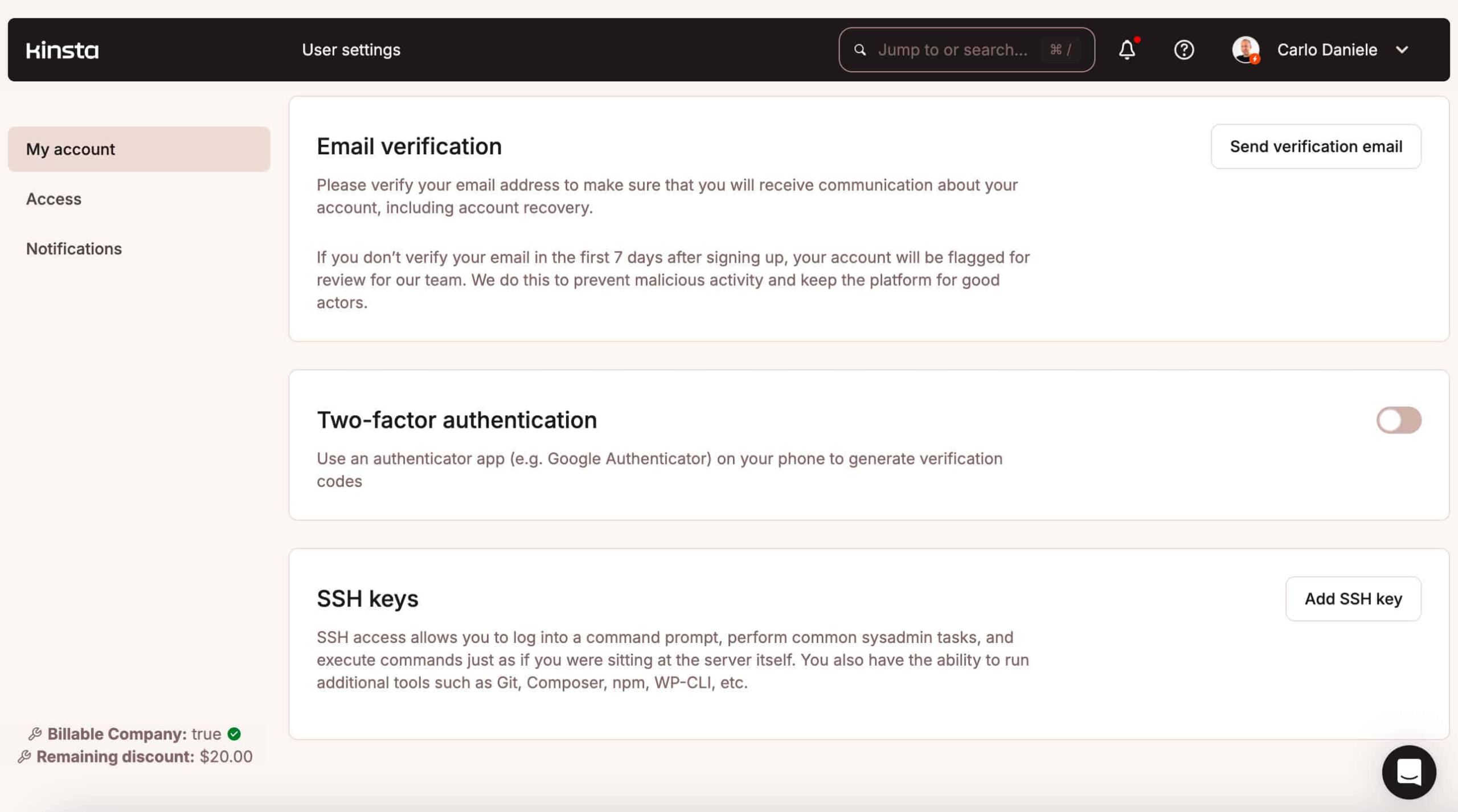
Be aware that Kinsta not helps SMS-based 2FA as a result of it’s liable to phone-based assaults and is much less safe than a time-based token. A up to date Authy knowledge breach uncovered 33 million buyer telephone numbers, expanding the specter of SMS phishing and SIM-swapping assaults.
You’ll be able to learn extra about 2FA on Kinsta in our documentation.
Permit 2FA with WordPress
You may additionally wish to permit two-factor authentication to your e-commerce site. WordPress does no longer fortify 2FA out of the field, however you’ll be able to briefly and simply upload this selection on your site with one of the crucial following plugins:
7. Core, plugins, and theme updates
Along with WordPress core releases, new safety updates are issued continuously on every occasion a brand new vulnerability is detected. The similar occurs with issues and plugins.
To stay your WordPress site secure, you want to stay all your WordPress site up-to-the-minute to forestall safety vulnerabilities.
On your WordPress dashboard, beneath Dashboard > Updates, you’ll be able to permit computerized core updates for all WordPress variations, or for repairs and safety releases handiest.
You’ll be able to additionally organize computerized updates for issues and plugins.
Be aware that, beginning with WordPress 6.6, you’ll be able to rollback computerized updates to your plugins in case of failure.
When you favor, you’ll be able to disable this selection and carry out the updates your self, however updating a lot of websites is usually a time-consuming and uninteresting job. That’s why many businesses lodge to third-party equipment that permit them to regulate updates to all their WordPress websites from a unmarried exterior atmosphere.
Kinsta consumers don’t want to pay for third-party products and services to regulate their updates in bulk as a result of they are able to benefit from the majority updates characteristic to be had within the MyKinsta dashboard.
WordPress updates with Kinsta
You’ll be able to organize your WordPress site issues and plugins immediately from MyKinsta. On your dashboard, navigate to WordPress websites > Sitename > Issues and plugins. Right here, you’ll be able to choose a number of plugins or issues and replace them personally or in bulk.
