GitHub Movements is GitHub’s integrated steady integration and steady supply (CI/CD) platform that allows building groups to automate their workflow, together with the construct, take a look at, and deployment pipeline.
One drawback of the use of GitHub Movements is that your logs are public, and any individual can get right of entry to them with the important permissions.
To stop touchy information from being uncovered in GitHub Movements logs, you need to use encrypted surroundings variables to retailer touchy information safely. Those encrypted environmental variables are referred to as GitHub Movements Secrets and techniques.
This text presentations you tips on how to use GitHub Movements Secrets and techniques to forestall touchy knowledge from showing for your GitHub Movements logs.
Contents
Necessities:
To apply this educational:
- You should definitely have a GitHub account.
- Have an present GitHub repository. For this educational, you’ll be able to clone this demo repository.
- Practice those directions to clone the demo repository.
How To Stay Your GitHub Motion Logs Protected
While you construct workflows the use of GitHub Movements, any customer for your repository can view the logs, in order that they shouldn’t come with touchy knowledge. Alternatively, you’ll be able to’t simply delete your tokens, passwords, and different touchy knowledge — you want them for trying out and on your app to serve as accurately.
The answer is to cover them with the ::add-mask:: workflow command, which places an asterisk (*) instead of the touchy information it’s implemented to.
The next segment presentations you tips on how to masks a log.
How To Masks Logs
First, open the cloned repository for your textual content editor.
