Git doesn’t need to be advanced, however there are specific sides of it which might be intricate and require a deeper working out – Git hooks, as an example. Those are scripts that Git will run robotically according to sure occasions.
Whilst they are able to be easy, you’ve gotten a lot more scope to make use of them in a good way. Alternatively, to try this, you should perceive all of the cogs that make up all the wheel.
For this publish, we’ll take a look at complex ways for Git hooks that come with some basics, how you can create and set up them, and extra.
Right through, we’ll give an explanation for hook parameters and setting variables, be offering some guidelines and methods, run thru troubleshooting strategies, and plenty of different subjects.
Contents
- 1 The Basics of Git Hooks: A Primer
- 2 How To Create and Set up Customized Git Hooks
- 3 How To Create and Set up Complicated Customized Hooks
- 4 Figuring out Hook Parameters and Surroundings Variables
- 5 Pointers and Tips to Set up and Proportion Your Git Hooks
- 6 Conventional Practices to Assist You Handle Protected Git Hooks
- 7 How To Troubleshoot Your Hooks
- 8 The Advantages of Integrating Hooks Into Steady Integration (CI/CD) Pipelines
- 9 Abstract
The Basics of Git Hooks: A Primer
Certainly one of Git’s key options is its hooks: a formidable mechanism that permits you to automate duties, put into effect requirements, and make sure constant workflows during a assignment’s lifecycle.
Git hooks are scripts that execute robotically at particular issues within the Git workflow. You’ll use them to customise and lengthen Git’s habits to fulfill your assignment’s wishes. Hooks be sure that code high quality is maintained, assessments are run, and deployments are orchestrated easily.
Git provides different types of hooks, and each and every one will cause at other levels of the Git workflow:
- Pre-commit. Those hooks run prior to you finalize a dedicate, which helps you to put into effect code kinds, run assessments, or take a look at for syntax mistakes.
- Submit-commit. This will likely execute after you create a dedicate. It’s helpful for notifications or logging.
- Pre-push. This hook will cause prior to you push code and allows you to carry out integration assessments, take a look at for compatibility, or ensure that high quality.
- Submit-push. The general hook runs after you entire a push. As such, it’s precious for deploying code to manufacturing or updating documentation.
You’ll in finding hooks inside the .git/hooks listing of your Git repository. There are pattern hooks inside there, too – you’ll be able to use them as templates to create your personal customized scripts. The hooks duvet a variety of movements and use a sample- prefix for reference:
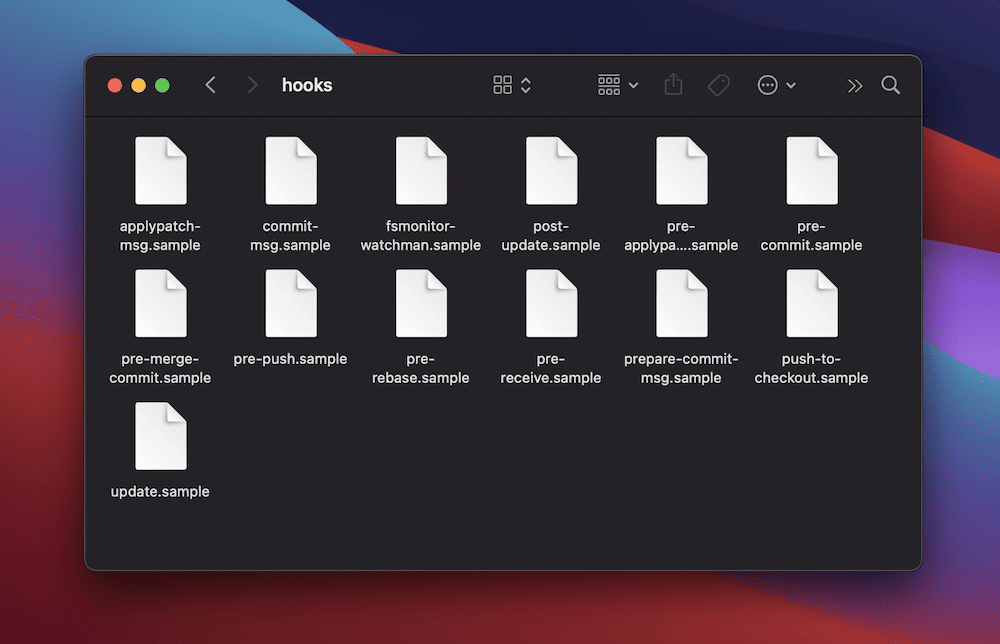
Hooks cause right through quite a lot of Git movements. As an example, a pre-commit hook runs while you dedicate adjustments, and a pre-push hook triggers prior to you push to far off. As soon as you know extra about those triggers, you’ll be able to deploy hooks extra strategically to put into effect high quality keep watch over and streamline your workflow.