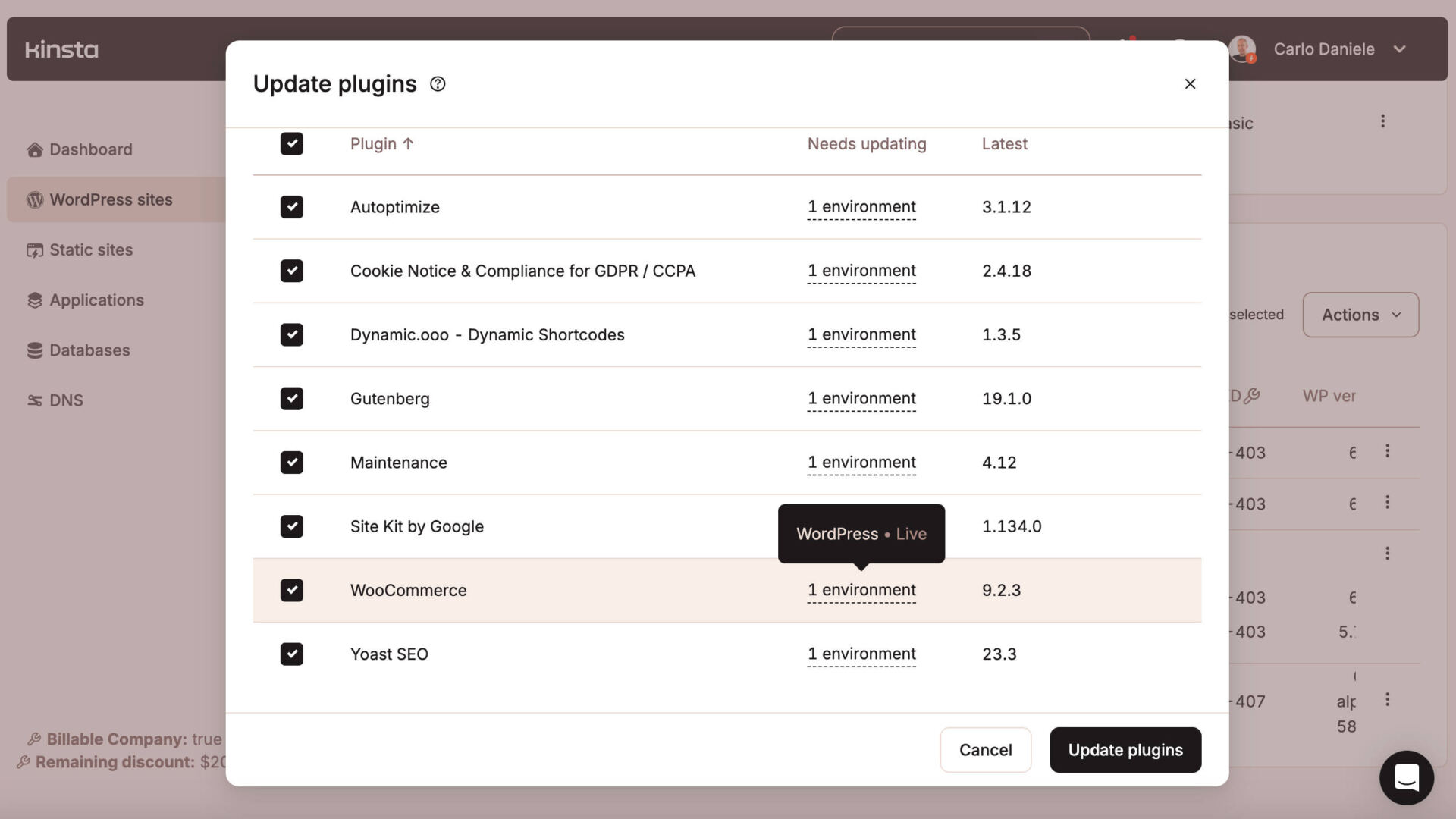
Be aware that whilst you run an replace from MyKinsta, a system-generated backup is created so you’ll be able to revert the method for two hours if the replace fails. This provides a layer of safety and provides you with peace of thoughts when you want to replace your plugins or issues.
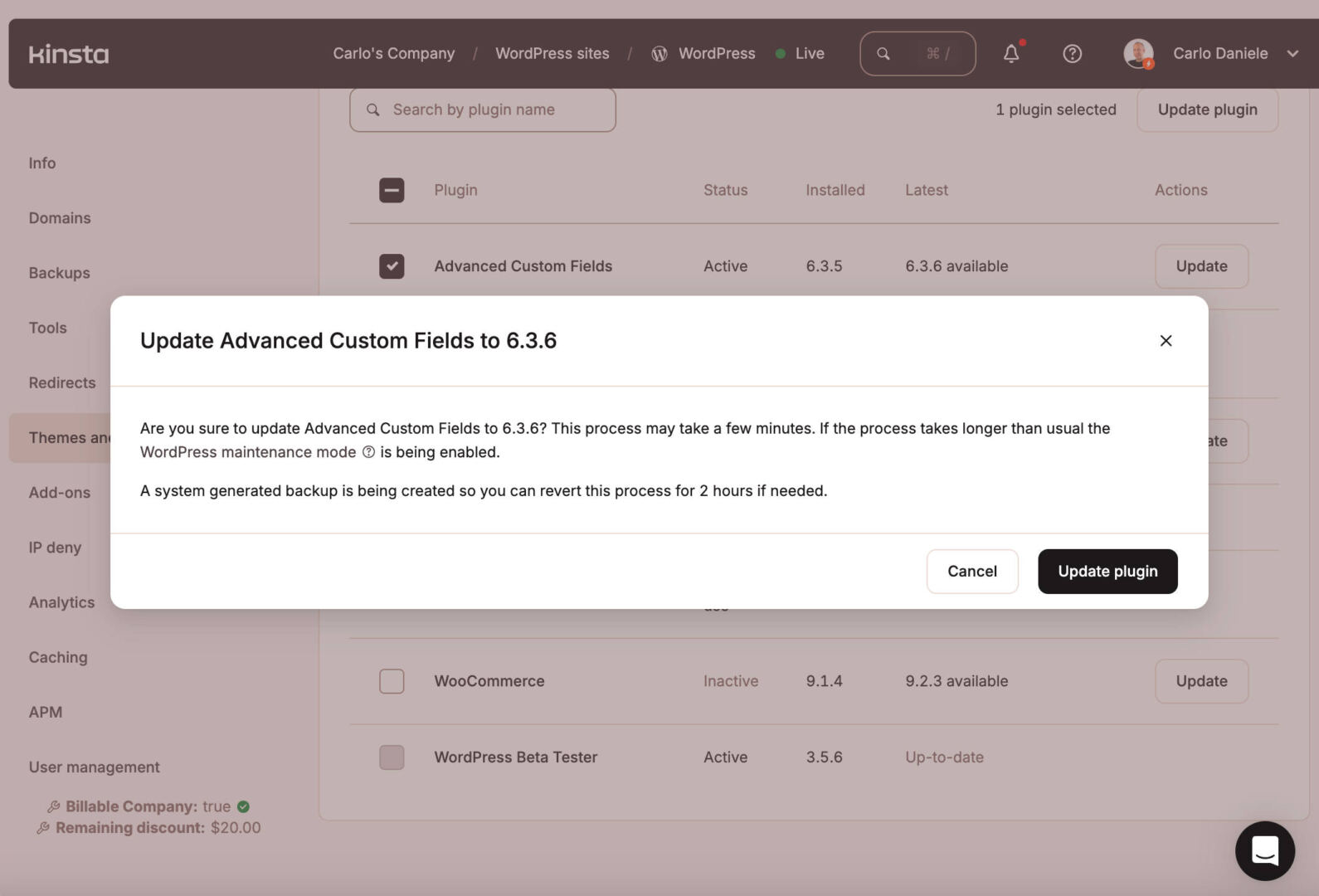
You’ll be able to additionally run bulk updates for a couple of WordPress web sites without delay. On your MyKinsta dashboard, choose WordPress websites. As soon as there, choose a number of web sites and click on at the Movements button at the proper, then choose the majority motion