Are you in a position to offer protection to your virtual global from the rising risks on-line? With cyber threats turning into extra refined on a daily basis, preserving your information secure hasn’t ever been extra necessary.
On this article, we’re going to discover how Prison IP, an OSINT seek engine, assist you to keep one step forward of cybercriminals. We’ll give an explanation for what Prison IP is, the way it works, and why the usage of open-source intelligence (OSINT) is a game-changer for recognizing and preventing threats.
Whether or not you’re deep into cybersecurity or simply need to be sure that your on-line presence is protected, figuring out learn how to use equipment like Prison IP may just make the entire distinction.
Attending to Know Prison IP
Prison IP is an OSINT seek engine designed for cybersecurity duties, similar to assessing assault surfaces and figuring out attainable threats.
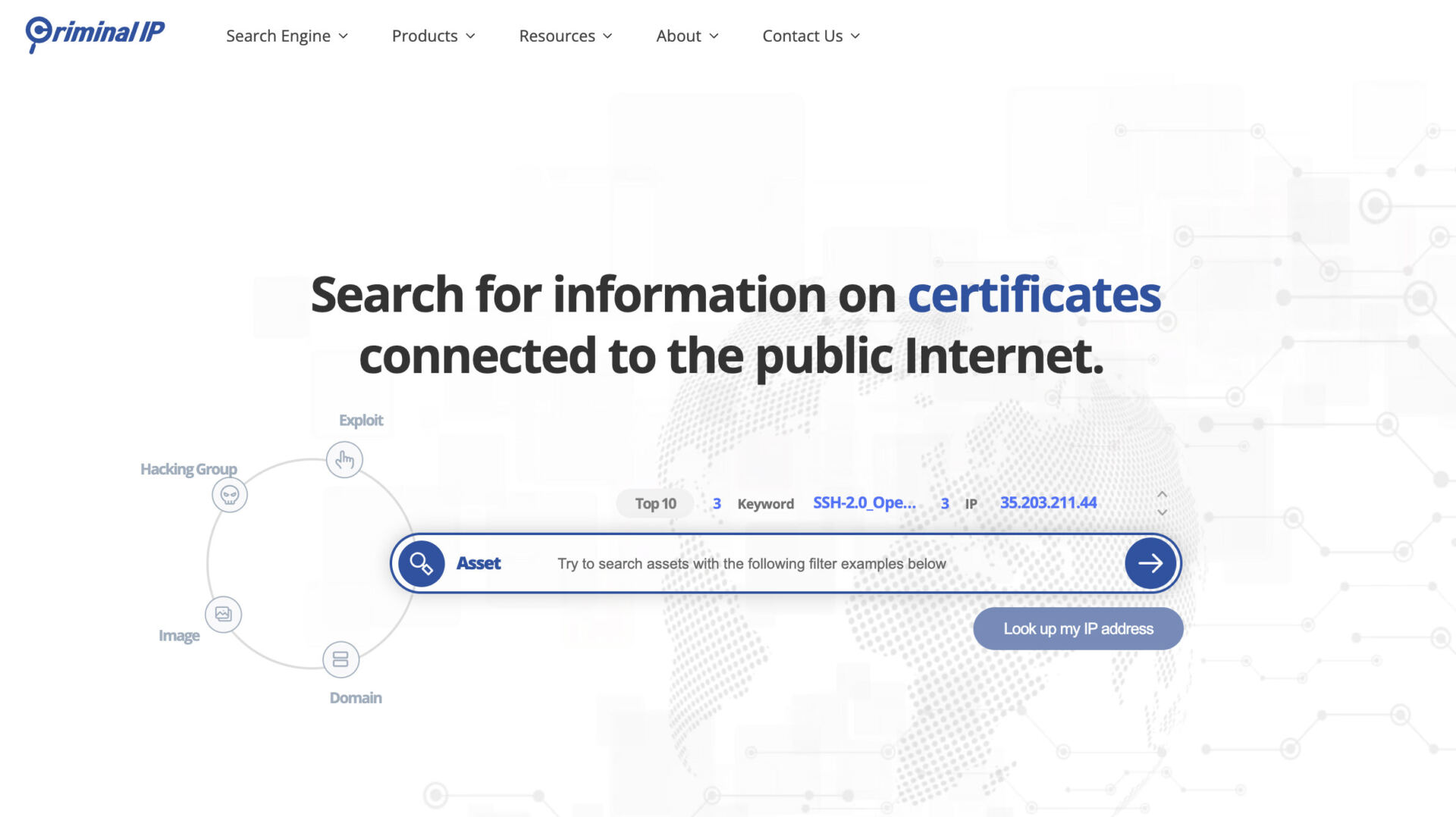

It ceaselessly gathers and updates information in real-time, the usage of AI era to pinpoint unhealthy IP addresses and domain names. The chance is then rated on a 5-level scale. The knowledge is arranged with filters and tags to make looking out simple. Moreover, it may be built-in with different equipment and techniques (e.g., Cisco, AWS Market, WordPress, Zabbix) the usage of an API for seamless integration.