How To Create and Set up Customized Git Hooks
Developing and putting in fundamental customized Git hooks generally is a advanced procedure. Alternatively, the basics you’ll use right here will set you up for creating complex hooks later. Let’s run thru a couple of ideas that observe to each hook you create and set up.
Opting for an Suitable Hook Sort
Using the best hook sort to your particular use case might be a very powerful first step to take. You’ll start via working out your personal construction workflow and wishes. Right here’s a handy guide a rough tick list of concerns in this:
- First, imagine your procedure’s quite a lot of levels, reminiscent of coding, checking out, and deployment. Additionally, establish the place that procedure may get pleasure from automation and assessments.
- From there, find spots on your workflow the place mistakes or inconsistencies happen regularly. Customized Git hooks may assist right here. For instance, in case you fail to remember to run assessments prior to a dedicate, a pre-commit hook can deal with the problem.
- Subsequent, imagine while you’d love to execute the hook inside your workflow. As an example, if you wish to be sure that all commits meet coding requirements, a pre-commit hook is suitable. If you wish to validate code prior to you push to far off, a pre-push hook might be extra appropriate.
- In any case, be sure that your preferred hook sort is appropriate along with your construction setting and the gear you employ. Imagine the scripting language you’ll use for the hook and its execution setting.
At this level, you will have to be capable of outline transparent goals to your hook. It is going to also be that each and every purpose calls for a distinct form of hook. Alternatively, whilst it’s tempting to create scripts for each conceivable state of affairs, it’s a good suggestion to concentrate on addressing important ache issues first.
Naming and Striking Customized Git Hooks
Naming and hanging customized Git hooks accurately is a very powerful for making sure their capability and maintainability. As along with your code’s purposes, information, magnificence names, and extra, your Git hooks will have to actually have a constant and descriptive naming conference.
If hooks will improve more than one tasks over the years as a template, you might need to use prefixes – possibly with developer initials, a division, or an organization call. Basically, Git hooks use lowercase letters and hyphens for clarity – e.g., my-project-pre-commit.
As well as, when you might retailer Git hooks within the .git/hooks listing of your repo, customized hooks will have to cross in a separate listing inside the assignment’s root folder. This will likely save you unintentional overwrites right through a Git replace. Alternatively, you will have to enforce model keep watch over for the ones hooks together with the remainder of your assignment’s code.
How To Create a Fundamental Customized Git Hook
The everyday solution to write a fundamental Git hook is to create a brand new record with the call of your preferred hook (reminiscent of pre-commit) on your hooks listing. We’ll record the hook names later when speaking about parameters.
Sooner than you open a record to paintings with it, you will have to ensure that it’s executable the usage of the next command line snippet:
chmod +x trail/to/record/hook-nameBear in mind to exchange our placeholders with the best data. We’ll reference this snippet during the publish, correctly a standard motion every time you create a brand new Git hook.
As soon as the record is executable and open, upload your customized common sense the usage of your most popular scripting language. This may well be Bash, Python, Ruby, and others. Crafting those is, after all, past the scope of what we’ll duvet right here. Alternatively, there are some pseudocode examples later directly to show off particular use circumstances and eventualities.
In any case, prior to you dedicate any adjustments, check your hook via making an attempt to run the comparable motion (reminiscent of a dedicate). That is the elemental technique to developing Git hooks, however there are many complex use circumstances. We’ll take a look at this subsequent.
How To Create and Set up Complicated Customized Hooks
Developing fundamental Git hooks might be one thing you do so much during your construction profession. Alternatively, a variety of eventualities will name for extra complex and sophisticated hooks. Subsequent, we’ll take a look at some use circumstances and pattern hooks for a number of not unusual eventualities.