you wish to have to accomplish. In case you are updating plugins, click on at the corresponding menu merchandise. A pop-up will show an inventory of plugins for which an replace is to be had.
Select the plugins to replace and wait a couple of seconds. A pop-up will can help you know if the method has been finished effectively.
If the replace fails, navigate to Sitename > Backups > Machine-generated web page in MyKinsta and repair the latest backup.
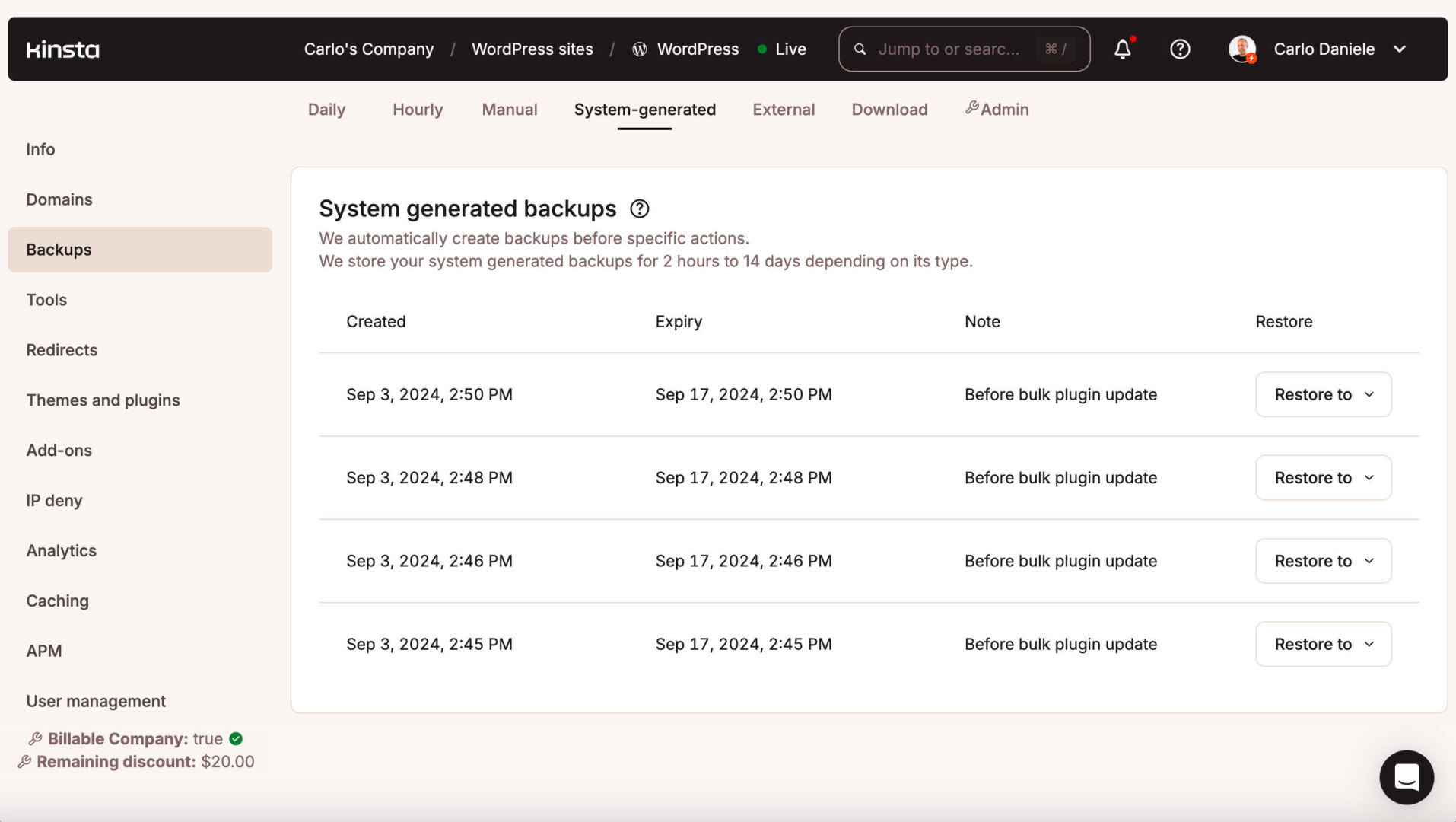
And, what’s much more robust, you’ll be able to carry out these kind of operations on a staging atmosphere first, then push staging to reside with none chance.
