Whilst it could no longer were a number one fear within the early days of the internet, for contemporary web customers, the facility to order the precise to withhold private data is paramount. Hacking is a huge (albeit unlawful) industry too, and it continues to develop.
The Tor Browser is without doubt one of the perfect tactics to stay prying eyes at bay.
Alternatively, there are many use circumstances for the Tor Browser instead of protecting a hacker at arm’s period. As an example, you’ll be able to anonymize your IP in nations that prohibit web get admission to, or navigate to portions of the web that may’t be reached another method (which is one explanation why regulation enforcement is a key consumer base for the browser).
This put up will glance into the Tor Browser and supply some comparisons to different in style answers. By means of the tip, you’ll have the entire data you wish to have to come to a decision whether or not Tor is true on your wishes.
What Is the Tor Browser and Venture?
Tor — shorthand for “The Onion Router” — is greater than only a browser. The whole challenge covers an entire array of gear, networks, and different similar products and services. It’s a non-profit group that oversees the other components within the community.

It has ties to different organizations such because the Digital Frontier Basis (EFF) and has gained fortify from builders at Mozilla, manufacturers of the open-source browser Firefox. Actually, investment for Tor comes from some assets you wouldn’t be expecting, such because the U.S. authorities and Google.
The Tor Venture fulfills the function of safeguarding anonymity around the world web. We’ll communicate extra about this in a while, however for now, simply know that the entire community keeps nameless pipelines open for lots of other customers.
Whilst you would possibly to find a few of the ones customers come to the community as a way to hide criminality, there’s a subjective interpretation to this. The “darkish internet” fills many jobs, and in scenarios the place a consumer should stay nameless as a way to unfold a message, the Tor community and browser can also be central.
Whilst a whole lot of its products and services have come and long past, corresponding to Tor Messenger, the browser is a mainstay. Within the subsequent phase, we’ll communicate extra about why it’s the most important mainstay to find out about.
Why We’re Reviewing the Tor Browser
The historical past of web privateness and safety is lengthy, convoluted, and sophisticated. There’s now sufficient fear from customers about data privateness for the Tor Browser to want to exist.
Leaks from whistleblowers corresponding to Edward Snowden and Wikileaks within the 2010s displays that world internet surveillance amongst nations is prime. Tasks and collaborations corresponding to “5 Eyes,” PRISM, and others concern some customers to the purpose the place they will concern for their very own protection, making on-line anonymity a number one fear.
In a nutshell, Tor permits get admission to to the “darkish internet.” Whilst the darkish internet will get some unhealthy press (particularly because of criminality), there may be quite a lot of just right too, as we’ll talk about. It exists on “darknets,” which can be overlays that you wish to have explicit gear or authorization to get admission to. The Tor Browser permits this get admission to to the darkish internet, even if it will probably additionally get admission to the common so-called visual internet too.
Actually, there are many different browsers that may get admission to the darkish internet. Alternatively, Tor handily beats the contest because of its array of options — such a lot in order that some choice browsers may also use Tor as its base.
Let’s communicate extra about what Tor can do.
Tor Browser’s Key Options
At its core, the Tor Browser is a “modded” model of Firefox. From there, the advance staff upload in a couple of different specifics that can assist you get admission to the darkish internet:
- TorButton. This element handles application-level safety and privateness inside the Firefox code base. It turns that browser into what Tor provides.
- NoScript. This can be a fundamental JavaScript blocker, that we could Tor prohibit get admission to to scripts — therefore the identify.
- HTTPS All over the place. This extension is from the EFF. It’s a company that takes privateness severely. HTTPS All over the place defaults all connections to the extra safe and encrypted layout, fairly than the extra inclined HTTP connection.
As is standard for most of these packages, Tor is open-source and there is not any top rate model to be had. This implies it’s loose for everybody to obtain and use. There’s even a GitHub repository for many who can’t get admission to the principle Tor site.
You may additionally prolong the platform similarly to Firefox, however this isn’t really helpful. As you’ll uncover, the usage of a browser corresponding to Tor isn’t a regular internet revel in.
Tor’s Building Gear
Similar to its father or mother browser, Tor supplies construction gear. Actually, they’re the similar as Firefox, so if in case you have familiarity with that browser, you’ll be at house right here. You’ll to find them in the course of the Gear > Browser Gear > Internet Building Gear menu inside the Tor toolbar:
Alternatively, we wouldn’t counsel you utilize them. For starters, Tor’s perfect use case isn’t construction paintings, and also you’d get via a lot better with an answer for that with one thing like Firefox Developer Version.
