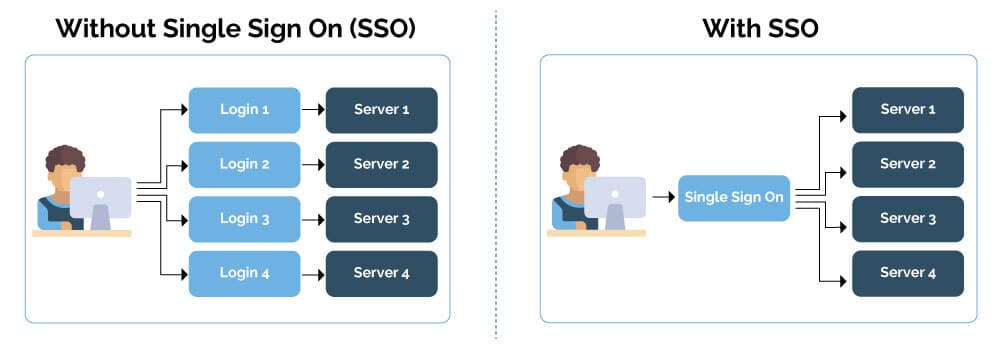
Organizations depend on numerous on-line apps and services and products day-to-day, every of which calls for other logins, making password control a rising problem.
Your group can make the most of a CRM, an intranet, a piece chat, and different third-party services and products, corresponding to your internet hosting supplier’s dashboard, each day. If this sounds acquainted, you most probably desire a centralized authentication machine that permits your group participants to make use of the similar login credentials throughout a large number of web pages and platforms.
That is the place Unmarried Signal-On (SSO) is available in, as an answer designed to streamline authentication, give a boost to safety, and enhance the potency of your group’s workflows. For on-line companies, SSO is greater than only a nice-to-have function. This can be a tough device that mean you can toughen your company’s safety and enhance trade processes.
SSO integration with the MyKinsta dashboard the usage of Safety Statement Markup Language (SAML) is designed particularly for this goal: it centralizes get right of entry to regulate with main Id Suppliers, automates the onboarding procedure by the use of JIT provisioning, and strengthens the protection of your internet hosting account and your shoppers’ information.
This newsletter explores SAML SSO in its key facets. You’re going to be informed what it’s and why it’s non-negotiable for adopting a zero-trust coverage in your small business.
There’s a lot to hide, so let’s get began!
What SAML SSO is and the way it works
SAML SSO is an authentication scheme that allows a consumer to safely log in to a couple of impartial packages or device services and products the usage of a unmarried set of credentials. Customers don’t wish to retailer or arrange a couple of passwords for various services and products; they simply wish to log in to certainly one of them to get right of entry to the others securely.
An SSO machine has two key actors: the provider supplier and the id supplier.
- The provider supplier (SP) is the appliance, internet provider, or useful resource an end-user desires to get right of entry to. It can be an intranet, a CRM, or a third-party provider.
- The id supplier (IdP) is a provider or machine that creates, maintains, and manages id data and offers authentication services and products to third-party services and products.
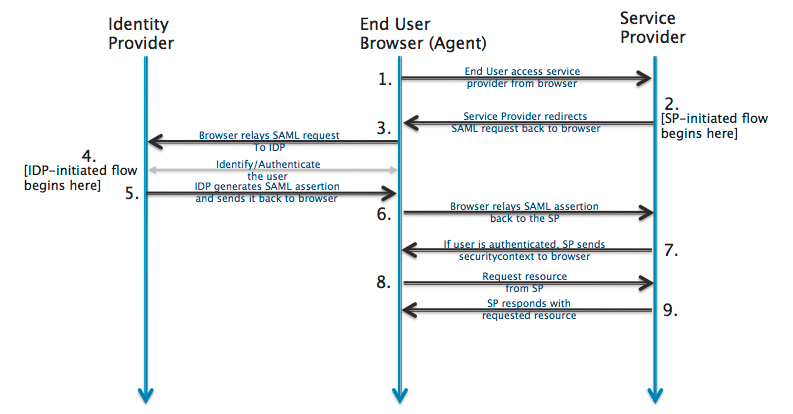
Right here’s the way it works:
- A consumer makes an attempt to log in to an utility, corresponding to a WordPress website online or your internet hosting supplier’s dashboard.
