In February 2024, Gmail and Yahoo Mail started imposing new regulations to offer protection to electronic mail recipients and assist stay their inboxes more secure and no more spammy.
Those regulations require all electronic mail senders to stick to express pointers to verify electronic mail deliverability.
This complete information explains what those new necessities are and the way they have an effect on your online business.
We’ll quilt:
- Google & Yahoo’s New Electronic mail Sending Necessities
- Working out SPF, DKIM, and DMARC
- Electronic mail Verification Examples
- The use of Verification Equipment
- Highest Practices For Electronic mail Senders
- Further Issues and Helpful Data
Google & Yahoo’s New Electronic mail Sending Necessities
In October 2023, Gmail’s Safety & Believe Team Product Supervisor Neil Kumaran introduced on Google’s weblog that from February 2024 electronic mail senders would wish to authenticate their emails, permit for simple unsubscription (bulk senders), and keep underneath a reported unsolicited mail threshold to ensure that their emails to be dropped at Gmail addresses.
As those necessities at the moment are in impact, ignoring them will see your mail being routinely rejected or despatched to the recipient’s unsolicited mail folder.
In line with Neil, even supposing Gmail’s detection equipment save you 99.9% of unsolicited mail, phishing and malware from achieving inboxes and block virtually 15 billion undesirable emails each day, the provider is now going through ever extra advanced threats than it did for the reason that provider introduced in April of 2004.
As Neil states on Google’s weblog…
“As elementary because it sounds, it’s nonetheless every now and then not possible to make sure who an electronic mail is from given the internet of antiquated and inconsistent techniques on the net.”
The brand new electronic mail sending necessities are designed to assist customers stay their inbox more secure and extra spam-free.
This initiative to battle fraudulent or spammy electronic mail by means of putting extra stringent necessities on electronic mail senders isn’t coming only from Google, alternatively. Business companions like Yahoo have additionally joined in to paintings along Google and the remainder of the e-mail neighborhood to make those new necessities business usual and a elementary electronic mail hygiene apply.
Yahoo’s electronic mail sender highest practices incorporates equivalent suggestions to Google’s and features a hyperlink to a a complete information on Senders Highest Commonplace Practices from the Messaging, Malware and Cellular Anti-Abuse Running Team (M3AAWG), a company dedicated to serving to industries combat and save you on-line abuse.
This record is geared toward any individual concerned within the supply and compliance of digital communications, together with advertising and marketing and control staff. It’s price downloading and covers the most recent and best really useful practices for sending business digital messages.
So, what are those new necessities and the way do they have an effect on your online business?
Necessarily, the primary necessities can also be summarized as follows:
- Your unsolicited mail criticism price must be underneath 0.3%.
- Authentication the use of SPF, DKIM, and DMARC (Bulk electronic mail senders) is now required.
- You should have a one-click unsubscribe possibility and take away other folks inquiring for to be unsubscribed out of your checklist inside 1-2 days (Bulk electronic mail senders).
Further necessities for all electronic mail senders come with:
- Making sure that sending domain names or IPs have legitimate ahead and opposite DNS information, additionally known as PTR information.
- Use a TLS connection for transmitting electronic mail.
- Structure messages in line with the Web Message Structure usual, RFC 5322
There are further necessities for bulk electronic mail senders.
You’ll learn Neil Kumaran’s submit right here and try Google’s electronic mail sender pointers and Yahoo’s electronic mail sender highest practices to learn to effectively ship emails to non-public Gmail and YahooMail accounts.
Working out SPF, DKIM, and DMARC
Imposing SPF, DKIM, and DMARC protocols complements electronic mail deliverability, safeguards sender popularity, and guarantees that emails succeed in recipients’ inboxes securely.
When you don’t seem to be aware of SPF, DKIM, and DMARC, right here’s an outline:
SPF
SPF (Sender Coverage Framework) is a protocol that verifies sender authenticity by means of checking if an electronic mail originated from a certified server.
It guarantees the legitimacy of electronic mail senders by means of validating a sender’s identification thru cross-referencing the IP deal with of the sending mail server with a predetermined checklist of licensed sending IP addresses contained throughout the DNS file.
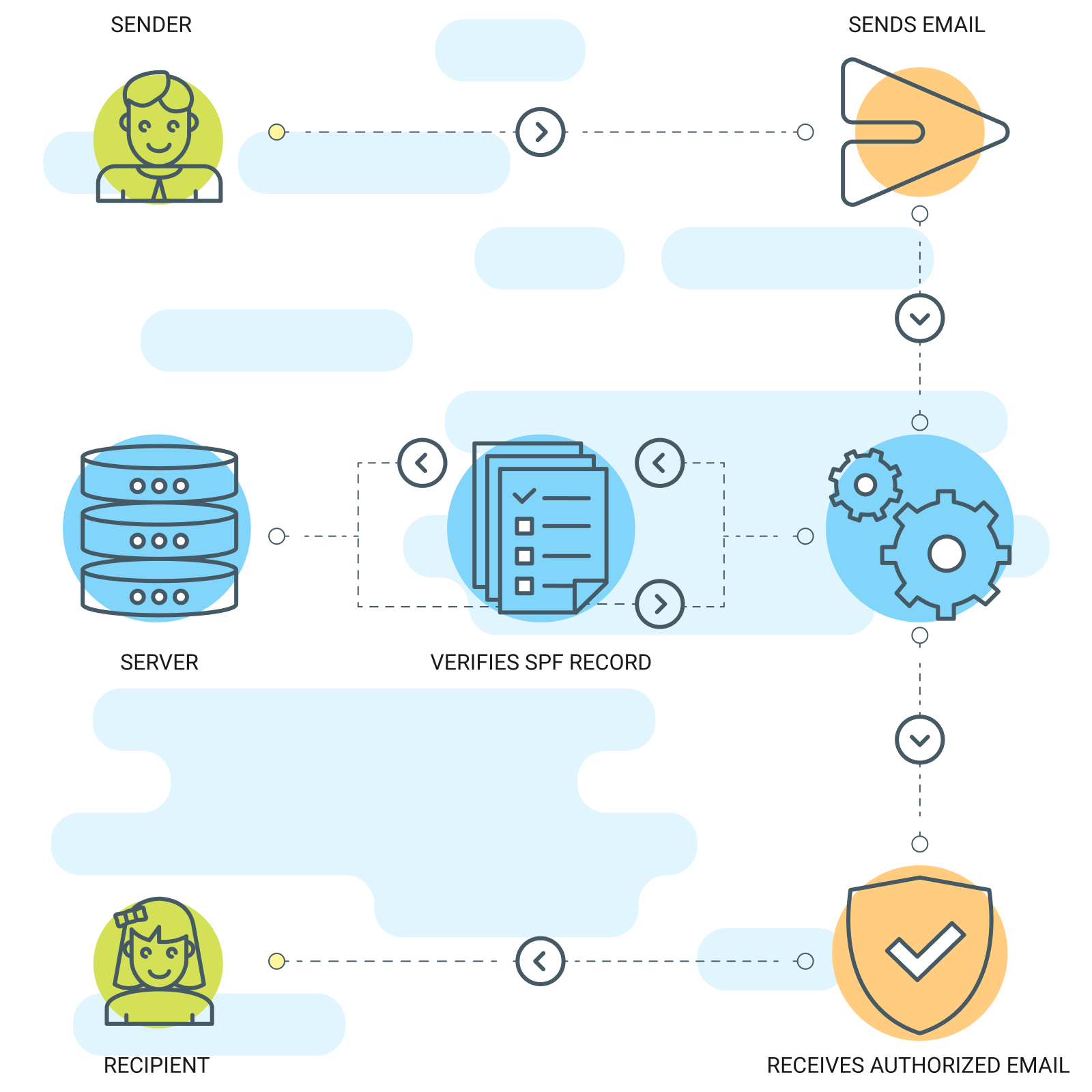
DNS information necessarily act as a listing that maps domains to their respective IP addresses and will come with directions on dealing with requests directed against that area.
