Up to now few years, including authentication for your app has long gone from one thing difficult to understand and complex to one thing you’ll be able to actually simply use an API for.
There’s no scarcity of instance repos and tutorials for tips on how to put into effect explicit auth schemes in Subsequent.js, however much less in regards to the why of what schemes, gear, and tradeoffs are selected.
This publish will stroll via what to believe when drawing near authentication in Subsequent.js, from selecting a supplier to development routes for sign-in and opting for between server vs. Jstomer facet.
Opting for an Authentication Manner / Supplier
There are principally 1,000 tactics to construct authentication into your app. Reasonably than focal point on explicit suppliers right here (the topic for some other weblog publish), let’s have a look at forms of auth answers and a couple of examples of every. With regards to implementation, next-auth is instantly changing into a well-liked choice for integrating your Subsequent.js app with more than one suppliers, including SSO, and many others.
Conventional Database
This one is so simple as it will get: you retailer usernames and passwords in a relational database. When a consumer indicators up for the primary time, you insert a brand new row into the `customers` desk with the supplied data. After they log in, you take a look at the credentials in opposition to what you have got saved within the desk. When a consumer desires to modify their password, you replace the worth within the desk.
Conventional database auth is no doubt the most well liked auth scheme while you have a look at the totality of current packages and has existed principally eternally. It’s extremely versatile, affordable, and doesn’t lock you into any explicit supplier. However you do wish to construct it your self, and specifically, concern about encryption and ensuring the ones candy, candy passwords don’t fall into the unsuitable arms.
Authentication Answers From Your Database Supplier
Over the last few years (and credit score to Firebase, various years in the past), it has transform quite usual for controlled database suppliers to supply some form of controlled authentication resolution. Firebase, Supabase, and AWS all be offering each controlled database and controlled authentication as a carrier by way of a set of APIs that simply abstracts consumer introduction and consultation control (extra in this later).
Signing a consumer in with Supabase authentication is so simple as:
async serve as signInWithEmail() {
const { knowledge, error } = anticipate supabase.auth.signInWithPassword({
e-mail: '[email protected]',
password: 'example-password',
})
}Authentication Answers Now not From Your Database Supplier
Most likely much more not unusual than authentication as a carrier out of your DBaaS is authentication as a carrier as a whole corporate or product. Auth0 has been round since 2013 (now owned by means of Okta), and up to date additions like Stytch have prioritized developer enjoy and won some mindshare.
Unmarried Signal On
SSO allows you to “outsource” your id to an exterior supplier, which is able to vary from an undertaking, security-focused supplier like Okta to one thing extra broadly followed like Google or GitHub. Google SSO is ubiquitous within the SaaS global, and a few developer-focused gear handiest authenticate by way of GitHub.
Whichever supplier(s) you select, SSO is typically an add-on to the opposite forms of authentication above and carries its personal idiosyncrasies round integrating with exterior platforms (be warned: SAML makes use of XML).
Ok, So Which One Is for Me?
There’s no “proper” selection right here – what’s proper in your mission will depend on your priorities. If you wish to get issues transferring rapid with no ton of prematurely configuration, outsourcing auth is smart (even outsourcing it utterly, UI incorporated, to somebody like Auth0). For those who look forward to a extra complicated setup, development your personal auth backend is smart. And for those who envision supporting better consumers, you’ll wish to upload SSO one day.
Subsequent.js is so common at this level that a lot of these authentication suppliers have Subsequent.js explicit medical doctors and integration guides.
Development Routes for Signal-Up and Signal-In, and Guidelines for Going to Further Authentication Mile
Some authentication suppliers like Auth0 in truth supply complete hosted internet pages for sign-up and sign-in. However for those who’re development the ones from scratch, I to find it’s helpful to create them early within the procedure because you’ll want them to offer as redirects while you in truth put into effect your auth.
So it is smart to create the construction for those pages after which upload the requests to the backend after the reality. The simplest strategy to put into effect auth is to have two of those routes:
- One for signing up
- Some other for signing in as soon as the consumer already has an account
Past the fundamentals, you’ll wish to duvet edge instances like when a consumer forgets their password. Some groups wish to have the password reset procedure on a separate direction, whilst others upload dynamic UI parts to the common sign-in web page.
A pleasant sign-up web page would possibly now not imply the adaptation between good fortune and failure, however small touches can go away a excellent influence and total supply a greater UX. Listed below are a couple of collated from websites across the internet that experience put a little bit additional love into their authentication processes.