- If the appliance (the SP) detects that the consumer isn’t authenticated, it redirects the consumer to the Id Supplier.
- The IdP then activates the consumer to log in with their credentials.
- The IdP verifies the consumer credentials. If they’re proper, the IdP authenticates the consumer and generates a safety token.
- The IdP sends the protection token to the SP.
- The SP receives the token, validates it, and grants the consumer get right of entry to.
Listed below are some well-liked IdPs:
- Microsoft Entra ID: Microsoft’s cloud-based id and get right of entry to control provider. Designed for seamless integration with Microsoft 365 and Azure services and products, it may be built-in with hundreds of SaaS packages. It helps SAML, OAuth 2.0, and OpenID Attach protocols, in addition to a variety of authentication strategies.
- Google Id Platform: A scalable and safe id and get right of entry to control answer in accordance with Google’s world infrastructure. It helps industry-standard authentication protocols, corresponding to SAML, OAuth 2.0, and OpenID Attach.
- Okta: An enterprise-grade id control provider. Okta helps the commonest authentication protocols, corresponding to Kerberos, LDAP, OAuth 2.0, RADIUS, and SAML.
- Auth0: Now a part of Okta, Auth0 is an id and get right of entry to control platform with nice flexibility and customization choices for builders to construct customized packages. It helps industry-standard protocols, together with OpenID Attach, SAML, OAuth 2.0, WS-Federation, LDAP, and extra.
- Keycloak: An open-source Id and Get right of entry to Control (IAM) answer advanced via Crimson Hat and launched underneath Apache License 2.0. It’s in accordance with traditional protocols and helps OpenID Attach, OAuth 2.0, and SAML.
SAML SSO vs social login
SAML SSO is steadily puzzled with social login, however there are key variations between the 2. Social login is a particular implementation of unmarried sign-on, nevertheless it has vital variations and particular use instances.
Very similar to Kinsta SAML SSO, social login permits customers to get right of entry to a couple of services and products with a unmarried id controlled via an id supplier. With social login, the id supplier (IdP) is a social community, corresponding to Fb, Google, or GitHub.
The 2 authentication techniques are identical in that they each use not unusual protocols, corresponding to OAuth 2.0 and OpenID Attach, to allow authentication thru a unmarried provider supplier. In each eventualities, the authentication enjoy and the management of get right of entry to credentials are significantly enhanced, as are machine safety and the productiveness of the IT group.
Alternatively, there are vital variations between the 2 techniques.
B2B vs B2C: SSO is an authentication and id control machine designed essentially for companies. Social login is one of those SSO aimed at customers and utilized in third-party packages or web pages.
Public platforms vs inside or devoted IdPs: The kind of IdP could also be other. For social login, the IdP is a social community or public platform. For venture SSO, the id supplier will also be an inside machine or a devoted IdP, corresponding to Okta, Auth0, or Microsoft Entra ID.
Accessibility and regulate: Social login IdPs are client platforms obtainable to any person with an account and don’t require advanced configuration via a talented IT group.
Conversely, SSO comes to machine configuration and id control, which fall inside of a company’s accountability. The group determines what information to percentage, which protocols to make use of, and which safety insurance policies to undertake (like two-factor authentication).
Information sharing: With social login, provider suppliers can percentage consumer information in accordance with the permissions granted.
Alternatively, conventional SSO best stocks the information important for authentication and authorization with out exposing private data.
Why SSO is very important for contemporary organizations
SSO is a key component in lately’s virtual ecosystem. It complements safety, improves the consumer enjoy, and streamlines consumer control.
