If providing your purchasers impregnable internet hosting safety for his or her WordPress internet sites with out lifting a finger sounds nice, you’re going to like Block XML-RPC … our latest weapon in opposition to XML-RPC assaults!
Since its inception, WordPress has allowed customers to engage remotely with their websites the use of a integrated characteristic referred to as XML-RPC. This isn’t most effective glorious for smartphone customers who need to weblog at the move … however hackers too!
On this article, we’ll duvet the whole lot you want to learn about XML-RPC and display you the right way to simply and mechanically offer protection to WordPress websites hosted with WPMU DEV from hackers exploiting XML-RPC vulnerabilities the use of our newest internet hosting safety device.
We’ll additionally display you ways to give protection to WordPress websites hosted somewhere else.
Learn on or click on on a hyperlink beneath to skip the fundamentals and get to the great things:
The Fundamentals:
The Just right Stuff:
- Automate Your Internet hosting Safety with WPMU DEV’s Block XML-RPC Device
- No longer Hosted with WPMU DEV? We’ve Were given You Lined
Let’s bounce proper in …
Contents
What Is XML-RPC?
XML-RPC is a faraway process name (RPC) protocol that makes use of XML to encode its calls and HTTP as a delivery mechanism.
In easy and sensible phrases, XML-RPC is used for enabling exterior packages to engage together with your WordPress website. This comprises movements like posting content material, fetching posts, and managing feedback remotely, with out the use of the WordPress internet interface.
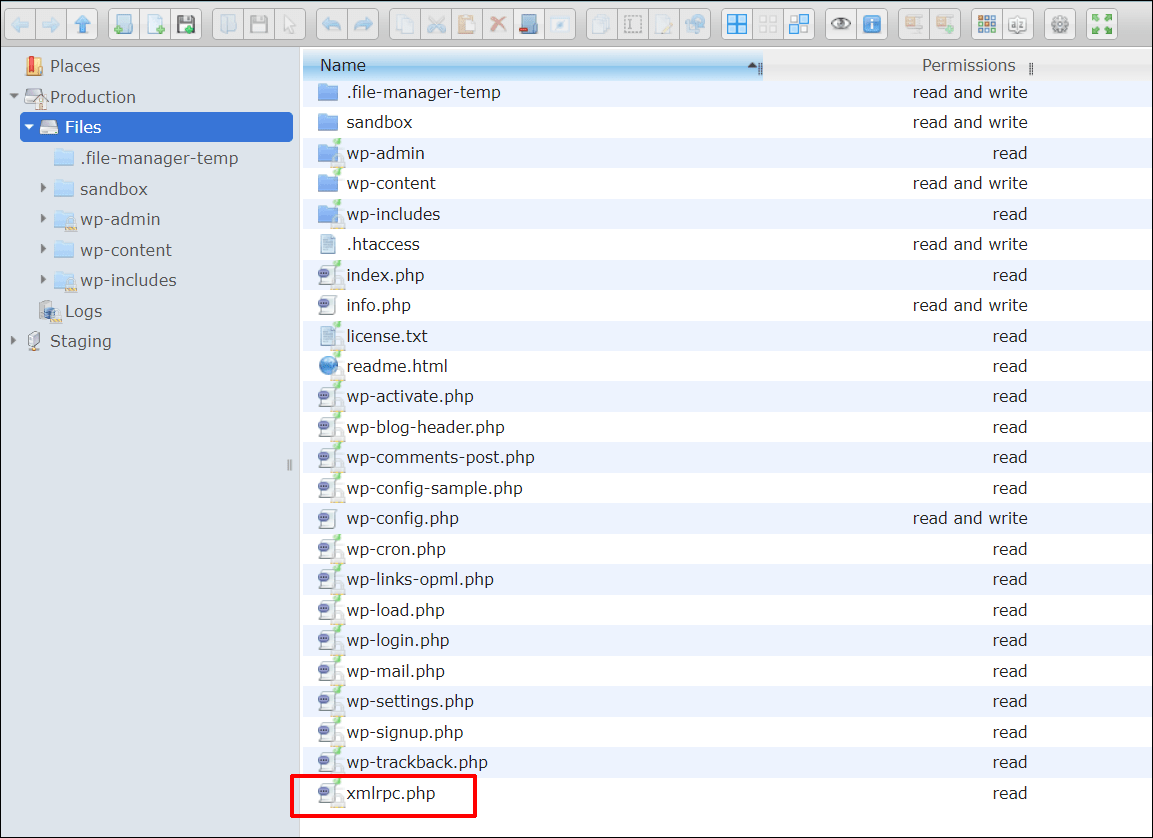
WordPress helps XML-RPC via a record referred to as xmlrpc.php, which may also be discovered within the root listing of each WordPress set up. If truth be told, WordPress fortify for XML-RPC has been part of WordPress even earlier than WordPress formally become WordPress.