Create the .github/workflows/ listing within the root of your repository to retailer your workflow recordsdata. Then, create a brand new record named hide-secrets.yml within the .github/workflows listing and upload the next code to it:
identify: Conceal Delicate Data
on: push
jobs:
print-secret-token:
runs-on: ubuntu-latest
steps:
- identify: echo a secret
run: echo "your secret token is verySecretToken"Devote the adjustments and push them for your GitHub repository. The up to date GitHub Movements workflow is lively and might be brought on on every occasion you push a brand new trade.
Open your repository on GitHub and make a choice the Movements tab to view the logs. Your workflow will have to seem as follows:
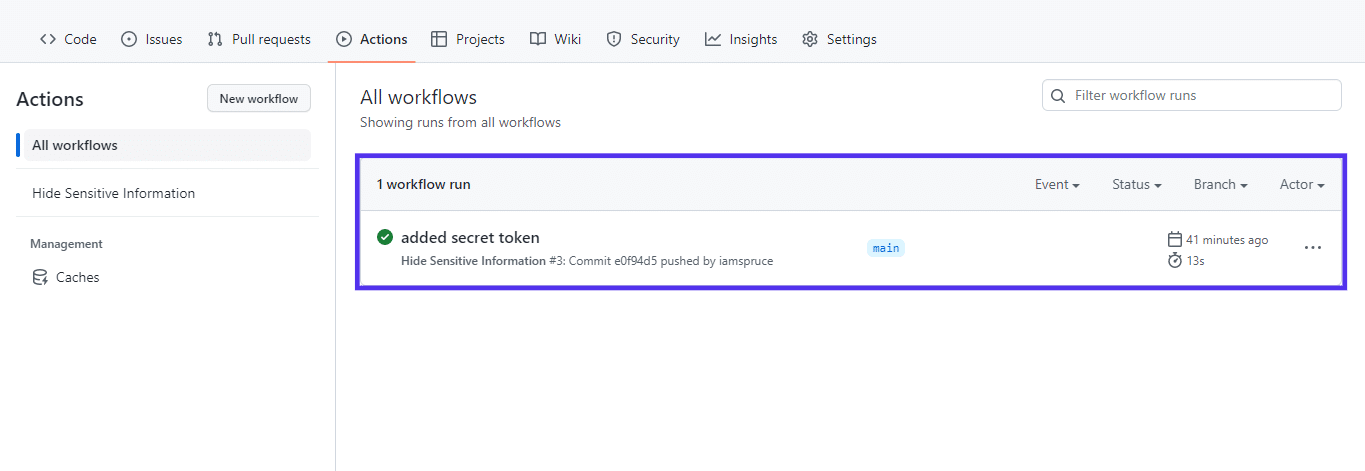
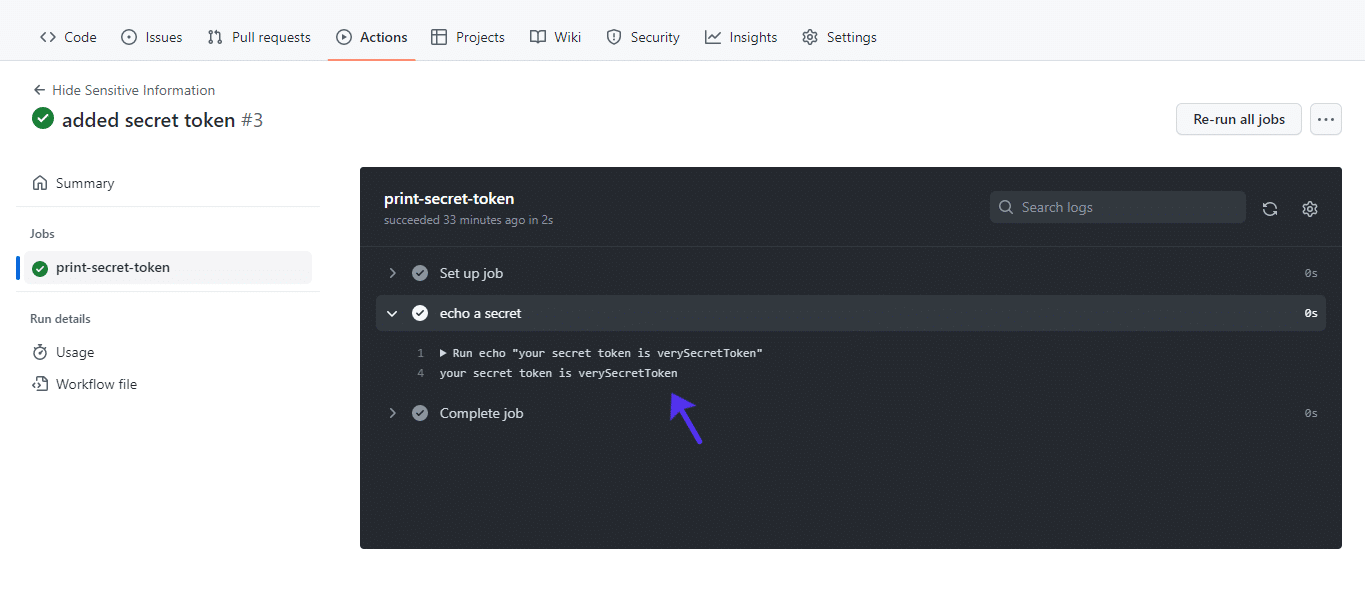
Analyzing the workflow logs, you’ll in finding the verySecretToken string imprinted on the logs. Click on in your workflow, after which the duty identify (print-secret-token) to view the log. It will have to seem like this:
To cover it, use the ::add-mask:: command, edit the hide-secrets.yml record, and upload a brand new step to the print-secret-token process:
identify: Conceal Delicate Data
on: push
jobs:
print-secret-token:
runs-on: ubuntu-latest
steps:
- identify: Upload Masks
run: echo "::add-mask::verySecretToken"
- identify: echo a secret
run: echo "your secret token is verySecretToken"You will have to upload the Upload Masks step on the most sensible, since protecting best applies after ::add-mask:: has run. If you happen to put the name of the game verySecretToken ahead of the Upload Masks step, it’s going to nonetheless seem unmasked. So, to make sure the price is masked, it’s crucial to make use of ::add-mask:: once conceivable.
