If there’s something Hollywood films train us, it’s that hackers are artful and feature more than a few tips to bypass our safety. In the actual global, a safety factor incessantly comes right down to alternative reasonably than evolved ability. A “DNS poisoning” assault suits this description, and in reality, you want to have the abilities to stay your area from being spoofed.
The idea that is understated: guests see what looks as if your web site, however it’s fraudulent and damaging, whilst this pretend web site seems to be identical. As such, you wish to have to make use of a number of ways to verify customers are secure, and your web page stays unfastened from assaults.
On this submit, we’re going to dive into the concept that of DNS poisoning and area spoofing. We’re additionally going to discuss one of the most surrounding ideas that will help you perceive why your eventual reaction is the most productive way.
Contents
A Primer At the Area Identify Machine (DNS)
Ahead of we get into the specifics of DNS poisoning, let’s chat concerning the Domain Name System. Whilst surfing a web site seems a simple process, so much is happening underneath the server’s hood.
There are many parts concerned to get you from ‘A’ to ‘B’:
- IP Deal with. It’s a string of numbers this is your exact internet cope with. Imagine them the coordinates of your home. As an example, 127.0.0.1:8080 is a normal “localhost” cope with (i.e. your pc).
- Area title. If the IP cope with represents coordinates, the domain name is your cope with as it sounds as if at the envelope. After all, “kinsta.com” is without doubt one of the hundreds of thousands of examples.
- A DNS request. It’s a very good instance of a high-level frontend process with a posh low-level procedure. For now, imagine a request to be your browser asking a devoted server what the cope with is for a collection of coordinates.
- A DNS server. That is other out of your web site’s server in that it’s 4 servers in a single. Its activity is to process DNS requests. We’ll speak about this in a bit extra element in later sections.
- Recursive server. You’ll additionally see those servers referred to as “resolving title servers.” It’s a part of the DNS search for procedure and is liable for querying servers for the area title on the subject of an IP cope with.
At the complete, a DNS makes fetching a site title clear-cut for the end-user. It’s a core a part of the internet, and as such, it has many shifting portions.
We can take a look at the search for procedure itself subsequent, despite the fact that you’ll be able to already see how the DNS has an important activity to satisfy.
frame a.novashare-ctt{show:block;background:#00abf0;margin:30px auto;padding:20px 20px 20px 15px;colour:#fff;text-decoration:none!necessary;box-shadow:none!necessary;-webkit-box-shadow:none!necessary;-moz-box-shadow:none!necessary;border:none;border-left:5px forged #00abf0}frame a.novashare-ctt:hover{colour:#fff;border-left:5px forged #008cc4}frame a.novashare-ctt:visited{colour:#fff}frame a.novashare-ctt *{pointer-events:none}frame a.novashare-ctt .novashare-ctt-tweet{show:block;font-size:18px;line-height:27px;margin-bottom:10px}frame a.novashare-ctt .novashare-ctt-cta-container{show:block;overflow:hidden}frame a.novashare-ctt .novashare-ctt-cta{flow:proper}frame a.novashare-ctt.novashare-ctt-cta-left .novashare-ctt-cta{flow:left}frame a.novashare-ctt .novashare-ctt-cta-text{font-size:16px;line-height:16px;vertical-align:heart}frame a.novashare-ctt .novashare-ctt-cta-icon{margin-left:10px;show:inline-block;vertical-align:heart}frame a.novashare-ctt .novashare-ctt-cta-icon svg{vertical-align:heart;top:18px}frame a.novashare-ctt.novashare-ctt-simple{background:0 0;padding:10px 0 10px 20px;colour:inherit}frame a.novashare-ctt.novashare-ctt-simple-alt{background:#f9f9f9;padding:20px;colour:#404040}frame a.novashare-ctt.novashare-ctt-simple-alt:hover,frame a.novashare-ctt.novashare-ctt-simple:hover{border-left:5px forged #008cc4}frame a.novashare-ctt.novashare-ctt-simple .novashare-ctt-cta,frame a.novashare-ctt.novashare-ctt-simple-alt .novashare-ctt-cta{colour:#00abf0}frame a.novashare-ctt.novashare-ctt-simple-alt:hover .novashare-ctt-cta,frame a.novashare-ctt.novashare-ctt-simple:hover .novashare-ctt-cta{colour:#008cc4}
The Means of a DNS Look up
Undergo with us right here whilst we provide what looks as if an summary analogy.