Cast safety
SSO centralizes id control in a safe and specialised machine: the IdP. To place it merely, because of SSO, your web page now not wishes to control the authentication procedure at once as a result of this accountability is delegated to the IdP. This reduces the dangers related to the fallacious control of login data and accounts. Let’s take a better glance.
Susceptible passwords: With SSO, you now not wish to create and retailer a number of safe passwords. The one set of credentials you want is from the IdP, which in most cases has transparent and strict password insurance policies, which makes issues a lot more safe.
Credential stuffing: Some of the not unusual password control errors is the usage of the similar password throughout other on-line services and products. This will building up a machine’s general vulnerability as a result of, if one web page is hacked, the similar aggregate of credentials can be utilized to get right of entry to different websites. These kinds of assaults are referred to as credential stuffing.
Due to SSO, customers don’t wish to reuse the similar credentials to get right of entry to a couple of internet services and products. When a consumer logs in to a internet provider by the use of SSO, that provider does no longer obtain or retailer the consumer’s password. Due to this fact, a conceivable assault would no longer divulge your customers’ login credentials. This reduces the assault floor dramatically, getting rid of the danger of password robbery.
What occurs if the IdP is compromised? Because the IdP is the one de-provisioning level, it is usually the one regulate level for disabling hacked accounts. Once a breach is detected, the administrator can disable the account, combating all hooked up packages (SPs) from being breached.
Robbery of credentials from insecure techniques: Web sites with vulnerable security features can retailer passwords in an unencrypted or simply reversible structure.
With SSO, you might be delegating the accountability of managing and storing your credentials to the IdP, which makes a speciality of safe garage and employs {industry} perfect practices for credential coverage.
Phishing and machine-in-the-middle assaults: A phishing assault is an try to thieve delicate data, corresponding to usernames, passwords, bank card numbers, or financial institution main points, to be used or sale with malicious intent. A identical situation happens with a machine-in-the-middle assault, the place an attacker inserts themselves into the conversation channel between two gadgets.
Generally, IdPs be offering complicated safety features, corresponding to multi-factor authentication (MFA) and fraud detection. Because of this even supposing a consumer supplies their credentials to a malicious actor, a 2d authentication component blocks get right of entry to. Moreover, safe protocols like SAML and OIDC give protection to communications between customers, provider suppliers, and id suppliers.
Inefficient onboarding and de-provisioning: When a consumer leaves the group, some accounts would possibly stay unnecessarily lively. This will create vulnerable spots within the machine’s safety.
With SSO, the de-provisioning procedure is centralized. Disabling the consumer within the IdP blocks their get right of entry to to all hooked up services and products.
Advanced consumer enjoy
With SAML SSO, a unmarried login mechanically authenticates customers throughout all services and products, granting them get right of entry to to all of the assets inside the ecosystem.
This additionally boosts group member productiveness. Customers can briefly transfer between packages with out interruption, getting rid of the time it takes to go into or retrieve passwords. Fewer logins additionally imply fewer authentication mistakes, fewer password resets, and no more paintings for IT departments.
For on-line trade homeowners, SSO isn’t just a pleasant function to have; it’s a strategic device that at once affects trade safety and consumer enjoy.
Higher productiveness and lowered running prices
SAML SSO supplies substantial advantages in relation to operational potency and long-term trade sustainability:
Lowered load on IT departments: Some of the not unusual pitfalls of credential control is customers forgetting their passwords or making a couple of login makes an attempt with fallacious credentials. This steadily ends up in fortify requests to IT places of work for password resets. Those requests constitute a price in relation to time and assets.
Via imposing SSO, customers best wish to arrange one password. Consequently, there are fewer fortify requests, and the IT group can center of attention on strategic actions, corresponding to technological innovation and infrastructure safety.
Simplified consumer control: In huge, advanced organizations, consumer control is a in particular burdensome process. Believe an organization that makes use of dozens of various packages. With out SSO, each time a brand new group member joins the group, they will have to create a brand new account for every utility in use.
