SSL (Protected Socket Layer) encrypts information transactions between a browser and server, improving the safety of your web page. Whilst the usage of HTTP for localhost is typically sufficient for construction, infrequently you want to check it in HTTPS. For instance, it’s possible you’ll want to take a look at a carrier employee, set safe cookies which want the website to load over HTTPS, or take a look at third-party API that most often calls for HTTPS equivalent to an Auth or Cost form of APIs.
Checking out your website with SSL throughout construction guarantees all components, together with URLs and sources like CSS and JavaScript, serve as correctly beneath HTTPS. This is helping reflect the manufacturing atmosphere extra as it should be, serving to in smoother transitions when going reside.
On this article, we’ll information you throughout the strategy of enabling HTTPS in your localhost, making sure you’re ready for any safe trying out wishes.
In a position to get began? Let’s cross!
Contents
Getting Began with mkcert
mkcert simplifies the method of putting in SSL certificate for localhost. In contrast to the normal strategies which might be incessantly advanced, mkcert gives an easy means. It units up a in the neighborhood relied on construction certificates by means of mechanically putting in and trusting an area Certificates Authority (CA) in your device. This instrument is appropriate with macOS, Linux, and Home windows, masking quite a lot of construction environments.
In the event you’re on macOS or Linux, you’ll first want to set up Homebrew. Home windows customers must set up Chocolatey. With those equipment in position, you’ll simply set up mkcert by means of operating the next instructions:
// For macOS or Linux brew set up mkcert && brew set up nss # "nss" is wanted for Firefox fortify // For Home windows choco set up mkcert
Putting in SSL Certs
Start by means of executing the command beneath to create a Certificates Authority (CA) that can signal your certificate:
mkcert -install
It’s necessary to stay the rootCA-key.pem document safe and not percentage it. If compromised, an attacker may just probably intercept your safe connections to any website. Please care for this document with warning!
Following the advent of the CA, generate a certificates for the localhost hostname the usage of this command:
mkcert localhost
This instrument could also be flexible sufficient to provide certificate for different hostnames and even native IP addresses, equivalent to 127.0.0.1.
As an example:
mkcert hongkiat.native www.hongkiat.native 127.0.0.1
Operating an HTTP Server
Together with your SSL certificate able, you’ll now release your native server the usage of HTTPS. For the ones using Node.js, the http-server bundle gives an easy option to get started a server. You wish to have to specify the trails for your certificates and key recordsdata.
As an example, right here’s methods to run a localhost server on port 8080:
http-server -S -C localhost.pem -Okay localhost-key.pem -p 8080
As soon as operating, your localhost may also be accessed by the use of HTTPS at https://localhost:8080.
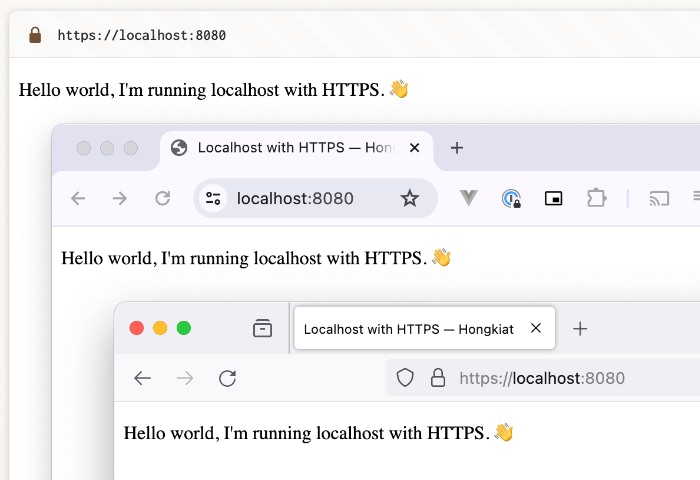

Operating with Docker and Nginx
If Docker and Nginx are a part of your setup, the next server configuration permits you to run HTTPS:
server {
concentrate 443 ssl;
server_name localhost;
ssl_certificate /trail/to/localhost.pem;
ssl_certificate_key /trail/to/localhost-key.pem;
location / {
root /var/www/html;
}
}
Hyperlink the vital certificate and configuration recordsdata for your Docker container via a Docker Compose configuration document, as proven beneath:
products and services:
nginx:
symbol: nginx:newest
ports:
- "8081:443"
volumes:
- ./localhost-key.pem:/and so on/nginx/certs/localhost-key.pem
- ./localhost.pem:/and so on/nginx/certs/localhost.pem
- ./nginx.conf:/and so on/nginx/conf.d/default.conf
- ./index.html:/var/www/html/index.html
Uninstall mkcert
If making a decision to forestall the usage of HTTPS for native construction or in the event you’re switching to some other manner for dealing with SSL certificate, you could wish to uninstall mkcert.
To take away mkcert out of your device, execute the next command:
mkcert -uninstall
This command deletes the basis CA from each your device and browser. You must additionally take away the basis certificates document and any certificate pairs you’ve generated:
rm -r "$(mkcert -CAROOT)"
Conclusion
Enforcing HTTPS in your native server is an important for correctly trying out options equivalent to carrier employees, safe cookies, and third-party APIs that require a safe connection. mkcert supplies an effective option to generate and set up SSL certificate throughout more than a few platforms and browsers, streamlining the method for builders.
The submit How you can Run Localhost with HTTPS seemed first on Hongkiat.
WordPress Website Development Source: https://www.hongkiat.com/blog/run-localhost-https/