Tor Browser’s Center of attention on Nameless Surfing
In a technical sense, Tor works simply as Firefox does at the frontend. This implies you get the revel in of a stellar internet browser that may obtain common updates and fortify.
Alternatively, underneath the hood, there may be extra occurring.
The preliminary construction of the Tor Browser comes from the US Army of all puts. The preliminary thought to offer protection to inside, cross-government communications marries up neatly with the overall want to offer protection to privateness everyday. Any data you ship to or from a Tor Browser has automated encryption.
From there, knowledge transfers throughout more than one relays inside the Onion Router community. The information runs over 3 relays, each and every of which is a part of a volunteer-led community of machines. This “homogenizes” the consumer base, that means that you’d best see {that a} consumer is operating Tor and little else.
Safety Ranges
The Tor Browser allows you to customise its safety provision the usage of other ranges. There are 3 you’ll be able to make a choice from, and each and every one chops off some facet of the capability:
- Usual: That is the default mode, the place the entire options and capability are energetic.
- More secure. With this mode, you’ll have to click on HTML5 media as a way to play it. What’s extra, you received’t have the ability to use JavaScript on non-encrypted websites. You’ll additionally to find that some capability is disabled for higher safety.
- Most secure: Right here, you’ll best have the ability to view static websites, with additional restrictions to a couple usable capability. JavaScript is disabled for all websites.
You’ll alternate those at any time in accordance with your wishes, even if for many packages, the Usual tier will paintings advantageous.
The Onion Community
The Onion Community is a descriptive identify for the best way knowledge packets transfer via encrypted messages. Those messages transfer via a number of layers, just like an onion, and information travels throughout 4 other community nodes.
Every node peels away a layer of encryption, and divulges the following vacation spot for the information. On the finish of the chain, the information will provide itself at its vacation spot. What’s extra, each and every node will best know the positioning of the former and subsequent node. This boosts anonymity and manner you’ll have a prime point of safety without reference to the place you’re.
Advert Blocking off and Extending the Browser
In relation to browser extensions, as a result of Tor is in accordance with Firefox, you’ll be able to set up any and they all inside the Extensions Library. Alternatively, nearly none of those have fortify from the Tor Venture.
Tor comprises the entire extensions that it helps, and the caution within the documentation states that it is advisable damage capability — or worse, compromise your safety and privateness.
As for advert blockading, there is not any integrated method that Tor achieves this. Some sides of the NoScript extension will put a halt to sure commercials, however this received’t forestall all of them.
As a substitute, the usage of the safety ranges inside Tor’s settings will likely be one of the simplest ways to forestall commercials from showing, in addition to the place you’ll be able to regulate many different sides of a web site’s capability.
Is It Criminal To Use the Tor Browser?
For all intents and functions, the Tor Browser is felony to obtain, set up, and use for each consumer. We speak about many use circumstances on this put up about felony tactics you’d use the capability Tor provides.
Alternatively, it’s additionally true that many unlawful actions happen the usage of Tor — particularly at the darkish internet. In the USA, no less than, Tor is felony to make use of. For some nations that regularly suppress data, corresponding to China or Russia, Tor can’t be used legally.
That stated, even in the USA, regulation enforcement tries to close down sure customers — so there may be particular pushback at a central authority point relating to Tor utilization, specifically because it grants larger anonymity.
Drawbacks of The usage of Tor
As with maximum issues, Tor has each positives and negatives. We’d recommend that it’s one of the simplest ways to browse the internet in an nameless method, but it surely’s no longer a foolproof resolution. Actually, the browser can’t save you end-to-end “correlation.” That is the place you’ll be able to pinpoint the supply of a malicious hacking strive via more than one knowledge issues.
What’s extra, in sure unusual eventualities, you should still be uncovered to vulnerabilities:
- Some internet sites can sense that you simply use Tor and block your get admission to in consequence.
- It’s imaginable for a nasty actor to snatch a fingerprint of your mouse actions, then use that to additional identify your identification.
- Similar to an ordinary Direct Denial of Provider (DDoS) assault, a malicious consumer can weigh down Tor’s “go out nodes.” Briefly, those are the tip level of the community chain, and it’s what you’ll see while you view a web site at the darkish internet. In some circumstances, this “sniper assault” too can ship you via an go out node that the attacker controls.
So, Tor isn’t a failsafe resolution for nameless surfing. Regardless of this, Tor continues to be broadly thought to be the most secure and maximum safe solution to browse the darkish internet.
The usage of a Digital Non-public Community (VPN) With the Tor Browser
Whilst the Tor Browser is felony to make use of, it does instill concern in some companies, corporations, and businesses on account of what it permits customers to do. It’s even imaginable that your Web Provider Supplier (ISP) may punish you for the usage of it underneath their explicit phrases of carrier.