When an worker leaves, you will have to delete their account from all the ones services and products. This procedure is bulky, and inadvertently leaving an lively consumer account on a provider can create safety gaps. With SSO, there is not any wish to fear about this. Simply create one account, and the consumer can straight away get right of entry to all services and products.
De-provisioning could also be speedy and safe since you best wish to delete one account to disconnect the consumer from all services and products within the group.
Streamlined provider integration: Person control is crucial and sophisticated facet of utility building. On every occasion you introduce a brand new provider into your company, you will have to broaden a brand new machine for authenticating and managing consumer accounts.
With id control protocols corresponding to SAML and OpenID Attach, integrating SSO into your machine is reasonably simple as a result of your utility does no longer need to care for id control, permitting your IT division to concentrate on the strategic options of your core trade.
Centralized get right of entry to regulate: With many services and products in use, controlling who has get right of entry to to every of those services and products is a difficult process for IT directors.
SAML SSO solves this drawback via offering a unmarried level of get right of entry to to all services and products. From a unmarried central level, admins can track consumer get right of entry to and job, in addition to locate safety holes, all from a unmarried dashboard. The result’s an greater capability to regulate get right of entry to and a quicker reaction time in case of incidents.
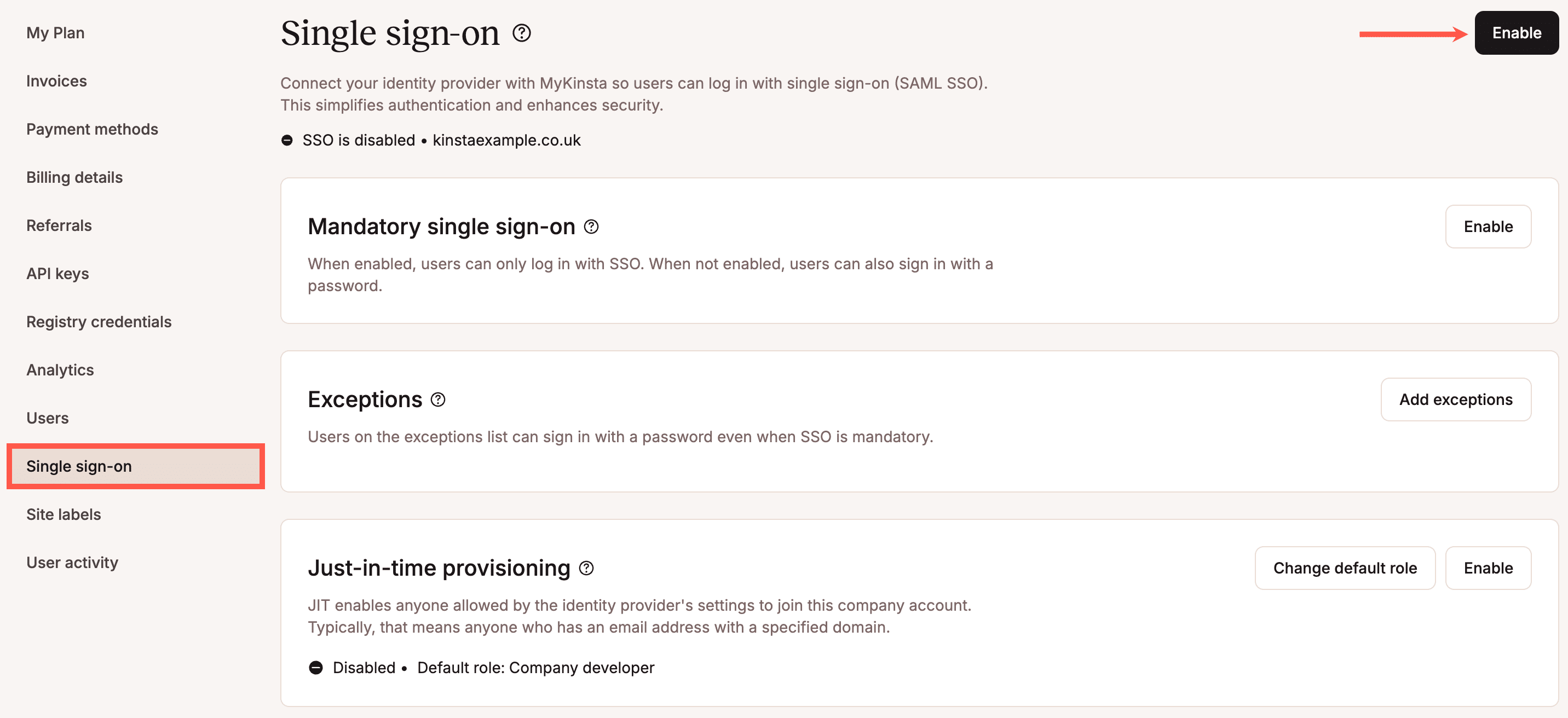
Kinsta SAML SSO authentication
MyKinsta helps the XML-based SAML protocol to allow the safe trade of authentication and authorization information between an IdP and an SP.