While you dedicate and submit your adjustments for your GitHub repository, the string verySecretToken might be changed by means of asterisks (*) anyplace it seems that for your logs:
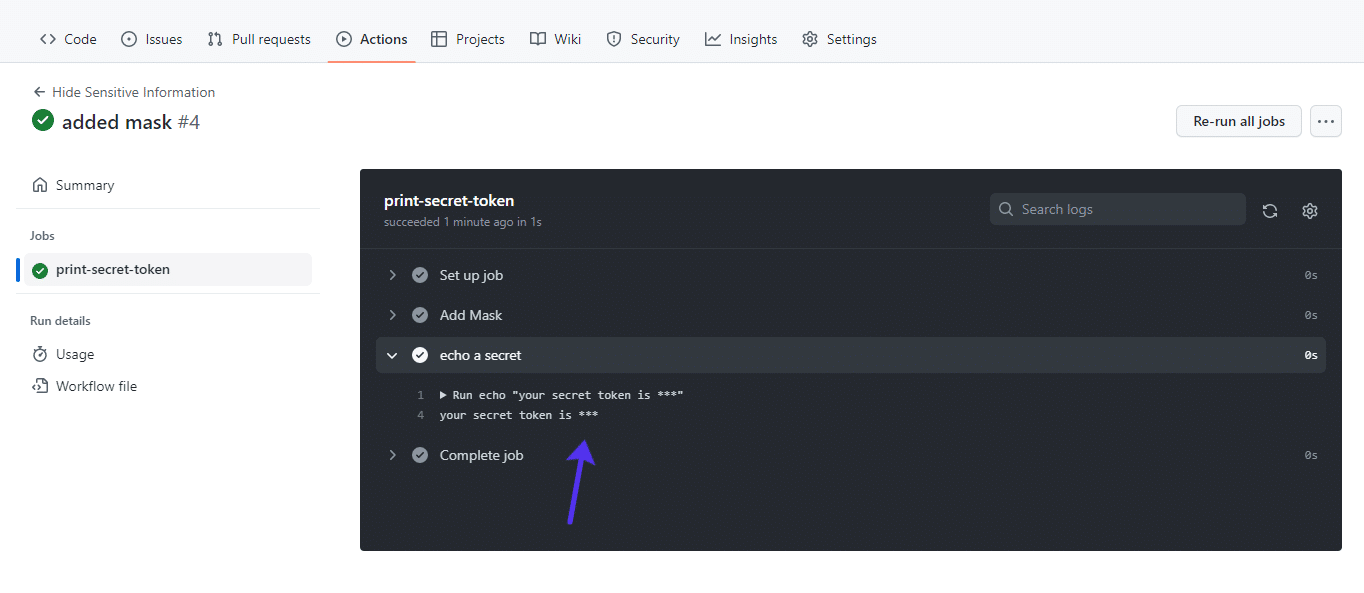
Whilst this fixes the protecting downside, it introduces a brand new one. Your verySecretToken continues to be within the workflow record, so any individual with get right of entry to to the supply code can see it.
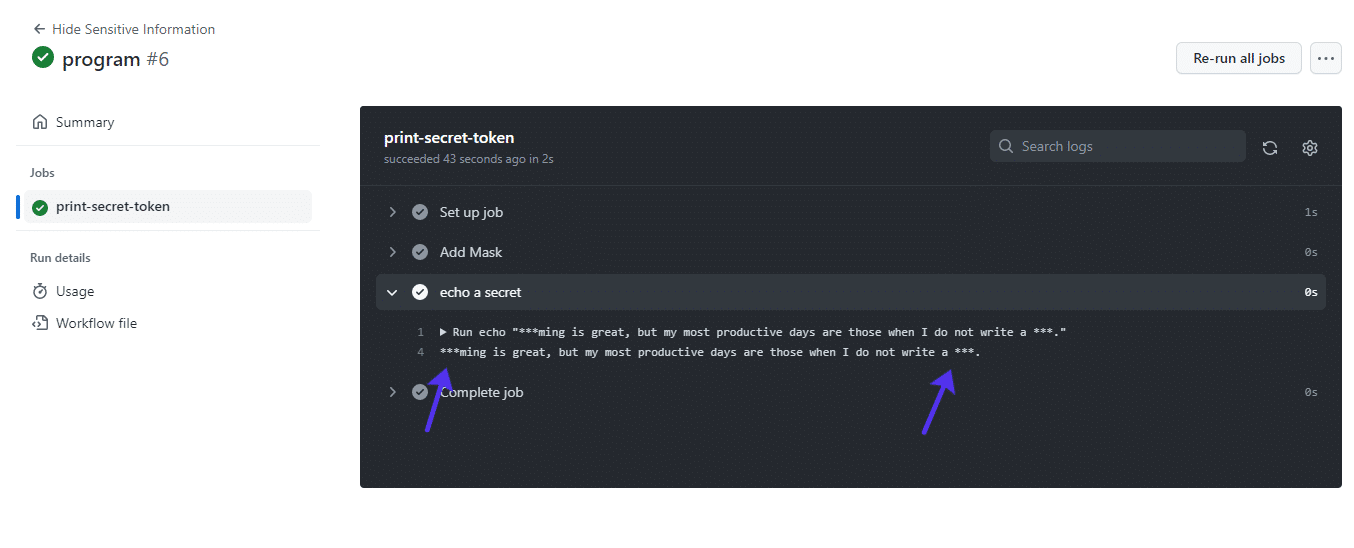
Some other drawback of protecting undeniable textual content is that protecting simply a part of a phrase will disguise all cases of it. As an example, take the next sentence: “Programming is excellent, however my most efficient days are the ones once I don’t write a program.” If you happen to masks the phrase “program,” it received’t best masks the phrase on the finish of the sentence but in addition anyplace else it seems that, corresponding to in “programming.”
If you happen to attempt to masks undeniable textual content, you’ll finally end up with one thing like this:
A greater way to hiding touchy information in GitHub Movements logs is to make use of GitHub Movements Secrets and techniques, as demonstrated within the following segment.
How To Use GitHub Movements Secrets and techniques
You’ll be able to use GitHub Movements Secrets and techniques to retailer any non-public information you wish to have to make use of for your GitHub movements workflow. Secrets and techniques are created as key/price pairs on the repository or organizational stage.
Whilst that repository might best get right of entry to secrets and techniques created on the repository stage, secrets and techniques created on the group stage are shared by means of all repositories inside a company.
Secrets and techniques created on the repository stage are to be had to be used in movements by means of any individual who has collaborator function permissions. You’ll be able to trade the price of your secrets and techniques at any time. Alternatively, secrets and techniques can’t be used with workflows from a forked repository.
The next pointers observe for naming secrets and techniques:
- Secret names can’t include areas.
- Secret names aren’t case-sensitive.
- Secret names can’t start with a host.
- Secret names should now not start with the prefix
GITHUB_. - Secret names should be distinctive — secrets and techniques with the similar identify can’t exist on the identical stage.
You’ll be able to use those secrets and techniques inside the GitHub movements workflow by means of merely including secrets and techniques ahead of your secret identify as a YML variable, as proven underneath:
${{ secrets and techniques.MY_SECRET_TOKEN }}You’ll be able to additionally masks secrets and techniques for extra safety, as proven within the following segment.