On Kinsta, you’ll be able to bulk replace issues and plugins for your whole WordPress websites with ease from a unmarried web page with none chance. Easiest for businesses dealing with a large number of websites in a single position.
8. Backups
If an replace is going fallacious, or a web site is compromised or totally burnt up because of a safety vulnerability, a backup can save your existence. In case your host does no longer supply an automated backup method, you’ll be able to all the time lodge to a WordPress plugin. We suggest the usage of a WordPress plugin that gives incremental backups: This lets you have a backup of your web site with out dropping disk area or decreasing web site efficiency.
Then again, a internet web hosting carrier that truly cares about your e-commerce site will have to supply common WordPress backups. Kinsta supplies six several types of backup.
The six sorts of backups equipped by means of Kinsta
We offer day by day computerized WordPress backups, in addition to system-generated backups for all WordPress web sites. Those backups, along side handbook backups, are to be had as repair issues in MyKinsta. You’ll be able to additionally manually create a downloadable backup as soon as per week.
You’ll be able to browse your backups for your MyKinsta dashboard beneath WordPress websites > Sitename > Backups. Right here you’ll be able to repair your backup to an atmosphere of your selection with a unmarried click on.
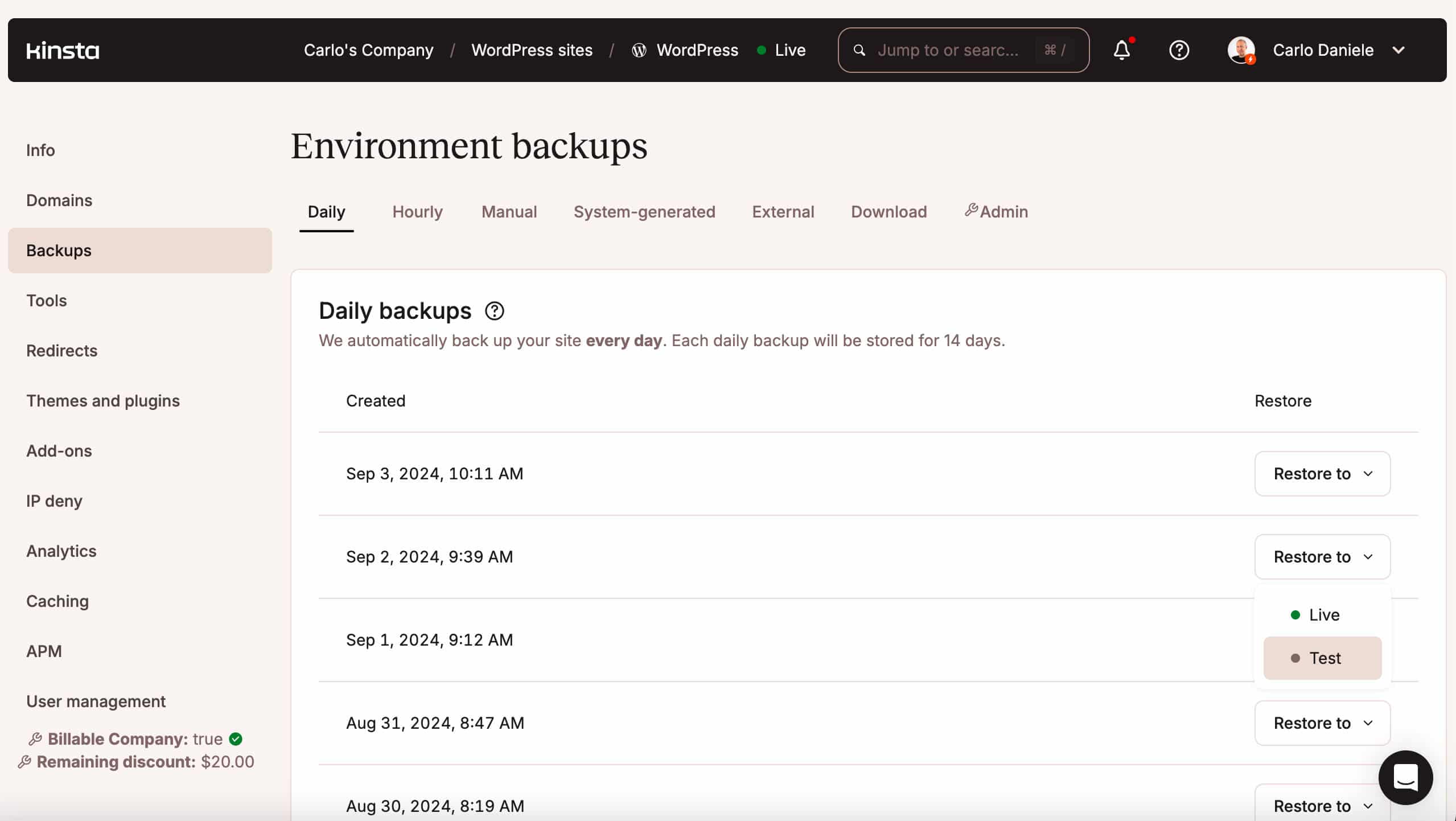
When you replace your e-commerce site a number of instances an afternoon and you want extra backups, you’ll be able to acquire an add-on for hourly backups.
