Your computer is not only a tool; it’s a vault stuffed with essential recordsdata, delicate data, and private knowledge. The mere thought of it being stolen is distressing. Whilst backing up very important recordsdata to cloud garage and on-line backup products and services is conceivable, the lack of the bodily tool provided with units monitoring remains to be a vital blow. Additionally, the information left on a stolen computer can also be misused.
Being ready for such unlucky situations is smart. On this article, we display you fice of the most efficient apps available in the market designed to allow you to get better your stolen computer. Take into accout, those apps are best when put in prematurely, slightly than after the robbery has already came about.
.no-js #ref-block-post-16314 .ref-block__thumbnail { background-image: url(“https://property.hongkiat.com/uploads/thumbs/250×160/track-lost-stolen-android-devices.jpg”); }
Contents
8 Apps to Observe Misplaced Android Telephones
Shedding a telephone could be a irritating and aggravating revel in, particularly if it incorporates delicate knowledge or non-public… Learn extra
Review:
| App Identify | Primary Options | Is it Unfastened? | Paid Plans (Beginning Worth) | Compatibility |
|---|---|---|---|---|
| Prey | Complete tool monitoring (GPS, WiFi, GeoIP), Sensible Monitoring, Regulate Zones (Geofencing), Location Historical past, Lacking Reviews | No | Sure ($1.1 per thirty days in keeping with tool slot) | Mac, Home windows, Ubuntu, iOS, Android |
| To find My | Integrated Apple tool monitoring, Far off tool locking, Far off knowledge wipe | Sure | No | Mac, iOS |
| LockItTight | GPS-based location monitoring, Zone indicators, Surfing historical past and app monitoring, Display screen captures, key logging (Home windows) | Sure | Sure ($1.99 in keeping with tool per thirty days) | Home windows, ChromeOS, Android, iOS |
| Absolute | Complete tool and information coverage, GPS, Wi-Fi, and IP monitoring, Far off tool locking and information wipe, Software restoration characteristic with Investigations Crew | No | Sure ($19.99 for three hundred and sixty five days) | Home windows, macOS |
| Pombo | Encrypted monitoring knowledge, Person-controlled consumer and server, Open-source, Minimum device footprint | Sure | No | GNU/Linux, Mac, Home windows |
1. Prey
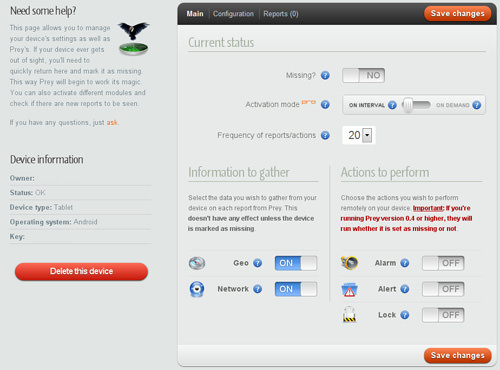

Prey is a strong app designed to trace and protected quite a lot of instruments comparable to laptops, smartphones, and drugs. It employs more than one monitoring strategies like GPS, WiFi triangulation, and GeoIP to verify actual location monitoring. The app’s “Sensible Monitoring” characteristic is not just correct but additionally battery-efficient. It updates the tool’s location every time it detects motion. A world view permits you to track the site of your entire instruments concurrently.
Moreover, Prey permits you to create “Regulate Zones,” that are geofenced spaces that ship indicators if a tool enters or leaves them. You’ll be able to additionally set automatic safety movements, comparable to tool locking, in accordance with those zones.
The “Location Historical past” characteristic in Prey permits you to backpedal a tool’s actions. This will let you spot any odd job. The knowledge is arranged by means of date and time and is visually represented thru a heatmap. If a tool is misplaced, the “Lacking Reviews” characteristic collects very important knowledge like within reach WiFi networks and tool pictures to help in its restoration.
