Each day, numerous companies are taking their operations on-line to draw new shoppers and scale globally. One of the most fastest tactics to get a site up and working is thru WordPress, which powers over 43% of all websites on the web.
However with this reputation comes a drawback. Bots and hackers are all the time looking out, seeking to exploit any vulnerabilities in WordPress websites. Those vulnerabilities ceaselessly stand up from putting in compromised plugins or subject matters or the usage of deficient internet hosting that may’t hit upon or save you the commonest assaults, like Disbursed Denial of Carrier (DDoS) or brute power makes an attempt.
Many industry house owners fall into the lure of opting for affordable internet hosting, solely to later lay our a fortune keeping off assaults — assaults that ceaselessly stem from the insufficient safety in their internet hosting supplier.
That is why, as a industry, you shouldn’t be swayed through low prices when settling on a bunch. The point of interest must be on high quality, particularly in the case of safety. You should dig deeper and ask the fitting questions or search detailed details about your host’s security features ahead of opting for. It’s now not sufficient for a bunch to vow safety. You want to know how that safety is carried out.
That’s the place this information is available in. We’ve created a complete tick list of very important questions you must ask your internet host about safety ahead of making your resolution.
1. Knowledge encryption
Knowledge encryption is significant for shielding the guidelines exchanged between your site and its customers. Whether or not it’s buyer main points, cost knowledge, or confidential industry knowledge, making sure this data is encrypted is non-negotiable.
What to invite:
- Does the internet hosting supplier be offering SSL/TLS certificate, and are they integrated within the internet hosting package deal?
- What point of encryption is used for knowledge in transit and at leisure?
- How does the host be certain the safety of delicate knowledge (e.g., buyer knowledge, monetary transactions)?
Why it issues:
SSL/TLS certificate are very important for encrypting knowledge transmitted between your site and its customers. They be sure that delicate knowledge — like bank card numbers or private main points — can’t be intercepted through malicious actors. With out SSL/TLS encryption, your website is at risk of man-in-the-middle assaults, the place hackers can intercept and manipulate the information flowing to and out of your website.
However encryption shouldn’t prevent at knowledge in transit. It’s similarly essential to be sure that your knowledge is encrypted at leisure, that means it’s securely saved at the server, making it inaccessible to unauthorized customers even though they achieve get right of entry to to the bodily server or the information middle.
When opting for a internet host, it’s the most important to substantiate that they provide SSL/TLS certificate and use robust encryption requirements, comparable to 256-bit Complicated Encryption Same old (AES), to give protection to your knowledge in transit and at leisure.
Ask about their insurance policies and practices for encrypting delicate knowledge and making sure your knowledge stays safe, even in worst-case eventualities. Figuring out those encryption measures offers you peace of thoughts, realizing your small business and buyer knowledge are safe.
How Kinsta handles knowledge encryption
At Kinsta, we give protection to your knowledge thru powerful encryption practices, each in transit and at leisure.
As an example, all verified domain names on Kinsta (localhost domain names, brief domain names, and tradition domain names) get pleasure from our integration with Cloudflare, which incorporates unfastened SSL certificate with TLS 1.2 and TLS 1.3 enabled — requirements that offer robust encryption and are broadly supported through all main browsers. This computerized SSL setup way you don’t have to fret about manually configuring your website’s safety until you need to make use of a tradition SSL certificates.
Along with securing knowledge in transit, Kinsta leverages the Google Cloud Platform’s (GCP) state of the art security features to give protection to your knowledge at leisure. This implies all knowledge saved on Kinsta’s servers is encrypted the usage of 256-bit AES encryption, which protects the information if anyone had been to achieve bodily get right of entry to to the disks within the knowledge middle. The encryption keys are frequently turned around and safe with further layers of encryption, including additional safety.
Then again, it’s essential to notice that whilst the disks are encrypted, an attacker who features get right of entry to for your site thru compromised credentials (like SSH get right of entry to) or a vulnerability on your website can learn unencrypted copies of the information. This makes it the most important to handle robust safety practices on the website point, comparable to the usage of robust passwords, enabling two-factor authentication, and frequently updating tool.