Create a Hook That Enforces Code Taste The use of Linters
The use of a linter to put into effect code styling is an incredible software for Git hooks. It will possibly assist to handle constant code high quality during your repository and will have to be one thing you’ll be able to get numerous price from.
After all, you will have to make a selection a linter that fits your assignment’s programming language. For instance, Black is improbable for Python. We’re going to make use of ESLint for JavaScript right here to create a pre-commit hook.
First, set up the linter as an international or native package deal inside your assignment. You’ll want Node.js and npm for this:
npm set up eslint --save-devSubsequent, navigate in your hooks listing inside your repo. Create your pre-commit record, then write a script that runs the linter to your staged information. The hook will have to save you the dedicate if the linter reveals any problems. Right here’s a coarse instance:
#!/bin/sh
# Stash unstaged adjustments (non-compulsory however beneficial)
git stash -q --keep-index
# Run the linter on staged information
npm run lint # Exchange with the correct linting command
LINT_RESULT=$?
# Unstash the stashed adjustments (non-compulsory however beneficial)
git stash pop -q
# Go out with the linter's go out code
go out $LINT_RESULTWhen you ensure that the hook is executable, check it out thru a dedicate. The pre-commit hook will have to run the linter. If there are any code taste violations, you received’t be capable of entire the dedicate till you repair the problems.
After all, you will have to write a hook that works with your personal programming language and linter, in step with your assignment. As an example, it is advisable lengthen this case with linter configuration settings, integrating it along with your construct procedure, and extra.
Put in force a Hook for Operating Exams Sooner than a Devote
Enforcing a pre-commit hook to run assessments prior to a dedicate is a wonderful solution to catch any attainable problems early on. As such, you’ll be able to be sure that you dedicate best passing dependable code.
For this case, we’ll use the Jest checking out framework for JavaScript. You’ll need to set up one thing appropriate to your assignment (as all the time):
npm set up jest --save-devAs with each hook, navigate in your hooks listing, create a brand new record, call it, and make it executable. From right here, write a script that runs assessments on all staged information prior to the dedicate. Right here’s a coarse template:
#!/bin/sh
# Stash unstaged adjustments (non-compulsory however beneficial)
git stash -q --keep-index
# Run assessments on staged information
npm check # Exchange with the correct check command
TEST_RESULT=$?
# Unstash the stashed adjustments (non-compulsory however beneficial)
git stash pop -q
# Go out with the check's go out code
go out $TEST_RESULTWhile you try to dedicate adjustments, the hook will execute your assessments at the staged information. The dedicate will stop for any failed assessments, and also you will have to deal with the problems prior to re-committing.
Broaden a Hook for Automating Versioning and Tagging
One very good solution to streamline the discharge procedure is to automate versioning and tagging inside Git. This will likely ensure that constant versioning throughout your codebase.
To start out, make a selection a versioning scheme appropriate to your assignment. That is past the scope of the object, however not unusual schemes come with Semantic Versioning (SemVer) or a customized versioning trend.
Subsequent, make a decision precisely what your hook will do. As an example, it will learn the present model, increment it in step with a delegated scheme, and replace the important information with the brand new model. You’ll additionally need to write a script for developing tags according to the model, which makes use of Git instructions to create light-weight or annotated tags.
When you create and set permissions to your record, you’ll be able to start to write your hook. This is a advanced and extremely particular hook that can even alternate from assignment to assignment. Alternatively, maximum hooks of this kind will come with the next:
- A serve as that increments a specified a part of a model string (as an example,
1.2.3) and returns the brand new model. - The power to learn the present model from a devoted model record.
- A serve as to calculate the brand new model quantity, together with which particular section to increment. As an example,
0for main,1for minor,2for patch.
From right here, the script will have to replace the model record with the brand new quantity, create a light-weight tag with the brand new model, and optionally push the brand new tag to a far off repository. When you dedicate adjustments, the hook will be sure that each dedicate is related to an acceptable model and tag.
You are going to most likely need to make this hook suit your assignment’s necessities even additional. As an example, it is advisable maintain circumstances reminiscent of developing preliminary tags, coping with model conflicts, and updating model references in information.