How To Masks Secrets and techniques
First, create a GitHub secret. To your repository on GitHub, click on the Settings tab, make a choice Secrets and techniques > Movements from the left sidebar, after which click on New repository secret so as to add a brand new secret:
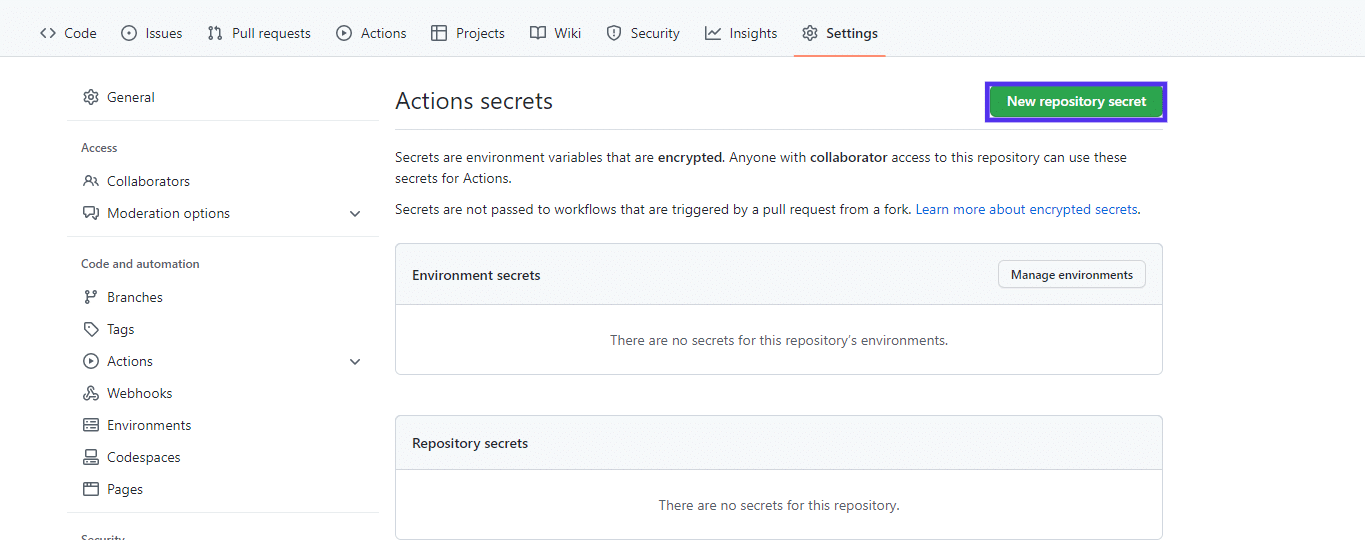
Give your secret a reputation and a secret price, then click on Upload secret:
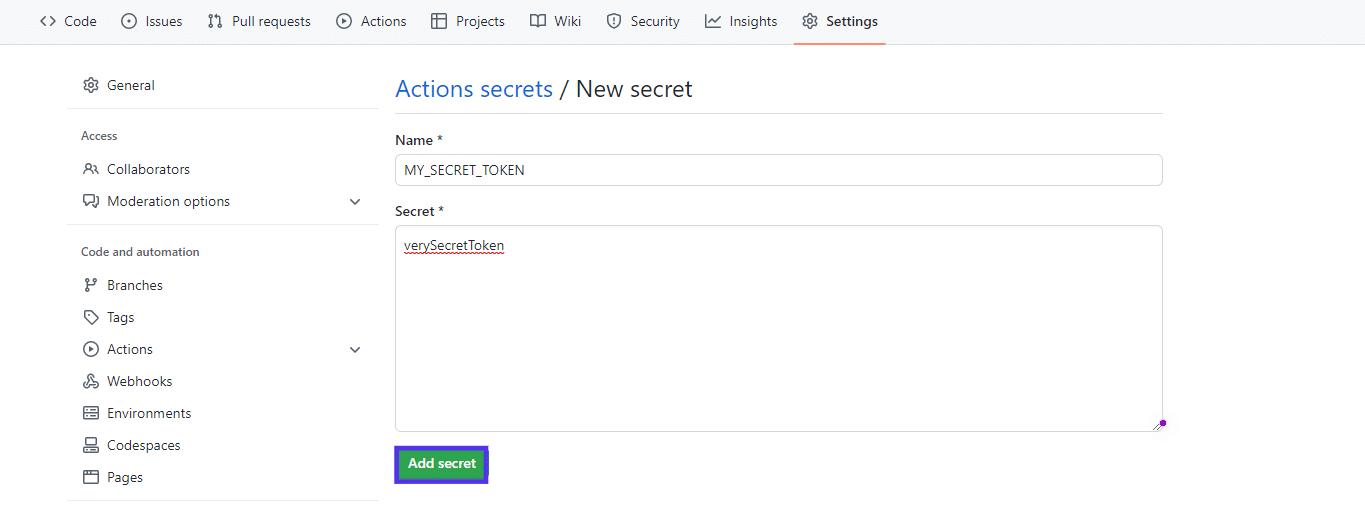
Now that you simply’ve created your secret and given it the verySecretToken price, you’ll be able to use it for your workflow record. Open your hide-secrets.yml record and make the next adjustments:
identify: Conceal Delicate Data
on: push
jobs:
print-secret-token:
runs-on: ubuntu-latest
steps:
- identify: Upload Masks
run: echo "::add-mask::${{ secrets and techniques.MY_SECRET_TOKEN }}"
- identify: Echo a secret
run: echo "your secret token is ${{ secrets and techniques.MY_SECRET_TOKEN }}"The one distinction between this and the former code is that you simply changed the name of the game token along with your newly created GitHub secret “${{ secrets and techniques.MY_SECRET_TOKEN }}.”