You’ll be able to be told extra about XML-RPC and WordPress in this submit: XML-RPC and Why It’s Time to Take away it for WordPress Safety.
What Is XML-RPC Used For?
If you want to get admission to your WordPress site, however you’re nowhere close to your laptop, XML-RPC facilitates faraway content material control and integration with third-party packages and streamlines the method of managing WordPress websites with out direct get admission to to the admin dashboard.
WordPress customers can take pleasure in the use of XML-RPC in spaces like:
- Cellular Running a blog: Post posts, edit pages, and add media information remotely the use of the WordPress cell app or different cell apps.
- Integration with Desktop Running a blog Shoppers: Programs like Home windows Are living Author or MarsEdit permit customers to write down and post content material from their desktops.
- Integration with Products and services: Make connections to products and services like IFTTT
- Far flung Control Equipment: Permit the control of a couple of WordPress websites from a unmarried dashboard.
- Trackbacks and Pingbacks utilized by different websites to refer on your website.
Regardless of dropping its reputation to more moderen, extra environment friendly, and extra safe APIs constructed on requirements like REST or GraphQL and not being supported via PHP from model 8.0 onward, XML-RPC remains to be broadly utilized in WordPress as it’s built-in into many present methods.
XML-RPC and WordPress Safety
If you’re the use of the WordPress cell app, need to make connections to products and services like IFTTT, or need to get admission to and post on your weblog remotely, then you want XML-RPC enabled. In a different way it’s simply every other portal for hackers to focus on and exploit.
Professionals and Cons of The usage of XML-RPC
The professionals of the use of XML-RPC are most commonly comfort and potency.
Despite the fact that maximum packages can use the WordPress API as an alternative of XML-RPC, some would possibly nonetheless require get admission to to xmlrpc.php and use it to make sure backward compatibility with actively put in older variations.
It’s vital, on the other hand, to grasp the cons of the use of XML-RPC.
Mainly, XML-RPC is an old-fashioned protocol with inherent safety flaws.
Those come with:
- Safety Chance: XML-RPC may also be exploited for massive scale brute drive assaults, because it lets in limitless login makes an attempt. Attackers have used XML-RPC capability to execute common brute drive assaults in opposition to WordPress websites. By way of leveraging the machine.multicall manner, attackers can check 1000’s of password mixtures with a unmarried request.
- Efficiency: XML-RPC is usually a vector for DDoS assaults throughout the pingback characteristic, turning unsuspecting WordPress websites into bots in opposition to centered domain names, and probably slowing down or crashing the website.