Figuring out Hook Parameters and Surroundings Variables
One explanation why Git hooks are so robust is because of how they maintain dynamic variables. Alternatively, it is a advanced thought to grasp. Subsequent, we’ll take a look at each setting variables and hook parameters – beginning with the latter.
How Parameters Cross to Hooks
Hooks can get hold of particular parameters from Git to get entry to contextual data out of your primary codebase. Git units parameters on an automated foundation at run-time, and when you received’t particularly wish to outline them as a rule, you might wish to claim them. It’s very important to grasp those to increase efficient hooks.
Right here’s an outline of the important thing issues about hook parameters:
- Git hooks use positional variables, the place
$1refers back to the first parameter,$2to the second one parameter, and so forth. Those parameters don’t seem to be arbitrary; they’ve particular meanings and functions. As such, whilst they aren’t ‘legitimate,’ they constitute authorised conventions when gaining access to the values of parameters. - The order of the parameters follows a particular trend. Git passes those parameters in your hook script in a predetermined order according to the context of the hook tournament.
- The variable names replicate the overall objective of the parameters. As an example,
$1regularly comprises the trail to a record whilst$2may well be the supply of an motion.
In the event you have been so as to add a parameter that the hook can’t name, the script would most often no longer be capable of use it. Parameters are particular to a selected hook and execution context. To keep away from problems, you will have to best use documented parameters. Alternatively, you can assign the price of a positional parameter to any other variable after which use it on your script:
#!/bin/sh
# Assign $1 to the variable EXAMPLE
EXAMPLE=$1
# Use EXAMPLE variable
echo "The dedicate message record is: $EXAMPLE"On this case, the EXAMPLE variable may have the similar price as $1, which is the trail to the dedicate message record. Alternatively, the usage of the documented variable names makes your code extra comprehensible.
Observe that during some circumstances, you’ll use usual enter (stdin) to outline parameters, through which case you will have to paintings the ones components into your hooks.
Discovering Git Hook Parameter Values and Definitions
As a result of each and every Git hook may have its personal parameters, you are going to most likely want a reference to determine what they’re to your particular software. The excellent news is there are a couple of techniques to try this.
For instance, the legitimate Git hooks documentation comprises one of the most extra not unusual parameters. Alternatively, the most productive method is to open probably the most pattern Git hooks. Those encompass a mini-guide on how you can script the hook and can come with parameter definitions for you:
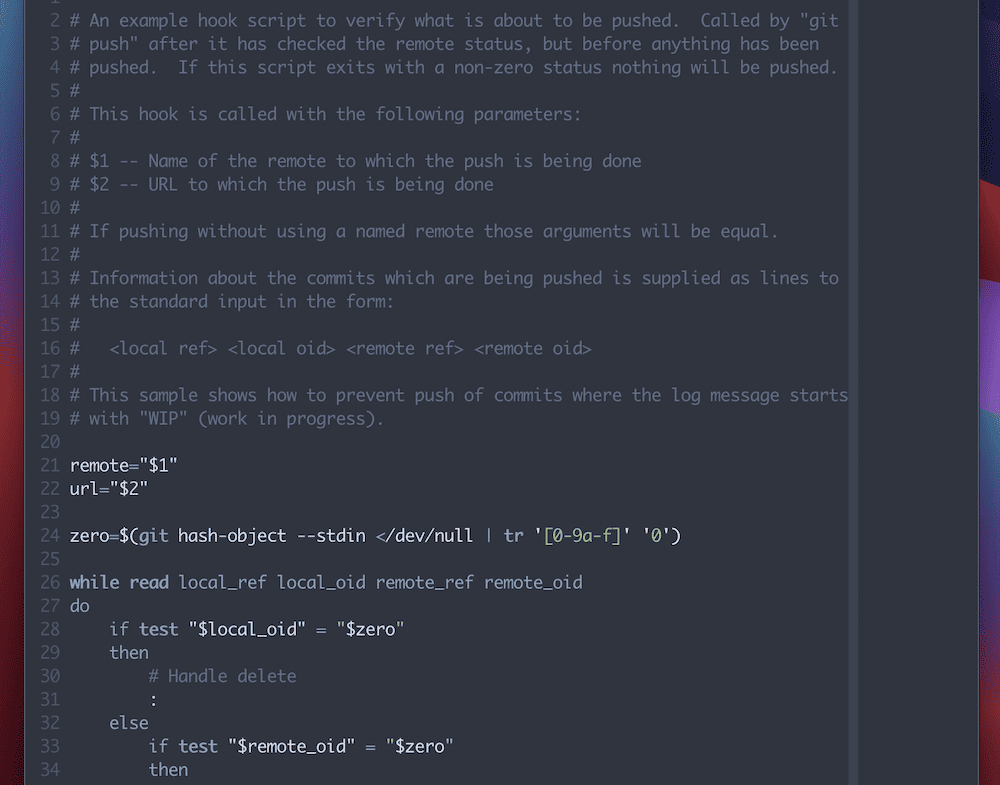
Those are a very good solution to familiarize yourself with Git hooks and may also get you some a part of the best way in the case of coding them.