1. Replace Your Nav Bar if There’s an Energetic Consultation
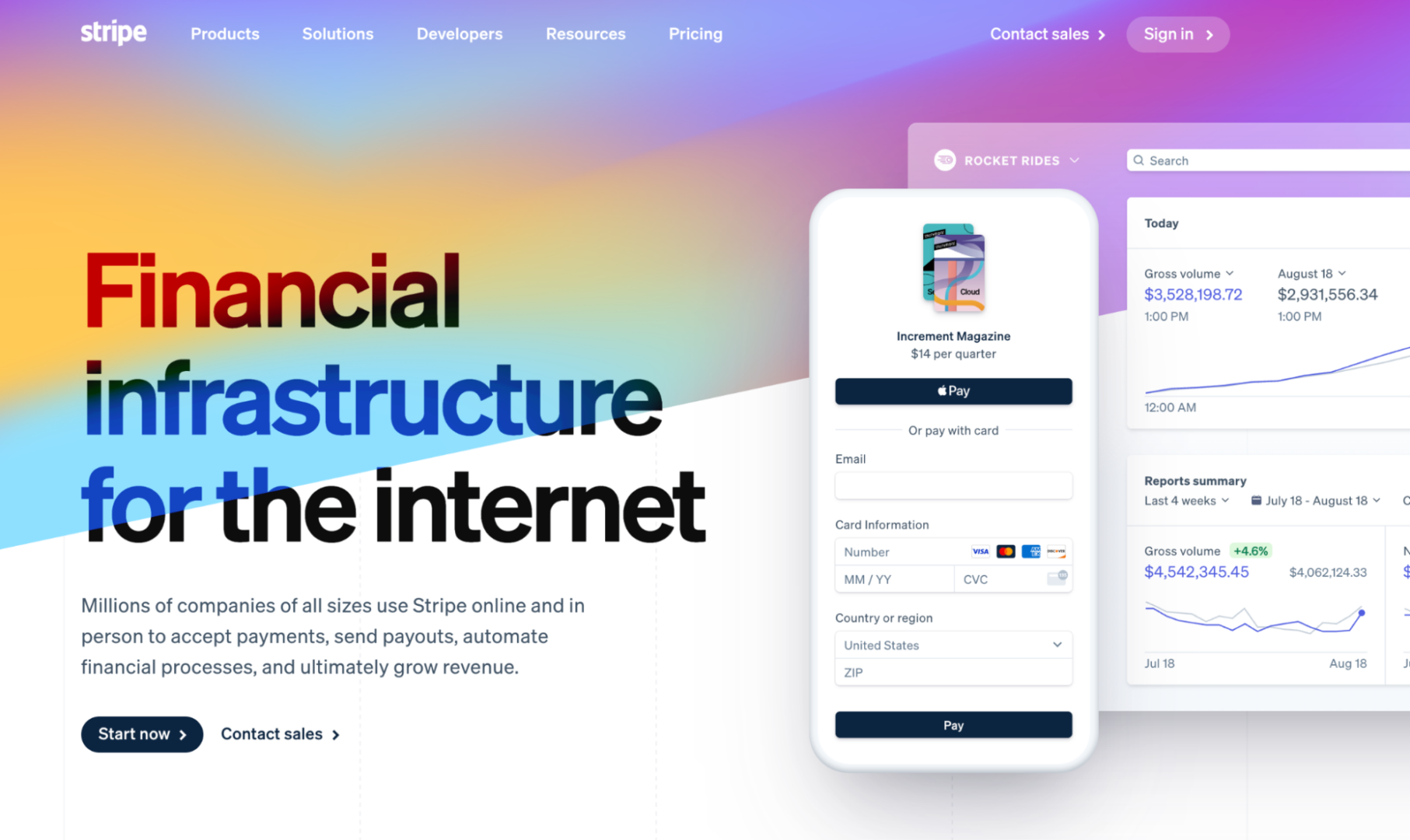
Stripe’s name to motion of their navbar adjustments in response to whether or not you have got an authenticated consultation or now not. Right here’s what the selling website online seems like for those who’re now not authenticated. Word the decision to motion to check in:
And right here’s what it seems like if you’re authenticated. Word that the decision to motion adjustments to take the consumer to their dashboard as an alternative of signing in:
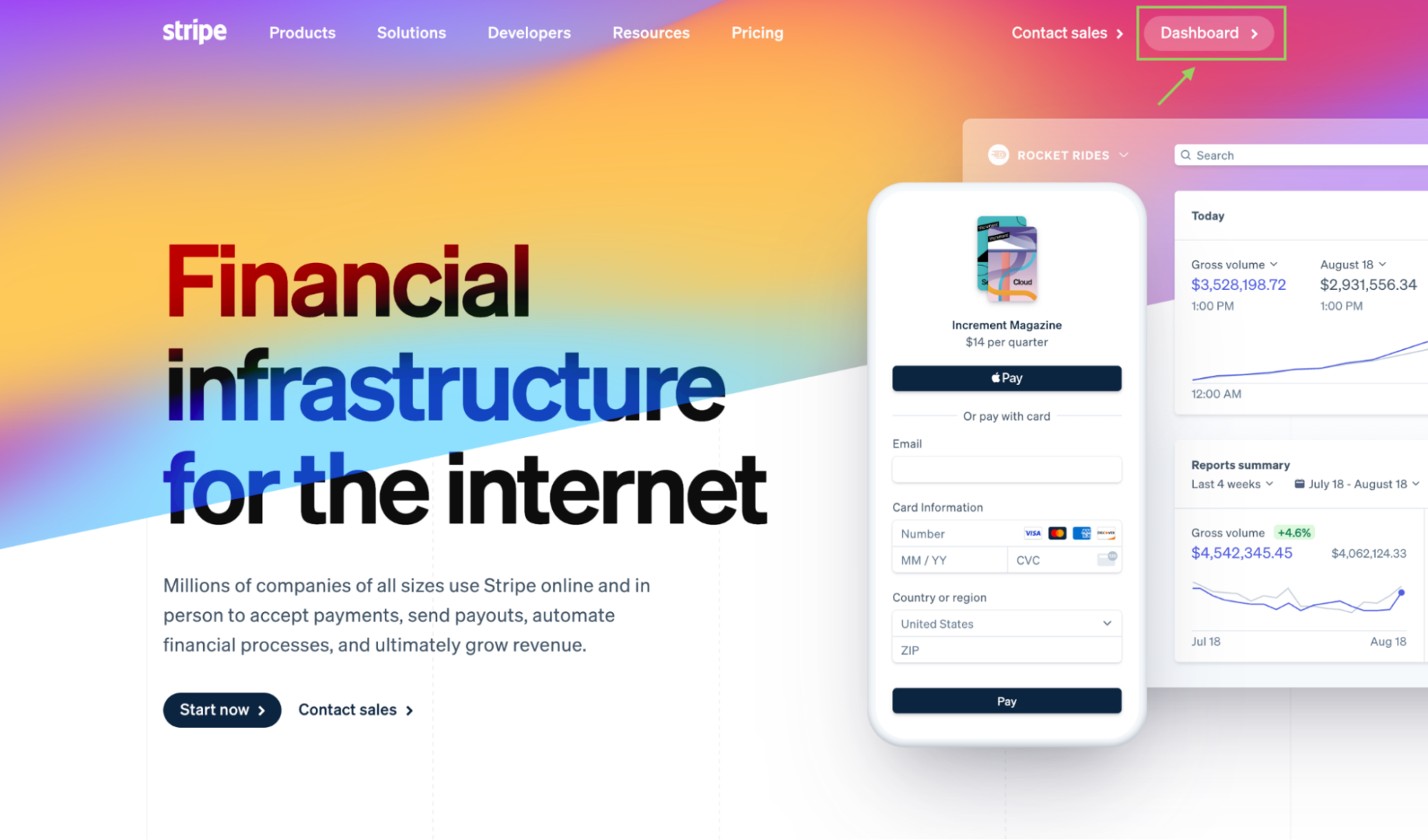
Doesn’t essentially trade my Stripe enjoy, however it’s great.
A fascinating technical apart: there’s a excellent reason why that almost all corporations don’t have the navbar on their advertising website online “rely” on authentication – it might imply an additional API request to test for authenticated state on each unmarried web page load, the vast majority of which might be for guests who’re more than likely now not.
2. Upload Some Useful Content material Along the Signal-Up Shape
Over the last couple of years, particularly in SaaS, corporations have began including content material to the sign-up web page to “inspire” the consumer to in truth whole the sign-up. This may lend a hand make stronger your conversion at the web page, a minimum of incrementally.