Actions that take other people into far flung puts, equivalent to climbing or crusing, percentage one explicit threat: getting misplaced and no longer being present in time. The standard approach of finding stranded other people has been to make use of coordinates. They’re specific and be offering pinpoint accuracy.
On the other hand, this procedure has drawbacks. First, you wish to have to understand how to calculate your coordinates for any location — difficult if in a far flung a part of the arena. 2d, you must articulate the ones coordinates to the rescue crew. One mistaken quantity, and the results are dire.
The what3words app takes the advanced technique of calculating and passing on coordinates and turns it right into a three-word abstract of your normal location. As an example, take Automattic’s headquarters:
The Automattic workplaces in Apple Maps.
The coordinates of the positioning are 37.744159, -122.421555. Until you’re a professional navigator, regardless that, you’re not really to grasp this. Even supposing you probably did, getting this within the palms of any person who may can help you is a narrow proposition.
In a nutshell, what3words takes an summary set of coordinates and interprets them into 3 memorable phrases. On the subject of Automattic’s workplaces, it’s first rate.transfers.sleeps:
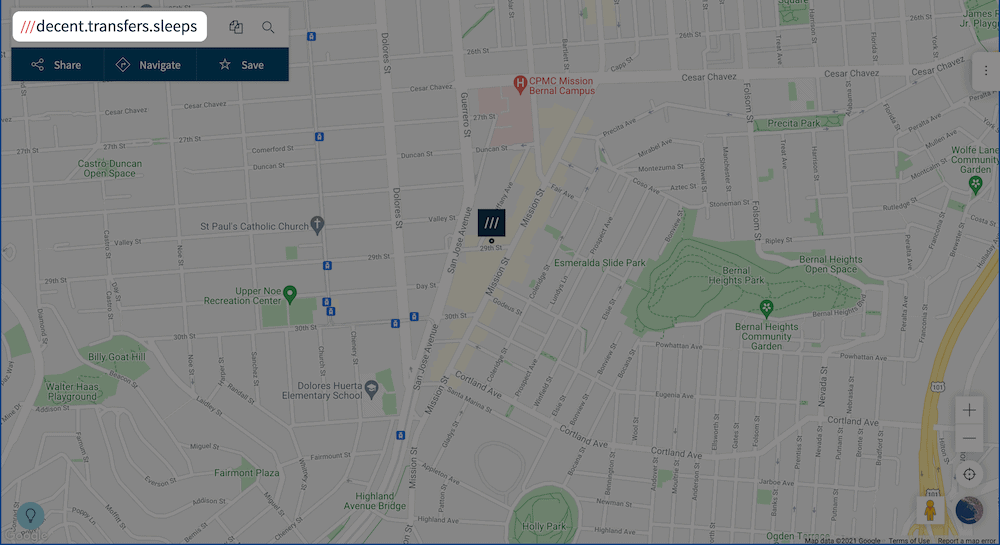
The what3words web site, appearing Automattic’s workplaces.
This places advanced international positioning within the palms of just about somebody with get entry to to the app. It’s saved a lot of civilian lives already.
This ties in with a DNS search for since the procedure is identical. On the subject of what3words, the rescuer asks the app for the coordinates of a notice string. The request is shipped throughout servers to search for the coordinates and go back to the end-user once they’re discovered.
A DNS lookup has a similar flow:
- Your browser requests the IP cope with for a site title.
- Your working machine (OS) asks the recursive server to search out the area title and starts a run via its selection of servers.
- When it reveals the area title, it’s returned to the browser.
One of the crucial drawbacks of what3words is how a notice string isn’t as correct as a collection of coordinates. This implies you’ll be able to pinpoint a normal location speedy however would possibly spend longer discovering the stranded particular person.
A DNS search for has drawbacks as smartly, and malicious attackers can exploit them. Ahead of we take a look at this, regardless that, let’s take a short lived detour to discuss caching and the way it will accelerate a search for.
DNS Caching
Just like internet caching, DNS caching help you recall common queries to the server. This will likely make the method of fetching an IP cope with sooner for every new seek advice from.
In brief, the cache is positioned throughout the DNS server machine and cuts out the additional commute to the recursive server. This implies a browser can fetch an IP cope with directly from the DNS server and entire the GET request in a faster time.
You’ll in finding DNS caches right through all of your machine. As an example, your pc may have a DNS cache, as will your router and web carrier supplier (ISP). You incessantly don’t understand how a lot your surfing enjoy depends upon DNS caching — till you’re a sufferer of DNS poisoning, this is.