Value:
-
Prey Monitoring: At $1.1 per thirty days in keeping with tool slot, this plan gives elementary monitoring options. It comprises location historical past, lacking stories, job logs, and geofencing. The plan additionally lets in far flung display screen locking. NGOs and academic establishments are eligible for a ten% cut price.
-
Prey Coverage: Priced at $1.6 per thirty days in keeping with tool slot, this plan comprises the entire monitoring options of the primary plan, together with added security measures. You’ll be able to carry out customized wipes, manufacturing facility resets, or even use a kill transfer on Home windows instruments. It additionally helps far flung encryption for Home windows and document retrieval. A ten% cut price is to be had for NGOs and academic establishments.
-
Prey Complete Suite: Costing $1.8 per thirty days in keeping with tool slot, this all-inclusive plan gives the entire options from the former plans and provides mass movements, audit logs, and tool mortgage control. Computerized movements in accordance with particular occasions or time frames also are integrated. Any long term options will likely be added to this plan at no additional fee.
Compatibility:
Prey is appropriate with Mac, Home windows, Ubuntu, iOS, and Android.
2. To find My
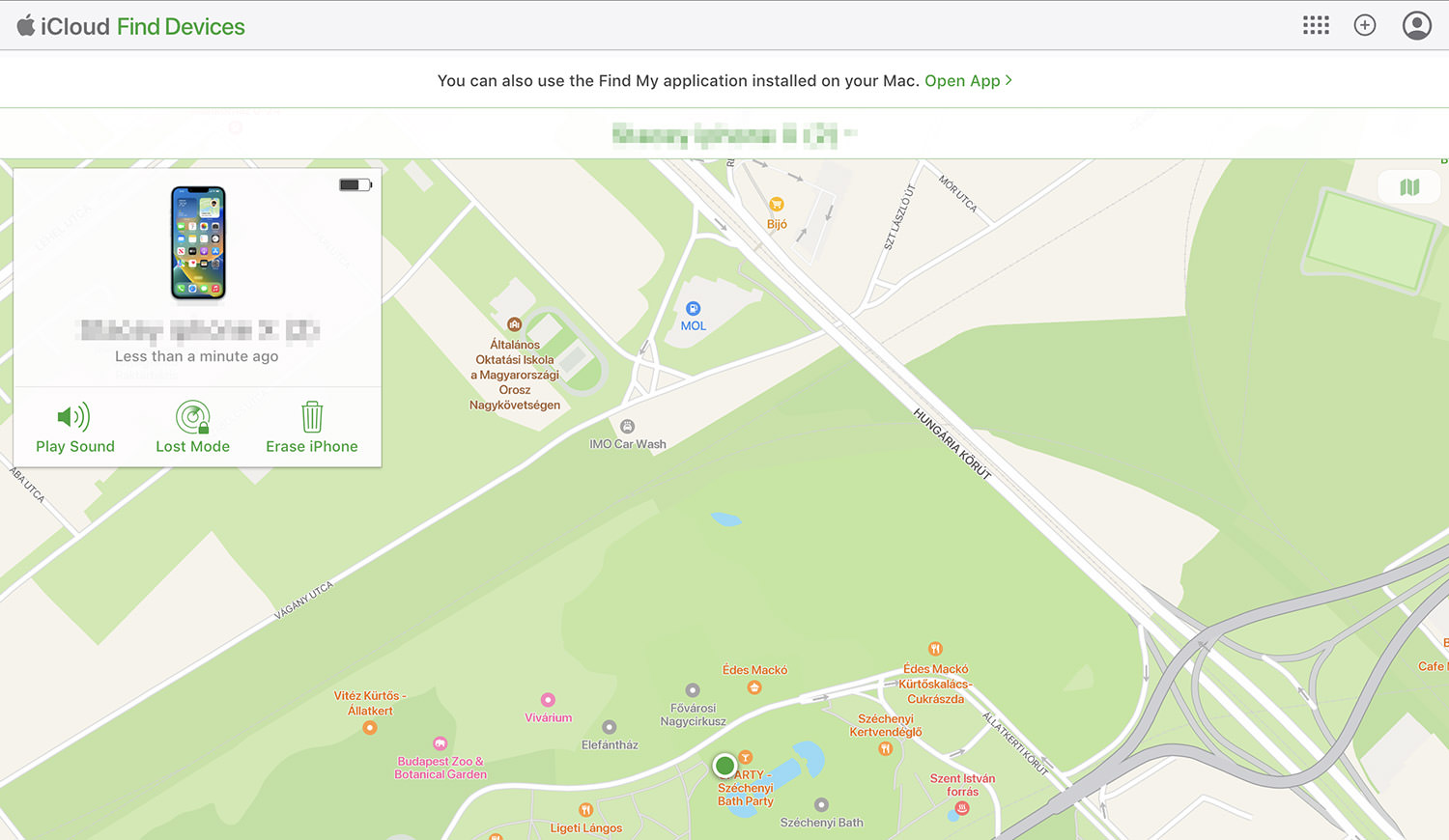

If you happen to’re part of the Apple ecosystem, the To find My characteristic is a integrated resolution for monitoring your Apple instruments. To permit this option, cross to Gadget Personal tastes > iCloud and test the To find My field. This permits you to find lacking Apple instruments like Apple Watch, AirPods, Macs, iPhones, and iPads thru iCloud, or by way of your Mac.
Past simply monitoring, To find My additionally gives further security measures. You’ll be able to remotely lock your tool the use of a customized passcode. In additional serious circumstances, you’ve the technique to remotely wipe the tool to safeguard your own knowledge.
Value:
The To find My app is loose, it comes integrated along with your iOS and iPadOS instruments.
Compatibility:
To find My is appropriate with Mac and iOS.