Take a look at if XML-RPC is Enabled/Disabled on WordPress Websites
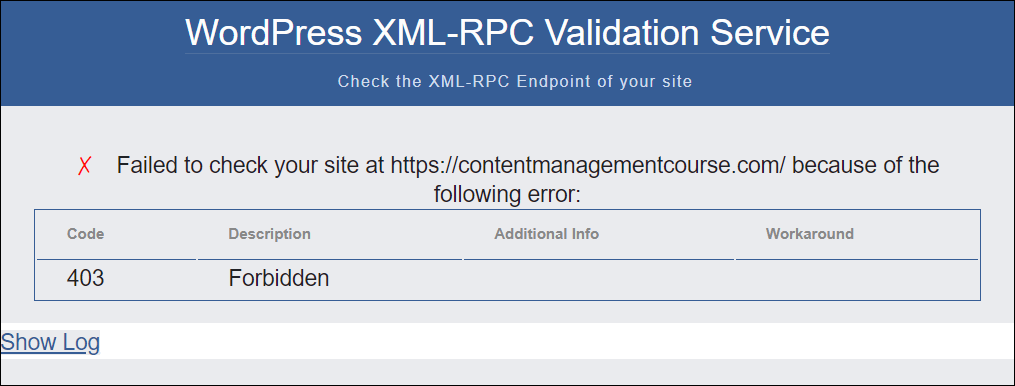
You’ll be able to use an XML-RPC validation device to test whether or not your WordPress website has XML-RPC enabled or disabled.
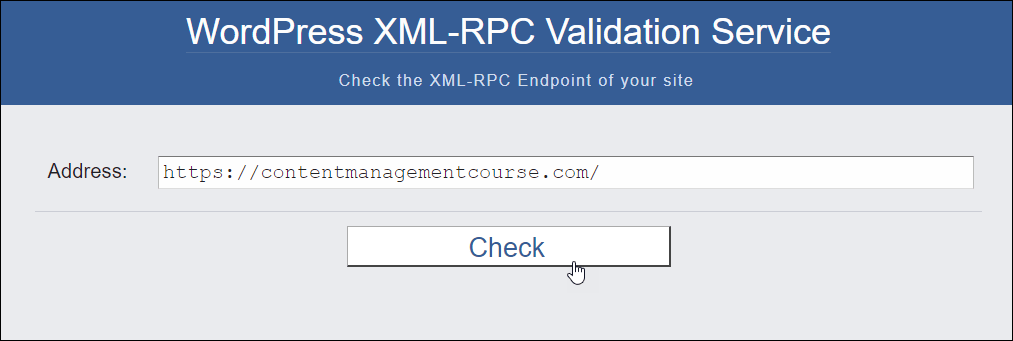
Input your URL into the Cope with box and click on the Take a look at button.
If XML-RPC is enabled, you are going to see a message like the only proven beneath.
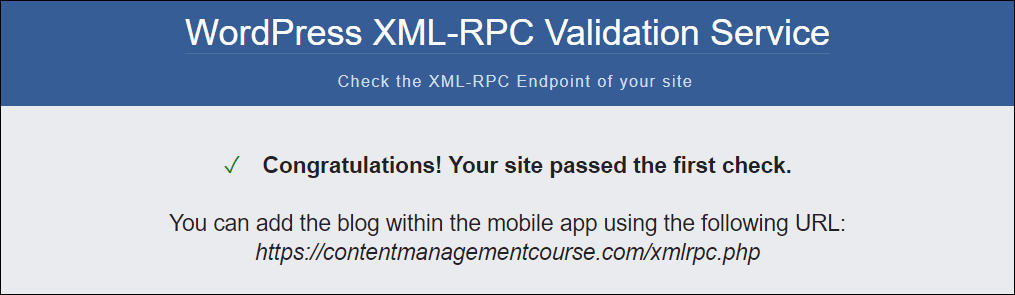
As defined above, XML-RPC could make WordPress websites susceptible to unsolicited mail and cyber assaults.
Because of this the most productive internet hosting corporations block XML-RPC via default and why we advise you must disable XML-RPC in your WordPress website(s), until you might have packages put in that require it to be enabled.
Let’s have a look, then, at a few choices you’ll be able to use to mechanically disable XML-RPC in your website (see this submit for a guide manner that comes to including code on your .htaccess record).