Our dedication to knowledge encryption extends past technical measures. Through the years, now we have labored exhausting to develop into SOC 2 compliant and lately accomplished ISO 27001, 27017, and 27018 certifications. See additional info on this article’s safety audits and compliance segment.
2. Firewall and DDoS coverage
Your site’s safety is predicated closely at the power of its firewall, which serves as the primary defensive line in opposition to a lot of cyber threats, together with DDoS assaults.
A strong firewall filters out malicious site visitors, prevents unauthorized get right of entry to, and guarantees your website stays to be had right through tried disruptions. Figuring out how your internet hosting supplier implements those protections is the most important for keeping up your website’s safety and function.
What to invite:
- Does your internet hosting carrier come with a internet utility firewall (WAF) as a part of the package deal?
- How does your firewall give protection to in opposition to DDoS assaults and different not unusual threats?
Why it issues:
A Internet Software Firewall (WAF) protects your website from more than a few threats, together with SQL injections, cross-site scripting (XSS), and DDoS assaults. Those are the commonest and doubtlessly destructive assaults threatening your site.
A well-managed WAF can block those threats ahead of they achieve your website, minimizing the chance of a safety breach and making sure your website stays obtainable.
DDoS assaults, particularly, goal to weigh down your website with a large inflow of site visitors, rendering it gradual or totally unavailable to professional customers. The affect will also be devastating, resulting in misplaced income, broken recognition, and annoyed shoppers.
A robust firewall now not solely filters out this malicious site visitors but additionally performs a crucial function in protecting your website in opposition to DDoS assaults, making sure that your website stays operational even right through an assault.
Efficient firewall and DDoS coverage comes to extra than simply putting in place elementary defenses. It calls for steady tracking, computerized danger detection, and the facility to soak up and mitigate large-scale assaults.
How Kinsta handles firewall and DDoS coverage
At Kinsta, we take a multi-layered strategy to stay your site safe, particularly from threats like DDoS assaults. Central to our coverage technique is our integration with Cloudflare.
All site visitors for websites hosted on Kinsta passes thru Cloudflare, the place an impressive WAF filters it. The WAF mechanically blocks damaging requests, together with DDoS assaults, ahead of they are able to achieve your website.
As an example, we reported how we controlled to serve 75.51 billion requests thru Cloudflare in only one month, of which 3.3 billion had been mitigated through Cloudflare’s Internet Software Firewall (WAF). This displays the effectiveness of Cloudflare’s DDoS coverage in filtering out malicious site visitors.
Our protection doesn’t prevent with Cloudflare. We additionally use GCP’s firewall as a 2d layer of coverage, and now we have inside methods that take a look at abusive traits throughout our infrastructure that can block patterns deemed to be damaging. This guarantees general platform balance.
Moreover, our SysOps crew repeatedly updates firewall regulations in response to explicit problems or threats. We arrange those updates in-house to verify top-notch safety and don’t be offering handbook regulate over those regulations thru shoppers’ MyKinsta dashboards.
For patrons with distinctive wishes, we suggest having their WAF resolution in entrance of our infrastructure the usage of WAF suppliers like Sucuri and Wordfence.
3. Backup and restoration plans
Backups are your protection internet. Within the tournament of a cyberattack, server failure, or unintentional knowledge loss, having a competent backup guarantees that you’ll repair your site briefly and steer clear of extended downtime or everlasting lack of essential knowledge.
However backups are solely as excellent because the frequency with which they’re made and the way simply they are able to be restored. When opting for a bunch, it’s essential to grasp what backup and restoration choices are to be had and the way they give protection to your knowledge.
What to invite:
- How ceaselessly are backups carried out, and the place are they saved?
- What’s the procedure for restoring knowledge in case of a breach or loss?
- Are backups encrypted and saved off-site to forestall loss in case of a neighborhood crisis?
Why it issues:
Common, computerized backups be sure you don’t lose crucial site knowledge because of sudden problems like a breach, server crash, or consumer error. Figuring out that backups are carried out day-to-day or extra often supplies peace of thoughts that you’ll repair your website to a up to date model with out vital knowledge loss.
The positioning of backup garage may be essential. Storing backups in a safe, off-site location way your knowledge stays safe even though there’s an issue with the principle server or knowledge middle. Encrypting backups guarantees that your delicate knowledge stays secure even though they’re intercepted.