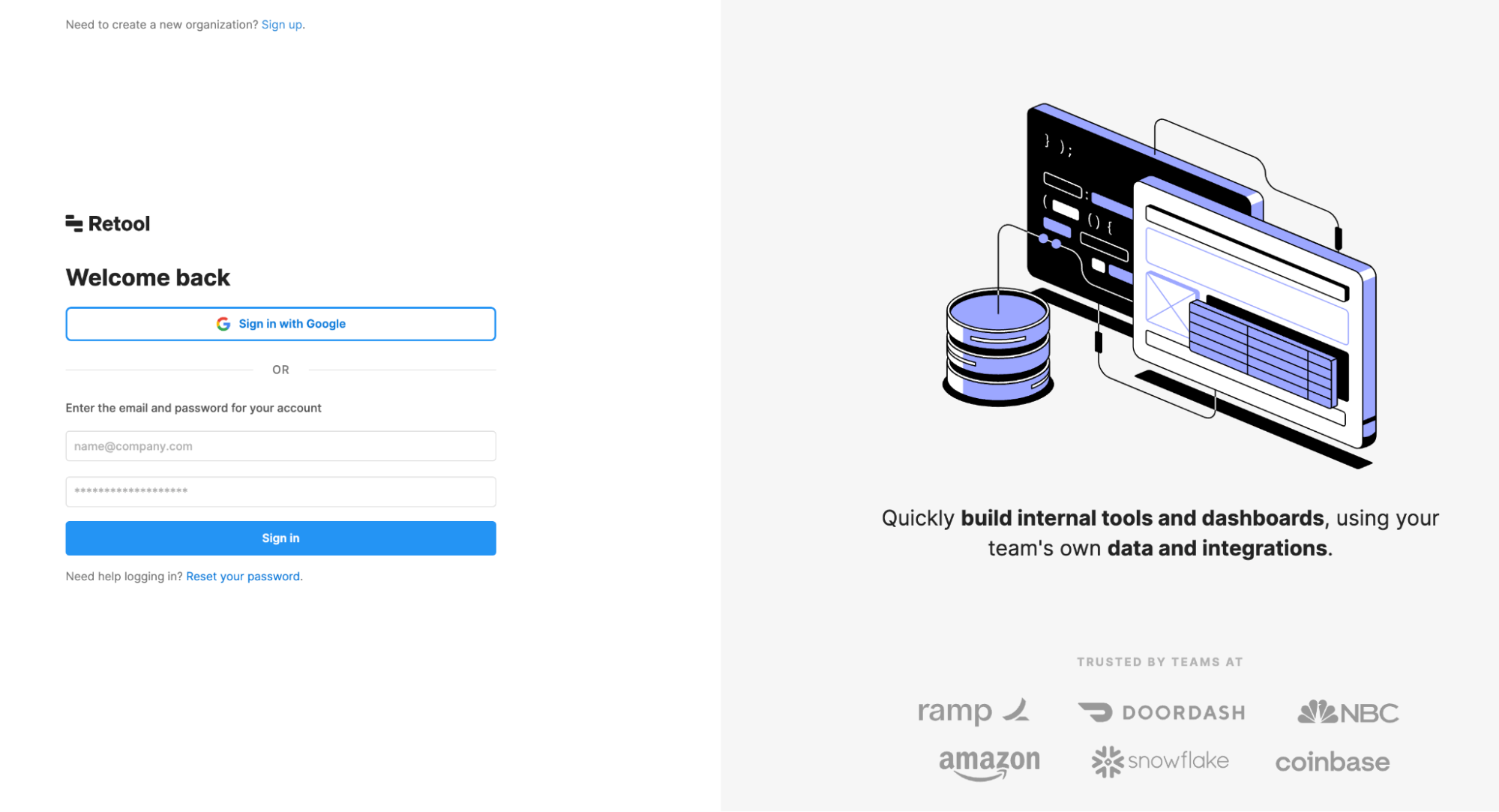
Right here’s a signup web page from Retool, with an animation and a few trademarks at the facet:
We additionally do that at Kinsta for our signup web page:
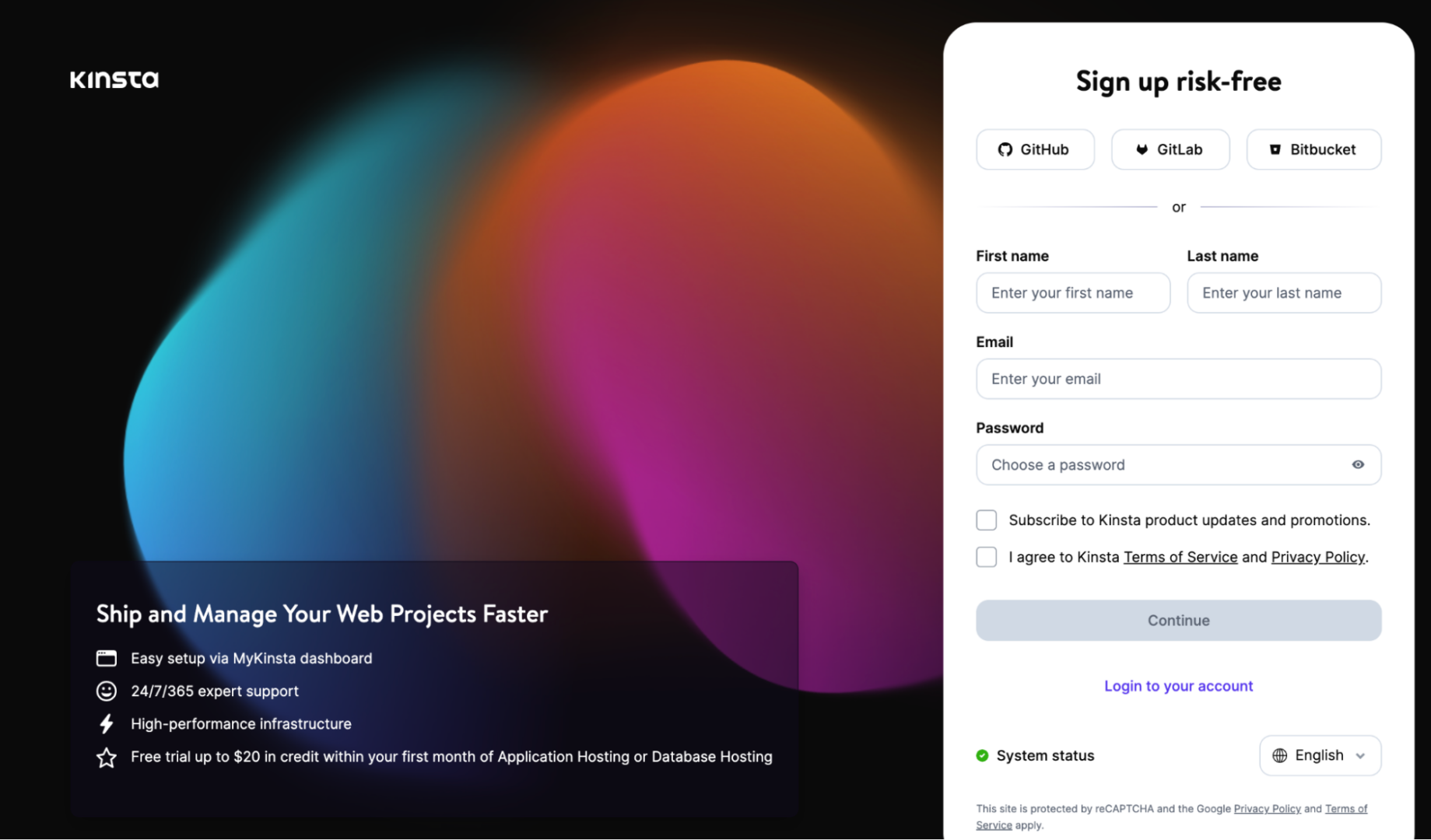
The little additional content material can lend a hand remind the consumer what they’re signing up for and why they want it.
3. If The usage of a Password: Recommend or Put into effect a Sturdy One
I think at ease announcing that it’s not unusual wisdom amongst builders that passwords are inherently insecure, however it’s now not not unusual wisdom amongst the entire individuals who will likely be signing up in your product. Encouraging your customers to create safe passwords is excellent for you and excellent for them.