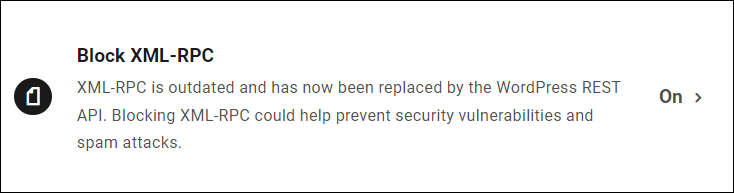
Automate Your Internet hosting Safety with WPMU DEV’s Block XML-RPC Device
We’ve just lately introduced a internet hosting device referred to as Block XML-RPC that mechanically blocks incoming requests on /xmlrpc.php when enabled.
If the device is disabled, your WordPress website will permit packages get admission to to the /xmlrpc.php record.
Notice: New websites hosted on WPMU DEV are created with the Block XML-RPC device enabled via default.
To get admission to the device and allow XML-RPC blockading on present websites, move to The Hub and make a choice the Internet hosting > Equipment tab.
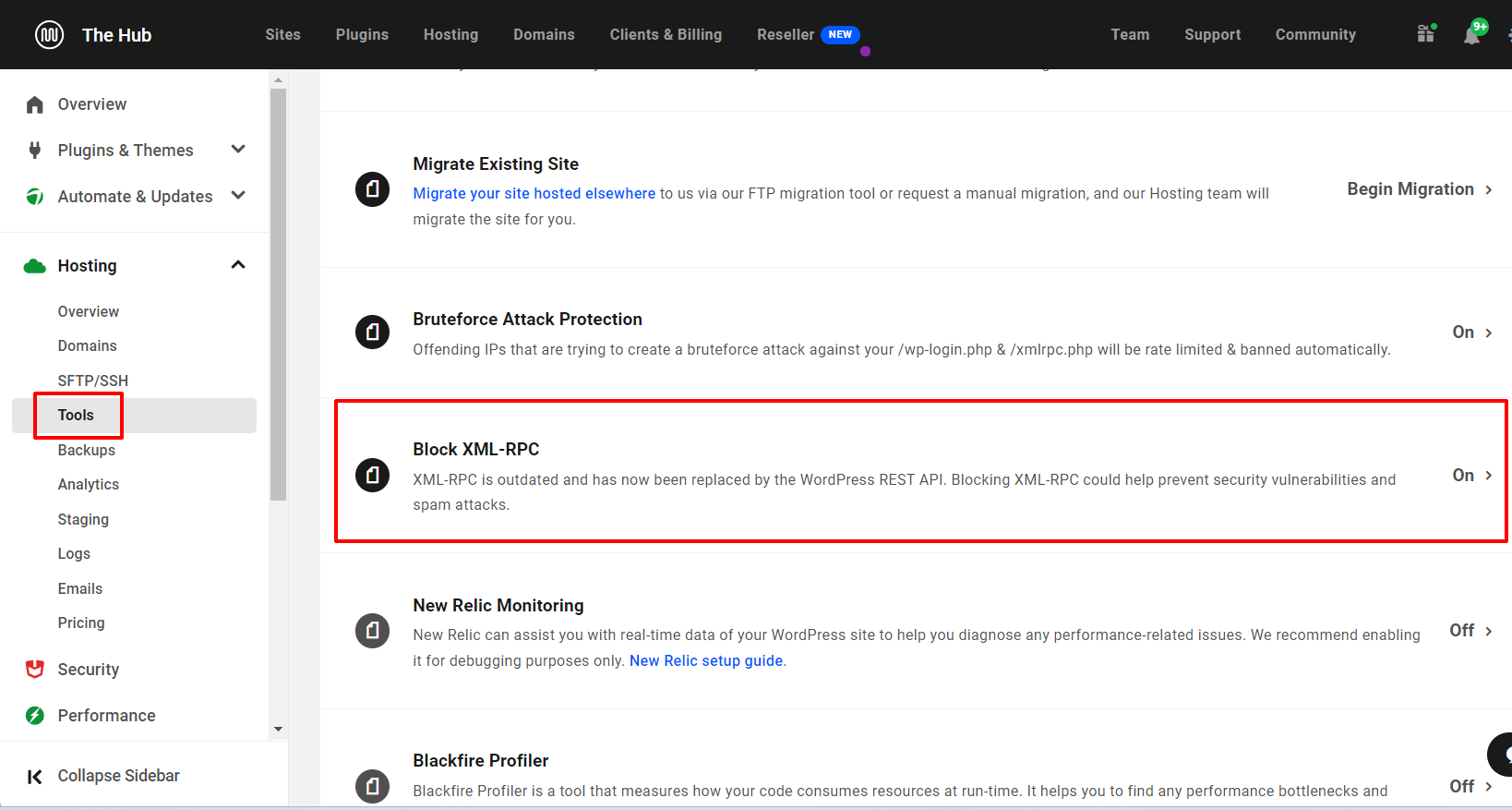
Click on On/Off to toggle the characteristic and save your settings when accomplished.