Surroundings Variables
Git hooks can fetch arguments from command-line arguments, and stdin, as we talk about. Alternatively, they are able to additionally fetch arguments from the surroundings itself because it runs inside a bash shell.
Those setting variables will let you customise the habits of your Git hooks and make selections according to quite a lot of facets of the Git workflow. This manner, you’ll be able to create dynamic and context-aware Git hooks. For instance, you’ll be able to use them to validate dedicate messages, keep watch over get entry to to express branches, or cause customized movements according to the creator’s identification.
Record the entire setting variables is past the scope of this publish, too. We propose you take a look at the Git documentation and pattern hooks for hints on which variables it’ll use.
Checking out the Values of Surroundings Variables
Git usually units other setting variables robotically relying at the hook it calls. As such, this may motive issues for you in case you’re no longer conscious of what’s being set. As an example, take the next end result for the GIT_REFLOG_ACTION variable for the pre-rebase and post-merge hooks:
pre-rebase.GIT_REFLOG_ACTION=rebasepost-merge.GIT_REFLOG_ACTION=’pull different grasp’
Thankfully, there’s a solution to check out what Git will do with setting variables the usage of a small snippet inside your hook:
#!/bin/bash
echo Operating $BASH_SOURCE
set | egrep GIT
echo PWD is $PWDTo summarize the code, line two prints the script lately operating; line 3 units all setting variables to show, then filters them for the ones with “GIT” within the call; line 4 prints the present running listing.
When you run this, you’ll see output that corresponds with the surroundings variables related along with your hook. From right here, you are going to have the information to ensure your personal Git hooks can make the most of setting variables in the best way you’d like.
Pointers and Tips to Set up and Proportion Your Git Hooks
Managing Git hooks throughout a crew or group is a very powerful to verify constant construction practices and automate your workflows in an effective manner. As an example, take the easy act of assigning a devoted hooks listing. There are two items of recommendation we will be able to provide you with right here:
- Create a central repository or shared location the place you retailer standardized hooks. You’ll reuse the ones hooks throughout more than one tasks and clone or hyperlink to the repository to supply international get entry to.
- Arrange your hooks right into a registry or listing construction. This will likely make it simple to your crew to seek out and use the hooks they want.
The much more likely that hooks will function in more than one tasks, the higher the significance of documentation. You will have to handle complete documentation that outlines the aim, utilization, and configuration choices for each and every hook inside the repo. Code opinions and replace methods for those international hooks can also be very important.
We’d additionally counsel you retailer customized hooks within the Model Keep an eye on Device (VCS) together with your assignment’s codebase. This guarantees that all the crew has get entry to to all the library of hooks.
The use of Server-Facet Git Hooks
Server-side hooks will execute at the server that hosts the central Git repo. As such, you’ll be able to put into effect insurance policies, carry out assessments, or cause movements at the server aspect.
You may have two garage choices to your server-side hooks: inside the VCS along your assignment or in separate repositories.
Storing Server-Facet Hooks The use of a VCS
There are two benefits to the usage of your VCS to retailer server-side hooks. First, you’ll be able to ensure that the hooks have the similar versioning and upkeep as the remainder of your codebase. 2d, you’ll best wish to clone one repository to get entry to each the assignment code and the hooks.