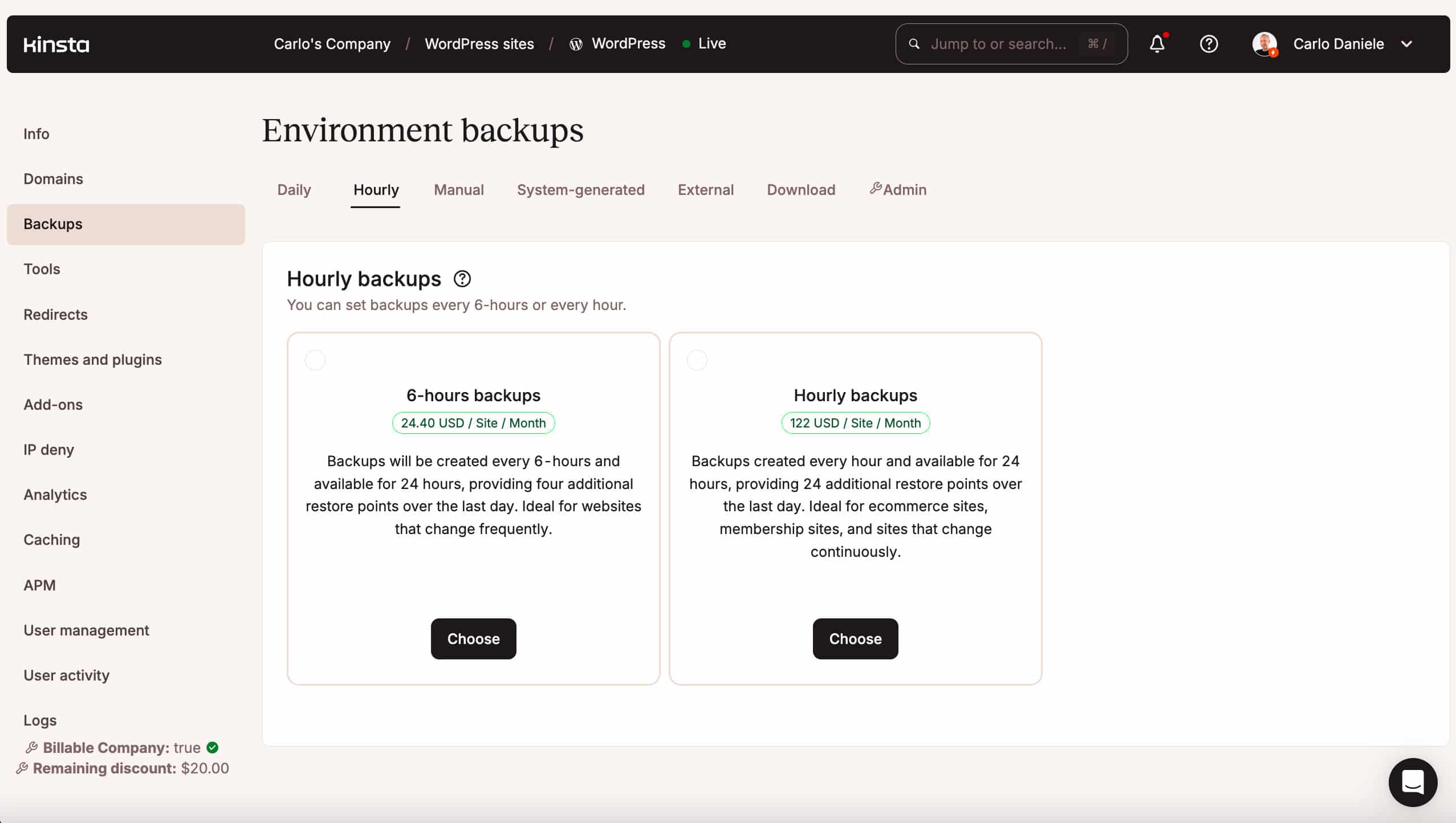
An add-on for exterior backups could also be to be had, permitting you to retailer your backups on an exterior garage carrier corresponding to Amazon S3 or Google Cloud Garage.
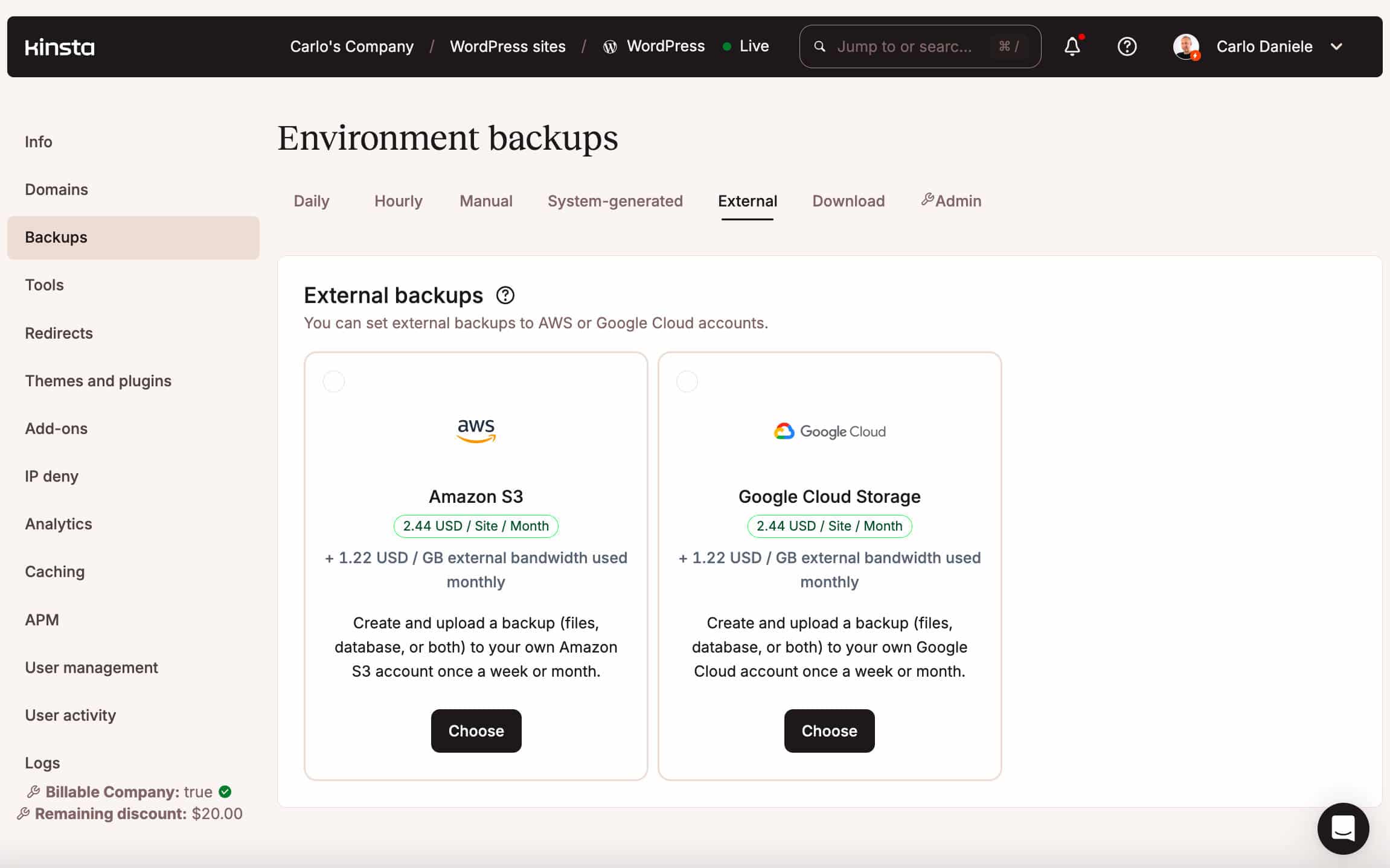
The retention duration for backups is 14 to 30 days, relying at the web hosting plan you subscribed to.