Coinbase is lovely strict with signup and calls for you to make use of a safe password that’s extra difficult than simply your first identify:
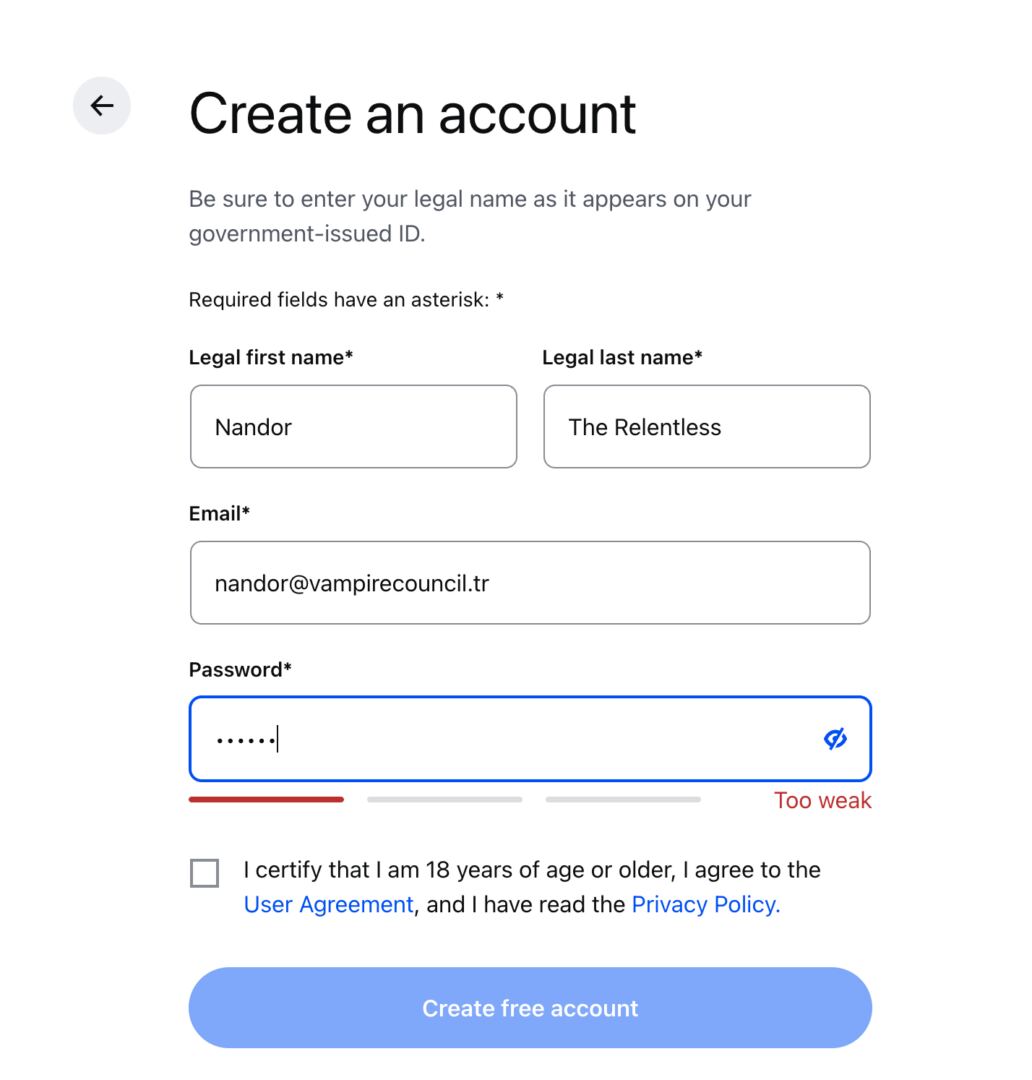
After producing one from my password supervisor as an alternative, I used to be excellent to move:
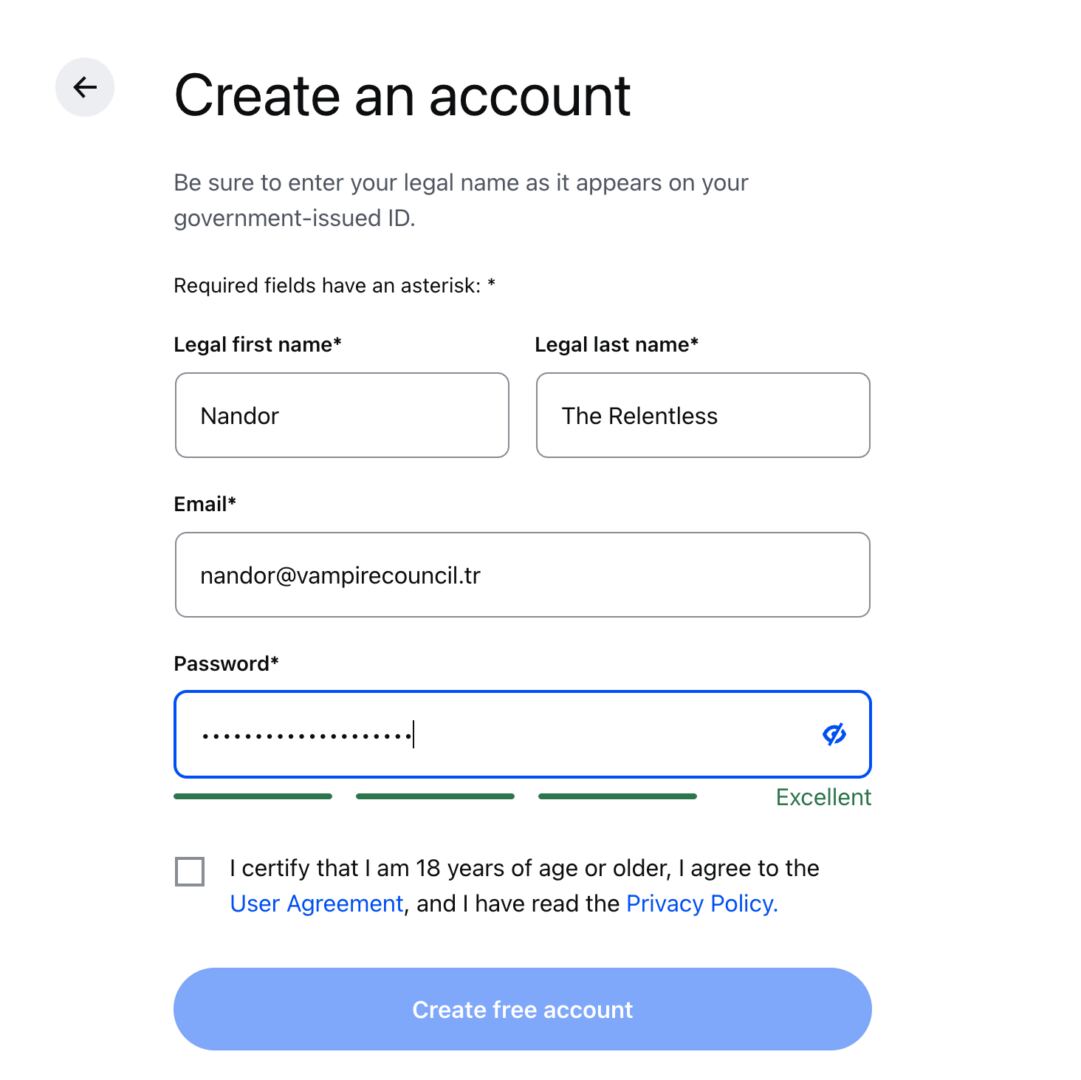
The UI didn’t inform me why the password wasn’t safe sufficient, although, or any necessities past having a host. Together with the ones to your product replica will make issues smoother in your consumer and lend a hand keep away from password retry frustration.
4. Label Your Inputs so They Play Great With a Password Supervisor
One in 3 American citizens use a password supervisor like 1Password, and but such a lot of bureaucracy on the internet proceed to forget about the `sort=` in HTML inputs. Make your bureaucracy play ball with password managers:
- Enclose your enter parts in a kind component
- Give inputs a sort and a label
- Upload autocomplete features for your inputs
- Don’t dynamically upload fields (I’m taking a look at you, Delta)
It will possibly make the adaptation between a 10-second, extremely clean sign-in and an traumatic guide one, particularly on cell.
Opting for Between Periods and JWT
As soon as your consumer authenticates, you wish to have to make a choice a technique for keeping up that state all the way through next requests. HTTP is stateless, and we no doubt don’t need to ask our consumer for his or her password on each unmarried request. There are two common strategies for dealing with this – periods (or cookies) and JWTs (JSON internet tokens) – they usually vary with regards to whether or not the server or the buyer does the paintings.
Periods, AKA Cookies
In session-based authentication, the good judgment and paintings for keeping up authentication is treated by means of the server. Right here’s the fundamental glide:
- The consumer authenticates by way of the sign-in web page.
- The server creates a report that represents this actual surfing “consultation.” This in most cases will get inserted right into a database with a random identifier and information about the consultation, like when it began and when it expires.
- That random identifier – one thing like `6982e583b1874abf9078e1d1dd5442f1` – will get despatched for your browser and saved as a cookie.
- On next requests from the buyer, the identifier is incorporated and checked in opposition to the periods desk within the database.