That’s it! Your website is now safe from XML-RPC exploits and assaults on the server stage.
No longer Hosted with WPMU DEV? We’ve Were given You Lined
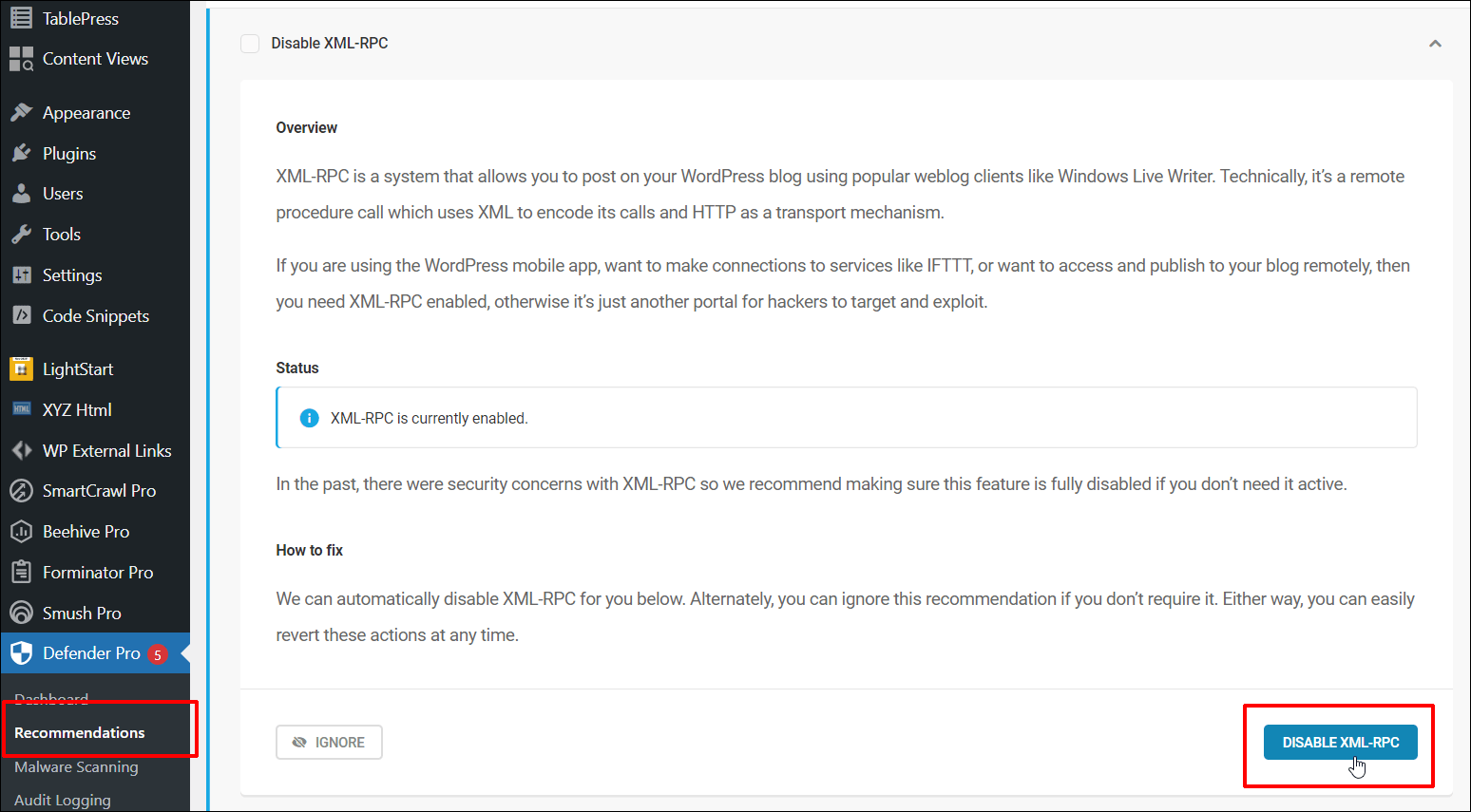
In case your website isn’t hosted with WPMU DEV (tsk, tsk…), you’ll be able to use our loose Defender safety plugin to disable XML-RPC.