Because of this Kinsta’s shopper companies can upload unmarried sign-on capability and safety to their internet hosting dashboard.
The usage of SSO with MyKinsta is perfect for companies with rising groups, because it gets rid of the effort of handbook get right of entry to control and streamlines all of the onboarding, consumer control, and offboarding procedure.
Centralized id control and granular get right of entry to regulate
Via enabling Kinsta SAML SSO, companies can mix centralized id control with the MyKinsta multi-user dashboard.
The IdP acts as unmarried supply of reality. Right here, companies make a decision which group participants can get right of entry to their Corporate account in MyKinsta.
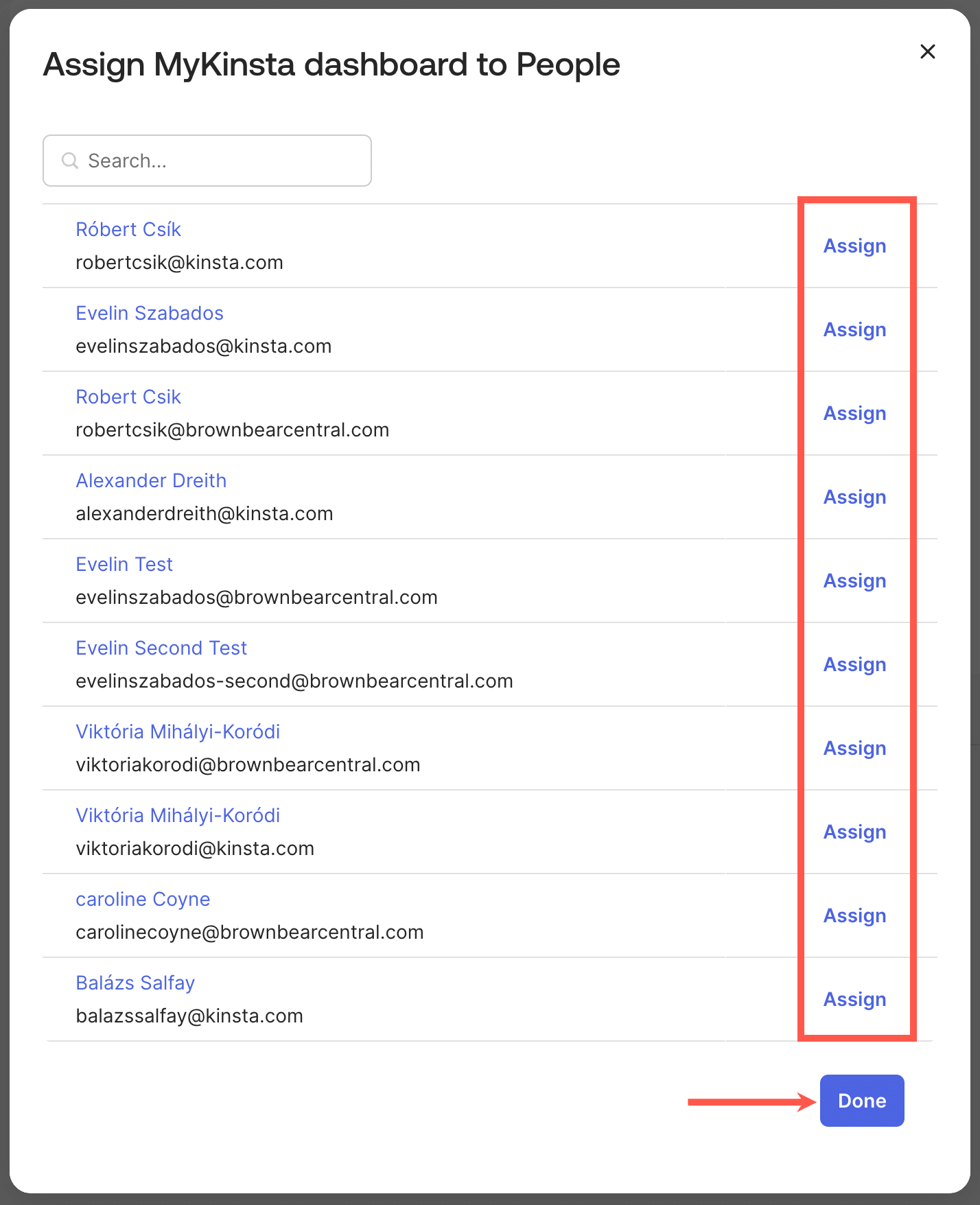
MyKinsta is your heart for granular consumer regulate. When customers log in to MyKinsta, they’re assigned a default position. This will also be changed later via the Corporate proprietor or directors.
Enabling Kinsta SAML SSO complements safety via protective your company account with the IdP’s safety insurance policies, together with multi-factor authentication and stringent password necessities. Moreover, Corporate account customers now not wish to use their login credentials, which minimizes the danger of credential robbery.