To mitigate this, you’ll be able to use Tor together with a Digital Non-public Community (VPN). This may obfuscate your location sufficient that you simply’ll have the ability to use Tor with relative anonymity.
There are two tactics you’ll be able to mix the 2 gear:
- You’ll run your VPN first, then open Tor inside it; or
- You’ll open Tor first, then attach your VPN.
They sound like the similar procedure, however there are some elementary variations that carry up some positives and negatives for each and every.
Normally, you’ll need to attach your VPN prior to you run Tor as a result of this fashion you’ll be able to get admission to devoted “Onion” websites.
Alternatively, word that both choice will disclose your surfing data to a third-party. This might be the VPN supplier, your ISP, or each. It’s some other aspect you’ll want to weigh up as a way to make the most efficient resolution on your privateness wishes.
Tor’s Pace and Efficiency
The focal point of the Tor Browser is on safety, anonymity, and consumer protection. None of those contain a focal point on pace.
Briefly, the efficiency of the Tor Browser relating to pace is deficient (in different phrases, it’s too gradual for the typical internet surfer). That is vital to grasp this when taking into account the usage of Tor since the pace deficit may negatively have an effect on your revel in.
Because of the character of the usage of relays to hook up with the internet and the way this set of connections is nearly random each time, you’ll be able to’t pin down specifics when it comes to benchmarks. As an example, safety weblog Cloudwards’ personal benchmarks display the Tor Browser be uncompetitive in comparison to different browsers. Actually, it doesn’t ranking anything else in any respect in a few assessments.
Alternatively, if you happen to have a look at a web site corresponding to HTML5test, you’ll be able to see that Firefox — the father or mother browser on this case — plays neatly.
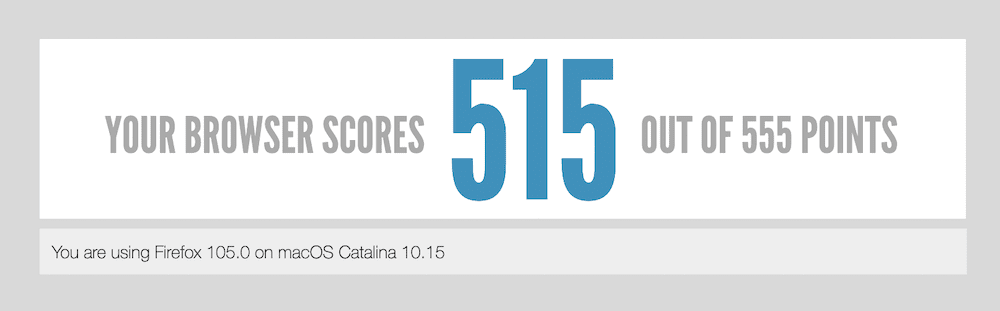
Take into account, although, the Tor Browser has larger ranges of safety and makes use of an absolutely other method of getting access to the internet. What’s extra, undertaking benchmark assessments isn’t going to come up with a real-world view of your personal revel in of ways Tor plays.
How Tor Compares To Different Browsers
In the following couple of sections, we’re going to have a look at how Tor compares to different in style browsers. Alternatively, this shouldn’t be your number one solution to come to a decision whether or not the Tor Browser is for you. Maximum business internet browsers don’t have privateness and safety as a number one, marquee function (even if it’ll be given due consideration).
Let’s get started with an answer this is in some ways diametrically hostile to the Tor Browser: Google Chrome.
Tor Browser vs Google Chrome
You’ll most probably already find out about Google Chrome. It has a marketplace percentage that’s unrivaled in its box, which you’d be expecting for the reason that it’s subsidized via the hunt massive, Google.

You’ll get this browser on nearly all units, and it’ll even come usual on some telephones, such because the Google Pixel.
Actually, it is advisable say that it units the usual for browsers, particularly relating to the generation it brings to the desk:
- It will provide you with a mixed seek bar and cope with bar that may additionally pick information and paperwork from different Google products and services.
- Talking of which, there may be deep integration with Google Workspace on faucet, with record and account sync inbuilt.
- There’s a integrated password supervisor that shops your credentials within the cloud.
- You additionally get a large extension library to tailor your revel in for your wishes.
It could appear extraordinary to match Google Chrome to Tor right here, however that is price mentioning: Chrome — and Google itself — are at the leading edge of sharing data. Even a cursory seek will carry up the corporate’s practices when it comes to knowledge harvesting. There were a large number of complaints previously directed on the objectively shady method Google handles knowledge.