You’ll be able to learn extra about WordPress backups in our medical doctors.
9. Watch out with plugins
You regularly want many plugins to your WordPress site. That is very true for e-commerce, which regularly calls for options no longer to be had in WordPress or WooCommerce out of the field. We have now an extended listing of really useful plugins you’ll be able to flick thru to look for your self:
- 28 Very best WooCommerce Plugins
- 10 Plugins for Including Merchandise in WooCommerce
- WooCommerce Multi-Supplier Plugins
- WooCommerce Wishlist Plugins
- WooCommerce Product Clear out Plugins
- WooCommerce Weight Based totally Transport Plugins
However you will have to by no means set up the primary plugin that pops up. There are some ultimate practices to observe when opting for plugins to your WooCommerce site:
Don’t set up nulled plugins. That is essential for an e-commerce industry. Nulled plugins are top rate WordPress plugins or issues which have been hacked and will comprise changed code designed to reason hurt or accumulate knowledge.
Want plugins that obtain common updates from distributors with just right reputations. Agree with the group and take a look at evaluations and rankings from different customers. Keep away from, if conceivable, plugins with low rankings and maintained by means of unknown distributors.
All the time take a look at a plugin in a staging atmosphere earlier than the usage of it in manufacturing. This prevents compatibility problems with different plugins or the WordPress core itself.
All the time again up your web site earlier than putting in the plugin in manufacturing.
Don’t set up useless plugins or plugins offering redundant options. Needless plugins may doubtlessly create useless safety flaws, warfare with different plugins, or cut back web site efficiency.
Test if there are any recognized vulnerabilities related to the plugin. Use safety products and services such because the WordPress Vulnerability Database or WPScan.
Then again, safety vulnerabilities may also be detected in widespread plugins that obtain common updates. Plugins like WooCommerce and Simple Virtual Downloads aren’t any exception.
So, how can a internet host lend a hand with plugin and theme vulnerabilities?
Kinsta safety indicators
Each time a safety vulnerability is detected on one among your websites, whether or not it’s a core, plugin, or theme flaw, you instantly obtain a notification in MyKinsta and an electronic mail notifying you about the problem and suggesting steps to mend it.
This option is extremely valued by means of our consumers as it permits them to take fast motion on vulnerabilities detected on their websites. In case you are a Kinsta consumer, in the future, you are going to in all probability obtain an electronic mail like this:
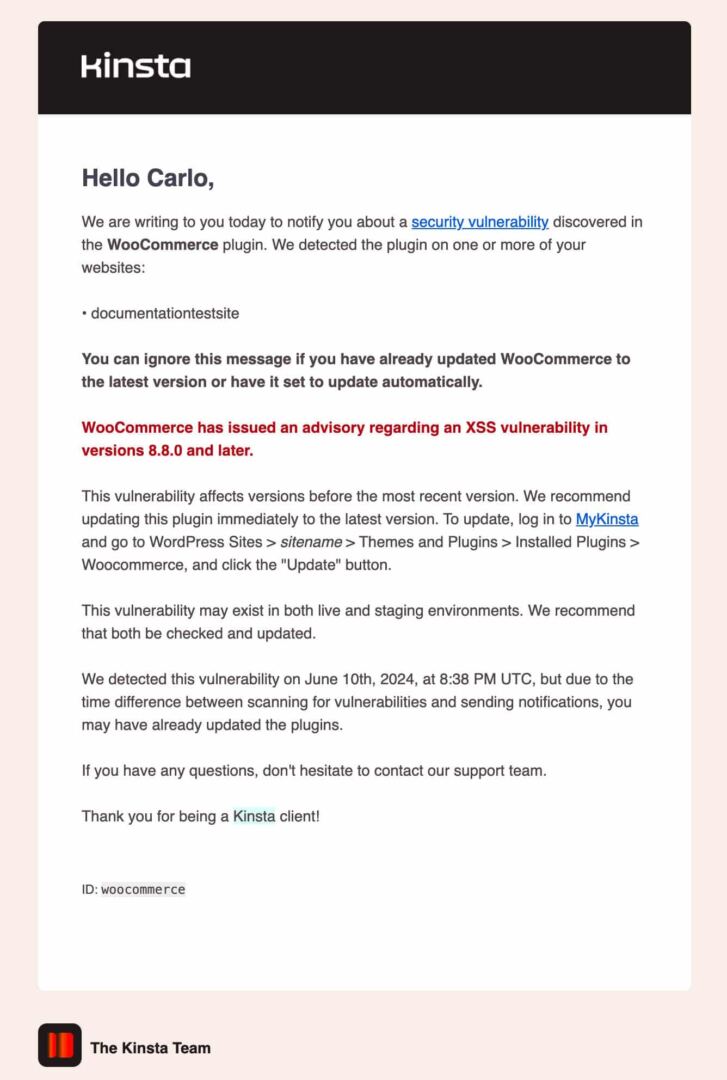
WordPress-specific threats and tips on how to save you them
Within the first segment of this newsletter, we’ve indexed one of the main safety threats that have an effect on the generality of e-commerce web sites. A few of these threats are specifically severe for WordPress/WooCommerce websites.