Simply-in-time provisioning with Kinsta SAML SSO
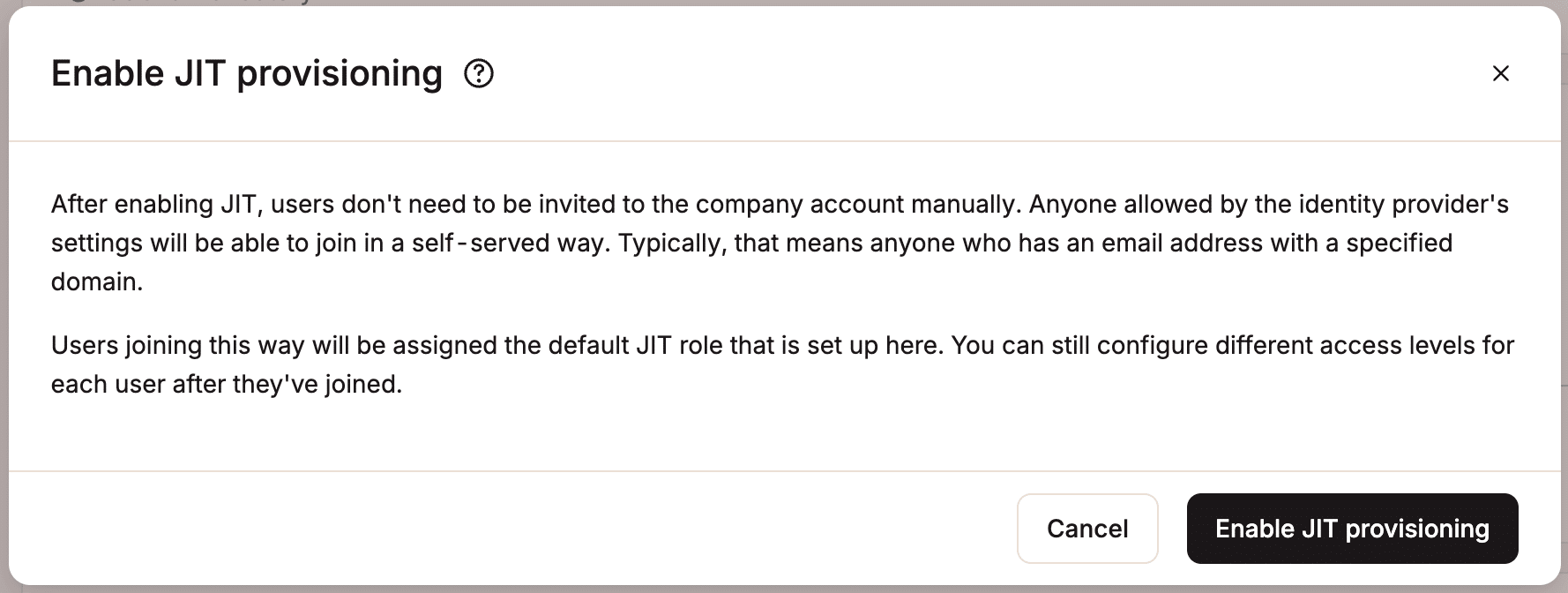
MyKinsta helps just-in-time (JIT) provisioning, which lets you mechanically create a brand new MyKinsta consumer account when a consumer logs in for the primary time by the use of SAML SSO.
When JIT provisioning is enabled, licensed customers on the IdP can at once get right of entry to MyKinsta with no need a handbook invitation or a separate consumer account. This implies licensed customers best want an e mail deal with together with your corporate’s area to get right of entry to your MyKinsta account.
Via default, group participants who get right of entry to MyKinsta by the use of JIT provisioning are assigned the Corporate Developer position. Corporate homeowners and directors can alternate a consumer’s position when they sign up for or adjust the default position for brand spanking new JIT-provisioned customers earlier than the consumer joins.
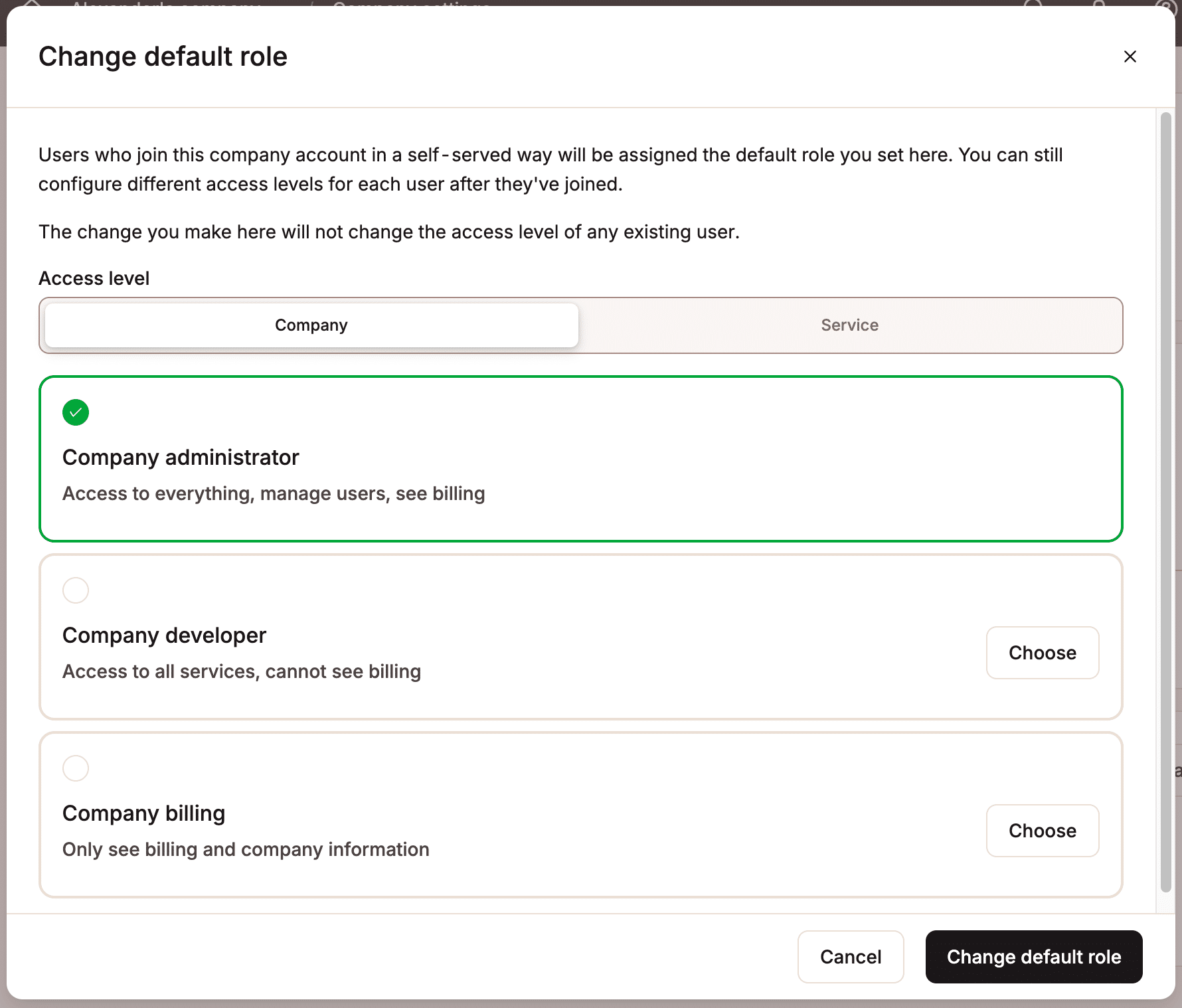
Via automating the onboarding procedure, companies and different organizations can considerably scale back the effort and time enthusiastic about onboarding and consumer control processes. This allows them to briefly reply to buyer requests via scaling their group with minimum effort.