Alternatively, relying at the nature of the particular hooks, storing them in the similar repo would possibly lift safety issues if the ones hooks get entry to delicate data. What’s extra, if the hooks are advanced or require particular configurations, it will build up the complexity of your primary repo.
Storing Server-Facet Hooks in Separate Repositories
Maintaining server-side hooks in separate repos allows you to replace and model them independently out of your codebase, which will cut back attainable conflicts. This modularity can be offering higher flexibility.
What’s extra, you’ll be able to retailer the ones hooks in repositories with limited get entry to. This will likely permit you to cut back the chance of delicate information publicity.
By contrast, keeping up more than one repositories would possibly require further effort. Additionally, if hooks depend on particular variations of your primary codebase, it may be a problem to coordinate adjustments between your repos.
Automating Hooks Installations
Automating hook installations throughout more than one repositories can save time and make sure consistency on your construction workflow. Through the usage of scripts and templates, you’ll be able to simply arrange hooks in quite a lot of repositories with out guide intervention.
The method starts with a devoted repository that comprises your international hooks. You’ll need to standardize those: as an example, keep away from hardcoding paths or values particular to a unmarried repo.
From right here, you’ll be able to start to write your set up script. For instance, the next pseudocode will clone a hook’s template repo and replica (or ‘symlink’) the hooks into the .git/hooks listing of each and every repository:
# Instance set up script
# Utilization: ./install_hooks.sh /trail/to/repository
TEMPLATE_REPO="https://github.com/yourusername/hooks-template.git"
REPO_PATH="$1"
REPO_NAME=$(basename "$REPO_PATH")
# Clone the template repository
git clone --depth 1 "$TEMPLATE_REPO" "$REPO_NAME-hooks"
# Reproduction or symlink hooks to the repository
cp -r "$REPO_NAME-hooks/hooks" "$REPO_PATH/.git/"
rm -rf "$REPO_NAME-hooks"
echo "Hooks put in in $REPO_NAME”When you save your adjustments, you’ll be able to run the set up script for each and every repo the place you need to put in the hooks:
./install_hooks.sh /trail/to/repository1
./install_hooks.sh /trail/to/repository2
# …Make adjustments within the template repository every time you want to replace or upload hooks. The following time you run the set up script in a repository, the up to date hooks will set up.
Git Templates
Git templates will let you outline not unusual hooks and configurations for brand spanking new repositories. They supply a scientific method that will help you automate setups, configurations, and different components while you create or clone new repositories. As such, you’ll be able to be sure that each repo adheres in your standard and established practices.
When you create a template listing and upload your hook scripts, you’ll be able to configure Git to make use of the listing because the template for brand spanking new repositories. You’ll set this up on an international or native foundation for each and every person.
For international configurations, level in your hooks template listing:
git config --global init.templateDir /trail/to/hooks-templateFor native configurations, you’ll be able to specify the precise repo:
git init --template=/trail/to/hooks-templateEvery time you create a brand new repository the usage of git init or clone an present repository, Git will robotically replica the contents of your hooks template listing to the .git listing within the new repo.
In any case, whilst template hooks may also be generic, you’ll be able to additionally permit for personalization hooks according to particular wishes. For instance, a script may take a look at for a repository-specific hook configuration record and use it if provide.
Conventional Practices to Assist You Handle Protected Git Hooks
The use of Git hooks may also be robust for procedure automation and implementing standard practices. Alternatively, this may include the prospective to introduce vulnerabilities in case you don’t arrange your hooks smartly sufficient.
Right here’s a handy guide a rough record of practices it is advisable enforce to your personal hooks:
- Be sure you assessment and limit permissions for hooks, particularly if they’re third-party examples.
- All the time validate and sanitize your enter parameters to mitigate code injections. Use protected practices, reminiscent of keeping off direct use of person enter on your scripts.
- Be sure that hooks don’t come with confidential data. That is the place setting variables or protected garage be offering immense price.
- Evaluation and check hooks frequently to forestall unintentional useful resource intake. This is able to even lead to Disbursed Denial of Provider (DDoS) assaults.
You are going to additionally need to enforce an intensive and complete check and assessment procedure. This will likely assist maintain down vulnerabilities and different mistakes one day.
Validation
We will have to communicate extra about imposing correct validation and error dealing with to your hooks. That is a very powerful to verify reliability, balance, and safety.