By contrast, Tor is so locked down that it will probably’t compete with any browser on efficiency. Alternatively, that is precisely why it’ll be of an enormous get advantages to you if you wish to offer protection to your identification and knowledge.
We will be able to’t say that Tor is best than Chrome around the board since the two browsers have other targets. Alternatively, you received’t need to use Google Chrome in any respect if you wish to have to stick nameless.
Tor Browser vs Courageous
The Courageous browser is one we duvet in different places at the Kinsta weblog, and it appears to be like to mix a well-liked core function set with additional privateness and safety features that come with advert blockading as usual.

The browser’s founders come with the inventor of JavaScript and the co-founder of Mozilla (i.e. the Firefox builders.) Alternatively, Courageous builds on peak of Google Chrome fairly than Firefox. Right here’s what it’ll be offering along with the Chrome revel in:
- There’s a novel function that permits you to earn cryptocurrency for the usage of the browser. You’ll gather it, and will ship it to different content material creators.
- Courageous builds at the construction model of Google Chrome — Chromium. As such, you’ll be able to upload the similar extensions as you’ll to find within the Chrome Internet Retailer.
- Given the focal point on blockading commercials and protective the consumer, Courageous additionally comprises devoted capability for this. There’s a password supervisor, you’ll be able to keep an eye on cookies, media autoplay, and extra on a per-site foundation.
This ultimate level is the place we will be able to evaluate Courageous to Tor. Actually, Courageous’s non-public surfing home windows use the capability because the Tor Browser to anonymize your fingerprint. This can be a nice step, however Courageous does have some drawbacks.
As an example, you earn cryptocurrency via viewing commercials, which is in stark distinction to the basic explanation why to make use of Courageous. This additionally manner you’ll be matter to monitoring as a way to tally up your advert perspectives.
For a normal surfing revel in, we’d say Courageous is without doubt one of the higher choices, particularly given the rate benefit over Tor. The personal surfing choice could also be welcome. Alternatively, for safety and privateness, Courageous would possibly no longer do sufficient, and its normal function set contradicts its major targets frequently.
Tor Browser vs Chromium
In case you use Courageous, Google Chrome, Microsoft Edge, and lots of different an identical browsers, you’ll to find all of them use Chromium as a base. That is the advance and open-source model of those browsers, however this doesn’t at all times come up with bleeding edge capability.

In case you evaluate Chromium to different browsers that construct upon it, you’ll to find an anemic function set. It is because it’s no longer for public intake, even if some do use it. Alternatively, we’d counsel you select nearly another browser for the next causes:
- Chromium is largely a “beta” model of a browser. There’s no set up supervisor, so that you’ll want to “bring together” the tool prior to you’ll be able to use it.
- The present model of the browser — all variations, in truth — will best be offering nightly builds. That is the “end-of-the-day” model of the browser the builders will add, this means that it will have insects, mistakes, or vulnerabilities.
Chromium’s focal point is on studying the right way to broaden a internet browser, no longer on privateness or safety. We’d argue that the usage of Chromium will provide you with the least coverage for the entire causes we point out.
On account of this, Tor is a a lot better guess on your safety and privateness.
Tor Browser vs Mozilla Firefox
Amongst customers and builders alike, Firefox is a standout. It holds its floor as a champion of open-source basics, privateness, safety, and a lot more.
Right here’s what Firefox will provide you with relating to a safe surfing revel in:
- There’s a full-featured non-public surfing mode, on par with maximum different browsers.
- Firefox will block a variety of internet components via default. This comprises cryptomining scripts, social trackers, and third-party monitoring cookies.
- Firefox comes with a local password supervisor to assist retailer each set of credentials you utilize.
- Firefox will block media that makes an attempt to autoplay, providing you with the selection to play it or no longer.
- The browser additionally provides an extension library, so you’ll be able to upload HTTPS connections via default, combine an advert blocker, and extra.
Whilst you evaluate Firefox to Tor, you additionally must believe the place it sits while you evaluate it to different browsers. For a core point of privateness and safety, we’d make a selection Firefox over any Chromium-based browser, particularly Chrome.
Alternatively, Tor does be offering a lot better safety and privateness with a side-by-side comparability. That is comprehensible in accordance with what each and every browser provides.
We’d say that if in case you have issues about day by day privateness however nonetheless want a snappy surfing revel in, Firefox will are compatible the invoice.
Tor Browser vs Apple Safari
For Apple customers, Safari is the default and plays neatly on all its units. It’s in style as a “set and put out of your mind” form of browser.