Working out OSINT Seek Engines
To in reality perceive what Prison IP can do, one should first know what an OSINT seek engine is.
OSINT stands for Open Supply Intelligence, which comes to collecting and inspecting information from open assets just like the web, social media, and public data.
An OSINT seek engine is a device particularly designed to lend a hand customers in finding and analyze data this is publicly to be had throughout more than a few on-line assets.
Those search engines like google and yahoo are frequently utilized by cybersecurity mavens, investigators, newshounds, and researchers to discover a very powerful data, establish attainable threats, or disclose hidden main points.
They incessantly include complicated options that permit customers to go looking more than one platforms directly, follow particular filters, or even stay monitor of ongoing actions.
10 Causes Why OSINT Issues in Cybersecurity
The significance of Open Supply Intelligence (OSINT) in cybersecurity can’t be overstated, because it performs an important function in serving to organizations and execs establish and arrange threats, make stronger situational consciousness, and make knowledgeable selections.
Right here’s why it’s so a very powerful…
1. Figuring out and Tracking Threats
By way of tracking publicly to be had information—similar to social media, boards, and internet sites—cybersecurity groups can spot early indicators of attainable assaults, similar to discussions about vulnerabilities or deliberate movements. This permits them to take proactive defensive measures.
2. Assessing Vulnerabilities
Equipment that analyze open-source data are key in uncovering weaknesses in a company’s virtual infrastructure. This contains discovering uncovered servers, unsecured databases, and misconfigured techniques that may be exploited by means of attackers. Addressing those problems promptly can save you breaches.
3. Responding to Incidents
Within the tournament of a cybersecurity incident, collecting intelligence from publicly to be had assets is helping perceive the attacker’s strategies, equipment, and motivations. This knowledge is a very powerful for assessing the assault’s scope, figuring out compromised techniques, and crafting an efficient reaction technique.
4. Supporting Penetration Checking out
Right through the reconnaissance section of penetration trying out, collecting open-source information a couple of goal is helping simulate real-world assaults. This permits penetration testers to spot attainable weaknesses in defenses and recommend enhancements.
5. Managing Emblem and Popularity
Tracking public mentions of a emblem, merchandise, or workers can alert organizations to attainable threats like phishing websites, pretend social media profiles, or leaked information. This early caution is helping offer protection to and arrange the group’s recognition.
6. Making sure Compliance and Due Diligence
Open-source intelligence could also be treasured for making sure regulatory compliance. Tracking for information leaks, unauthorized disclosures, or any public data that would possibly point out non-compliance is very important. It’s similarly helpful in due diligence all over mergers, acquisitions, or partnerships, offering perception into the cybersecurity posture of attainable companions.
7. Bettering Situational Consciousness
By way of accumulating and inspecting information from more than a few assets, organizations acquire a broader view of the cybersecurity panorama. This advanced situational consciousness is helping them keep forward of rising threats, trade tendencies, and cybercriminal actions.