In spite of everything, ease of recovery is vital. If one thing is going unsuitable, the facility to briefly and simply repair a backup with out technical headaches or delays is the most important to minimizing downtime and maintaining your website working easily.
Having a transparent figuring out of your internet host’s backup and restoration plans is helping be sure that, it doesn’t matter what occurs, you’ll repair your website with minimal disruption.
How we maintain backup and restoration at Kinsta
At Kinsta, we perceive the crucial significance of getting dependable backups. That’s why we provide a complete backup resolution that guarantees you’ll briefly recuperate your website in case of an emergency.
We provide the next varieties of backups:
- Computerized day-to-day backups: We offer computerized day-to-day backups for all WordPress websites hosted on our platform. Those backups seize a whole snapshot of your website, together with information, databases, redirects, and MyKinsta settings. Which means if one thing is going unsuitable, you’ll simply repair your website to its earlier state with only a few clicks in MyKinsta.
- Handbook and hourly backups: When making vital adjustments for your website, you’ll create as much as 5 handbook backups, making sure you might have repair issues precisely when you wish to have them. Moreover, we provide an hourly backup add-on for customers who want much more common repair issues — very best for eCommerce websites or different dynamic environments the place knowledge adjustments ceaselessly.
- Exterior backups: We provide an exterior backups add-on that lets you again up your website to Google Cloud Garage or Amazon S3. This off-site backup possibility provides an additional layer of safety, making it simple to include those backups into your broader crisis restoration technique.
- Downloadable backups: We additionally let you create and obtain a backup of your website in a ZIP report as soon as every week. This backup contains your website’s information and database, permitting you to make a copy offline for additonal safety.
At Kinsta, we additionally know the significance of simple backup recovery. In MyKinsta, the method is fast and easy whether or not you wish to have to revive for your are living setting or a staging website. If you happen to ever wish to undo a recovery, a brand new backup is mechanically created ahead of the repair, providing you with flexibility and regulate over your website’s state.
Additionally, relying for your plan, backups are retained for as much as 30 days, making sure you might have plentiful repair issues to make a choice from if one thing is going unsuitable. We provide prolonged retention sessions for the ones on our higher-tier plans, offering even larger peace of thoughts.
4. Get admission to regulate and authentication
Controlling who can get right of entry to your site’s backend and server setting is the most important for keeping up safety.
Unauthorized get right of entry to may end up in knowledge breaches, website defacement, or compromise. Imposing robust get right of entry to regulate measures and safe authentication strategies is very important to protective your website.
When comparing a internet hosting supplier, figuring out how they arrange get right of entry to regulate and authentication can provide you with self assurance that your website is well-protected from unauthorized customers.
What to invite:
- What get right of entry to regulate measures are in position to forestall unauthorized get right of entry to to my account and server?
- Does the host fortify multi-factor authentication (MFA) for gaining access to the regulate panel, FTP/SFTP, and SSH?
- How are permissions controlled for more than one customers or crew individuals?
Why it issues:
Robust get right of entry to regulate is the basis of your site’s safety. With out correct get right of entry to controls, unauthorized customers may just achieve access for your website’s backend, doubtlessly resulting in knowledge robbery, unauthorized adjustments, and even whole website takeover.
Efficient get right of entry to regulate comes to proscribing who can get right of entry to your website and making sure that the ones with get right of entry to use safe, up-to-date authentication strategies.
MFA is a key part of safe get right of entry to regulate. Via requiring a 2d type of verification — comparable to a textual content message code or authentication app — along with a password, MFA provides an additional layer of coverage in opposition to unauthorized get right of entry to. That is particularly essential for crucial spaces like your internet hosting regulate panel and FTP/SFTP and SSH get right of entry to, the place a breach will have serious penalties.
Managing permissions successfully may be very important, specifically for websites with more than one customers or crew individuals. A well-structured permission device guarantees that customers solely have get right of entry to to the spaces of the website they want, lowering the chance of unintentional or malicious adjustments.
It’s essential to know how your internet hosting supplier handles consumer permissions and whether or not they be offering gear that will help you arrange get right of entry to throughout your crew.