By way of verifying the authenticity of the sender’s identification in opposition to licensed sending IP addresses indexed within the DNS file for a site, SPF is helping to stop electronic mail spoofing and enhanced deliverability by means of lowering the possibility of emails being blacklisted or marked as unsolicited mail.
Listed below are the stairs concerned about developing an SPF file for electronic mail authentication:
1. Acquire Data: Acquire the IP addresses of all servers licensed to ship emails on behalf of your area. This comprises your personal mail servers, third-party electronic mail provider suppliers, and every other servers used for sending emails.
2. Establish Sending Domain names: Make a listing of all domain names used to ship emails, even supposing now not these days lively. This prevents area spoofing makes an attempt.
3. Create SPF Report Syntax:
-
- Get started with the model tag:
v=spf1 - Upload licensed IP addresses: e.g.
ip4:192.0.2.0 - Come with third-party senders:
come with:thirdparty.com - Specify SPF coverage:
-all(laborious fail) or~all(comfortable fail).
- Get started with the model tag:
After following the above steps, your SPF file must appear to be the instance proven beneath:
v=spf1 ip4:192.0.2.0 come with:thirdparty.com -all
Notice: SPF information must be underneath 255 characters and restricted to not more than ten come with statements.
4. Submit SPF Report to DNS: Get right of entry to your DNS control console supplied by means of your area registrar or website hosting supplier, upload a brand new TXT file together with your area’s hostname and the SPF file syntax, and save the adjustments.
5. Take a look at SPF Report: Use SPF take a look at equipment (e.g. EasyDMARC’s SPF Report Checker) to test if the SPF file is provide or now not and be sure that all legit sending IP addresses are indexed and accurately formatted.
DKIM
DKIM (DomainKeys Recognized Mail) is an electronic mail authentication means that provides a virtual signature to outgoing emails.
This signature is validated by means of the recipient’s mail server, making sure the e-mail’s integrity and authenticity. DKIM prevents electronic mail tampering and strengthens electronic mail deliverability by means of lowering the danger of emails being flagged as unsolicited mail or phishing.
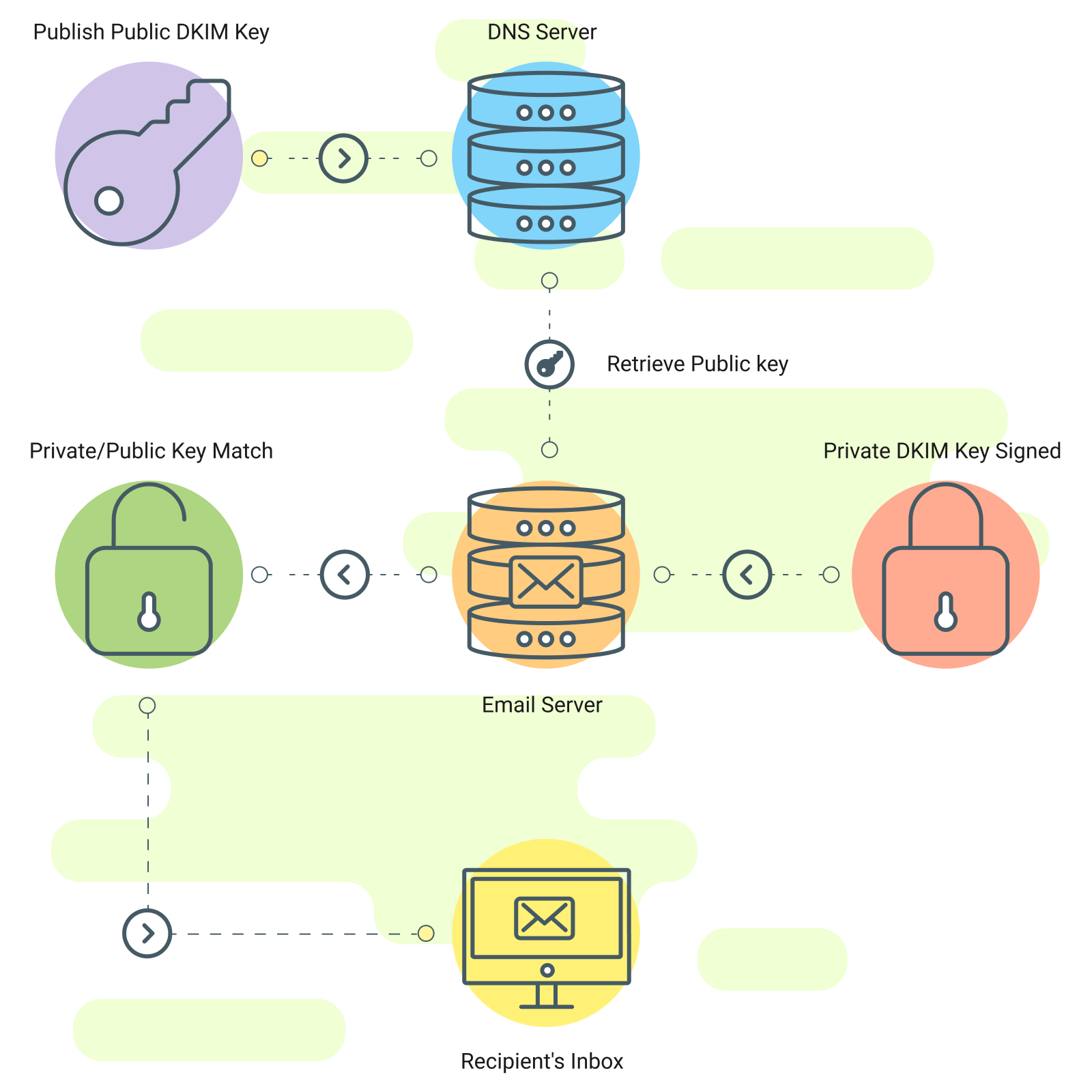
DKIM is sort of a virtual signature for emails, some way for the sender (you) to end up they in point of fact despatched the e-mail and that it hasn’t been modified by means of any individual in between.
A DKIM Signature Header generally comprises a number of parts represented by means of tag=price pairs.
Right here’s an instance that illustrates the very important elements important for electronic mail authentication thru DKIM:
DKIM-Signature: v=1; a=rsa-sha256; c=comfortable/comfortable; d=instance.com; s=dkim1; h=From:To:Matter:Date; bh=XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX; b=YYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYY
Clarification of each and every component:
v=1: Model of the DKIM specification getting used.a=rsa-sha256: The cryptographic set of rules used to generate the signature.c=comfortable/comfortable: Canonicalization strategies used for the header and frame of the e-mail.d=instance.com: The area that owns the DKIM key pair.s=dkim1: The DKIM selector, which signifies the particular key used for signing.h=From:To:Matter:Date: Checklist of header fields incorporated within the signature.bh=XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX: The hash of the frame of the e-mail.b=YYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYYY: The real virtual signature generated the use of the personal key related to the selector.
Listed below are the stairs concerned about making a DKIM file:
1. Generate DKIM Keys: Use a DKIM key generator instrument supplied by means of your electronic mail provider supplier or a third-party provider (see checklist beneath). This generates a private and non-private key pair.
2. Submit Public Key to DNS:
-
- Log in for your DNS control console supplied by means of your area registrar or website hosting supplier.
- Navigate to the DNS settings to your area.
- Upload a brand new TXT file with the DKIM selector because the subdomain identify and the general public key because the file price. The selector is normally supplied by means of your electronic mail provider supplier and is particular for your DKIM configuration.