8. Collecting Intelligence Value-Successfully
Because the data comes from public assets, it’s incessantly extra cost-effective than different intelligence strategies. Organizations can accumulate treasured insights with no need dear assets or get admission to to limited information.
9. Supporting Legislation Enforcement and Investigations
Publicly to be had intelligence is extensively utilized by legislation enforcement businesses to accumulate proof and monitor legal actions. In cybersecurity, it is helping hint assault origins, establish perpetrators, and improve criminal movements in opposition to cybercriminals.
10. Managing Provide Chain Dangers
Tracking the provision chain for vulnerabilities or threats is every other essential software. Figuring out dangers related to third-party distributors or companions is helping offer protection to the group from attainable exploits.
What Prison IP Can Do?
Now, again to Prison IP, the OSINT seek engine. Prison IP gives tough equipment for exploring vulnerabilities and monitoring all forms of units hooked up to the web, together with IP addresses, domain names, IoT units, and business keep watch over techniques (ICS).
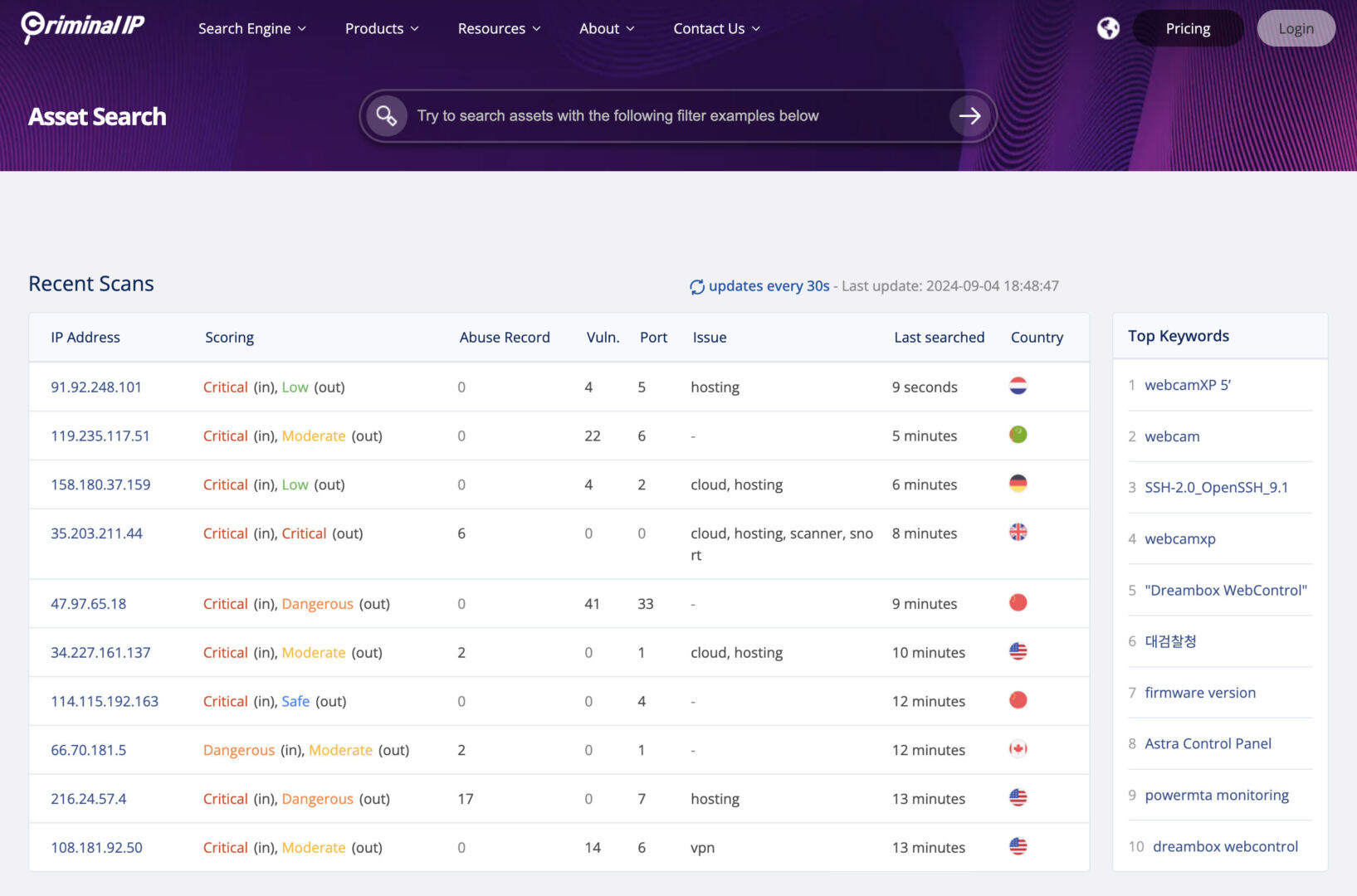
Right here’s a handy guide a rough have a look at what all of them do:
Seek Purposes:
| Asset Seek | Supplies chance scoring, related asset data, abuse historical past, and related vulnerability data to resolve the specter of a searched IP cope with. Then again, you’ll seek without delay for the provider title with a key phrase, or seek for the CVE quantity to search out the related IP cope with. |
| Area Seek | Scans area data in real-time to offer data, together with whether or not this is a phishing hyperlink, malicious hyperlink, and certificates validity, along side chance scoring. |