As an example, you must all the time validate any inputs or parameters your hook scripts get hold of. Alternatively, there’s a lot more you’ll be able to do to verify excellent validation. You want to be sure that the repository is within the anticipated state for the hook to run effectively. For instance, in a pre-commit hook, take a look at that you simply’re staging the important information prior to the dedicate.
Error dealing with can also be precious. Go out codes are simply as a very powerful in hooks as they’re on your codebase, as are error logs and informative error messages. ‘Sleek failure’ will have to be your function right here, as it could be with better codebases.
After all, in a real-world state of affairs, your hooks would possibly want extra advanced validation and error-handling common sense. This implies common checking out is much more necessary than prior to.
Unintentional Harmful Movements
Injuries occur, so putting in place your Git hooks to forestall those undesirable harmful movements is a very powerful to safeguard from information loss or injury. Hooks can necessarily act as protection nets thru person prompting for doubtlessly destructive movements.
Pre-receive and pre-commit hooks paintings smartly right here. Let’s temporarily cross over how either one of those can assist:
- Pre-receive hooks assist for server-side assessments. This will likely cause prior to accepting new branches or tags from the customer. Your script will have to read about incoming references, take a look at for movements reminiscent of pressure pushes or department deletions, and instructed the person for affirmation. You’ll additionally need to analyze the driven references to decide whether or not they contain movements reminiscent of pressure pushing (
--force) or department deletion. - Pre-commit hooks paintings at the client-side and run prior to you finalize a dedicate. Whilst it received’t at once save you harmful movements at the server, it can assist save you native errors prior to pushing. Your script will have to analyze the staged adjustments and search for components reminiscent of
pressure pushinstructions in dedicate messages. From there, show a caution or error message for the person.
Alternatively, irrespective of the practices you enforce, they need to be protected, environment friendly, and optimum to your wishes. This will likely require an intensive assessment and checking out technique.
Reviewing and Checking out Git Hooks
Reviewing and checking out hooks is very important to verify they serve as accurately and align along with your construction workflow. Peer opinions, transparent documentation, an abundance of feedback, and extra can help in making certain hooks are able for manufacturing.
In terms of checking out, it’s necessary to take action in isolation the usage of various pattern information. You may also enforce computerized regression or integration checking out.
In any case, we’d advise you to check out hooks in numerous environments (reminiscent of your construction, staging, and manufacturing servers) to verify they offer constant habits. An actual-time logging setup will assist right here, as it will possibly show off what occurs as information strikes from server to server.
How To Troubleshoot Your Hooks
As with all codebase, you will have to troubleshoot your hooks, too – even throughout a couple of makes an attempt. If truth be told, it doesn’t matter what your Git hook sort is, you’ll in finding that the similar mistakes crop up over and once more. Many of those might be easy problems that impact all kinds of tasks, reminiscent of syntax mistakes, permissions problems, the usage of relative or hardcoded paths, and a lot more.
Alternatively, it’s additionally a good suggestion to test for lacking dependencies, as some hooks depend on exterior gear, information, or libraries. As such, you must lead them to to be had within the setting the place you execute the hook.
There are certain problems that may crop up with Git hooks, even though. For instance, hooks will have to go out with a non-zero standing code to suggest a failure. What’s extra, hooks shouldn’t include limitless loops. With out either one of those in position, you’ll be able to motive surprising habits and disrupt your workflow.
You might also in finding that conflicts between two hooks provide you with unintentional interactions and penalties. So-called ‘race stipulations’ can bog down your expectancies, too. That is the place two or extra hooks cause thru an identical occasions, however one completes prior to the opposite – it’ll have an have an effect on at the ultimate end result you are expecting.
That is the place opinions and assessments grow to be important. Keeping up documentation may be necessary to keep away from problems and make sure hooks serve as as you’d be expecting.
Talking of documentation, Git’s personal reference subject material is very important studying. If truth be told, together with this text and possibly the impartial Git Hooks instruction manual website online (the usage of GitHub Pages), you shouldn’t want an excessive amount of studying subject material.
Alternatively, you might need to take a look at apps that will help you arrange Git hooks, too. Lefthook has common updates and quite a lot of improve on GitHub, whilst Husky is excellent for linting your dedicate messages.