Instance DKIM file:
selector._domainkey.instance.com. IN TXT "v=DKIM1; okay=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQC2h9gFo3... (lengthy string)"
3. Check DKIM Report: After including the DKIM file, check its correctness the use of DNS search for equipment and be sure that the TXT file incorporates the proper DKIM selector and public key.
4. Take a look at DKIM: Ship take a look at emails out of your area and check that they move DKIM authentication assessments the use of electronic mail authentication trying out equipment.
Listed below are some equipment you’ll use to generate DKIM keys:
- DKIMCORE.org
- DKIM Report Generator by means of EasyDMARC
- DKIM Generator Wizard by means of SocketLabs
DMARC
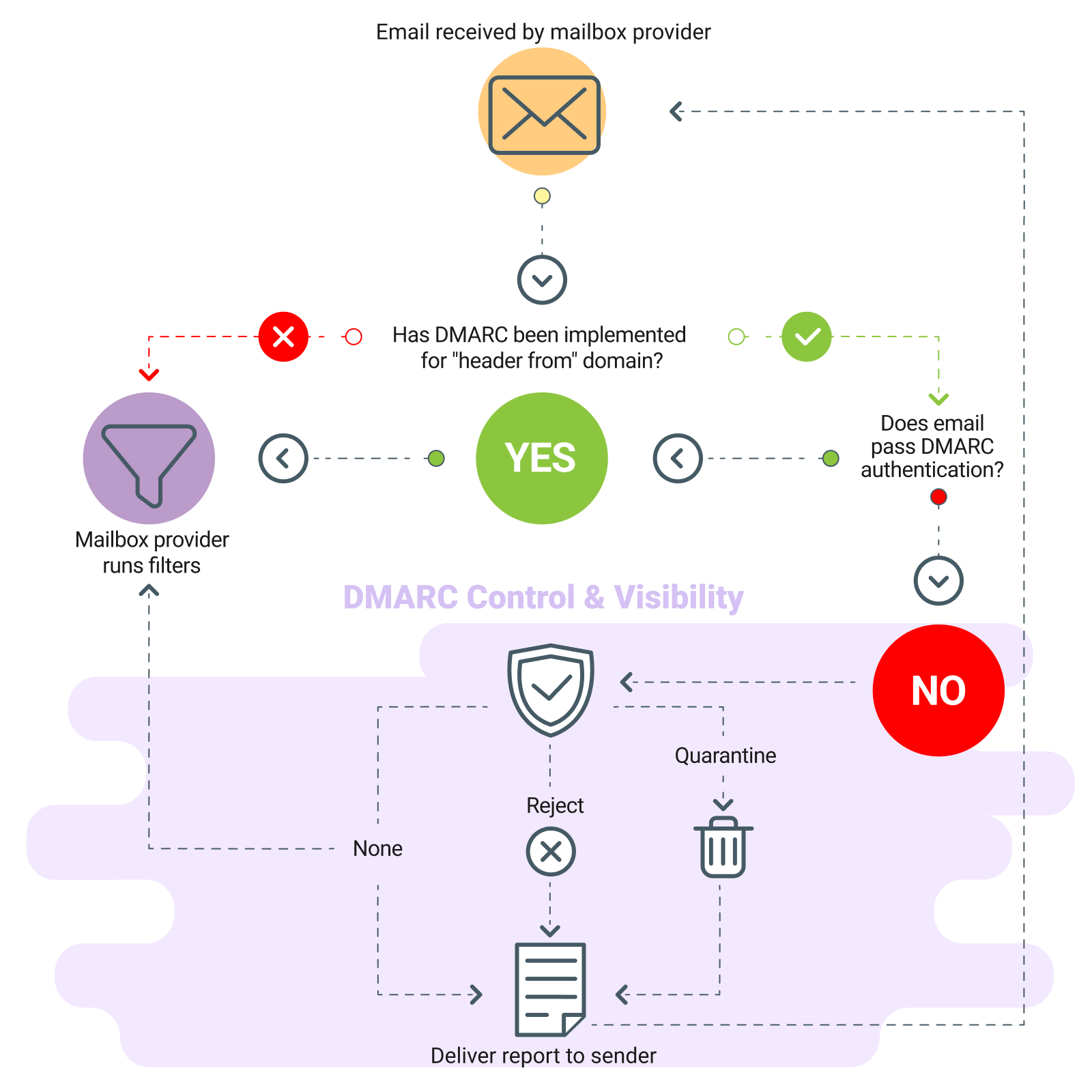
DMARC (Area-based Message Authentication, Reporting, and Conformance) is a protocol that is helping offer protection to electronic mail domain names from getting used for phishing, spoofing, and different malicious actions, and builds on SPF and DKIM to offer further electronic mail authentication and reporting functions.
DMARC is helping to be sure that the emails you ship are in point of fact from you. If anyone tries to faux your electronic mail deal with, DMARC is helping block the ones phony messages from achieving others, protecting your electronic mail popularity secure and sound.
DMARC:
- Improves electronic mail deliverability by means of permitting senders to observe and implement electronic mail authentication insurance policies.
- Permits area house owners to specify a dealing with coverage for emails that fail SPF and DKIM assessments, bettering transparency and safety, and lowering spoofing and phishing makes an attempt.
- Permits area house owners to obtain signals when unauthorized events misuse the area for electronic mail spoofing, protective their emblem’s popularity.
To move DMARC’s standards, SPF and DKIM should be correctly configured for the e-mail’s From area. The From area should then fit the authenticated area by means of SPF or DKIM.
Easy methods to enforce DMARC
1. Outline DMARC Coverage: Make a decision at the DMARC coverage you wish to have to implement. DMARC gives 3 coverage choices:
-
- None: Tracking mode simplest, no movements are taken if an electronic mail fails DMARC.
- Quarantine: Suspicious emails are despatched to the unsolicited mail/junk folder.
- Reject: Suspicious emails are rejected outright.
2. Generate DMARC Report: Create a DMARC TXT file together with your selected coverage. Use the next syntax:
_dmarc.instance.com. IN TXT "v=DMARC1; p=none; rua=mailto:your@electronic mail.com; ruf=mailto:your@electronic mail.com"
-
- Exchange
instance.comtogether with your area. v=DMARC1: Signifies the DMARC model.p=none/quarantine/reject: Defines the coverage.rua: Specifies the e-mail deal with to obtain combination experiences.ruf: Specifies the e-mail deal with to obtain forensic experiences.
- Exchange
3. Submit DMARC Report to DNS: Log in for your DNS supplier’s dashboard.
-
- Navigate for your area’s DNS control segment.
- Upload a brand new TXT file with the
host _dmarcand the price because the DMARC file you generated.
4. Check DMARC Report: Use DNS search for equipment to verify the DMARC file is accurately revealed and propagated.
5. Track Experiences: Frequently take a look at the mixture and forensic experiences despatched to the e-mail addresses specified within the DMARC file. Those experiences supply insights into electronic mail authentication screw ups and assist fine-tune your DMARC coverage.
Notes:
- Be very cautious when making a DMARC file, as any misconfiguration will negatively affect your electronic mail supply. We advise following those pointers from Google when beginning out with DMARC.
- Make certain that SPF and DKIM are authenticating emails for no less than 48 hours BEFORE enabling DMARC.
Listed below are some loose equipment you’ll use to create, check and validate DMARC information:
- DMARC Equipment by means of dmarcian.
- DMARC Report Look up and Checker by means of EasyDMARC
- DMARC Digests – When you arrange a DMARC reporting deal with, the use of your own or industry deal with isn’t really useful, as your inbox can be flooded with unintelligible emails. As an alternative, believe signing up for a DMARC reporting instrument to be sure that you’ve gotten correctly authenticated the entire equipment you utilize to ship electronic mail.