Alternatively, it will not be the most efficient if you happen to price your privateness and safety.
At the entire, Safari is a purposeful browser that integrates in one of the simplest ways with different Apple merchandise. This is a bonus for many customers and manner the main function of the browser is met.
Alternatively, Safari doesn’t be offering one of the vital components we’d be expecting from a safe and personal browser:
- There’s no autoplay blockading capability, this means that you’ll want to to find an extension (if one exists).
- Safari doesn’t block cryptomining scripts. This would possibly no longer impact you an excessive amount of, but it surely’s great to understand a browser has your again on all forms of malicious movements.
- Apple is in the back of in terms of imposing safety capability into its browser; as such, Safari has a sparse set of choices to assist offer protection to you. That stated, you’ll be able to nonetheless block all cookies, forestall websites monitoring whether or not you utilize Apple Pay, and save you cross-site monitoring too.
- Apple Safari is a proprietary piece of tool. This implies the code base isn’t to be had to have a look at. Whilst this isn’t essentially an issue, open-source tool has a lot extra eyes at the core code, that means builders can give a contribution to mend insects and mistakes sooner.
The Tor Browser could also be open-source and comprises the entirety Apple Safari lacks. Once more, efficiency is a matter, however the total targets of each browsers are other.
We wouldn’t say Tor is an “on a regular basis” browser, however it’ll undoubtedly offer protection to you higher than Safari if you wish to have to browser as an nameless consumer.
How To Set up and Use the Tor Browser
As with all app, you’ll first want to obtain and set up the Tor Browser to your laptop. There’s an respectable web page to do that at the Tor Venture site.
The preliminary procedure is as easy as another set up: Obtain the bundle, extract it, and undergo the rest set up steps on your working machine (OS).
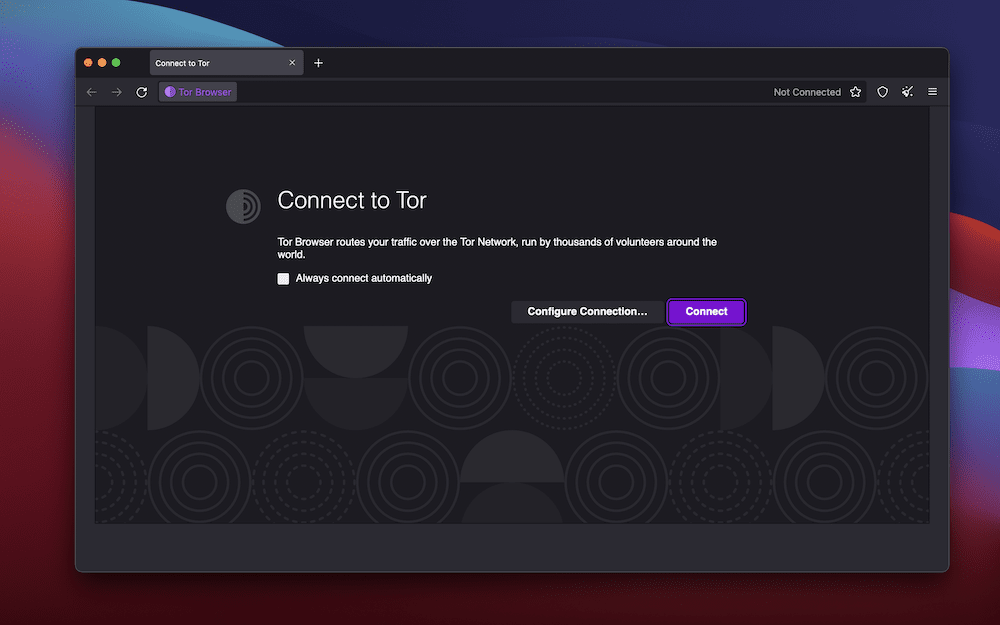
When you whole this step, you’ll be able to open the Tor Browser as you may another software. Doing so will carry up a clean window, whole with buttons to configure your shopper and connect with the community:
In case you click on the Attach button, you’ll see the browser glance to determine a connection to the Tor Community:
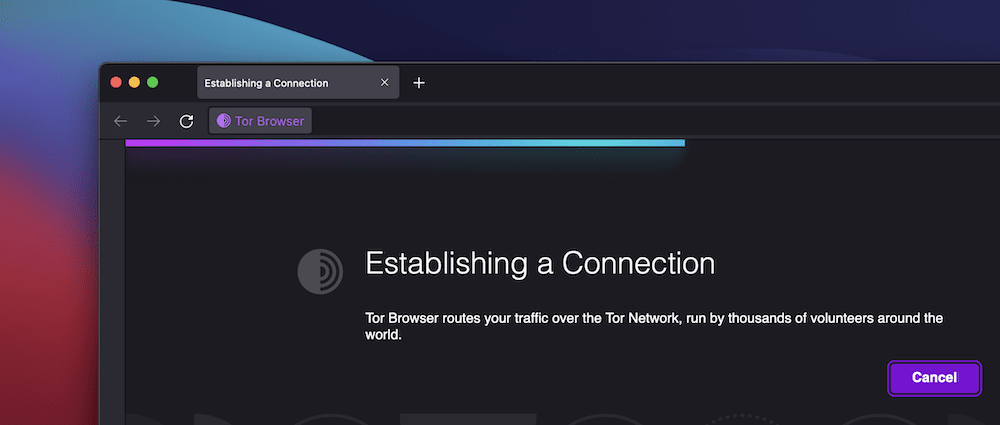
This might take some time relying on quite a lot of various factors. Typically, the Tor revel in is slower than moderate for the explanations we defined previous.