It’s lovely simple and tweakable in the case of how lengthy periods remaining, after they must be revoked, and many others. The drawback is latency at an important scale, given all of the writes and reads to the DB, however that is probably not a significant attention for many readers.
JSON Internet Tokens (JWT)
As a substitute of dealing with authentication for next requests at the server, JWTs let you care for them (most commonly) at the Jstomer facet. Right here’s the way it works:
- The consumer authenticates by way of the sign-in web page.
- The server generates a JWT that comprises the id of the consumer, the permissions they’re granted, and an expiration date (amongst attainable different issues).
- The server indicators that token cryptographically encrypts the contents of it, and sends all of the factor to the buyer.
- For every request, the buyer can decrypt the token and examine that the consumer has permission to make the request (all without having to be in contact with the server).
With the entire paintings post-initial authentication offloaded to the buyer, your utility can load and paintings a lot sooner. However there’s one primary factor: there’s no strategy to invalidate a JWT from the server. If the consumer desires to sign off of a tool or the scope in their authorization adjustments, you wish to have to attend till the JWT expires.
Opting for Between Server Aspect and Consumer Aspect Auth
A part of what makes Subsequent.js nice is the integrated static rendering – in case your web page is static, i.e. doesn’t wish to make any exterior API calls, Subsequent.js mechanically caches it and will serve it extraordinarily rapid by way of a CDN. Pre-Subsequent.js 13 is aware of if a web page is static for those who don’t come with any `getServerSideProps` or `getInitialProps` within the record, whilst any variations publish Subsequent.js 13 use React Server Parts to try this as an alternative.
For authentication, you have got a call: rendering a static “loading” web page and doing the fetching Jstomer facet or doing the entirety server facet. For pages that require authentication[1], you’ll be able to render a static “skeleton” after which make authentication requests at the Jstomer facet. In idea, this implies the web page so much sooner, even though the preliminary content material isn’t absolutely able to move.
Right here’s a simplified instance from the medical doctors that renders a loading state so long as the consumer object isn’t able:
import useUser from '../lib/useUser'
const Profile = () => {
// Fetch the consumer client-side
const { consumer } = useUser({ redirectTo: '/login' })
// Server-render loading state
if (!consumer || consumer.isLoggedIn === false) {
// Construct some form of loading web page right here
go back Loading...
}
// As soon as the consumer request finishes, display the consumer
go back (
Your Account
Username: {JSON.stringify(consumer.username,null)}
Electronic mail: {JSON.stringify(consumer.e-mail,null)}
Cope with: {JSON.stringify(consumer.cope with,null)}
)
}
export default ProfileWord that you just’d wish to construct some form of loading UI right here to carry area whilst the buyer makes requests post-load.
If you wish to simplify issues and run authentication server facet, you’ll be able to upload your authentication request into the `getServerSideProps` serve as, and Subsequent will wait to render the web page till the request is whole. As a substitute of the conditional good judgment within the snippet above, you’d run one thing more practical like this simplified model of the Subsequent medical doctors:
import withSession from '../lib/consultation'
export const getServerSideProps = withSession(async serve as ({ req, res }) {
const { consumer } = req.consultation
if (!consumer) {
go back {
redirect: {
vacation spot: '/login',
everlasting: false,
},
}
}
go back {
props: { consumer },
}
})
const Profile = ({ consumer }) => {
// Display the consumer. No loading state is needed
go back (
Your Account
Username: {JSON.stringify(consumer.username,null)}
Electronic mail: {JSON.stringify(consumer.e-mail,null)}
Cope with: {JSON.stringify(consumer.cope with,null)}
)
}
export default ProfileThere’s nonetheless good judgment in right here to care for when authentication fails, however it redirects to login as an alternative of rendering a loading state.
Abstract
So which this type of is true in your mission? Get started by means of comparing how assured you’re within the pace of your authentication scheme. In case your requests are taking no time in any respect, you’ll be able to run them server facet and keep away from the loading state. If you wish to prioritize rendering one thing instantly after which looking forward to the request, skip `getServerSideProps` and run authentication somewhere else.
[1] When the use of Subsequent, it is a excellent reason why to not blanket-require authentication for each unmarried web page. It’s more practical to take action, however approach you fail to notice the efficiency advantages of the internet framework within the first position.
The publish Issues When Environment Up Authentication in Subsequent.js seemed first on Kinsta®.
WP Hosting