Even if WordPress is open-source instrument, it’s value mentioning that hackers don’t breach WordPress web sites on account of inherent vulnerabilities within the CMS however relatively on account of vulnerabilities that may have been predicted and stuck previous to any incident.
Failure to replace the core, plugins, and theme could make your e-commerce site inclined, the similar approach as the usage of vulnerable passwords and no longer having a strict web site get entry to coverage.
Here’s a fast listing of threats and ultimate practices to forestall them that will let you stay your site safe:
- Make a selection usernames and passwords in moderation
- Stay your web site up to date
- Don’t use nulled WordPress plugins and issues
- Lock down WordPress dashboard
- Permit two-factor authentication in WordPress
- Harden wp-config.php
- Disable XML-RPC
- Conceal WordPress Model
- Upload HTTP safety headers
- Use WordPress safety plugins
- Set the best permissions on WordPress information and folders
- Disable record enhancing for your WordPress dashboard
- Save you hotlinking
- Take common WordPress backups
- Use staging environments
- Take a look at the safety of your WordPress site
- Use a WordPress process log
For a extra complete listing of movements you’ll be able to take to safe WordPress web sites, take a look at our WordPress Safety Information and Website online Safety Cheat Sheet.
Extra Kinsta options to your e-commerce site safety
At Kinsta, our project is to give you the quickest and maximum safe WordPress web hosting atmosphere on the planet. We’re all the time searching for new tactics to make sure that your e-commerce web sites can be offering the most productive buying groceries revel in on your customers and purchasers. Listed below are a few of Kinsta’s products and services and lines in particular aimed toward securing your WordPress/WooCommerce site.
Uptime exams
In case your site does no longer load or its reaction time is gradual, how are you able to make sure that it’s down for everybody or simply you?
The fast resolution is that you want to test in case your site is down. You’ll be able to do it your self following those steps or, in case your web site is hosted on Kinsta, you’ll be able to depend on Kinsta uptime exams.
Kinsta scans your site each 3 mins. It’s 480 exams each day.
In case your web site is down, our engineers delivery operating instantly at the downside. There’s a excellent probability that the issue shall be mounted earlier than you even understand it.
Test Out Our Video Information On How To Test if a Web site Is Down:
Kinsta’s safety pledge
Retaining an e-commerce web site up-to-date is essential for your small business, however it will not be sufficient. Because of this, scanning your site continuously with malware detection equipment, corresponding to Sucuri or WordFence, is all the time really useful even though you don’t suspect to had been inflamed. Our recommendation is to scan your e-commerce site at least one time a month, however we propose scanning a number of instances a month anytime you are making adjustments to the web site construction and set up new plugins. When you don’t know the place to start out, here’s a safety tick list to your site.
However occasionally, in spite of your whole efforts, it will occur that your web site will get inflamed. What to do then?
Kinsta consumers wouldn’t have to fret about this as a result of Kinsta supplies a loose hack repair ensure for all our purchasers irrespective of their plan. In case your WordPress web site is hacked whilst hosted at Kinsta, we’ll paintings with you without cost to check out and undo the wear and tear.
Our safety pledge comprises:
- An inspection of the web site and a deep scan of the web site’s information to spot malware.
- Restore of the WordPress core by means of putting in a blank reproduction of the core information.
- Identity and elimination of inflamed plugins and issues.
Test our medical doctors for a extra detailed evaluation of Kinsta’s safety pledge.
IP blockading
Infrequently, it can be essential to dam an IP deal with or vary of IPs to forestall malicious conduct from bots, spammers, or different actors. Typically, you’ll be able to block IP addresses from the server configuration record.
Kinsta customers wouldn’t have to manually configure their server as a result of Kinsta supplies all our consumers with a loose IP deny software to be had in MyKinsta.
To test IPs and the choice of requests, log in to MyKinsta and navigate to WordPress Websites > sitename > Analytics > Geo & IP.
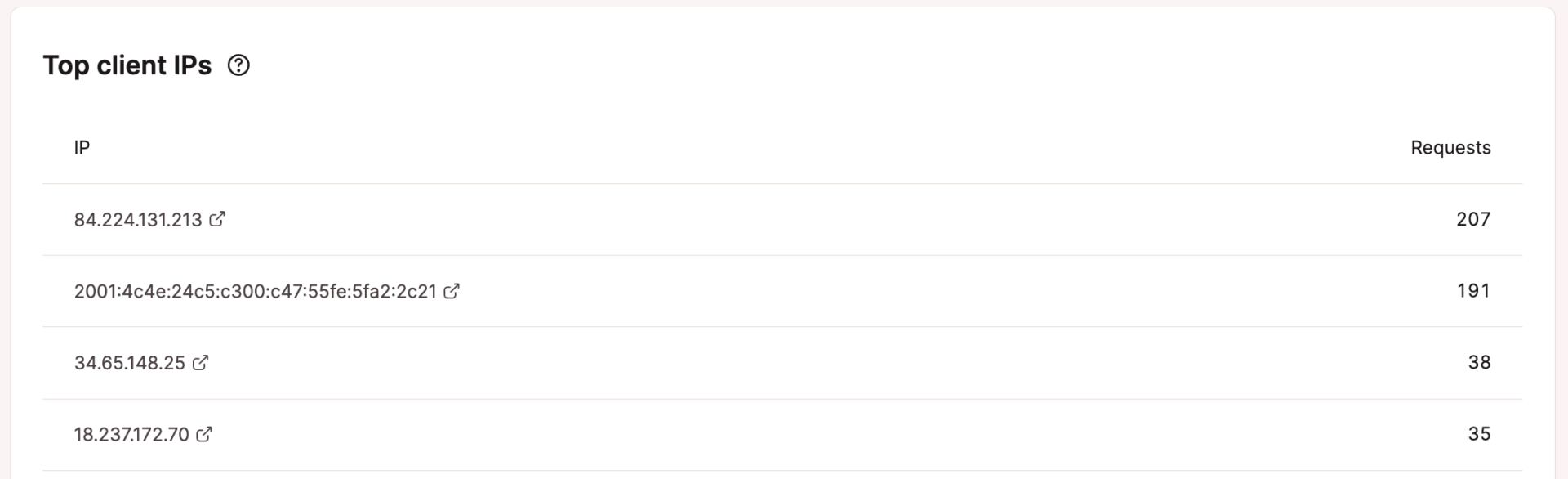
The Best consumer IPs segment presentations the listing of IP addresses and the choice of requests coming from each and every IP. When you understand an strange choice of requests from particular IPs, chances are you’ll wish to examine additional via a name checker like CleanTalk or Spamhaus to look if the IP deal with has been recognized as a bot, spammer, or different malicious IP deal with.