The Disable XML-RPC characteristic is positioned within the plugin’s Suggestions phase.
You’ll be able to test if XML-RPC has been disabled within the Standing phase.
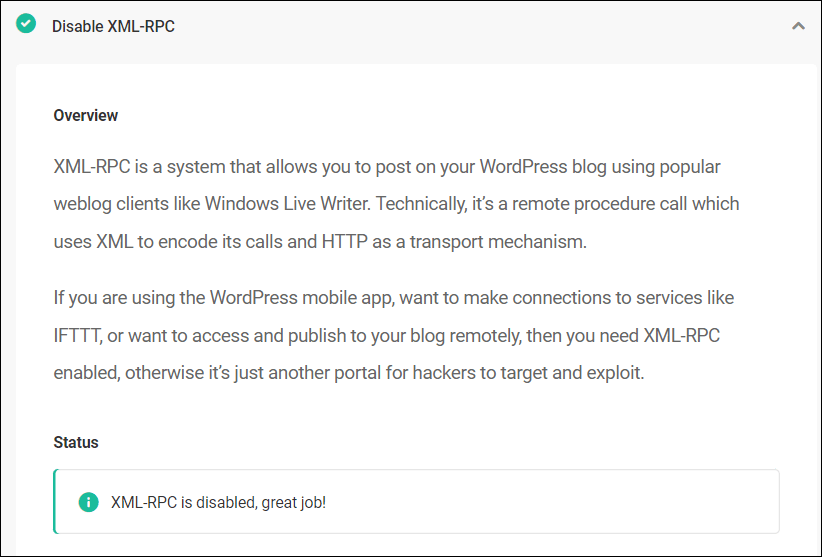
For added techniques to give protection to your website from DDoS assaults, see this educational: How To Give protection to Your Web page From DDoS Assaults.
Notice: WordPress plugins most effective block XML-RPC on the WordPress PHP stage, so if an assault happens, the request will nonetheless succeed in WordPress PHP, due to this fact expanding server load.
By contrast, whilst you allow Block XML-RPC on the server stage, the requests won’t ever succeed in your website and go back a “403 Forbidden” error message to the attackers.
For more info and detailed tutorials at the above, see those document sections: Block XML-RPC device (Internet hosting) and Disable XML RPC (Defender plugin).
R-E-S-P-E-C-T XML-RPC
Given the prospective safety dangers, WordPress website homeowners must in moderation believe whether or not the ease presented via XML-RPC outweighs its vulnerabilities.
For WordPress websites that take pleasure in XML-RPC, we advise imposing sturdy passwords, proscribing login makes an attempt, and the use of a safety plugin like Defender to assist mitigate the dangers.
On the other hand, if the capability isn’t wanted and your websites run on any of our internet hosting plans, we strongly counsel disabling XML-RPC on the server stage the use of the XML-RPC device to additional cut back the opportunity of DDoS and brute drive assaults.
WordPress Developers