Electronic mail Verification Examples
Now that we’ve got outlined what SPF, DKIM, and DMARC imply, let’s have a look at some precise examples of those protocols in motion, so you’ll higher perceive why your emails might or is probably not achieving their supposed recipients.
Emails Now not Achieving Recipients
First up, let’s have a look at an glaring unsolicited mail electronic mail despatched to a Gmail deal with. This may assist us know how Gmail and different electronic mail suppliers routinely filter junk electronic mail.
Right here’s an electronic mail despatched to my private Gmail deal with that by no means even made it to my inbox. Gmail filtered it and despatched it at once to my SPAM folder.
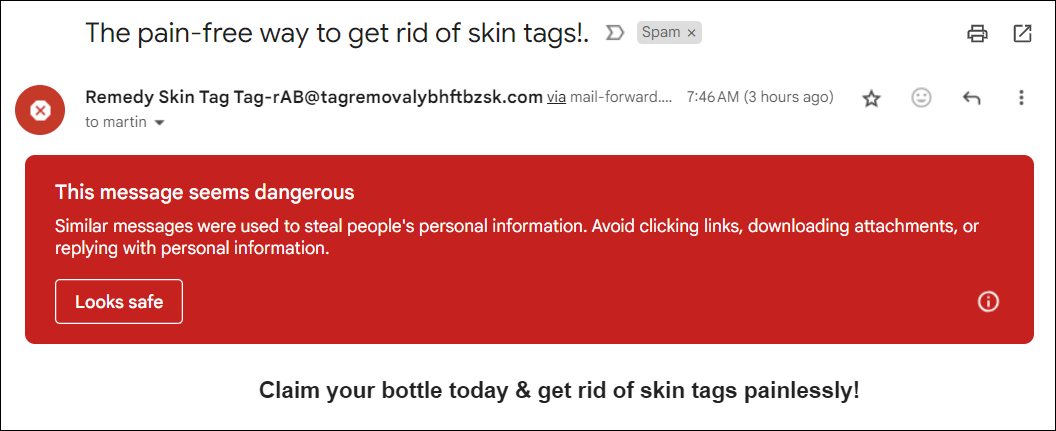
Let’s forget about the truth that that is an glaring unsolicited mail electronic mail and have a look at the e-mail header to look why Gmail’s automatic equipment detected and flagged it as unsolicited mail.
To do that, view the e-mail on your Gmail account (don’t click on on any hyperlinks within the electronic mail, after all!), click on at the vertical ellipsis icon, and choose Display unique from the menu choices …
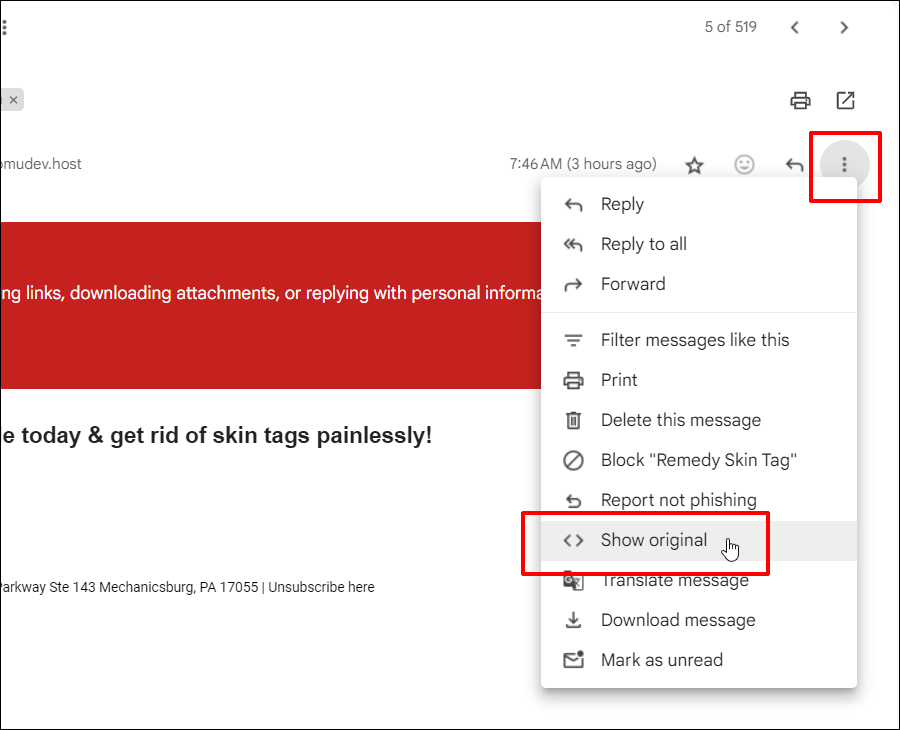
As you’ll see, this electronic mail didn’t meet Gmail’s DKIM coverage necessities.
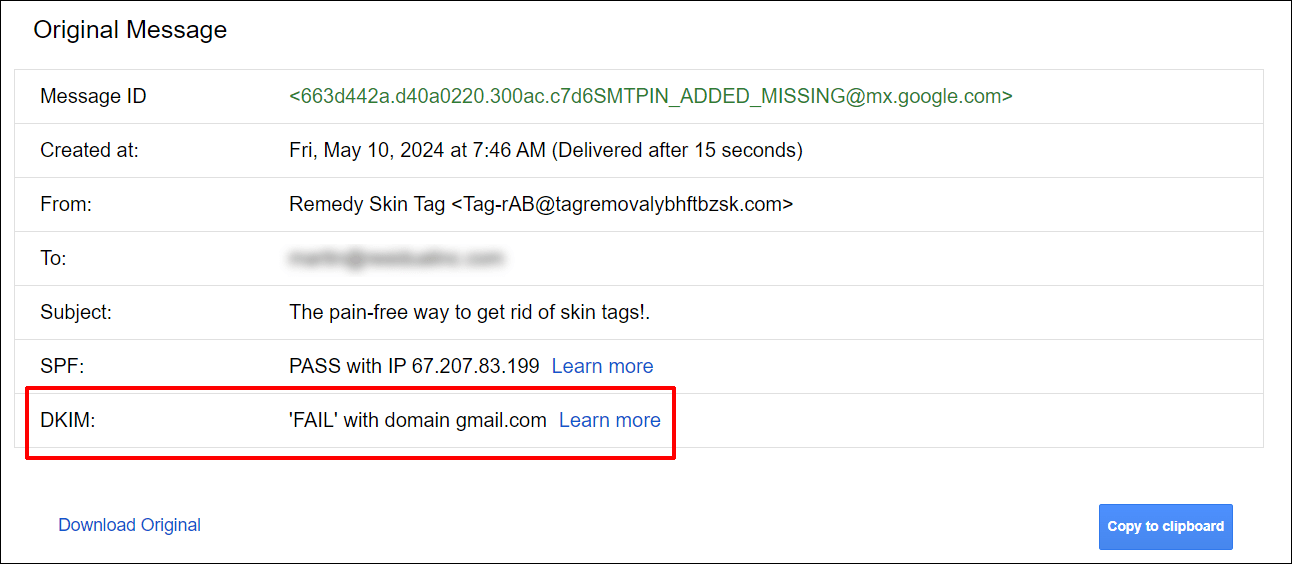
Compliant Emails
For comparability, right here’s the header of an electronic mail despatched to my industry Gmail deal with by means of a compliant sender. As you’ll see, this corporate has met all of Gmail’s necessities for secure electronic mail supply.