| Symbol Seek | Supplies symbol data for property susceptible to cyber threats when searched beneath more than a few stipulations similar to RDP, Phishing, Webcam, VNC, and RTSP. |
| Exploit Seek | Analyzes not unusual vulnerabilities and exposures (CVE) and offers detailed data, together with exact hijacking codes, according to provider. |
Intelligence Options:
| Banner Explorer | Supplies categorised danger intelligence on services similar to cryptocurrency, databases, and IoT units. |
| Vulnerability Intelligence | Provides main points on uncovered vulnerabilities, categorised by means of CVE ID and product title, helping in proactive tracking and control. |
| Statistics | Supplies statistical graphs of VPN, Proxy, Tor, scanner, and malicious IPs during the last 7 days, visualizing the standing of suspicious nameless IPs and providing pattern information. |
| Part Research | When acting a key phrase seek, filters will also be implemented for nation, provider, ASN, product title, port quantity, and favicon hash, permitting you to view statistics for each and every class. |
| Maps | Visualizes information geographically, appearing the places of IPs, domain names, or property, serving to to evaluate the scope of attainable assaults. |
The usage of Prison IP in Actual-International Eventualities
Prison IP is a device that you’ll get admission to via its API to assemble danger intelligence on any tool, server, or area hooked up to the web. It comes in handy in more than a few spaces of cybersecurity, similar to managing assault surfaces, penetration trying out, vulnerability and malware research, in addition to investigation and analysis.
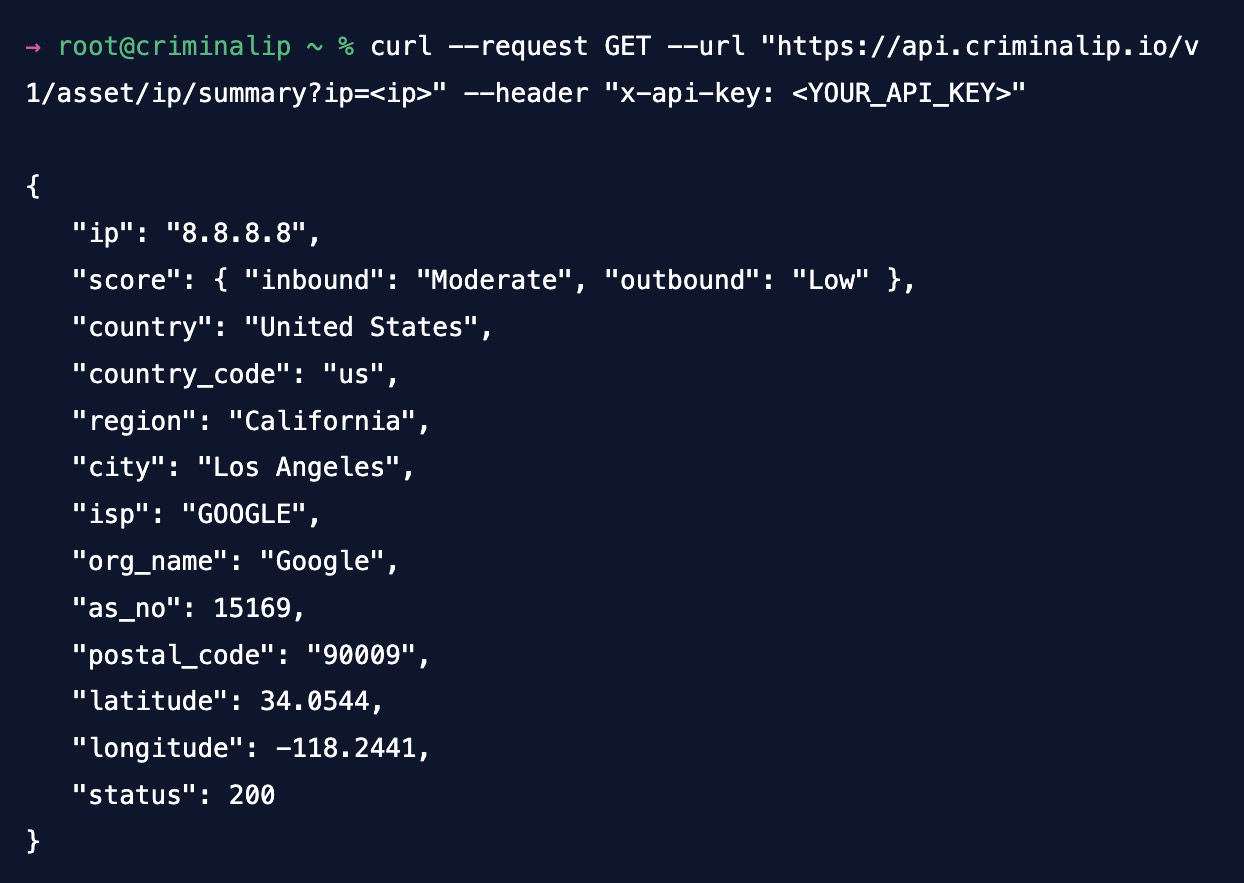