If an IP deal with is recognized as malicious, you’ll be able to block it the usage of the IP Deny software, to be had beneath WordPress Websites > sitename > IP deny.
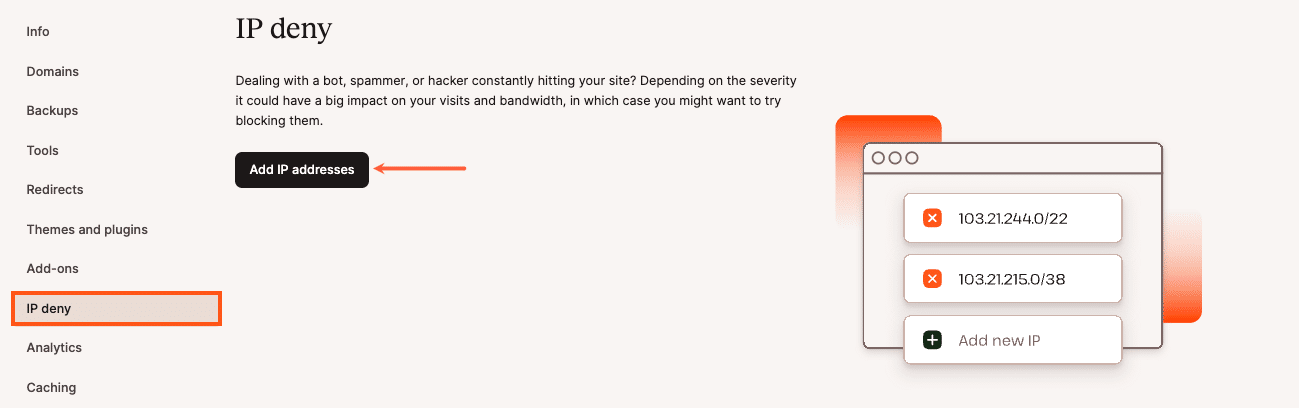
Upon getting blocked an IP deal with, you are going to see it indexed underneath at the identical web page.
Kinsta safety certifications
Kinsta dedication to making sure the safety of all purchasers’ websites is verified and authorized at other ranges.
Kinsta complies with the Safety criterion of the Machine and Group Controls (SOC 2) compliance framework advanced by means of the American Institute of Qualified Public Accountants (AICPA). This usual is used to judge a carrier group’s adherence to a number of accept as true with products and services standards.
The 5 accept as true with products and services standards are:
- Safety
- Availability
- Processing integrity
- Confidentiality
- Privateness
However this isn’t all. Kinsta has completed ISO 27001, 27017, and 27018 certifications. This success displays adherence to ultimate practices in knowledge safety, with further emphasis on controls safeguarding knowledge in cloud computing environments.
Those certifications supply a ensure of safety and steadiness for all e-commerce site homeowners who can depend on a web hosting carrier that permits them to dedicate themselves to their industry with peace of thoughts.
ISO/IEC 27001 is the arena’s best-known usual for info safety control programs. An ISMS applied in line with this usual “is a device for chance control, cyber-resilience, and operational excellence.”
Conformity with ISO/IEC 27001 implies that a company or industry has installed position a method to regulate dangers associated with the safety of information owned or treated by means of the corporate and that the program respects the entire ultimate practices and ideas enshrined on this World Usual.
ISO/IEC 27017:2015 establishes pointers for info safety controls acceptable to the availability and use of cloud products and services. It supplies:
- further implementation steering for related controls laid out in ISO/IEC 27002;
- further controls with implementation steering that in particular relate to cloud products and services.
Closing, ISO 27018:2019
establishes regularly approved keep an eye on goals, controls, and pointers for enforcing measures to give protection to In my view Identifiable Knowledge (PII) in keeping with the privateness ideas in ISO/IEC 29100 for the general public cloud computing atmosphere.
You’ll be able to discuss with Kinsta’s Agree with Middle for more info at the corporate’s ongoing compliance efforts.
Abstract
There’s a lot to be executed to safe an e-commerce site. Doing it your self calls for really extensive technical abilities that will not be to be had to small companies and start-ups.
But an organization proprietor who needs to release an internet retailer, accepting the problem of world markets, will have to no longer surrender the expansion alternatives that e-commerce has to supply. That is the place enterprise-level controlled WordPress and WooCommerce web hosting can lend a hand.
As a top rate controlled WordPress and WooCommerce internet web hosting carrier, Kinsta supplies a quick and safe cloud web hosting for any e-commerce site. With Kinsta, you’ll be able to release an internet retailer with out being worried about the entire technical intricacies, leaving at the back of an e-commerce site.
Our options come with computerized day by day backups, a devoted firewall powered by means of Cloudflare, real-time tracking for threats and vulnerabilities, loose SSL certificate for encrypted transactions, DDoS coverage to protect towards malicious site visitors, and plenty of extra options to give protection to your e-commerce site.
With these kind of proactive safety features, Kinsta locks your e-commerce site, minimizing the chance of information breaches and downtime.
Now it’s your flip. What are the dangers and vulnerabilities you take care of each day? Does your web hosting carrier supply your e-commerce web site with good enough coverage towards malicious brokers? Percentage your revel in within the feedback underneath.
The submit Safety necessities and 9 ultimate practices for tough e-commerce web sites seemed first on Kinsta®.
WP Hosting