How we maintain get right of entry to regulate and authentication at Kinsta
Kinsta is a controlled WordPress internet hosting resolution that gives a custom-built cPanel selection for managing your websites. This dashboard gives many options that don’t seem to be to be had within the cPanel whilst being more straightforward to make use of.
We use Position-Primarily based Get admission to Keep an eye on (RBAC) in MyKinsta. This implies you’ll assign other get right of entry to ranges to crew individuals in response to their roles, making sure that every individual solely has get right of entry to to what they want. As an example, a WordPress Website developer may have get right of entry to solely to staging environments, whilst a Corporate Administrator can arrange all the corporate account. This point of regulate minimizes the probabilities of unauthorized adjustments and helps to keep delicate spaces limited to the fitting other people.
Dashboard safety is bolstered through 2FA, which is to be had to all customers in MyKinsta. This additional step, requiring customers to ensure their identification with a code from an authenticator app, guarantees that get right of entry to to the account is safe even though a consumer’s password is compromised. It’s a easy but robust layer of protection that is helping safe your site and account.
Moreover, we fortify Unmarried Signal-On (SSO) the usage of OAuth 2.0 by the use of GitHub. This permits you to log in to MyKinsta securely together with your GitHub credentials, making the login procedure smoother whilst keeping up robust safety requirements.
At the infrastructure facet, we use GCP’s Identification and Get admission to Control (IAM) device to regulate inside get right of entry to to our servers. The program guarantees that our inside crew individuals solely have the minimal get right of entry to they wish to carry out their duties. Via sticking to the primary of least privilege, we reduce the chance of unauthorized get right of entry to to our infrastructure, making sure that your website stays safe through more than one layers of safety.
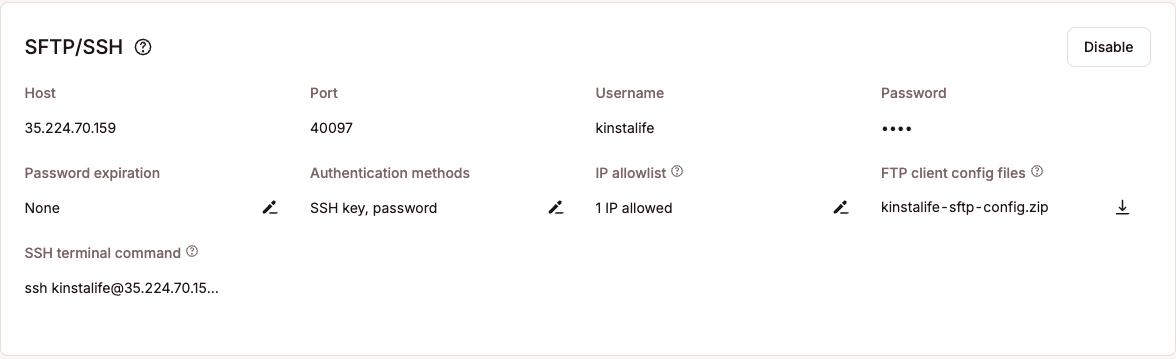
For safe backend get right of entry to, we offer SSH and SFTP connections, with credentials controlled in MyKinsta. You’ll be able to beef up safety through atmosphere password expiration periods, proscribing get right of entry to through IP deal with, or enabling SSH key-only get right of entry to.
Moreover, you’ll disable SFTP/SSH get right of entry to when now not wanted and alter password controls, providing you with complete regulate over how and when get right of entry to is authorized, making sure your website’s setting stays safe.
5. Malware detection and removing
With such a lot of plugins, subject matters, and tool elements, vulnerabilities can simply seem in a WordPress website, particularly when those components develop into out of date. This will increase the chance of malware (malicious tool) infections, resulting in critical penalties like knowledge robbery, website defacement, and even dropping regulate of your site.
Detecting and disposing of malware impulsively is significant to keeping up your site’s safety and recognition. That’s why it’s very important to know how your internet hosting supplier handles malware detection and removing.
What to invite:
- Does the internet hosting supplier be offering computerized malware scans, and the way ceaselessly are they carried out?
- What occurs if malware is detected, and the way is it got rid of?
- Can I upload further gear or plugins for enhanced malware coverage?