As an example, when a brand new vulnerability or ransomware is found out, Prison IP is helping you resolve what number of PCs or servers are in peril or already inflamed. You’ll be able to additionally take a look at if the IP addresses or domain names you might be the usage of are susceptible.
Moreover, Prison IP scans for malicious and phishing URLs generated by means of hackers in genuine time, permitting you to research threats with no need to have interaction with them without delay.
How the API Works
The Prison IP API makes it simple to combine those features into your personal techniques. By way of the usage of an API key for authentication, you’ll get admission to more than a few endpoints to research IP addresses, domain names, and URLs for attainable threats. Those endpoints supply key data like chance rankings, geolocation, and a historical past of malicious actions, all returned in JSON layout for clean integration.
The API makes use of easy HTTP requests and lets you automate danger detection, serving to you keep on most sensible of cybersecurity dangers.
To be told extra about integrating Prison IP’s API, take a look at their GitHub Reference web page or their Best possible Observe web page.
Prison IP’s Pricing
Closing however now not least, let’s check out the plans Prison IP gives and what sort of they charge:
- Loose: Rise up to 50 IP lookups and 100 seek question effects monthly.
- Lite: S$85/month, providing 100,000 IP lookups and one million seek question effects.
- Medium: S$454/month, offering one million IP lookups and 20,000,000 seek question effects.
- Professional: S$1,416/month, with limitless IP lookups and seek question effects, plus top class improve.
For extra main points, take a look at the pricing web page.
The publish Using Prison IP for Cyber Risk Searching seemed first on Hongkiat.
WordPress Website Development Source: https://www.hongkiat.com/blog/criminal-ip-osint-cybersecurity-threat-detection/