What DNS Poisoning Is
Now that you know the concept that of a DNS search for and all of the technique of fetching an IP cope with, we will be able to see how it may be exploited.
You’ll incessantly see DNS poisoning known as “spoofing” too as a result of having a fraudulent “lookalike” web site within the chain is a part of the assault.
We’re going to speak in additional element about all of those sides, however know that DNS poisoning or spoofing is a damaging assault that may purpose psychological, financial, and resource-related issues for customers and the web.
First, regardless that, let’s get into the method of cache poisoning.
How DNS Spoofing and Cache Poisoning Works
For the reason that the entire spoofing procedure is advanced, attackers have created many alternative techniques to succeed in their objective:
- System-in-the-Center. That is the place an attacker will get between the browser and DNS server, poisons each, and redirects a person to a fraudulent web page on their very own server.
- Server hijacking. If an attacker will get into the DNS server, they may be able to reconfigure it to ship all requests to their very own web page.
- Poisoning via junk mail. By contrast to a server hijack, this way poisons the client-side (i.e. the browser). Get entry to is incessantly granted via junk mail hyperlinks, emails, and fraudulent commercials.
- “Birthday assaults.” It is a complex cryptographic attack that takes some additional rationalization.
A birthday assault is according to the “birthday problem.” It is a likelihood state of affairs that claims (in a nutshell) if there are 23 other people in a room, there’s a 50% likelihood of 2 sharing the similar birthday. If there are extra other people within the room, the probabilities upward thrust.
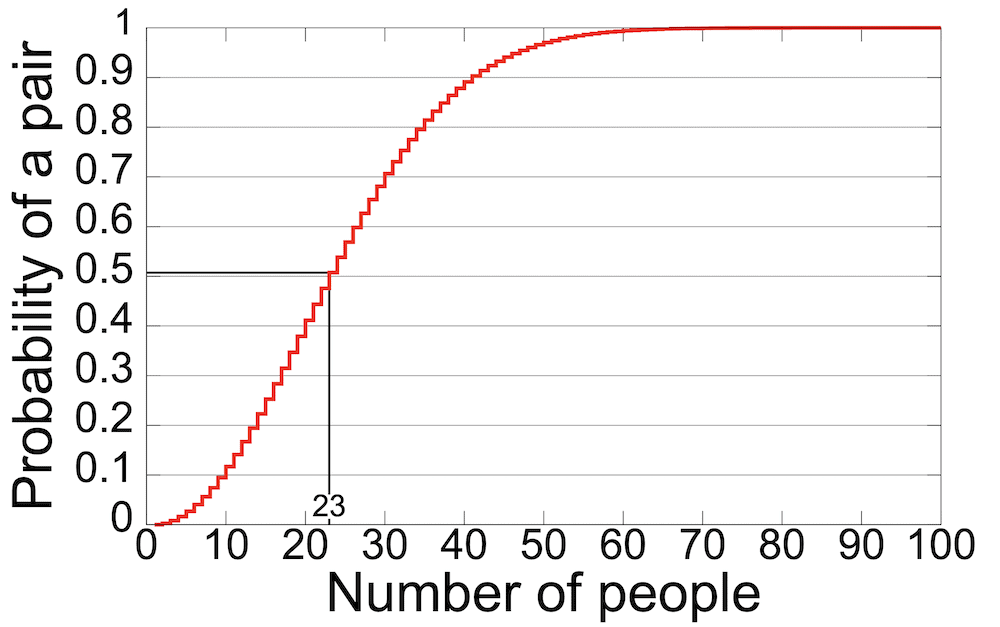
A graph appearing the Birthday Downside. (Symbol supply: Wikipedia)
This interprets to DNS poisoning according to the identifier that connects the DNS search for request to the GET reaction. If the attacker sends a undeniable choice of random requests and responses, there’s a excessive likelihood of a fit leading to a a hit poisoning strive. From round 450 requests, the likelihood is ready 75%, and at 700 requests, an attacker is nearly assured to crack the server.
In brief, assaults to the DNS server occur typically as a result of this provides a malicious person larger flexibility to control your web page and person knowledge. There’s additionally no verification for DNS knowledge as a result of requests and responses don’t use Transmission Control Protocol (TCP).
The vulnerable level within the chain is the DNS cache as a result of this acts as a repository for DNS entries. If an attacker can inject solid entries into the cache, each person who accesses it is going to in finding themselves at a fraudulent web page till the cache expires.