Why it issues:
Malware infections can compromise your website’s safety and recognition, resulting in lack of buyer accept as true with or even seek engine consequences. That is why common, computerized malware scans are very important. They let you hit upon threats early, making an allowance for instructed motion ahead of they purpose vital harm. If malware is located, having a transparent and environment friendly removing procedure is vital to briefly restoring your website to a blank state.
Moreover, having the choice so as to add your safety gear or plugins can additional support your protection.
Figuring out how your host handles malware detection and removing offers you peace of thoughts that your website is frequently monitored for threats and will also be briefly wiped clean if an an infection happens.
How Kinsta handles malware detection and removing
At Kinsta, we observe your websites 24/7, scanning for malicious code and doable threats. Our proactive method guarantees we catch malware early ahead of it could possibly purpose critical harm. Within the tournament that malware is detected or a website is compromised, we take swift motion to scrub up the an infection.
Our safety pledge promises that in case your WordPress website is hacked whilst hosted with us, we’ll paintings with you without spending a dime to take away the malware and repair your website. This features a deep scan of your website’s information, id of the supply of the an infection, and disposing of any affected plugins or subject matters.
Our container-based internet hosting infrastructure additionally prevents cross-contamination between websites on the server point, offering further peace of thoughts that your different websites stay unaffected. You’ll be able to additionally use common WordPress safety plugins like Sucuri and Wordfence.
6. Uptime tracking and reaction
When your site is going down, it could possibly have critical penalties for your small business — misplaced income, broken recognition, and annoyed customers. Uptime tracking is the most important to verify your website stays on-line and obtainable to guests.
A internet hosting supplier should be offering excellent uptime efficiency, powerful tracking methods, and a fast reaction plan to handle any downtime.
What to invite:
- Does the internet hosting supplier be offering 24/7 uptime tracking?
- How briefly do they reply to downtime, and what’s their procedure for buying the website again on-line?
- Is there a assured uptime proportion of their service-level settlement (SLA)?
Why it issues:
Site downtime will also be pricey. When your website is offline, you lose doable gross sales or engagement, your search engine optimization score too can undergo, and your emblem’s recognition might undergo. That’s why uptime tracking is very important.
Steady tracking guarantees that downtime is straight away detected, permitting the internet hosting supplier to take fast motion and reduce the affect.
A excellent internet hosting supplier may have methods in position to observe uptime 24/7 and a devoted crew in a position to answer issues. As well as, a assured uptime proportion — comparable to 99.9% — in a service-level settlement (SLA) assures that the host is dedicated to maintaining your website working easily.
Figuring out how your supplier handles uptime tracking and their reaction to downtime is vital to making sure your website’s reliability and availability.
How we maintain uptime tracking at Kinsta
Kinsta prioritizes uptime through tracking the standing of each WordPress website on our platform each 3 mins. This common tracking guarantees that we hit upon problems once they stand up. If a website fails to load, our engineers are straight away alerted and reply briefly to revive carrier.
Along with our inside reaction, we notify you at once if crucial problems persist over consecutive exams. This contains website mistakes, DNS misconfigurations, SSL certificates issues, and area expiration. Those proactive notifications let you keep knowledgeable and act impulsively if wanted.
Because of the power of our infrastructure, our platform is subsidized through a 99.9% uptime ensure thru our Carrier Degree Settlement (SLA).
7. Logging and process monitoring
Along with uptime tracking, detailed logging lets you monitor each motion and tournament taking place for your site. This is helping in troubleshooting, auditing, and keeping up the safety of your website through maintaining a report of consumer actions, knowledge get right of entry to, and server efficiency.
What to invite:
- Does the host be offering process logs to trace consumer movements and information get right of entry to?
- Can I get right of entry to server logs for troubleshooting and function tracking?
- How lengthy are logs saved, and are they simply obtainable?
Why it issues:
Logging is very important for keeping up your website’s safety and function. Process logs let you monitor who did what and when, which is the most important for detecting unauthorized movements or pinpointing the reason for a topic. Get admission to to server logs may be essential for troubleshooting server-level issues, diagnosing mistakes, and tracking useful resource utilization.
A excellent internet hosting supplier will be offering simple get right of entry to to consumer process and server logs, making sure you might have the gear to observe your website’s well being and safety.