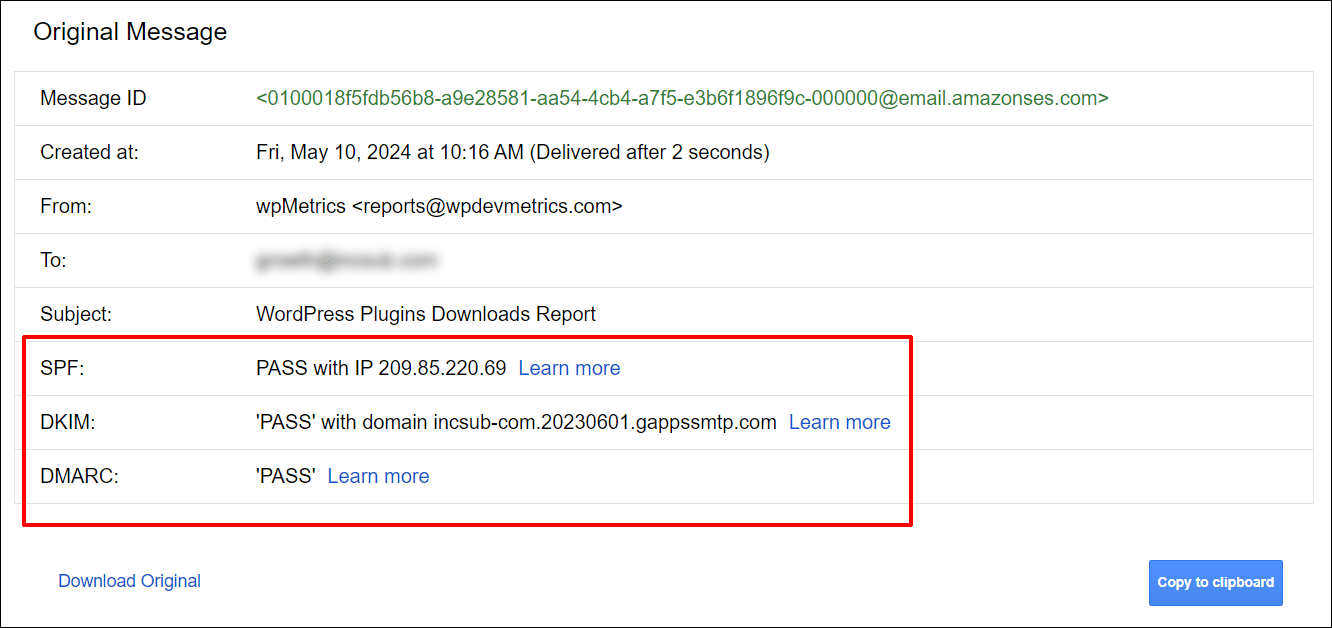
The use of Verification Equipment
As discussed previous, there are a variety of significant equipment you’ll use to test and/or troubleshoot whether or not your electronic mail area (or the e-mail area of a consumer or third-party provider) meets the desired protocols compliance with electronic mail sender pointers.
Take a look at SPF, DKIM & DMARC
For the examples on this segment, we’ll use the loose equipment from dmarcian.com.
Head on over to dmarcian’s loose equipment segment, and click on on their Area Checker instrument…
Input the e-mail area identify into the sector (simplest the area, no deal with@) and click on Take a look at Area …
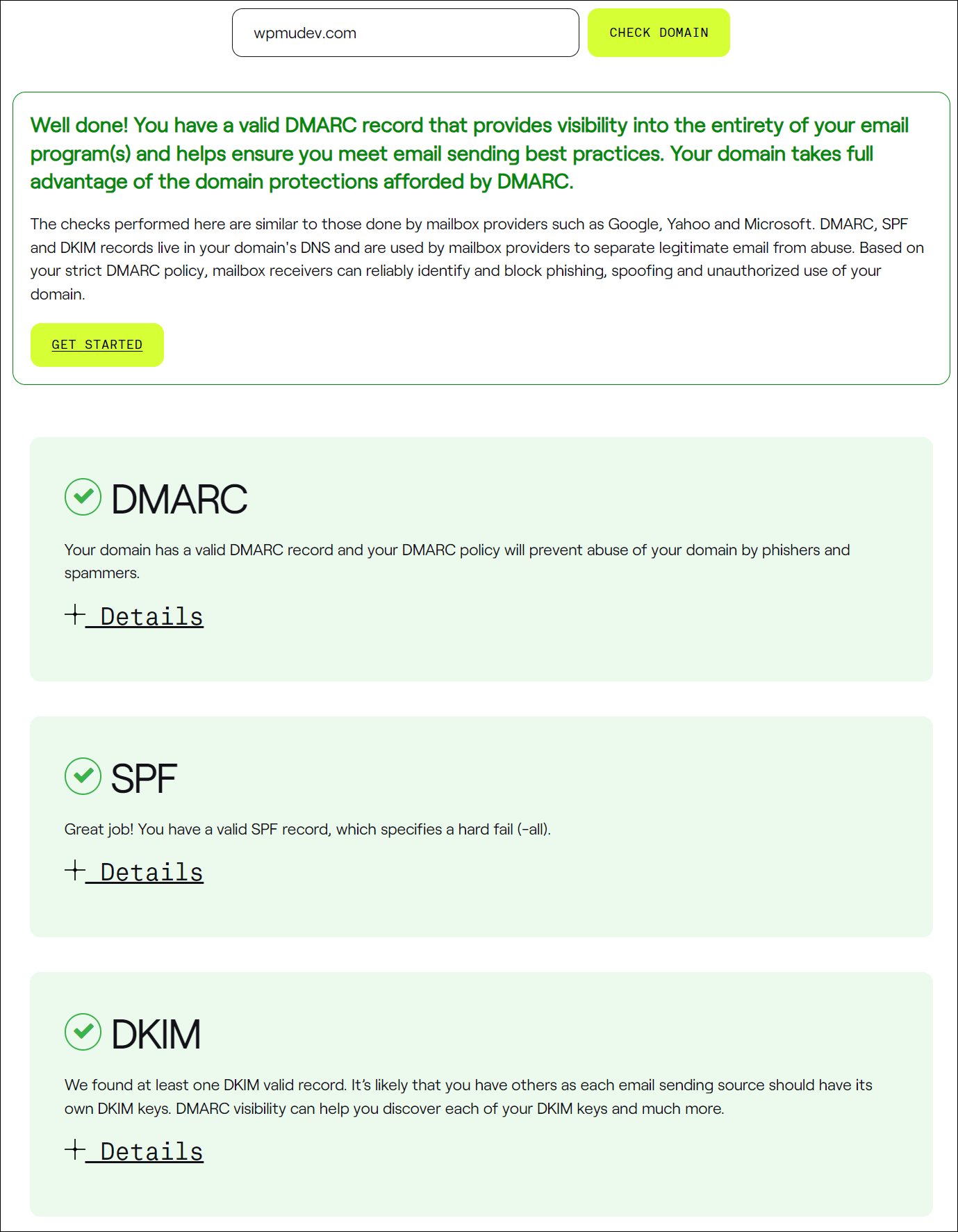
The instrument plays assessments very similar to the ones achieved by means of mailbox suppliers like Google, Yahoo, and Microsoft and shows effects that display if the e-mail area’s information meet SPF, DKIM, and DMARC necessities or now not.