Signal Up For the Publication
Attackers will incessantly search for a couple of alerts, vulnerable issues, and knowledge issues to focus on. They paintings to identify DNS queries that haven’t been cached but since the recursive server should adopt the question sooner or later. By way of extension, an attacker can even search for the nameserver a question will move to. As soon as they have got this, the port the resolver makes use of and the request ID quantity are necessary.
Whilst assembly all of those necessities isn’t vital — in the end, an attacker can get entry to servers via a large number of strategies — ticking those containers off makes their activity more straightforward.
Actual-Global Examples of DNS Poisoning
There were a couple of high-profile examples through the years of DNS poisoning. In some circumstances, it’s an intentional act. For example, China operates a firewall on a large scale (the so-called “Nice Firewall of China”) to keep an eye on the guidelines web customers obtain.
In a nutshell, they poison their very own servers by means of redirecting guests heading to state-unsanctioned websites equivalent to Twitter and Fb. In one case, Chinese language restrictions even made their approach into the Western global’s ecosystem.
A networking error from a Swedish ISP served root DNS knowledge from Chinese language servers. This supposed customers in Chile and the United States have been redirected somewhere else when getting access to some social media websites.
In another example, Bangladeshi hackers protesting mistreatment in Malaysia poisoned many domain names on the subject of Microsoft, Google, YouTube, and different high-profile websites. This seems to were a case of server hijacking reasonably than a client-side factor or junk mail.
Even WikiLeaks isn’t resistant to DNS poisoning assaults. A potential server hijack a couple of years in the past led to guests to the web site to be redirected to a web page devoted to the hackers.
DNS poisoning doesn’t must be an advanced procedure. So-called “moral hackers” — i.e. those that glance to show safety flaws reasonably than inflict injury — have straightforward methods for trying out spoofing on their very own computer systems.
As opposed to being redirected, regardless that, there won’t appear to be any long-term results of DNS poisoning at the floor. In reality, there are — and we’ll speak about them subsequent.
Why DNS Poisoning and Spoofing Is So Destructive
There are 3 major objectives of an attacker hoping to accomplish DNS poisoning on a server:
- To spread malware.
- Reroute you to any other web site that may get advantages them come what may.
- Thieve knowledge, both from you or any other entity.
After all, it does no longer bounce the creativeness to know why DNS poisoning or spoofing is an issue for ISPs, server operators, and end-users.
As we famous, spoofing is a large downside for ISPs, such a lot in order that there are tools like the CAIDA Spoofer to be had to assist.
Want a web hosting resolution that offers you a aggressive edge? Kinsta’s were given you lined with unbelievable velocity, cutting-edge safety, and auto-scaling. Check out our plans
The CAIDA web site.
A couple of years in the past, statistics showed that there have been round 30,000 assaults an afternoon. This quantity will virtually undoubtedly have larger for the reason that document used to be printed. What’s extra, as used to be the case with the instance within the earlier phase, handing over spoofed websites throughout a community brings person accept as true with problems to the fore, at the side of privateness issues.
Without reference to who you’re, there are a couple of dangers concerned while you’re the sufferer of poisoning and spoofing:
- As with the Great Firewall of China, you’ll want to be matter to censorship. This implies the guidelines you get gained’t be correct, which has a knock-on impact on many social and political arenas.
- Information robbery is a best worry, and it’s a profitable undertaking for many who wish to download person banking knowledge and different delicate knowledge.
- You need to be prone to malware and different Trojan viruses to your machine. As an example, an attacker may inject a keylogger or different sorts of spy ware to your machine via a spoofed web page.
There are different connected results of DNS poisoning too. For example, you won’t be capable of practice any safety updates on your machine whilst the restoration procedure is in complete swing. This leaves your pc inclined for longer.
Additionally, imagine the fee and complexity of this cleanup procedure, as it is going to impact everybody alongside the chain. Upper costs for all the hooked up services and products is solely one of the crucial negatives.
The hassle of getting rid of DNS poisoning is immense. For the reason that spoofing impacts each client- and server-side setups, ridding it from one doesn’t imply it’s long past from all.
Learn how to Save you DNS Poisoning
There are two spaces suffering from DNS poisoning — client-side and server-side. We’re going to try what you’ll be able to do to stop this harmful assault on each side of the coin.
Let’s start with what the web as an entire is doing at the server-side.
How the Web Tries to Save you DNS Poisoning and Spoofing Server-Aspect
Even supposing we’ve talked so much about DNS right through this newsletter, we haven’t famous how antiquated the generation is. In brief, DNS isn’t the most productive have compatibility for a contemporary internet surfing enjoy because of a couple of components. For starters, it’s unencrypted, and with out some necessary validation concerns, that might forestall a large number of DNS poisoning assaults from proceeding.