How Kinsta handles logging and process monitoring
Kinsta supplies detailed process logging and server logs to provide you with complete visibility over your website and account. With the process log, you’ll monitor all key movements carried out inside of MyKinsta, like website adjustments or updates, and notice who initiated them and when. That is particularly helpful for tracking crew actions and briefly figuring out any problems.
For troubleshooting, our platform offers you get right of entry to to essential server logs, together with error logs and get right of entry to logs, at once throughout the MyKinsta dashboard.
Those logs let you diagnose problems like PHP mistakes, cache efficiency, or server requests, making it more straightforward to unravel issues briefly. Further logs, like cache-purge and mail logs, are to be had by the use of SFTP for extra complicated diagnostics.
Our platform additionally sends real-time notifications to tell you of device standing, so that you’ll all the time know if platform-wide problems stand up.
8. Safety audits and compliance
Safety audits and compliance exams be certain your site meets {industry} requirements and follows absolute best practices for safeguarding delicate knowledge.
Common safety audits determine vulnerabilities and weaknesses on your device, whilst compliance with safety frameworks guarantees that your website follows the vital rules, particularly for companies dealing with private knowledge or monetary knowledge.
Figuring out how your internet hosting supplier handles safety audits and compliance is very important to keeping up a safe and compliant site.
What to invite:
- Does the internet hosting supplier behavior common safety audits on its infrastructure?
- Is the host compliant with {industry} safety requirements and rules (comparable to SOC 2, GDPR, PCI DSS)?
- What safety certifications does the internet hosting supplier have, and the way ceaselessly are they renewed?
Why it issues:
For companies that maintain delicate knowledge, compliance with rules like GDPR, PCI DSS, or SOC 2 is very important for heading off fines and keeping up buyer accept as true with.
Web hosting suppliers that behavior common audits and handle compliance with {industry} requirements display a dedication to keeping up a safe setting. Certifications like ISO 27001 and SOC 2 display that the host follows strict safety protocols and undergoes common exams to verify ongoing safety.
Via figuring out your host’s strategy to safety audits and compliance, you’ll leisure confident that your site meets each safety absolute best practices and regulatory necessities, lowering the chance of breaches and making sure knowledge coverage.
How we maintain safety audits and compliance at Kinsta