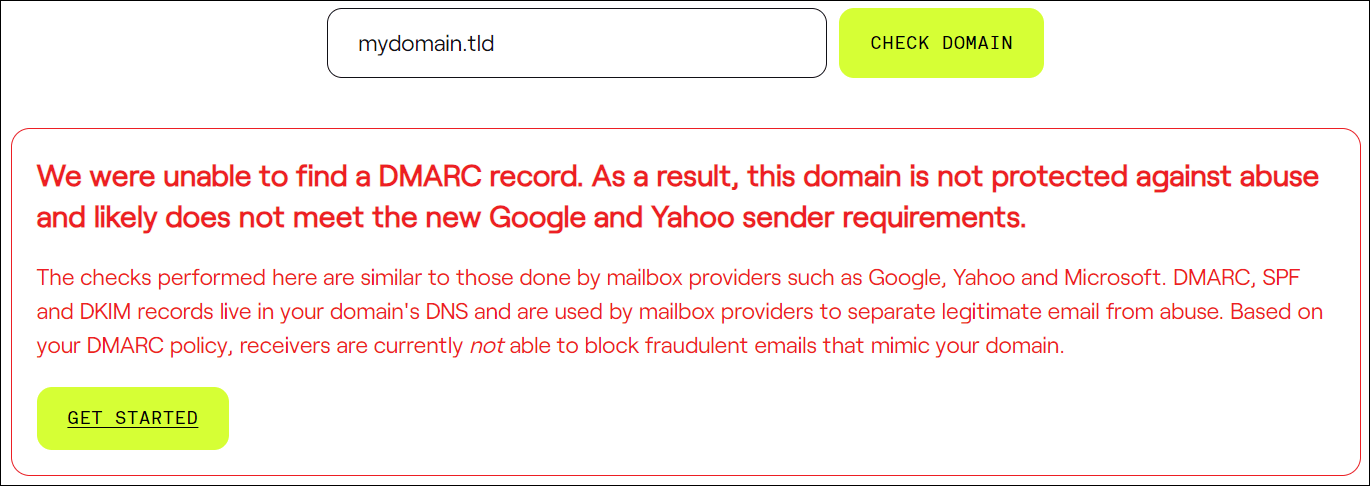
If an electronic mail area fails to fulfill the assessments, you’ll see a outcome very similar to the only proven beneath.
On occasion, you can get a message very similar to the only proven beneath. The message beneath infers that your emails meet the take a look at and can nonetheless get delivered, however you might need to use the corporate’s products and services to verify complete compliance.
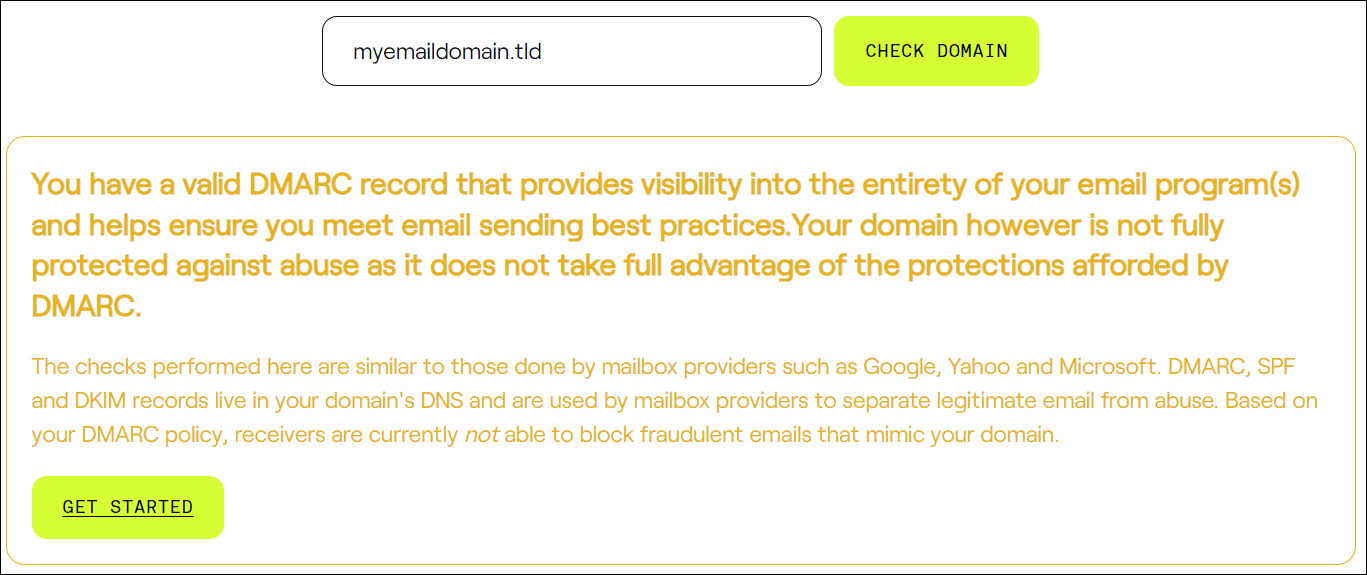
Right here’s another helpful tip to remember should you run a take a look at to your electronic mail domain names and get a DKIM take a look at outcome as proven within the screenshot beneath…
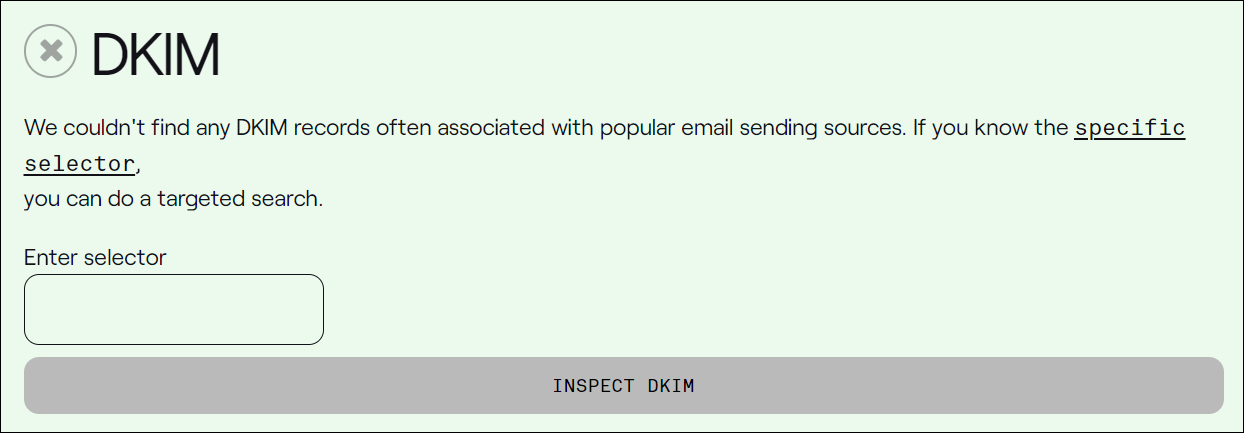
Within the above take a look at, the instrument couldn’t to find DKIM information for the e-mail area as a result of there’s a lacking selector. A selector is in most cases incorporated within the DKIM file when a compliant electronic mail is shipped.
To discover a selector to finish this take a look at, do the next:
- Fan the flames of your electronic mail account and to find an electronic mail despatched by means of the area you might be checking. On this instance, we’ll use Gmail.
- Click on at the vertical ellipsis icon, and choose Display unique from the menu choices
- Scroll down previous the Web headers segment till you get to the jumble of code.