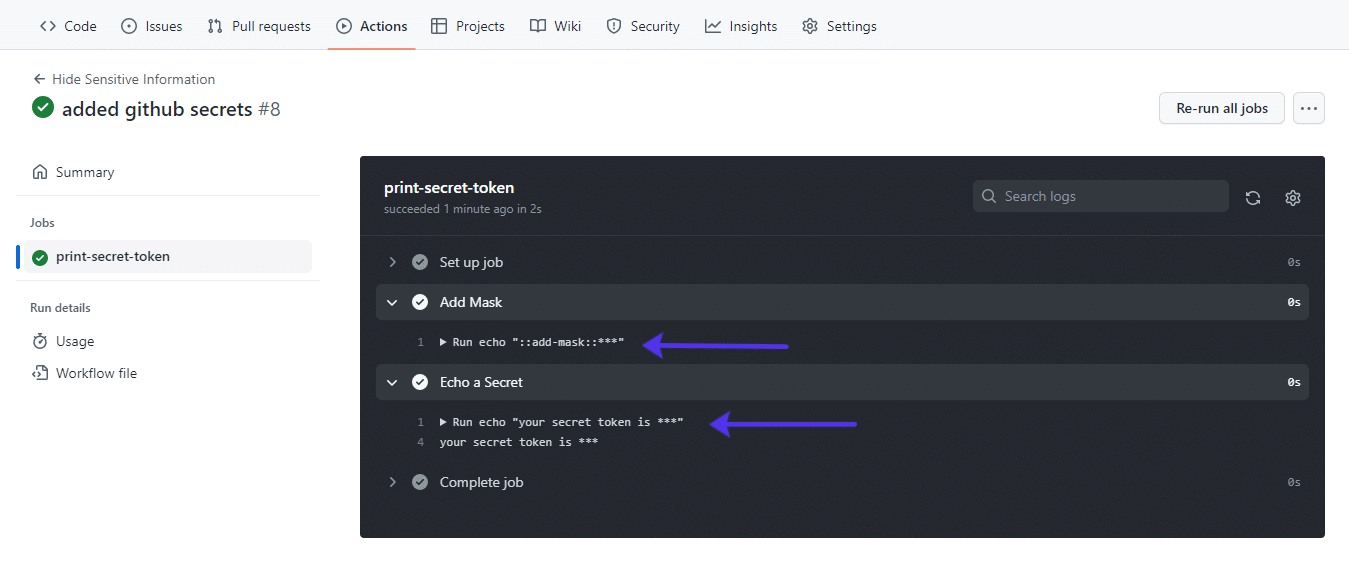
While you dedicate the code and push the adjustments for your GitHub repository, your secrets and techniques are masked:
Abstract
You mustn’t divulge any touchy knowledge for your GitHub Motion logs. Undeniable textual content protecting is one technique to disguise information, however any individual getting access to your workflow recordsdata can see the tips you’re looking to disguise.
As this educational demonstrates, GitHub Movements Key’s a a lot more protected way to safeguard your touchy information, after which masks it.
Learn our documentation to be told extra about the use of Git at Kinsta. Check out our Utility Webhosting totally free now.
The put up Quilt Your Tracks: Find out how to Conceal Issues in GitHub Movements Logs gave the impression first on Kinsta®.
WP Hosting