When you do attach, you’ll come to a get started display:
From right here, you’ll be able to start to browse the internet, both the usage of a devoted URL with the .onion TLD, or the DuckDuckGo seek bar.
And not using a replicate hyperlink for the web site you wish to have to view, Tor is just like another browser, albeit a painfully gradual one this is lacking some “high quality of existence” options (which we’ll talk about in a while):
Alternatively, you’ll be able to additionally use an onboarding wizard if that is your first time with Tor.
You’ll to find the hyperlink to this wizard within the top-left nook of the beginning display. This may carry up a tick list that can assist you discover ways to navigate your new browser.

Every panel will let you know extra about Tor, however in some circumstances will even come up with get admission to to different configuration monitors to make adjustments:
Actually, there are a couple of tactics to get admission to those settings, which we’ll cross into subsequent.
Adjusting the Tor Browser’s Settings
If you wish to have to configure the Tor Browser, you’ll be able to accomplish that in a couple of tactics. The everyday Tor Browser > Personal tastes hyperlink within the toolbar is one means:
Alternatively, you’ll be able to additionally to find the settings the usage of the Onboarding Wizard too:
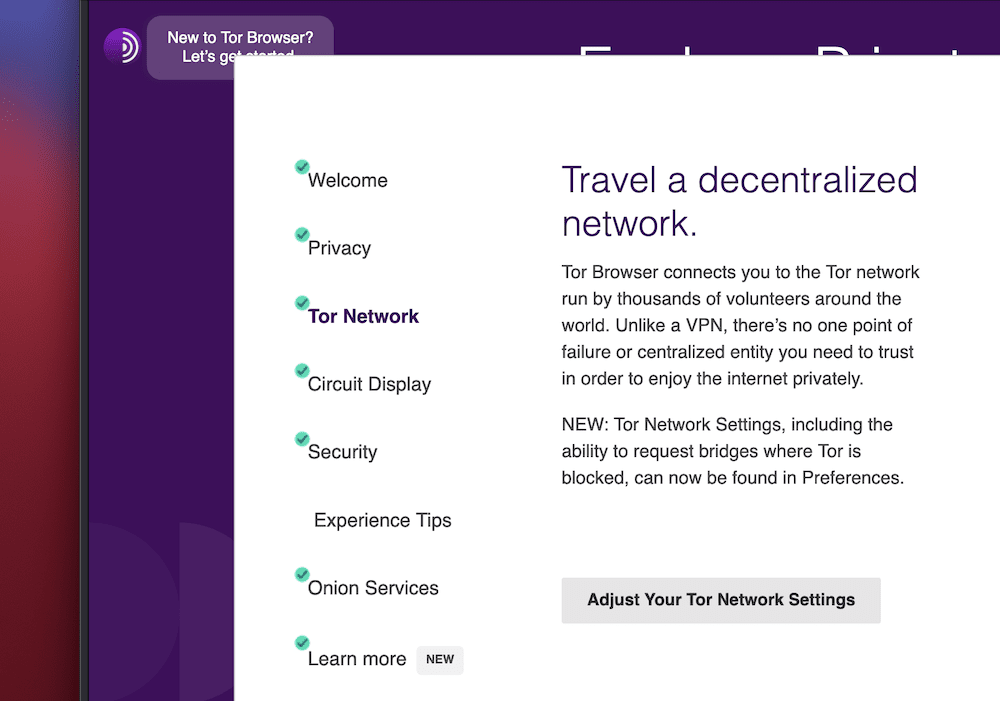
Regardless, the Connection tab inside the Personal tastes display will allow you to alternate issues up if you wish to have to:
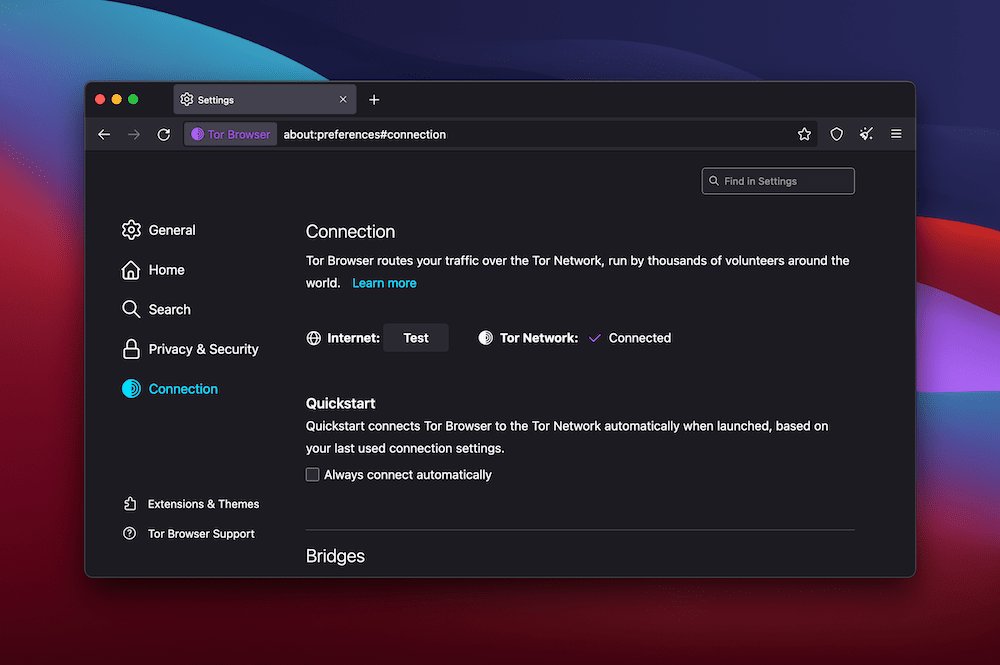
Converting those settings is past the scope of this newsletter, however there’s so much you’ll be able to do right here. As an example, you’ll be able to check your connection, arrange a handy guide a rough get started function, regulate your proxy settings, and extra.
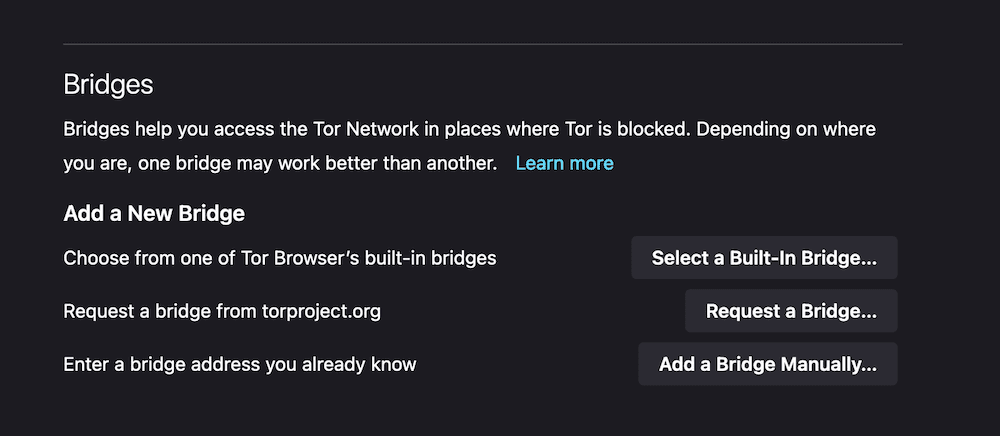
There’s additionally get admission to to “bridges.” Those are tactics to hook up with Tor the place it could differently be blocked. If of a bridge, you’ll be able to input it within the Bridges phase, or you’ll be able to request one from the Tor Venture itself:
Instead of this, you’ll need to take a look at over your safety settings from the icon within the browser’s toolbar:
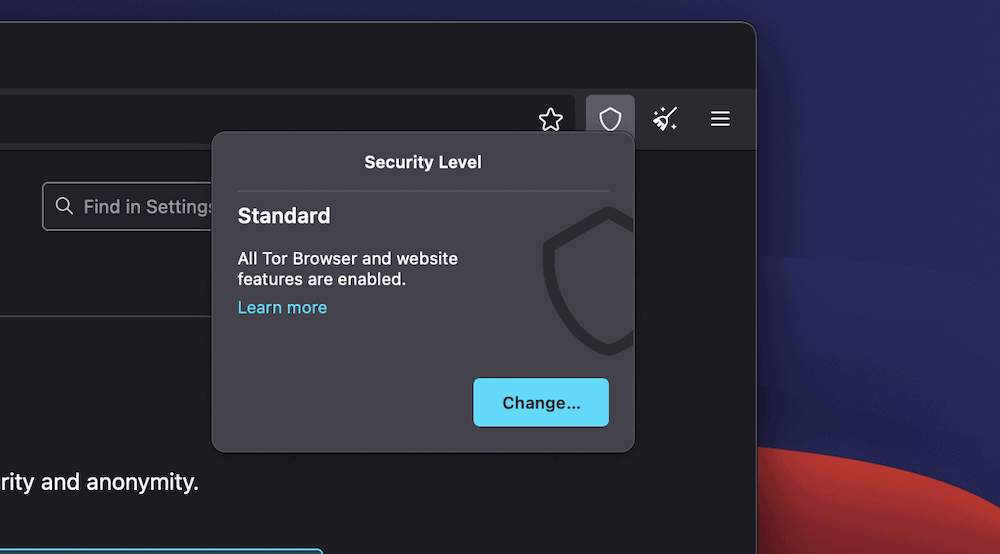
The Alternate button right here will take you to the Privateness and Safety phase of the Personal tastes web page. This will provide you with a solution to modify your safety settings on your explicit goal:
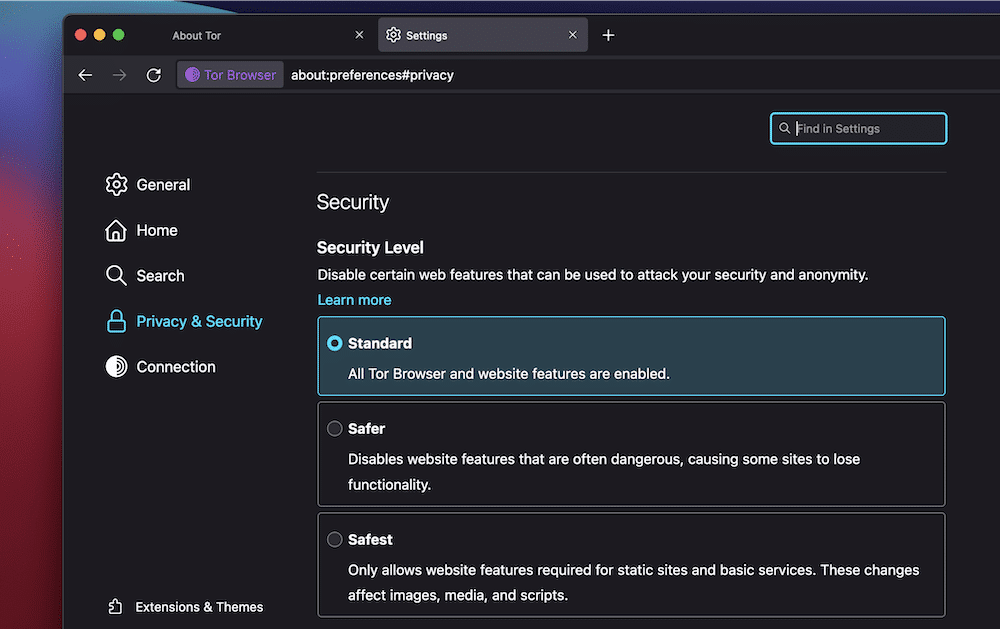
When you glance over the settings and set the entirety as much as your specs, you’re loose to browse the Onion Community.
Abstract
There are other ranges of privateness and safety you’ll be able to take relating to your internet protection. Whilst maximum business browsers corresponding to Chrome, Firefox, and Safari be offering various levels of choices that relate to privateness and safety, none can be offering the whole set of options you wish to have to traverse the darkish internet.
On this Tor Browser assessment, you discovered nearly the entirety you wish to have when it comes to how you’ll be able to get admission to that darkish internet and whether or not this selection is a superb one on your functions.
In our opinion, Tor is one of the simplest ways to get onto the darkish internet. Different browsers merely don’t have the capability or backing to maintain but.
Do you might have anything else so as to add to our Tor Browser assessment? Tell us your ideas within the feedback phase beneath!
The put up Tor Browser Evaluation: An Crucial and Nameless Solution to Surf the Internet gave the impression first on Kinsta®.
WP Hosting