- Search for the
s=a part of the DKIM Signature Header. That is your selector
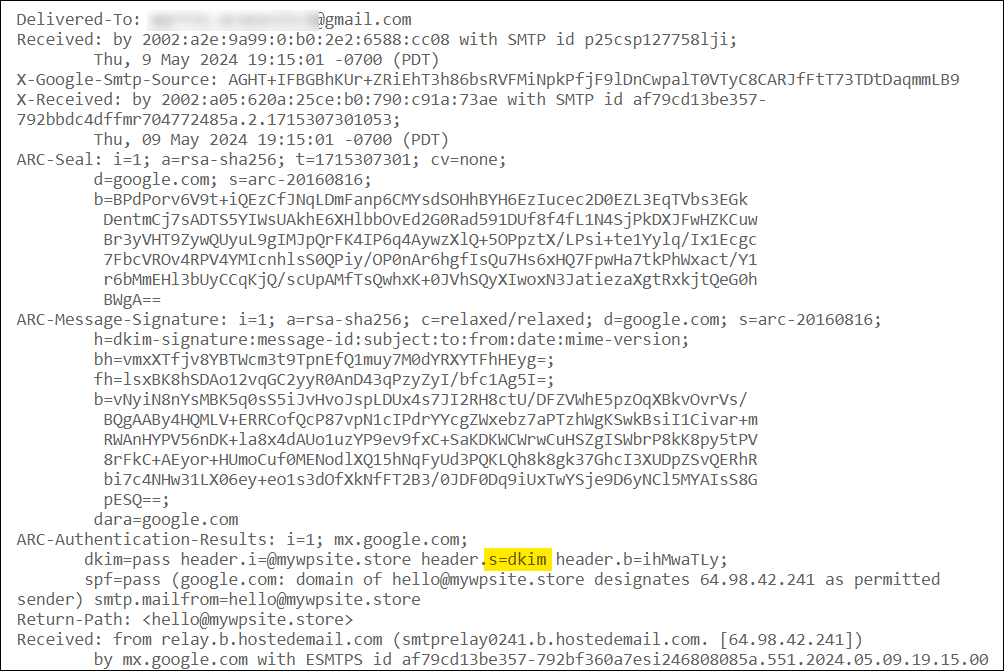
Reproduction the selector portion and paste it into the DKIM checking instrument, then click on the Investigate cross-check DKIM button.

That are meant to repair it and get your electronic mail to move the DKIM take a look at.
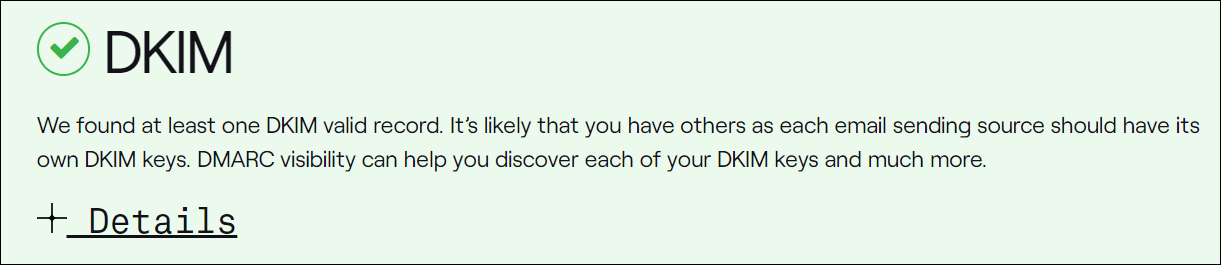
Click on the Main points hyperlink to view extra information about the consequences.
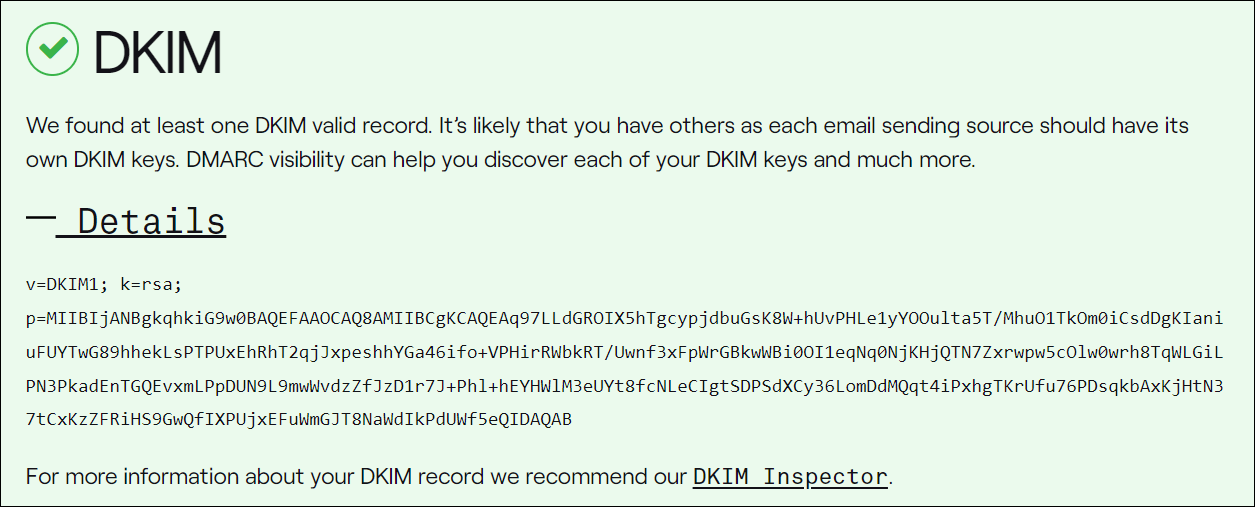
Take a look at PTR
A DNS pointer file, abbreviated as PTR, serves to hyperlink an IP deal with with its corresponding area identify. In contrast to the ‘A’ file, which maps domains to IP addresses, the PTR file plays the opposite serve as by means of associating IP addresses with domains.
To test that sending domain names or IPs have legitimate ahead and opposite DNS information as required, first find and duplicate the sending electronic mail area’s IP deal with within the electronic mail header …
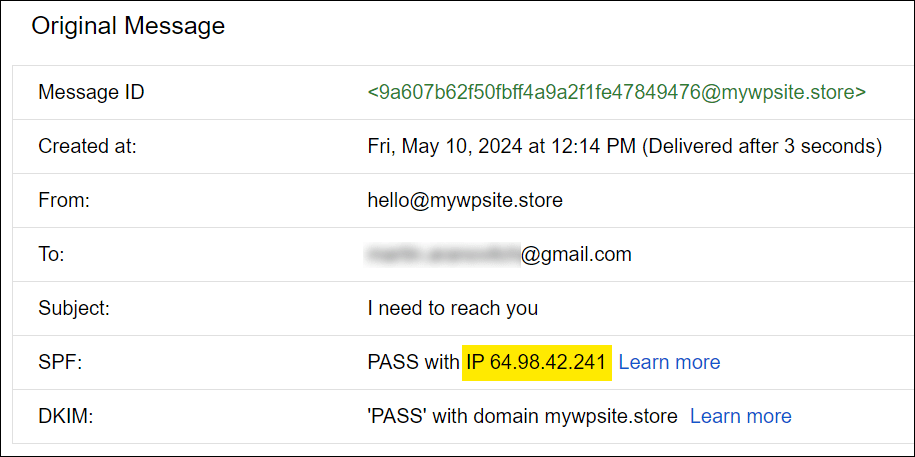
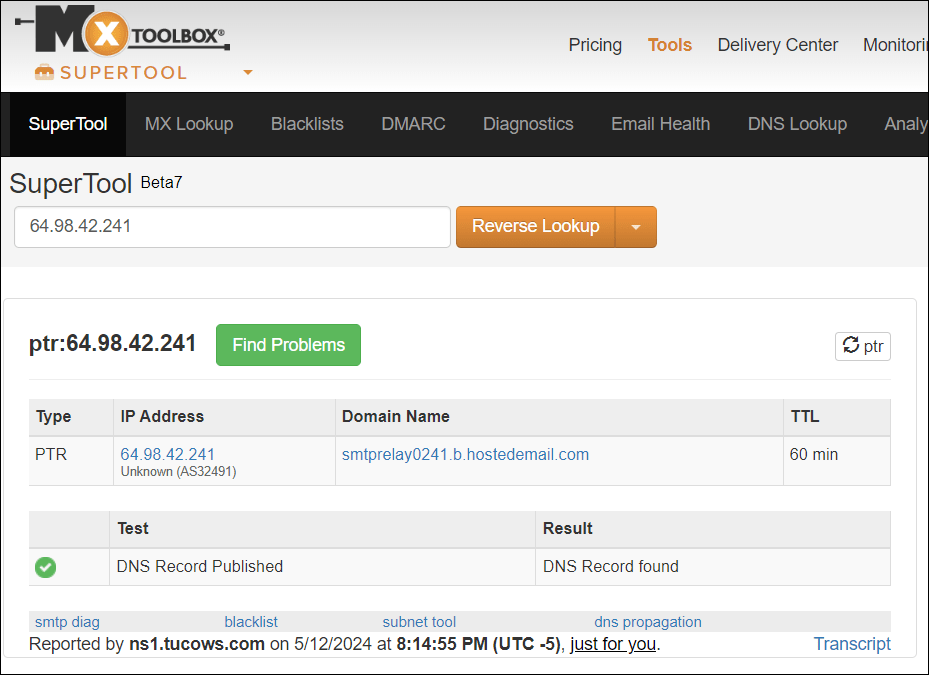
Then paste it right into a Opposite DNS search for instrument, like MXToolbox.com to test if the PTR is legitimate …
Whilst the above assessments offers you the proper knowledge, we additionally counsel trying out your electronic mail for spammyness. This may assist to verify optimum deliverability to your emails.