3. LockItTight
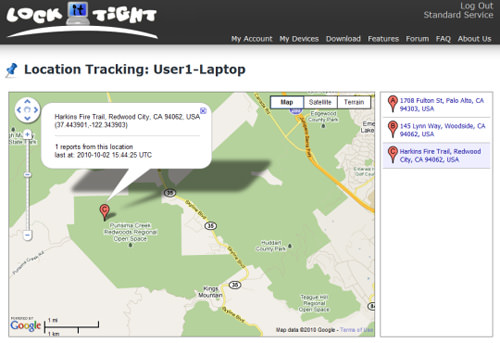

LockItTight is a multifaceted monitoring and tracking app appropriate for quite a lot of customers, together with folks, folks, and IT managers. For private use, it supplies GPS-based location monitoring for your entire computer systems and telephones. Oldsters can make the most of options like zone indicators, surfing historical past tracking, and app monitoring to verify their youngsters’s protection. IT managers in instructional or company settings can set up more than one instruments, generate stories, and follow common settings with only one click on.
The app boasts a variety of core options appropriate with other instruments. Those come with location monitoring and zone indicators, which notify you when a tool enters or leaves a specified space. Android customers can get pleasure from app monitoring, whilst Home windows customers have get right of entry to to options like display screen captures, digital camera photographs, key logging, clipboard logging, surfing historical past, and site blockading. This makes LockItTight a complete resolution for tracking your instruments, whether or not you’re a person, a father or mother, or an IT supervisor.
Value:
-
Unfastened Plan: This no-cost plan lets in monitoring of as much as 5 instruments and comprises 25 stored stories with updates each and every 5 mins. All stories are encrypted for safety.
-
Same old Plan: Prices $1.99 in keeping with tool per thirty days for per month billing or $0.99 in keeping with tool per thirty days for annual billing. It comprises 100 stored stories, 5-minute updates, and encrypted stories.
-
Top class Plan: Priced at $4.99 in keeping with tool per thirty days for per month billing or $2.99 in keeping with tool per thirty days for annual billing. It gives 500 stored stories, updates each and every 2 mins, and encrypted stories.
-
Final Plan: Prices $9.99 in keeping with tool per thirty days for per month billing or $7.99 in keeping with tool per thirty days for annual billing. It supplies 1000 stored stories, updates each and every minute, and most safety with encrypted stories.