Efficient deprovisioning
For a corporation that adopts a zero-trust philosophy, it is very important to briefly and securely revoke get right of entry to for customers who depart the group. Efficient deprovisioning could also be crucial to make sure compliance with information safety and privateness rules.
When a consumer leaves the group, the group administrator will have to delete the consumer’s account from the id supplier. Alternatively, when JIT provisioning is enabled, revoking a consumer’s get right of entry to on the IdP isn’t sufficient, and also you will have to take away them from each the IdP and MyKinsta. Merely taking out them from the IdP won’t paintings, as they’re going to nonetheless have the ability to get right of entry to your corporate account with their MyKinsta credentials.
Regulatory compliance
To be able to conform to safety rules and procure certifications corresponding to SOC2 and ISO 27001, organizations will have to reveal that they’ve strict get right of entry to regulate measures in position. Adopting Kinsta SAML SSO guarantees compliance with those necessities as it promises that safety insurance policies are implemented persistently throughout all hooked up services and products.
Kinsta SAML SSO could also be suitable with rules such because the GDPR, because it tracks get right of entry to to non-public information and guarantees the glory of the rules of information minimization and well timed revocation of get right of entry to thru speedy deprovisioning.
Abstract
Kinsta’s SAML SSO authentication function enhances the multi-user functions of the MyKinsta dashboard. Businesses can streamline their workflows via combining granular consumer control for the corporate account with SSO id and get right of entry to control, automating a lot of the onboarding procedure and adorning account safety.
Account directors can assign predefined roles to provisioned customers, make exceptions to the IdP provisioning procedure, and block get right of entry to to express customers. For companies with dozens of builders and group participants in numerous roles, Kinsta SAML SSO is very important for reinforcing safety, flexibility, and operational potency.
Curious to take a look at our top rate controlled WordPress internet hosting? Check out Kinsta at no cost lately!
The put up Kinsta SAML SSO is right here: Scale your company quicker and extra securely seemed first on Kinsta®.
WP Hosting