At Kinsta, we take safety and compliance critically, making sure that our platform meets industry-leading requirements. To handle our compliance with SOC 2 Sort II and ISO 27001, we go through annual safety audits performed through impartial companies, together with BARR. Those experiences, up to date yearly, display our dedication to safeguarding your knowledge and infrastructure.
Our compliance doesn’t prevent there. We also are qualified for ISO 27017 and ISO 27018, reinforcing our adherence to absolute best practices for cloud safety and protective private knowledge in cloud computing environments.
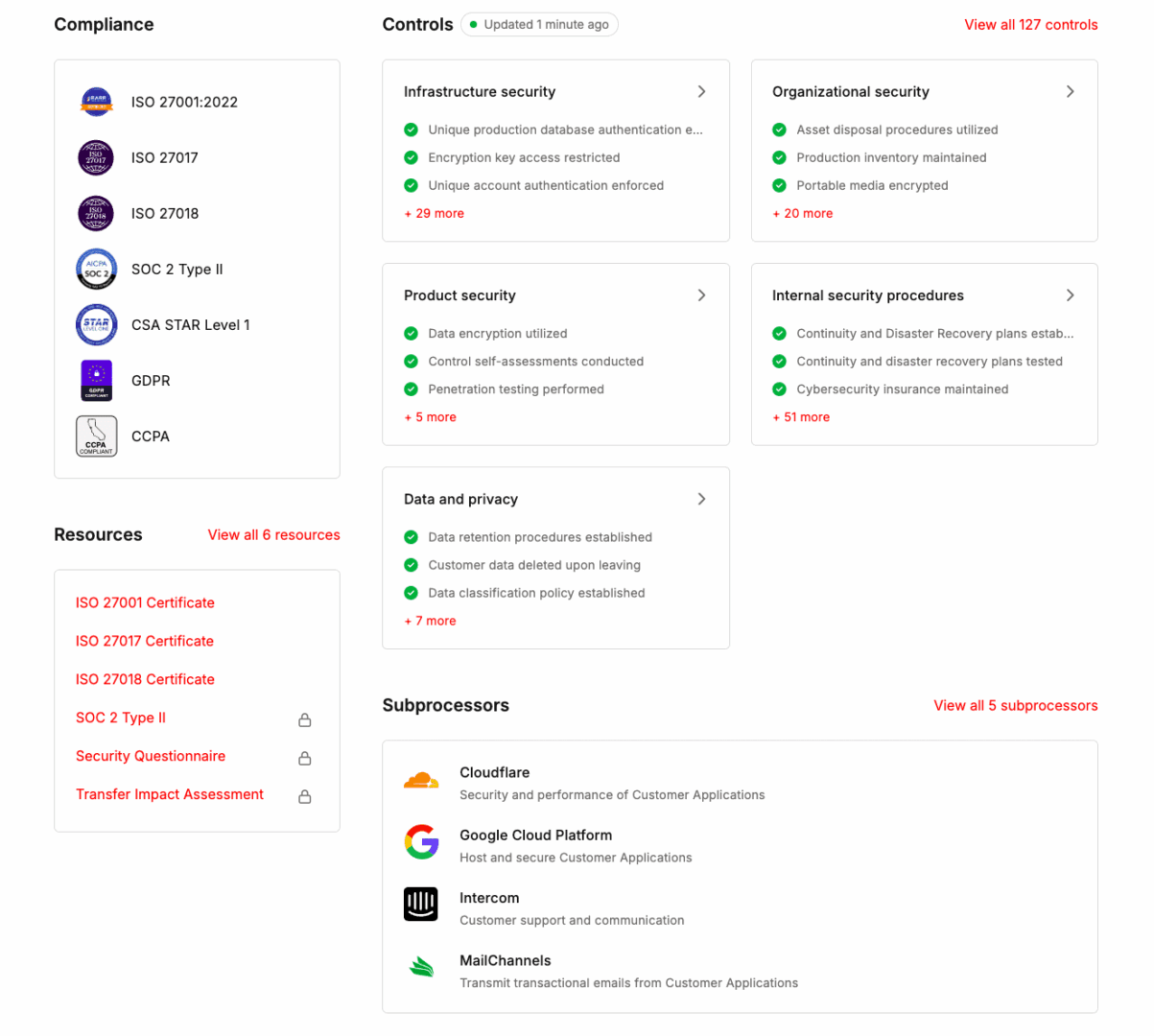
Moreover, we emphasize Knowledge Leak Prevention (DLP) and Knowledge Rights Control. Our device is designed to align together with your group’s Data Safety Coverage, making sure that delicate knowledge is safe in opposition to unauthorized get right of entry to or publicity.
Our Knowledge Processing Addendum (DPA), a part of our phrases of carrier, outlines how we maintain your knowledge, making sure compliance with rules like GDPR and CCPA. This contains how knowledge is processed, saved, and safe, providing you with peace of thoughts that your knowledge is secure and safe.
Via leveraging (GCP) and Cloudflare, we be sure that our infrastructure meets the best safety requirements. GCP’s infrastructure is independently assessed for compliance with PCI DSS 3.2 necessities, including every other layer of accept as true with and safety to our internet hosting platform.
With those certifications and common audits in position, we guarantee you that your website is hosted on a safe, compliant platform that persistently meets essentially the most stringent {industry} requirements.
You’ll be able to be informed extra from our accept as true with web page.
Abstract
This tick list isn’t exhaustive however covers many very important sides of internet hosting safety. You’ll be able to know how your internet hosting supplier handles safety through specializing in key spaces like knowledge coverage, DDoS prevention, uptime tracking, and compliance.
Asking those questions is helping be sure that your small business is safe from not unusual threats and aligned with absolute best practices for knowledge safety and privateness.
Being proactive about safety offers you self assurance that your site is secure, permitting you to concentrate on rising your small business.
If you happen to consider Kinsta meets your safety wishes and also you’d like to be told extra about our pricing to search out the most productive plan for your small business, touch our gross sales crew.
The publish What to invite your internet host about safety: A tick list for industry house owners seemed first on Kinsta®.
WP Hosting