The web has developed from a trifling repository of data to a posh social and trade platform. Whilst this technological development has made lifestyles more straightforward, it has additionally compromised our privateness.
As you navigate the internet, more than a few entities gather your own information, comparable to advertisers, entrepreneurs, and analytics amenities, to higher perceive your personal tastes.
For instance the type of private data in peril, believe this: You’ve almost certainly observed advertisements that say, “Chat with Alice. Sign up for our community and connect to folks in New York” (or your present location). Ever puzzled how they knew the place you have been?
.no-js #ref-block-post-57444 .ref-block__thumbnail { background-image: url(“https://property.hongkiat.com/uploads/thumbs/250×160/best-vpn-services-review.jpg”); }
Contents
10 Absolute best VPN Provider Suppliers for 2023
The whole lot is being tracked in this day and age, out of your actions on the net for your telephone and pc. Every click on,… Learn extra
How Your Knowledge Is Accumulated and Used
Firms accumulate data like your browser kind, platform, IP deal with, seek historical past, surfing habits, or even your geographical location. They use this information to create detailed profiles and leverage it for his or her receive advantages.


Additionally, the web is rife with different dangers comparable to viruses, malware, and unsolicited mail, which will compromise your device. There also are people who interact in unauthorized get right of entry to to thieve your information. Safeguarding your on-line identification has develop into a trade in itself.
Protective Non-public Knowledge with VPN
Whilst there are more than a few security features like antivirus tool and firewalls to offer protection to your device, those answers fall quick with regards to holding your own information on-line.
Internet browsers be offering options like Personal Surfing mode (Incognito for Chrome customers) and Do No longer Observe, however those have obstacles. A VPN serves as a powerful method to such privateness issues, successfully safeguarding your delicate data.
What’s a Digital Personal Community (VPN)?
A Digital Personal Community, or VPN, establishes an encrypted ‘tunnel’ between your pc and the VPN server. This safe tunnel guarantees that your information is secure when transmitted over the general public web, safeguarding it from unauthorized customers and information breaches. Whilst the underlying era of VPNs might appear advanced, it necessarily serves to forestall unauthorized get right of entry to for your information and conceals your IP deal with to offer protection to your on-line identification.
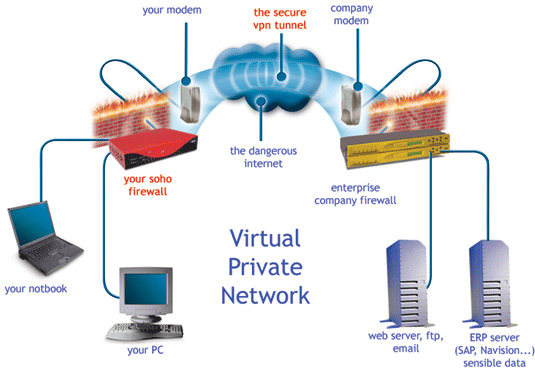

Connecting to a VPN is as easy as logging into your electronic mail account. While you acquire a VPN package deal, the supplier will provide you with a username and password, or in some instances, authentication recordsdata or certificate. You’ll then arrange a VPN connection for your working device, following the information supplied via the seller, and log in the use of your credentials.
On the other hand, chances are you’ll use a VPN shopper tool, if supplied via the seller, to simplify the relationship procedure after you’ve authenticated your self.
Figuring out VPN Safety Ranges
VPNs be offering a number of protocols, every with its personal point of safety and straightforwardness of use. Bring to mind it like commuting to paintings: some folks take the educate, whilst others pressure. In a similar way, VPNs have other strategies – referred to as protocols – for organising safe tunnels.
Those protocols range in relation to platform compatibility, price, and different options. If you’ve made up our minds to make use of a VPN, you’ll want to make a choice the particular VPN era (protocol) that most nearly fits your wishes.
1. PPTP
Level-to-Level Tunneling Protocol (PPTP) is probably the most often used protocol. It gives moderately vulnerable 128-bit encryption however is quicker because of decrease encryption overhead. PPTP is appropriate with quite a lot of platforms, together with Home windows, Mac OS X, iOS, Android, Linux, and DD-WRT routers, and doesn’t require any further tool.

PPTP is user-friendly, simply deployable, and works neatly with Devoted IPs. It’s usually probably the most reasonably priced protocol and is appropriate for customers who prioritize ease of use over high-level safety.
Causes to Select PPTP: Large platform fortify, user-friendly, and superb cellular instrument compatibility.
Causes to Keep away from PPTP: Decrease encryption ranges lead to diminished safety, loss of fortify for change VPN ports, and more straightforward to stumble on and block.
2. L2TP/IPSec
Layer Two Tunneling Protocol (L2TP) makes use of Web Protocol Safety (IPSec) for information encryption. It gives excessive 128-bit or 256-bit encryption and is appropriate with Home windows, macOS, Linux, iOS, and Android.

L2TP/IPSec calls for no further tool and is appropriate with Devoted IPs. It gives higher safety than PPTP and is perfect for the ones in quest of upper safety ranges.
Causes to Select L2TP/IPSec: Top safety, higher than PPTP.
Causes to Keep away from L2TP/IPSec: No fortify for change VPN ports.
3. OpenVPN
OpenVPN is probably the most safe VPN protocol and is efficacious even in puts like faculties and places of work the place different protocols are blocked. It gives powerful 256-bit encryption and is usually the most costly protocol possibility.

OpenVPN calls for its shopper tool to be put in in your device. It’s appropriate with Devoted IPs and operates on a couple of ports, making it tough to stumble on and block. It’s your best option for complicated customers in quest of excessive ranges of anonymity and safety.
Causes to Select OpenVPN: Top safety, works the place different protocols are blocked, fortify for change VPN ports.
Causes to Keep away from OpenVPN: Calls for tool set up, is also difficult to arrange on iOS and Android in some instances.
Conclusion
VPNs function an efficient instrument for protecting your delicate information from unauthorized get right of entry to. By means of encrypting your information, you succeed in the next point of anonymity and safety, giving your data the security it merits.
For extra insights, take a look at our different security-related articles.
The publish Figuring out VPN Protocols: The best way to Safeguard Your Non-public Knowledge On-line seemed first on Hongkiat.
WordPress Website Development Source: https://www.hongkiat.com/blog/vpn-protocols/