The Advantages of Integrating Hooks Into Steady Integration (CI/CD) Pipelines
CI/CD pipelines paintings smartly with Git hooks, as the ones scripts will let you automate duties, ensure that constant high quality, and supply safety assessments.
As an example, pre-commit hooks will let you run code high quality assessments, reminiscent of linting, static research, and formatting. In terms of checking out, you’ll be able to cause unit assessments, check suites, or different computerized assessments on the pre-commit level. Alternatively, pre-push hooks will let you run integration checking out, safety scanning, and extra.
There are many advantages you’ll be able to leverage from the usage of hooks inside your CI/CD pipelines:
- Consistency. Hooks will let you put into effect constant practices throughout all commits and deployments, which is able to cut back mistakes around the board.
- Computerized assessments. You’ll automate code high quality assessments, checking out, safety scanning, and different necessary duties. This will likely cut back guide effort and go away you with extra time to devote somewhere else.
- Early factor detection. Hooks will will let you catch problems early within the construction procedure, which prevents them from propagating thru your pipeline.
- Lowered deployment dangers. With computerized assessments and checking out caused via hooks, the chance of deploying inaccurate code may also be considerably lowered.
As a result of Kinsta’s API allows you to arrange CI/CD pipelines, you’ll be able to additionally combine Git hooks right here too. Kinsta allows you to pull all your repo down from a far off location and lets in for pushes the usage of a third-party plugin reminiscent of WP Pusher.
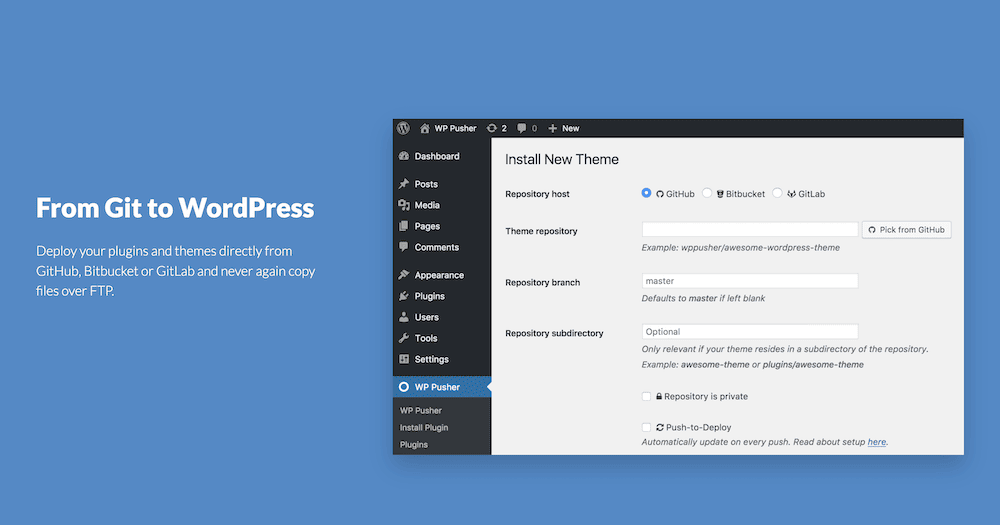
After all, this additionally approach you’ve gotten the method to make the most of Git hooks too. As such, your Kinsta set up can leverage those robust scripts inside your repo.
Abstract
Git is an very important instrument for any construction assignment, however one facet of it, particularly, may hypercharge your coding and deployment workflow. Git hooks will let you create scripts the usage of plenty of languages to automate quite a lot of facets of your model keep watch over procedure. It’s a easy thought with a quite advanced underbelly.
Our publish displays you how you can use complex ways to make use of Git hooks to their fullest. You’re ready to make use of them each in the neighborhood and server-side, lead them to dynamic the usage of parameters and variables, paintings with more than one far off repos, and extra. If truth be told, we propose that at this level, Git hooks would possibly grow to be your secret weapon to spice up productiveness, code high quality, and assignment turnaround time.
Do you’ve gotten any questions relating to Git hooks and how you can use them? Tell us within the feedback segment beneath!
The publish Mastering Git Hooks: Complicated Ways and Perfect Practices gave the impression first on Kinsta®.
WP Hosting