One fast solution to save you assaults from turning into more potent is thru a simple logging strategy. This carries out a simple comparability between the request and the reaction to look in the event that they fit.
On the other hand, the long-term solution (in keeping with the mavens) is by means of the use of Domain Name System Security Extensions (DNSSEC). It is a generation designed to battle DNS poisoning, and in clear-cut phrases, it places other ranges of verification in position.
Going deeper, DNSSEC makes use of “public-key cryptography” as verification. It is a approach of signing off at the knowledge as authentic and faithful. It’s saved along your different DNS knowledge, and the recursive server makes use of it to test that not one of the knowledge it receives has been altered.
In comparison to different web protocols and applied sciences, DNSSEC is a relative child — however it’s mature sufficient that it’s applied within the root point of the web, regardless that it’s no longer but mainstream. Google’s Public DNS is one carrier that helps DNSSEC in complete, with extra stoning up always.
Even so, there are nonetheless some drawbacks with DNSSEC which can be price noting:
- The protocol doesn’t encode responses. This implies attackers can nonetheless ‘pay attention in’ on site visitors, despite the fact that the assaults should be extra subtle to avoid DNSSEC.
- As a result of DNSSEC makes use of further information to assemble DNS knowledge, there’s any other vulnerability referred to as “zone enumeration.” This makes use of one document to “stroll via” and accumulate all DNS information inside a particular “zone.” Some variations of this document encrypt the knowledge, however others don’t but.
- DNSSEC is a posh protocol, and as it’s additionally new, it may on occasion be misconfigured. After all, it will erode the advantages of the use of it and provide additional issues down the road.
Even so, DNSSEC is the long run at the server-side, no less than. As for you because the end-user, there’re additionally some preventative measures you’ll be able to take.
How You Can Save you DNS Poisoning at the Shopper-Aspect
There are extra techniques to stop DNS poisoning at the client-side, despite the fact that none on their very own shall be as tough as server-side DNSSEC applied by means of a professional. Nonetheless, there are some clear-cut containers you’ll be able to take a look at off as a web page proprietor:
- Use end-to-end encryption for any requests and replies. Secure Sockets Layers (SSL) Certificates do a just right activity right here.
- Make use of spoofing detection equipment such as Xarp. Those scan gained knowledge packets earlier than sending them out. This mitigates any malicious knowledge transfers.
- Expanding the Time-To-Live (TTL) values to your DNS cache will assist flush malicious entries earlier than they may be able to succeed in end-users.
- You will have a just right DNS, DHCP, and IPAM (DDI) technique in position. This is composed of your DNS technique, Dynamic Host Configuration Protocol, and IP Deal with Control. It’s a posh but vital procedure treated by means of sysadmins and server safety mavens.
As an end-user, there are a couple of extra issues you’ll be able to do to assist save you poisoning and spoofing:
- Use a Virtual Private Network (VPN), as your knowledge shall be encrypted finish to finish. You’ll additionally get use of personal DNS servers, once more with end-to-end encryption.
- Take clear-cut precautions, equivalent to no longer clicking unrecognized hyperlinks and sporting out common safety scans.
- Flushing your DNS cache frequently additionally clears malicious knowledge from your machine. It’s one thing that takes seconds and is understated to hold out.
Whilst you’ll be able to’t rid DNS poisoning in overall, you’ll be able to save you the very worst from going down. As an end-user, you don’t have a lot keep an eye on over how the server handles assaults. Likewise, sysadmins don’t get to keep an eye on what occurs within the browser. As such, it’s a crew effort to forestall this maximum damaging of assaults from affecting all of the chain.
Abstract
Web assaults are common. DNS poisoning (or spoofing) is a commonplace assault that may impact hundreds of thousands of customers if left unchecked. It’s because the DNS protocol is previous and unsuited for contemporary internet surfing — despite the fact that more recent applied sciences are at the horizon.
In brief, DNS poisoning redirects an end-user to a fraudulent model of an present web site. It’s a solution to scouse borrow knowledge and infect systems with malware. There’s no foolproof solution to save you it altogether, however you can include it via some clear-cut measures.
Have you ever ever been a sufferer of DNS poisoning or spoofing, and if this is the case, what used to be the purpose? Please percentage your enjoy with us within the feedback phase beneath!
The submit An Introduction to “DNS Poisoning” (And How to Prevent It) gave the impression first on Kinsta.
WP Hosting