All plans be offering on-demand file requests and have encrypted stories for enhanced safety.
Compatibility:
LockItTight is appropriate with Home windows, ChromeOS, Android, and iOS.
4. Absolute
Absolute is a complete safety app designed to offer protection to each your own home and private instruments. It gives numerous options curious about safeguarding your delicate data and {hardware}. With enterprise-level knowledge and tool coverage functions, Absolute is especially well-suited for securing laptops and private computer systems.
If a tool is going lacking, you’ll be able to song it the use of GPS, Wi-Fi, and IP cope with knowledge. Moreover, you’ll be able to remotely lock the tool to forestall unauthorized use or even remotely wipe all delicate knowledge to offer protection to in opposition to fraud.
What units Absolute aside is its distinctive tool restoration characteristic, supported by means of a devoted Investigations Crew. This crew assists within the retrieval of stolen instruments. Additionally, the app gives a ensure: in case your stolen tool isn’t recovered inside of 60 days, you’ll be eligible for as much as $1,000, matter to precise stipulations. This provides an additional layer of assurance, supplying you with each keep watch over and a security web in unlucky scenarios.
Value:
-
Fundamental Plan: Priced at $19.99 for three hundred and sixty five days, this plan gives 3 core options:
- Find your tool
- Lock your tool
- Delete knowledge out of your tool
-
Same old Plan: Prices $39.99 for three hundred and sixty five days and comprises the entire options of the Fundamental Plan, plus:
- Get well your stolen tool
-
Top class Plan: Priced at $59.99 for three hundred and sixty five days, this plan comprises the entire options of the Same old Plan and provides an extra ensure:
- Obtain as much as $1,000 in case your stolen tool isn’t recovered inside of 60 days (stipulations follow).
Every plan is to be had for both a one-year or a three-year subscription duration.
Compatibility:
Absolute is appropriate with Home windows and macOS.
5. Pombo
Pombo is a safety tool designed to lend a hand within the restoration of stolen computer systems. Suitable with Home windows, GNU/Linux, and macOS, it runs unobtrusively within the background, sending encrypted monitoring knowledge to a internet server of your opting for. In case your laptop will get stolen, you’ll be able to log into your internet server to retrieve the latest document uploaded by means of Pombo.
As soon as decrypted, this document can also be passed over to regulation enforcement, offering them with essential data just like the thief’s IP cope with, timestamps, within reach routers, or even a photograph in case your laptop has a webcam.
With a focal point on person privateness and safety, Pombo encrypts all monitoring knowledge the use of GnuPG, making sure that most effective you’ll be able to decrypt it. Not like different answers, Pombo doesn’t rely on third-party products and services, supplying you with complete keep watch over over each the buyer and server. Being open-source, it lets in for personalisation and extra building.
Further options come with the versatility to change servers, no tool charges or subscriptions, and minimum have an effect on on device sources. The gathered knowledge comprises device main points, community interfaces, present connections, and within reach Wi-Fi get right of entry to issues.
Value:
Pombo is open-source and loose to make use of.
Compatibility:
Pombo is appropriate with GNU/Linux, Mac, and Home windows.
Ultimate Ideas
The adage “prevention is healthier than remedy” holds true, particularly in terms of safeguarding your computer. One of the best approach to get better a stolen computer is to be sure that it doesn’t get stolen within the first position. Whilst it’s true that unlucky occasions can’t at all times be have shyed away from, taking proactive measures can considerably scale back the chance.
All the time be vigilant while you’re away out of your computer or different property. Stay an additional eye out to verify their protection. Moreover, it’s recommended to not go away your instruments unattended for prolonged sessions. Through taking those precautionary steps, you no longer most effective decrease the possibilities of robbery but additionally save your self the effort and tension of coping with a stolen computer.
The put up 5 Highest Apps to Observe Down Your Stolen Computer (2023) gave the impression first on Hongkiat.
WordPress Website Development Source: https://www.hongkiat.com/blog/best-apps-track-stolen-laptop/