We advise the use of a provider like Mail Tester (additionally they have an SPF & DKIM checking instrument).
Confidently, this information has given you a elementary grab of what SPF, DKIM, and DMARC imply and find out how to use equipment to test the validity of electronic mail domain names and troubleshoot attainable problems.
When you use (or plan to make use of) WPMU DEV’s Webmail or Electronic mail Webhosting products and services, then take a look at our information on find out how to optimize electronic mail deliverability the use of WPMU DEV’s electronic mail products and services.
Highest Electronic mail Sending Practices
When you plan to do any more or less bulk mailing, right here’s an outline of key electronic mail sending practices to practice to stick compliant with the brand new pointers:
- Subscriptions: Most effective ship emails to people who have opted in. In case you are a professional bulk electronic mail sender, you’ll use a loose instrument like Google’s Postmaster Equipment to keep away from unsolicited mail markings and steadily get admission to information and diagnostics about Gmail supply mistakes, unsolicited mail experiences, comments loop, and extra to be sure that any criticism charges stay underneath 0.3% .
- Subscription Control: Permit one-click unsubscribe for environment friendly opt-outs. Permit recipients to check and unsubscribe from particular mailing lists.
- Message Formatting: Structure emails in line with RFC 5322 and HTML requirements. Steer clear of hiding content material and make sure transparent sender knowledge.
- Sending Pointers: Authenticate emails with SPF and DKIM. Take care of constant sending IPs and categorize messages. Use a TLS connection for transmitting electronic mail.
- Steer clear of Sending Practices: Don’t combine content material sorts, impersonate others, or acquire electronic mail lists.
- Build up Sending Quantity Slowly: Regularly build up quantity and track supply metrics.
- Particular Issues: Ensure that compliance with pointers, particularly for third-party suppliers.
- Associate Advertising and marketing & Phishing Workouts: Frequently track associates and keep away from sending take a look at phishing emails.
For extra detailed electronic mail sender pointers, see: Google Assist: Electronic mail Sender Pointers
Further Issues & Helpful Data
Protecting all there’s to find out about electronic mail deliverability is past the scope of this newsletter. Then again, we concept we would come with some further useful knowledge right here to save lots of you hours of study.
Bulk Emailing
Right here are a few things to remember in you intend to do any bulk emailing:
- Spoofed emails rely towards the majority sender prohibit of five,000. In line with Yahoo, “Spoofed emails will rely towards the mail we have a look at for enforcement. If in case you have a spoofing drawback, you must be enforcing a DMARC enforcement coverage (p=quarantine or p=reject) regardless.”
- Subdomains also are matter to the necessities. Non-compliant emails despatched from the subdomain of an organizational stage area this is matter to DMARC verification can be impacted.
Misconceptions about SPF (Sender Coverage Framework)
Working out SPF’s position in electronic mail authentication is necessary, however the protocol additionally has obstacles. Listed below are some fashionable misconceptions about SPF:
- SPF will totally offer protection to my area from spoofing: SPF does now not completely offer protection to the sender’s deal with visual to the consumer. It verifies the area’s authorization however doesn’t protected the sender’s deal with. Use DMARC to offer protection to visual domains from spoofing.
- Imposing SPF is enough to save you all spoofing and phishing makes an attempt: Whilst SPF is a an important measure, it’s not a whole answer in opposition to spoofing and phishing. Different electronic mail authentication strategies (e.g. DMARC) are important for complete coverage.
- Together with an organization’s SPF file in emails guarantees right kind authentication: Firms every now and then mistakenly instruct shoppers to incorporate their SPF file. Then again, this won’t successfully authenticate emails and can result in misconfigurations.
Misconceptions about DKIM (DomainKeys Recognized Mail)
As with SPF, it’s additionally necessary to grasp the position DKIM performs in getting your emails despatched out and delivered, however there are some misconceptions to concentrate on:
- Encryption False impression: Opposite to fashionable trust, DKIM doesn’t encrypt emails. As an alternative, it makes a speciality of verifying message integrity thru hashes underneath “bh” and “b” tags, offering coverage in opposition to amendment and replay assaults, albeit simplest in part safeguarding in opposition to identification robbery and forgery. A a hit DKIM verification signifies the sender’s authorization and guarantees message content material integrity all over transit.
- Forgery Fallacy: There’s a false impression that DKIM signatures can also be solid since their main points are publicly to be had in DNS information. Then again, DKIM is determined by a Public Key Infrastructure (PKI) with a couple of keys – private and non-private. Whilst the general public secret’s out there in DNS information, the personal key is living securely at the electronic mail provider supplier’s server, making sure message authenticity. Subsequently, DKIM signatures can’t be solid as the personal secret’s stored confidential and only used for message signing.
- Unsolicited mail Resolution Phantasm: Whilst DKIM aids in verifying sender authorization and message integrity, it doesn’t supply a definitive way to unsolicited mail. Whilst it reduces the possibility of spammers the use of solid or stolen electronic mail addresses, it doesn’t save you them from buying domain names and putting in place DKIM information to proceed their actions. Because of this, this will inadvertently legitimize unsolicited mail to some degree. Then again, unique area utilization can mitigate phishing assaults, bettering electronic mail safety in opposition to malicious makes an attempt, reminiscent of fraudulent emails purportedly from legit firms.
For the most recent updates on Google’s pointers for sending emails to non-public Gmail accounts and bulk emailing necessities, take a look at Google’s Electronic mail Sender Pointers FAQ
Have You Were given The Message But?
Because the an increasing number of advanced and ongoing combat in opposition to electronic mail unsolicited mail and phishing from refined malicious actors continues to escalate, main suppliers like Google, Yahoo, Microsoft, and others have begun imposing stringent electronic mail sending necessities for all customers to verify the secure supply of emails to supposed recipients.
Confidently, this newsletter has given you the entire knowledge you want to grasp and conform to all pointers and necessities for sending emails that can succeed in your recipients’ inboxes.
Seek advice from our information on find out how to optimize electronic mail deliverability the use of WPMU DEV’s electronic mail products and services to be told how your online business can simply conform to those new electronic mail sending regulations.
WordPress Developers